Real-time encryption and decryption system and real-time encryption and decryption method for mobile products
A mobile product, encryption and decryption technology, applied in the field of data security, can solve the problems of complicated operation, low efficiency, no encryption and decryption process, etc., and achieve the effect of high security and high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
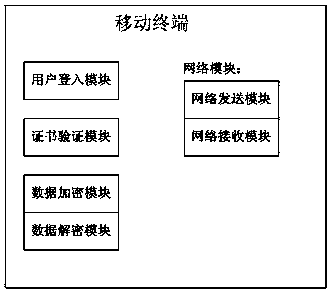
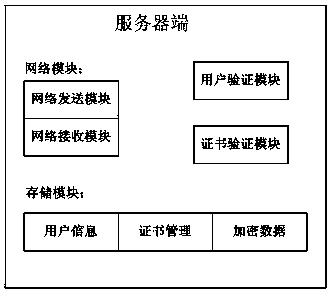
[0048] For portable mobile products, such as mobile phones, the present invention divides its data into common data and encrypted data. Save ordinary data on the user's mobile phone, while encrypted data is saved on the server side.
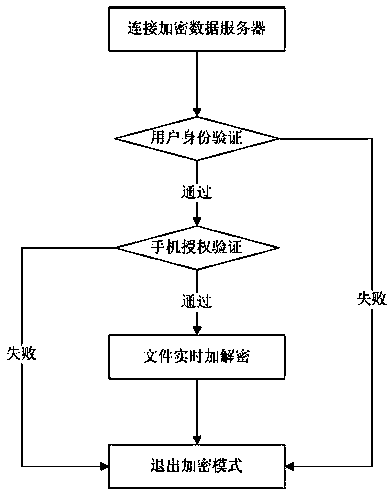
[0049] When the user connects to the encrypted data server and passes the identity verification and mobile phone certificate verification, the mobile phone will enter the encryption mode. In this mode, any document data operation (including creating, browsing, editing, changing, etc.) The client downloads the encrypted data, authorizes the mobile phone to decrypt and display it to the user in plain text, and any operation results of the user will be encrypted and stored on the server.
[0050] When the user exits the encryption mode, the mobile phone cannot access the encrypted data, and the user enters the normal mode, and the operation data is saved in the user's mobile phone at this time.
[0051] The real-time encryption and decryption devic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com