Method and system for processing signals of hardware Trojan detection in integrated circuit
A hardware Trojan detection, integrated circuit technology, applied in the direction of electronic circuit testing, etc., can solve the problem of not being able to detect hardware Trojans, etc., to achieve the effect of improving accuracy, improving security, and improving detection resolution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0067] Although the present invention has been described above in conjunction with the flow chart, the present invention is not limited to the above-mentioned specific embodiments, for example:
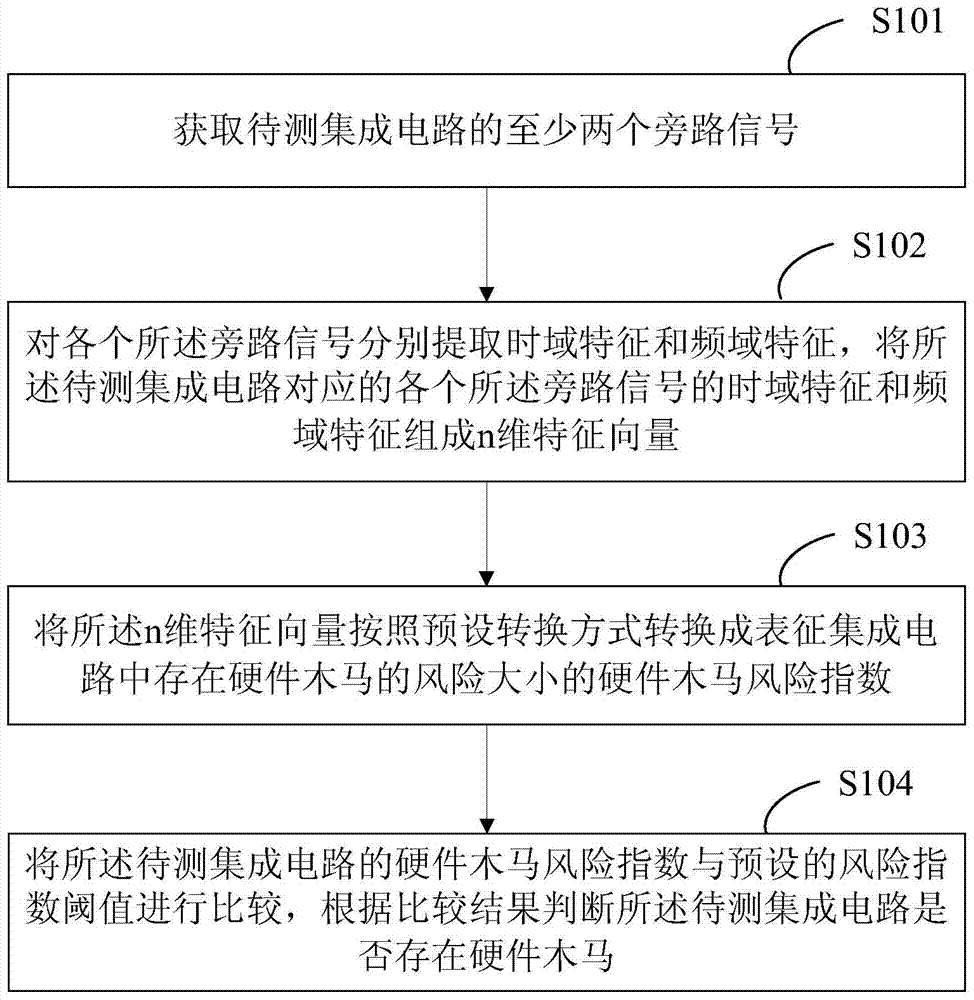
[0068] The signal preprocessing mentioned in the step S101 of the present invention, in addition to the above-mentioned "window truncation" and "filtering", can also include signal preprocessing methods such as "wavelet analysis" and "wavelet envelope analysis". The purpose of the present invention can still be achieved after the processing method replaces the "windowing and truncation" and "filtering" described above.
