Rule conflict detection method and system aimed at large-scale packet classification rule set
A conflict detection and packet classification technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of algorithm space complexity that cannot meet the requirements, only support, and too many bit vector operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
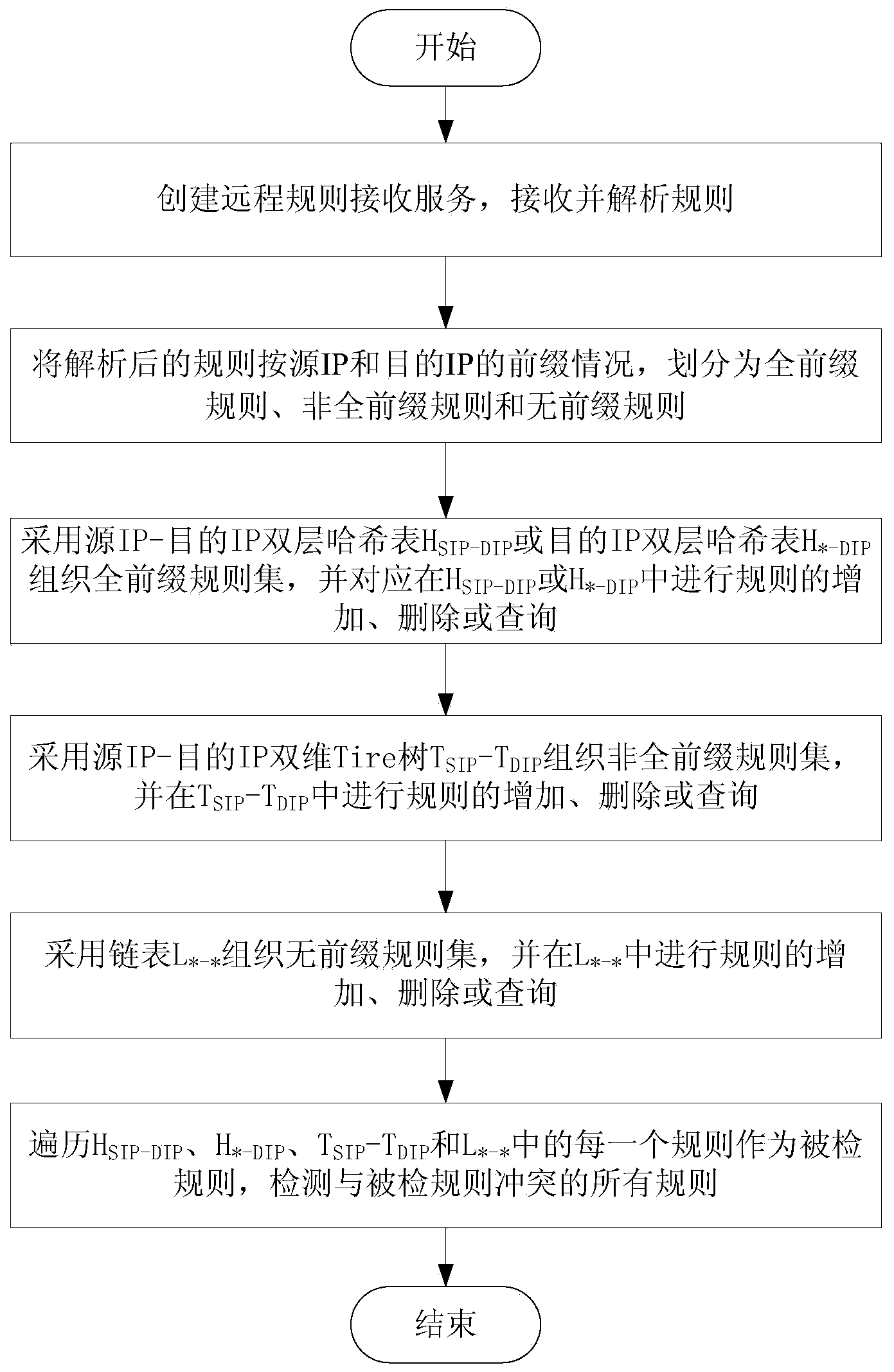
[0073] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
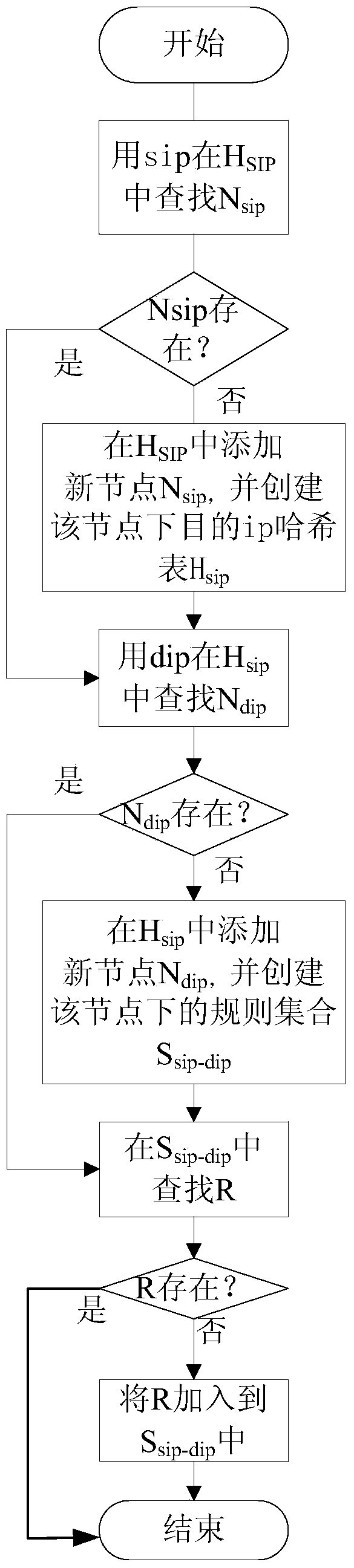
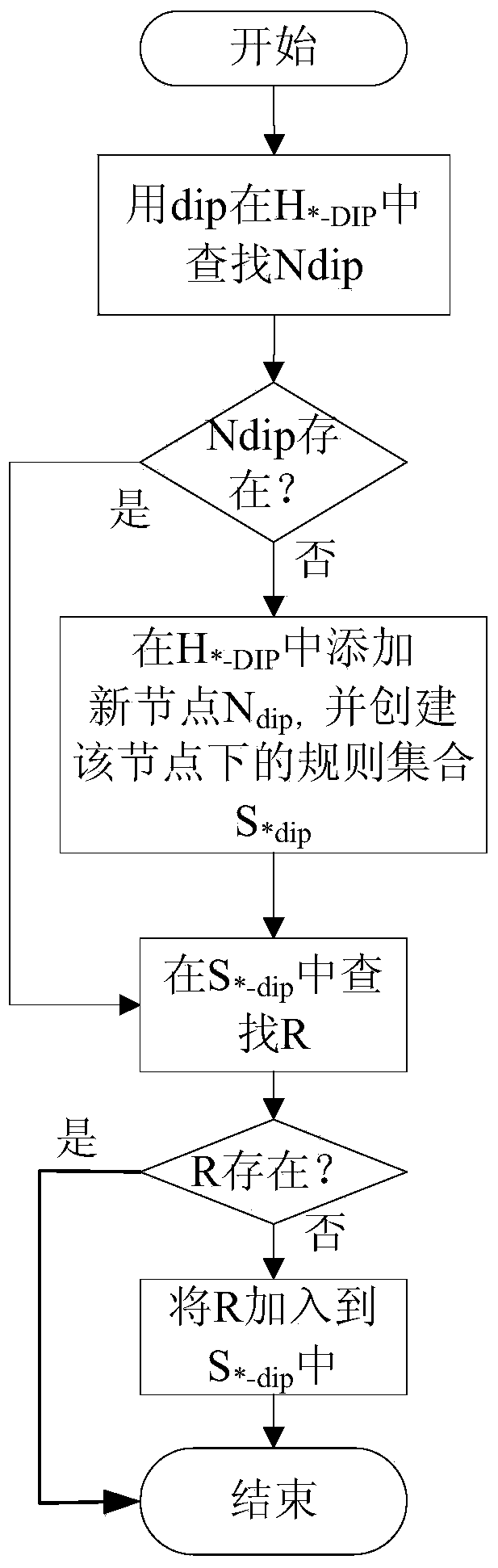
[0074] According to the prefixes of the source IP component and the destination IP component of the rule, the rules are divided into three types: full-prefix rules, non-full-prefix rules and no-prefix rules. When the prefix length of the source IP and the destination IP of the parsed rule are both 32, or when the prefix length of one of the source IP and the destination IP is 0 and the prefix length of the other is 32, the rule is divided into full prefixes rule; when the prefix length of the source IP or destination IP of the parsed rule is between 1-31, the rule is divided into a non-full prefix rule; when the prefix length of the source IP and destination IP of the parsed rule is When 0, the rule is classified as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com