Verification method achieved by combining human faces with identities
An identity verification method and identity verification technology, applied in digital data authentication, instruments, electronic digital data processing, etc., can solve the problems of security problems and limit the large-scale promotion and application of biometric identification technology, and achieve the effect of high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
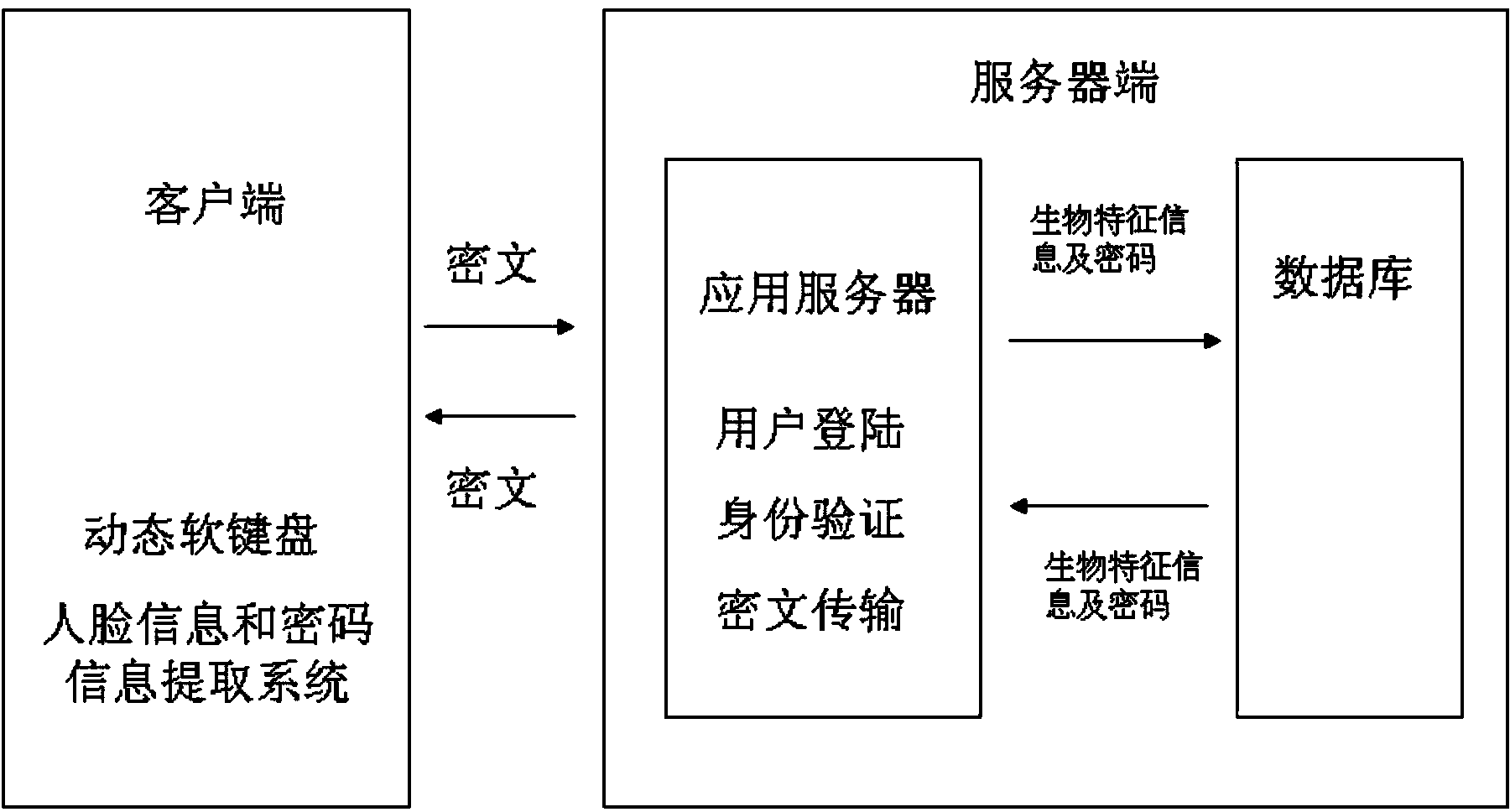
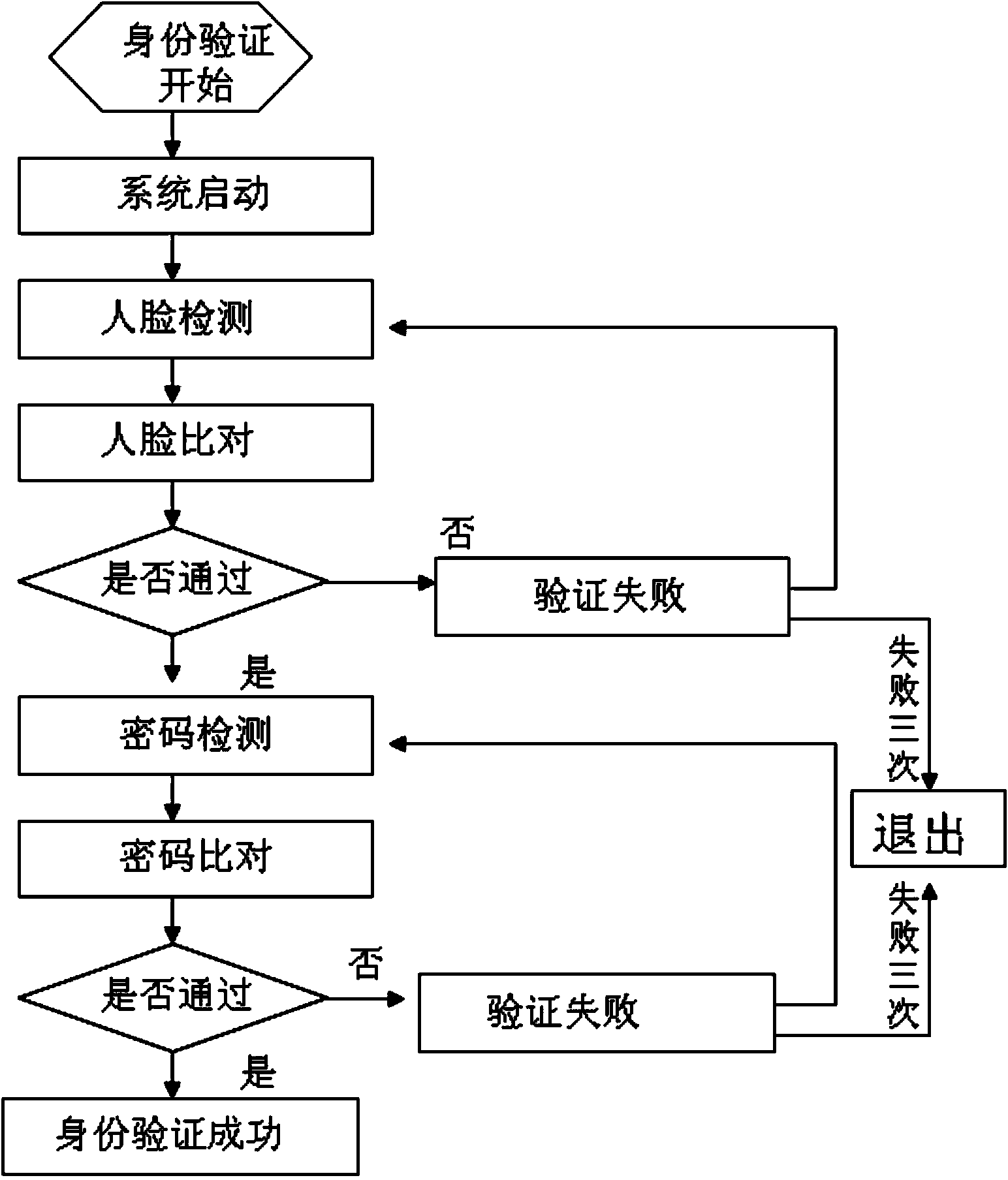
[0022] User Zhang San first sets up an account in the bank and submits face information and his chosen identity verification password of 56789, 2525 alarm password and 111888 backup password to be included in the database of the bank server. Then Zhang San needs to pay for online shopping through the client installed on the mobile phone. After logging into the bank account, he first captures his face image through the mobile phone camera and sends the ciphertext obtained through the symmetric encryption algorithm to the bank server. After feature extraction and template extraction, it is compared with the face information in the bank server database. After the comparison is matched, the bank server notifies Zhang San to enter the identity verification password through the cipher text, and Zhang San enters the identity verification password through the dynamic soft keyboard that comes with the client. And the ciphertext obtained through the asymmetric encryption algorithm is sen...
Embodiment 2
