Method for verifying compiler by graph isomorphism
A compiler and graph isomorphism technology, applied in the field of compiler security verification, can solve problems such as inability to verify compiler security, and achieve the effect of verifying security, easy implementation, and simple isomorphism judgment algorithm
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
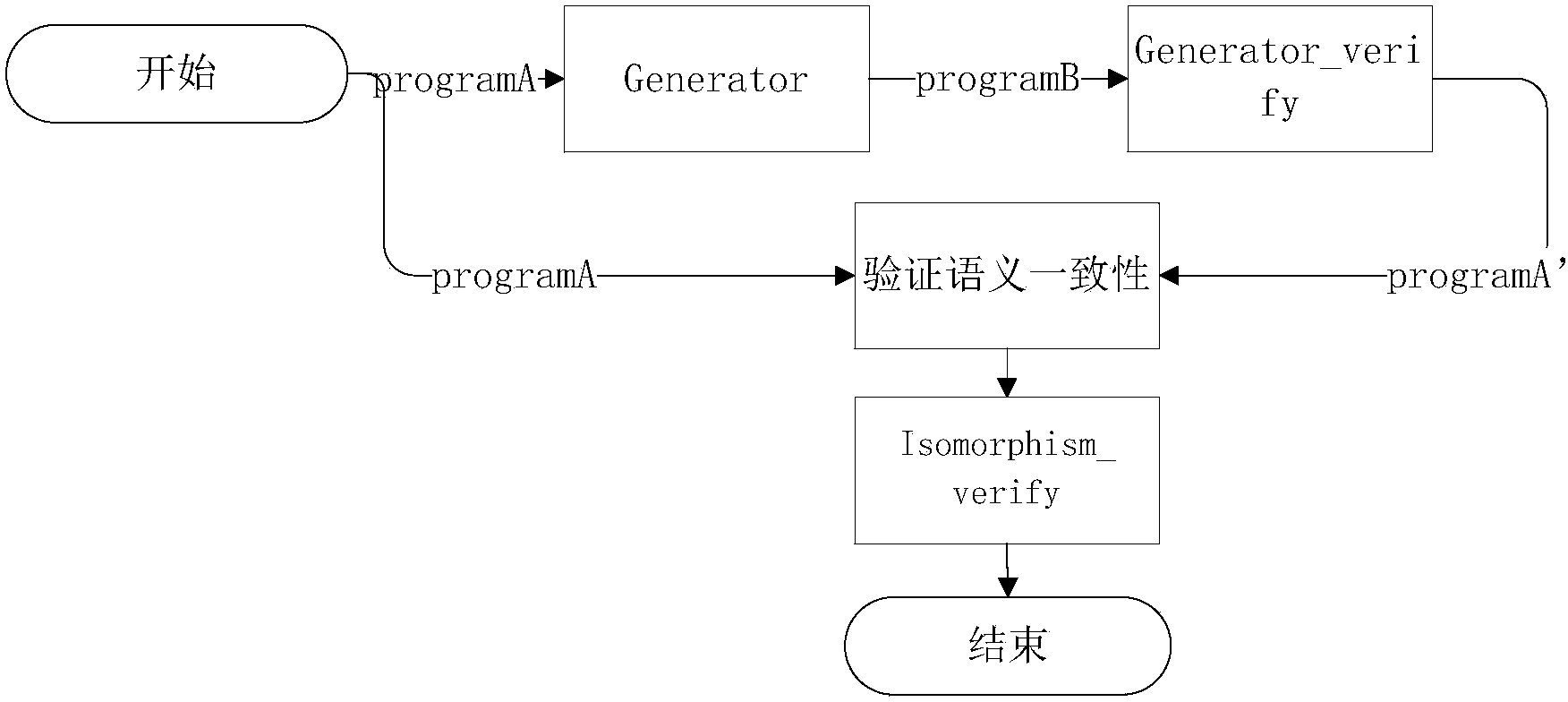
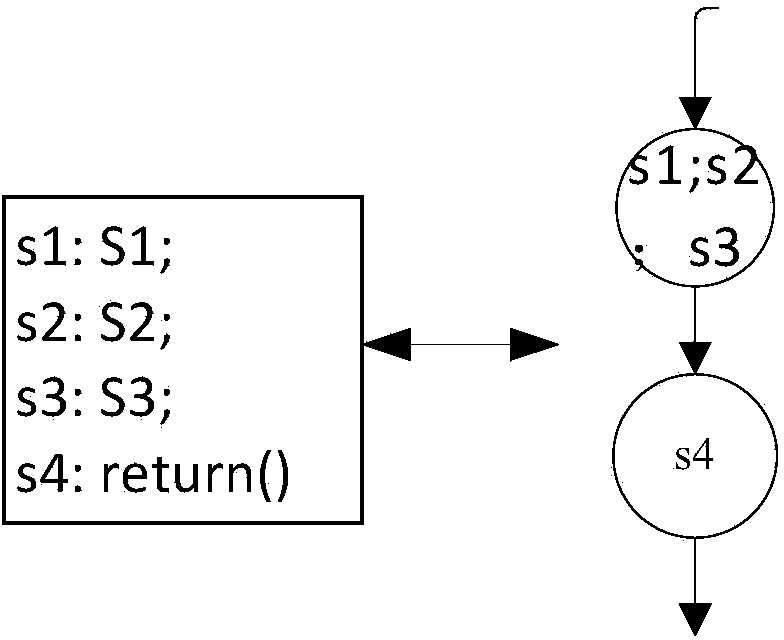
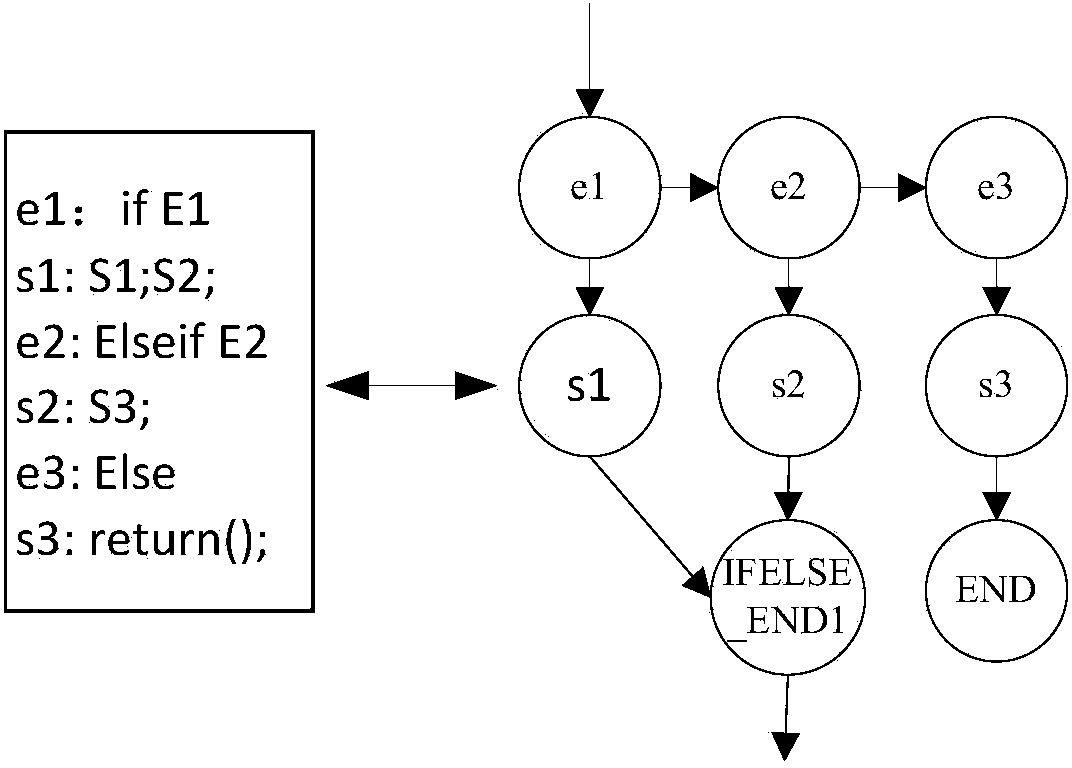
[0042]The method for verifying a compiler using graph isomorphism in the present invention includes a source program to be processed and a compiler for generating a target program from the source program, a decompiler is established in a selected environment, and the target program is decompiled by the decompiler into Comparing the program, verifying the semantic consistency between the comparing program and the source program, and then establishing the relevant node information of the control flow graph of the source program and the comparing program on this basis, and then performing isomorphism judgment. The verification environment of the present invention is C language.
[0043] Such as figure 1 As shown, for example: first use the compiler Generator to be verified to convert the source program programA into the target program programB;
[0044] Newly develop a decompiler Generator_verify for the target program programB;
[0045] Compile the target program programB using...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com