Malicious feature extraction method and device and storage media
A feature extraction and malicious technology, applied in the Internet and security fields, can solve the problems of low reporting rate, low family virus identification rate, and low efficiency, so as to improve the response speed, reduce the influence of human subjective factors, and save analysts Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
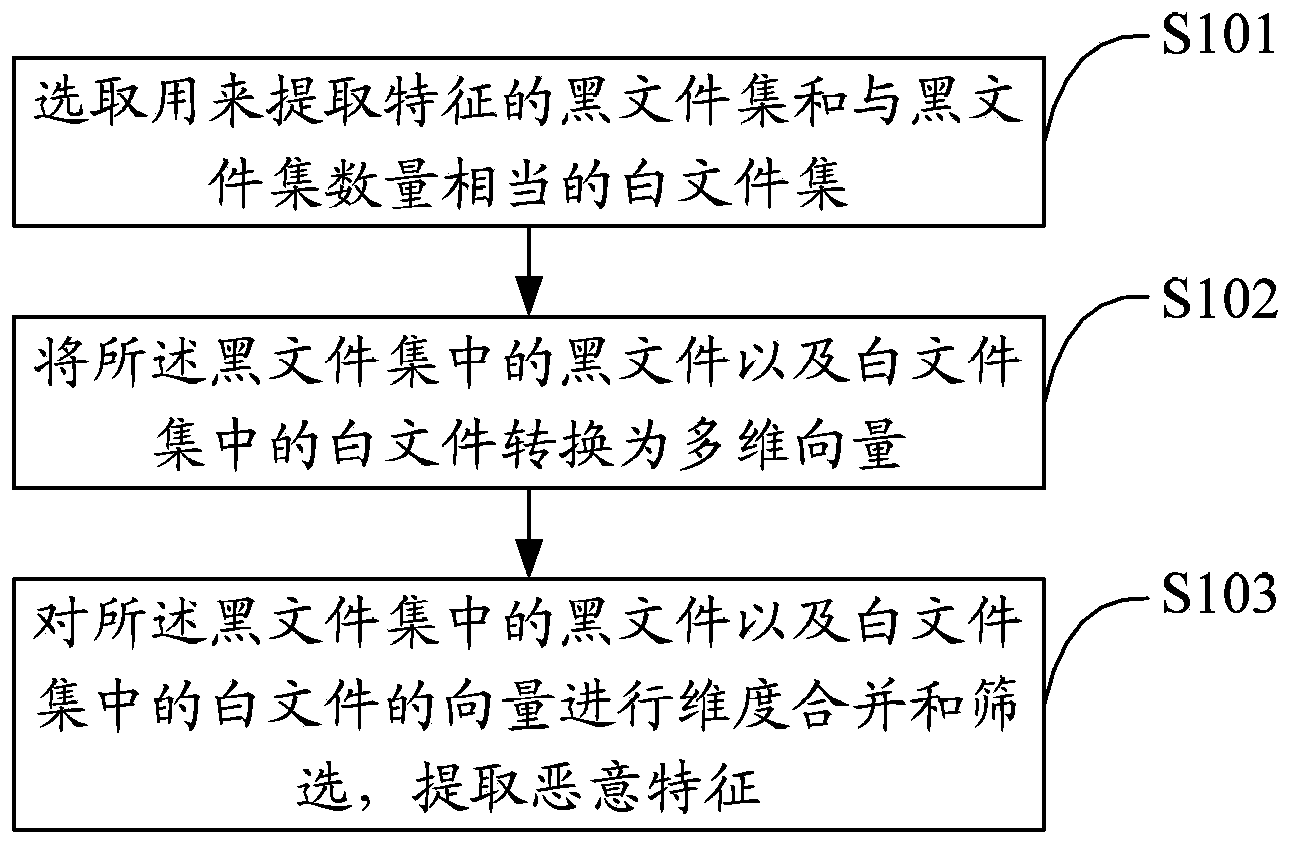
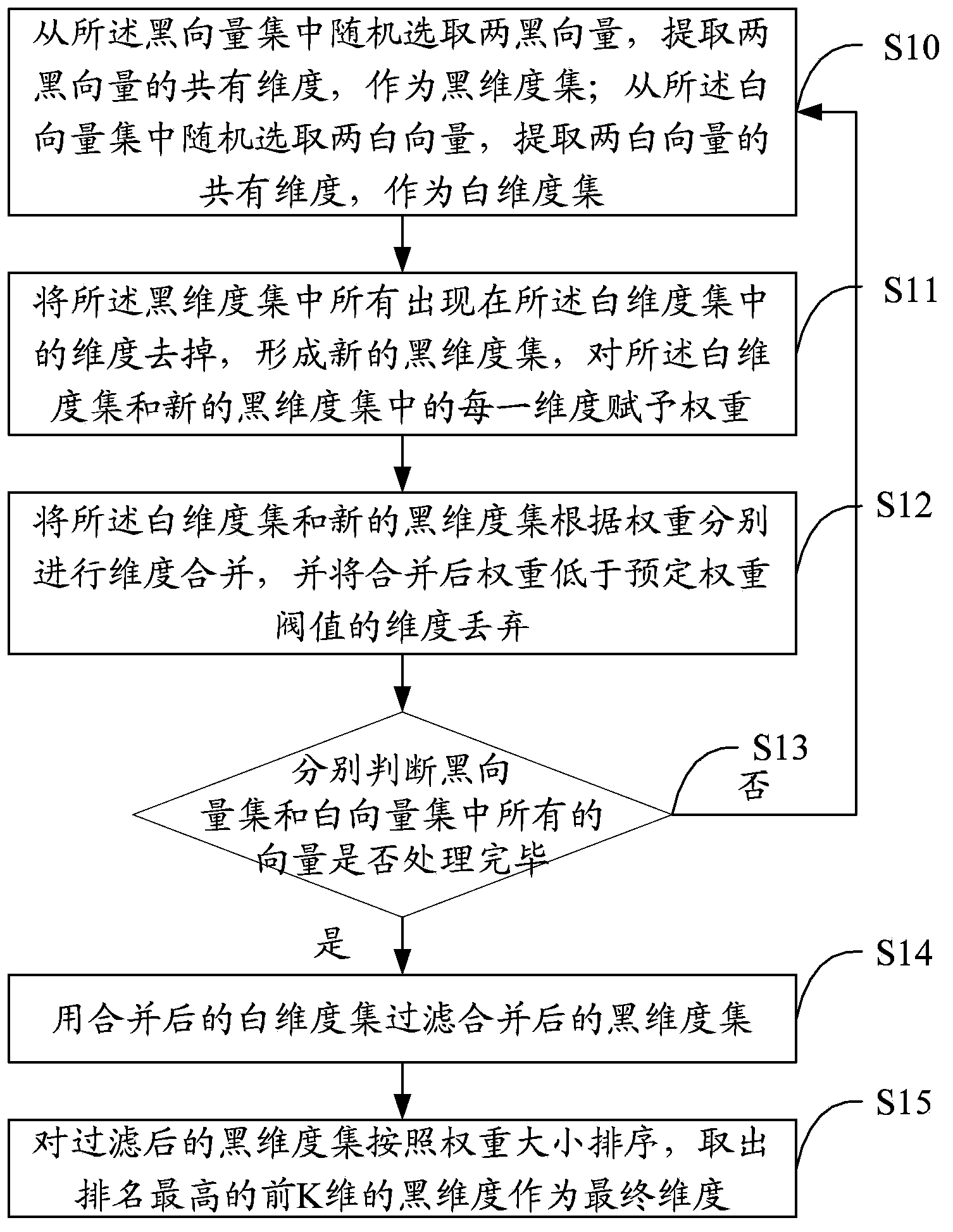
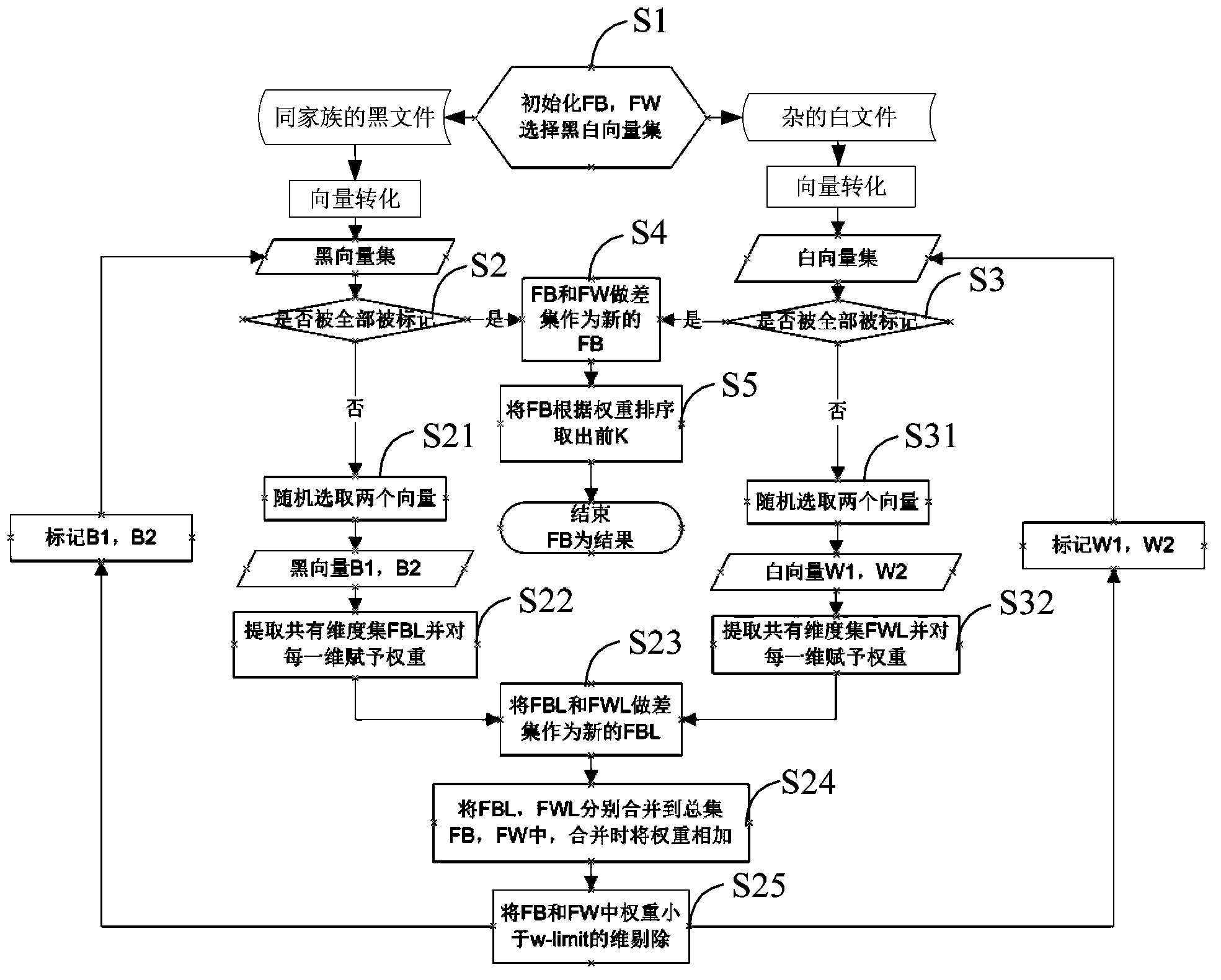
[0028] The solution of the embodiment of the present invention is mainly to: automatically perform vector conversion on known black file sets and white file sets, and perform dimension merging and screening on the converted vectors, so as to improve the extraction efficiency of malicious features.
[0029] The malicious file in the present invention may be a virus file or other malicious files, and the following embodiment uses a virus file as an example for illustration. Among them, the technical terms involved include:
[0030] Black Files: Virus Files
[0031] Black vectors: vectors converted from virus files
[0032] White files: normal non-virus files
[0033] White vector: the vector converted from a normal non-virus file
[0034] PE file: an executable file format under the windows system
[0035] Such as figure 1 As shown, a preferred embodiment of the present invention proposes a malicious feature extraction method, including:
[0036] Step S101, selecting a bla...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com