[0027] After a prison system sets up an access control system network, it first collects the face information submitted by each prison guard and the 13856 identity verification password and 25888 alarm password selected by the prison guard A to be included in the database of the access control system server. Usually prison guard A goes to work through the client with camera and dynamic soft keyboard installed at each cell door of the prison to use his face information to log in. The server compares the face image of prison guard A with the face information in the database of the access control server through feature extraction and template extraction. The built-in dynamic soft keyboard enters the identity verification password and sends the ciphertext obtained through the asymmetric encryption algorithm to the access control server. The access control server compares the identity verification password entered by prison guard A with the password information in the database, and ...
Embodiment 3
[0030] Wang Wu installs an authentication system with a camera and a dynamic soft keyboard on the safe, so that the safe can only be opened after successful authentication. Then Wang Wu submitted his face information and his selected 666888 identity verification password, 5188 alarm password and LI12345 backup password to be included in the database of the safe server. At this point the client and server are merged together. When Li Si needs to open the safe later, he first needs to log in through face information. The identity verification system of the safe compares Wang Wu's face information with the face information in the identity verification system database after feature extraction and template extraction. After matching, prompt to enter the identity verification password. Wang Wu enters the identity verification password through the dynamic soft keyboard of the identity verification system. The identity verification system compares the identity verification password en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com