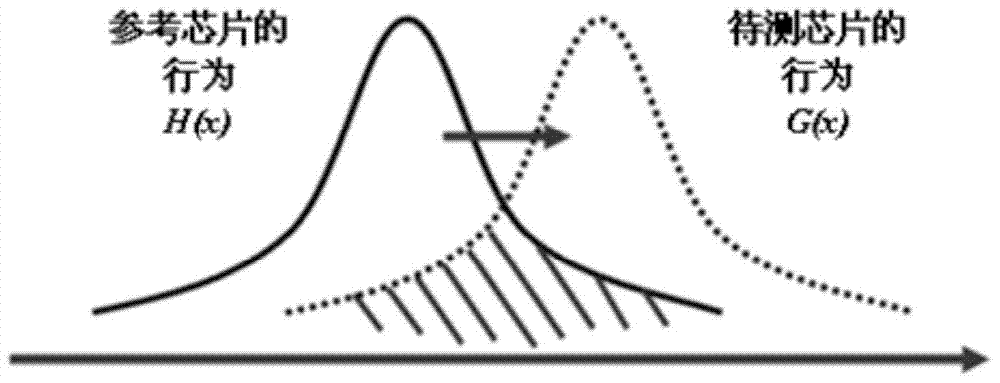
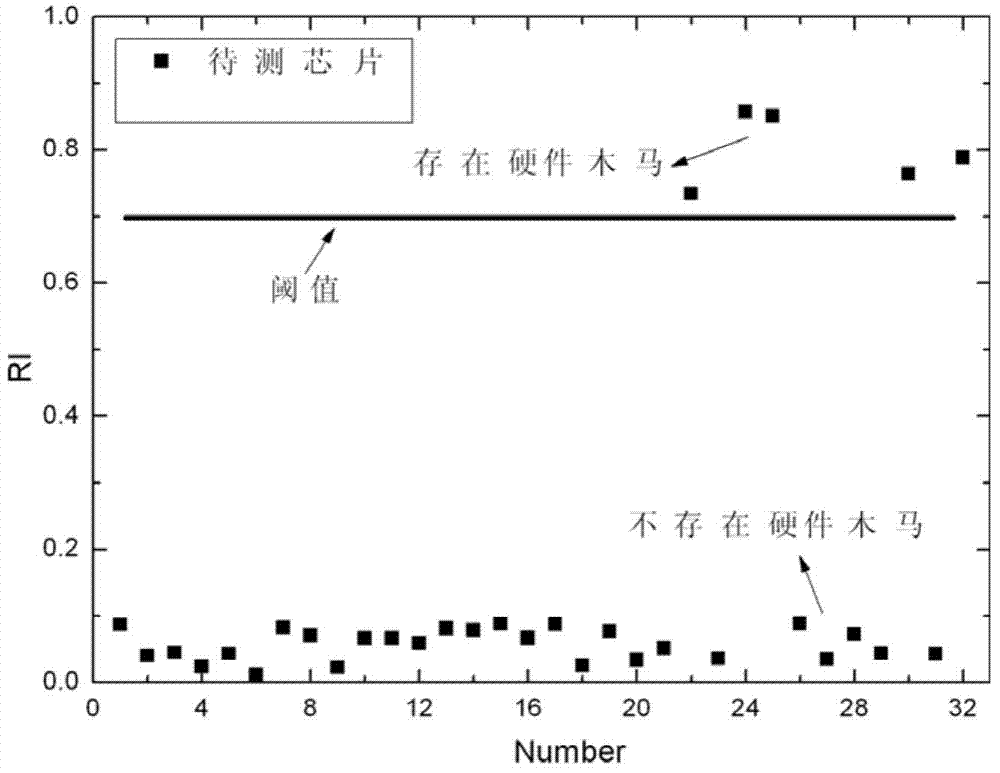
[0069] The hardware Trojan risk index generated in step S103 of the present invention, in addition to the above method based on the L2 distance calculation method between two different probability Gaussian distributions to generate the hardware Trojan risk index, can also use "based on self-organizing map (SOM) In the minimum quantization error (MQE)", "based on neura...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com