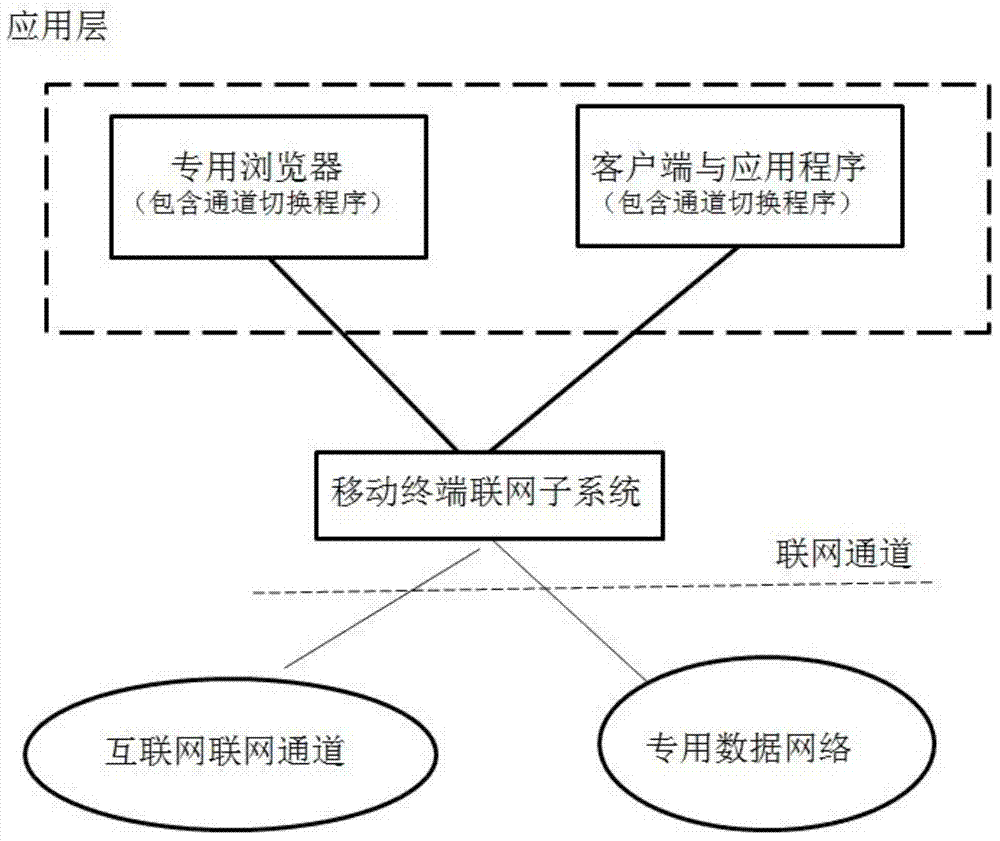
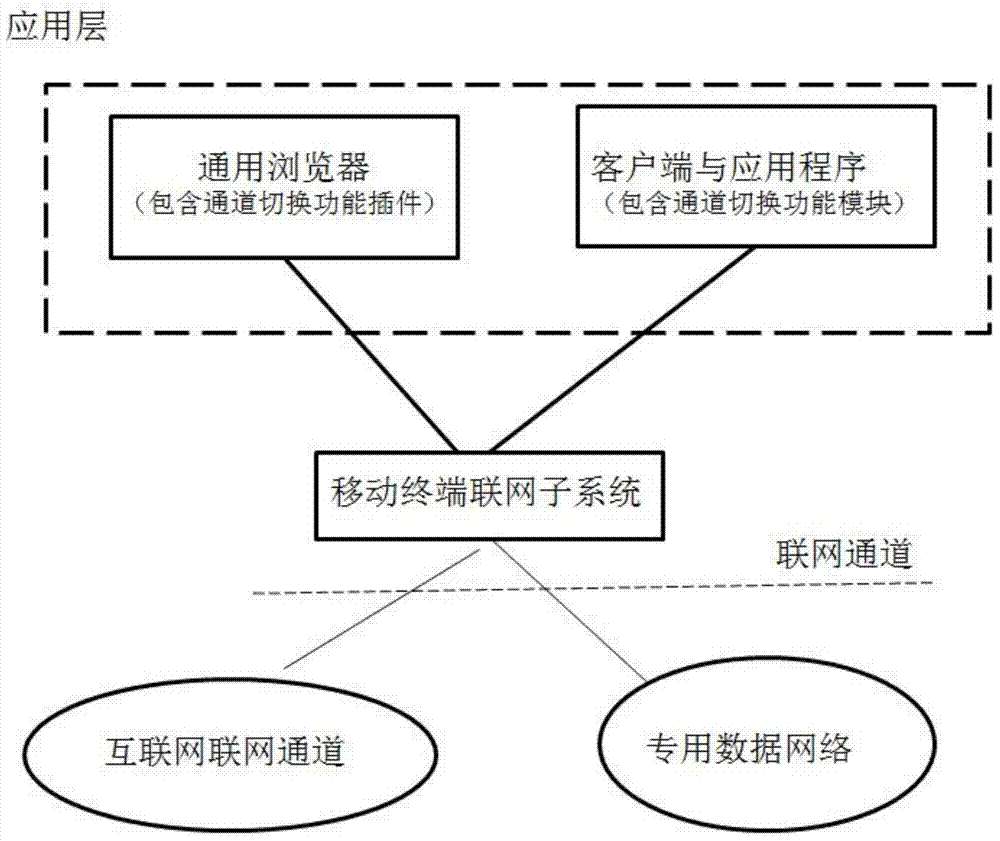
Mobile payment security system for wireless data private network physical isolation internet
A mobile payment and physical isolation technology, which is applied in the system field of switching network channels between Internet access channels and secure payment applications, can solve the problems of high fraud, high terminal requirements, and high costs, and achieves improved security, guaranteed security, and guaranteed security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
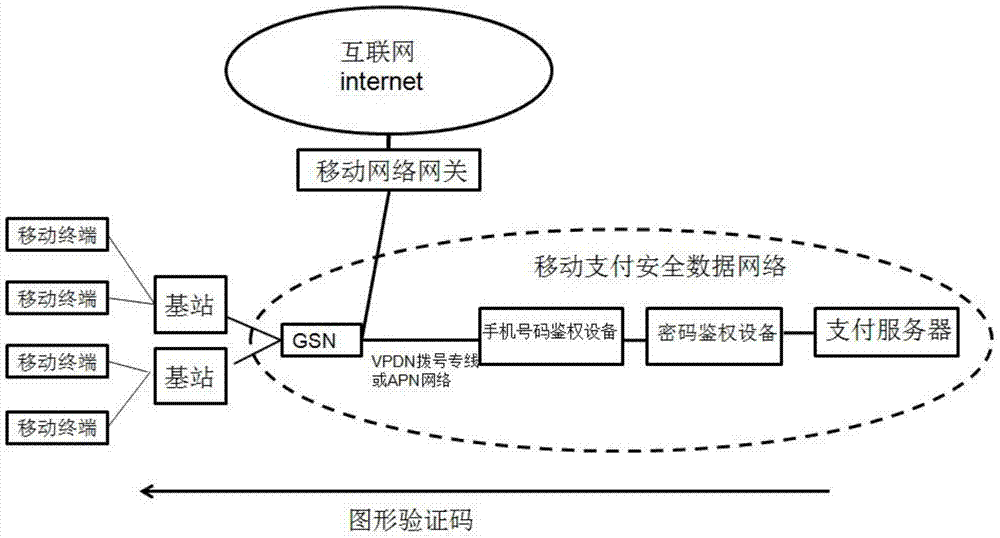
[0040] refer to figure 1 . In a preferred embodiment described below, the wireless data private network physically isolates the mobile payment security system of the Internet, which sequentially includes a payment server, a mobile phone number authentication device, a password authentication device, and a mobile payment security data network that is isolated from the Internet. APN or VPDN network connected to GSN gateway. The application system including the payment server and authentication device is built in the mobile payment security data network isolated from the Internet. The payment server establishes the account, mobile phone number, IMSI number, and password through the password authentication device and mobile phone number authentication device. The multi-authentication mode bound in one, connects to the mobile network gateway GSN through the mobile payment security data network access point name APN dedicated line and / or virtual private dial-up network VPDN dedicat...
Embodiment 2
[0041] Example 2: Mobile phone number binding account function
[0042] figure 1 Among them, in the mobile payment security system where the private wireless data network is physically isolated from the Internet, the system model of the mobile phone number binding function is used, and the system model of the mobile phone number binding function includes GSN equipment and mobile phone number authentication equipment in turn. The mobile phone shuts off the Internet access channel, connects to the mobile payment security network, and establishes a communication tunnel with the mobile phone number authentication device. During the establishment of the communication tunnel, when the mobile phone sends a time domain request, the mobile phone sends a time domain session (Session refers to an end user The time interval for communicating with the interactive system, usually refers to the time elapsed from registering into the system to logging out of the system); GGSN or SGSN first li...
Embodiment 3
[0045] Example 3: Password authentication mode
[0046] refer to figure 1 . In the above-mentioned embodiment 1, the mode of password authentication includes digital password, or biometric password such as fingerprint, face or pupil and so on. Password authentication can be a single form such as a number, or it can be a superposition of multiple forms. Such as the form of digital plus fingerprint.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com