Trusted security enhancement method in desktop virtualization environment
A desktop virtualization and trusted technology, applied in the field of network security, can solve the problem of access network and user terminal heterogeneity data center, reduce the ability of user behavior review, etc., to achieve the effect of improving security and ensuring transmission security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with drawings and embodiments.
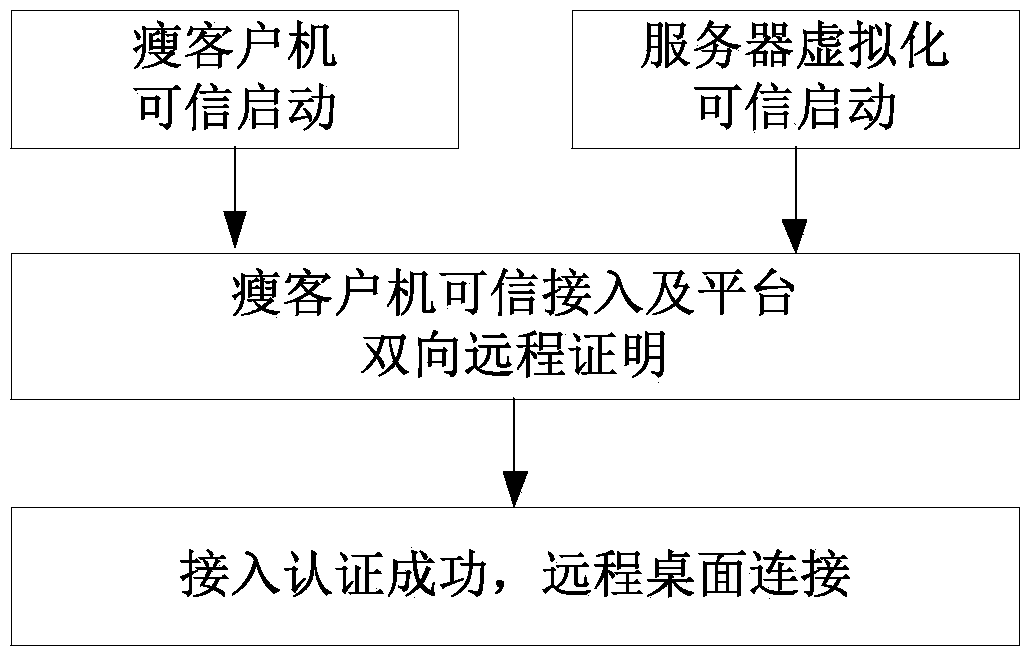
[0027] The main flow chart of the method of the present invention is as follows figure 2 shown, including the following steps:
[0028] Step 1: Thin client and server perform trusted boot.
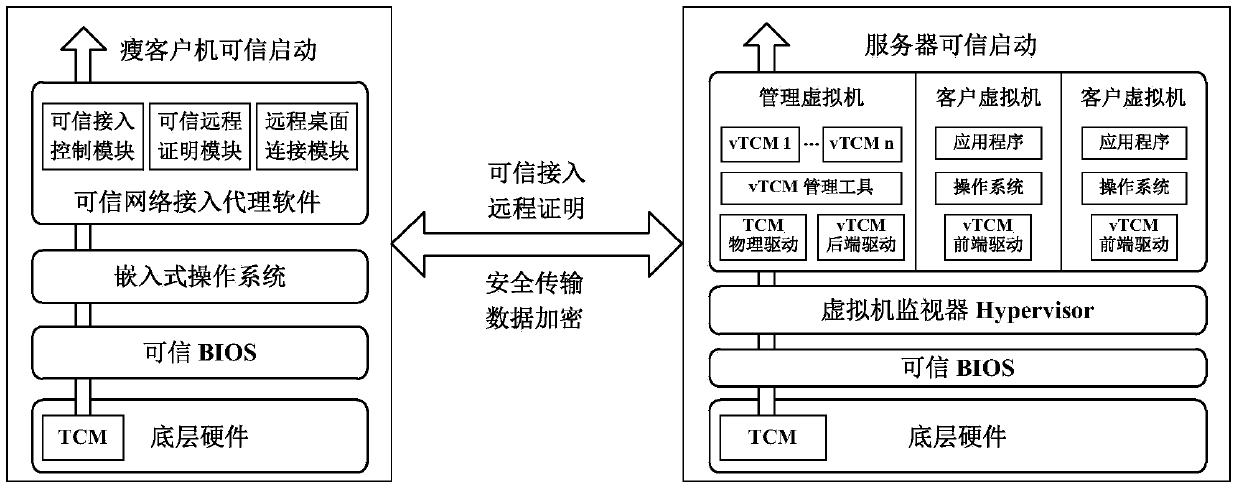
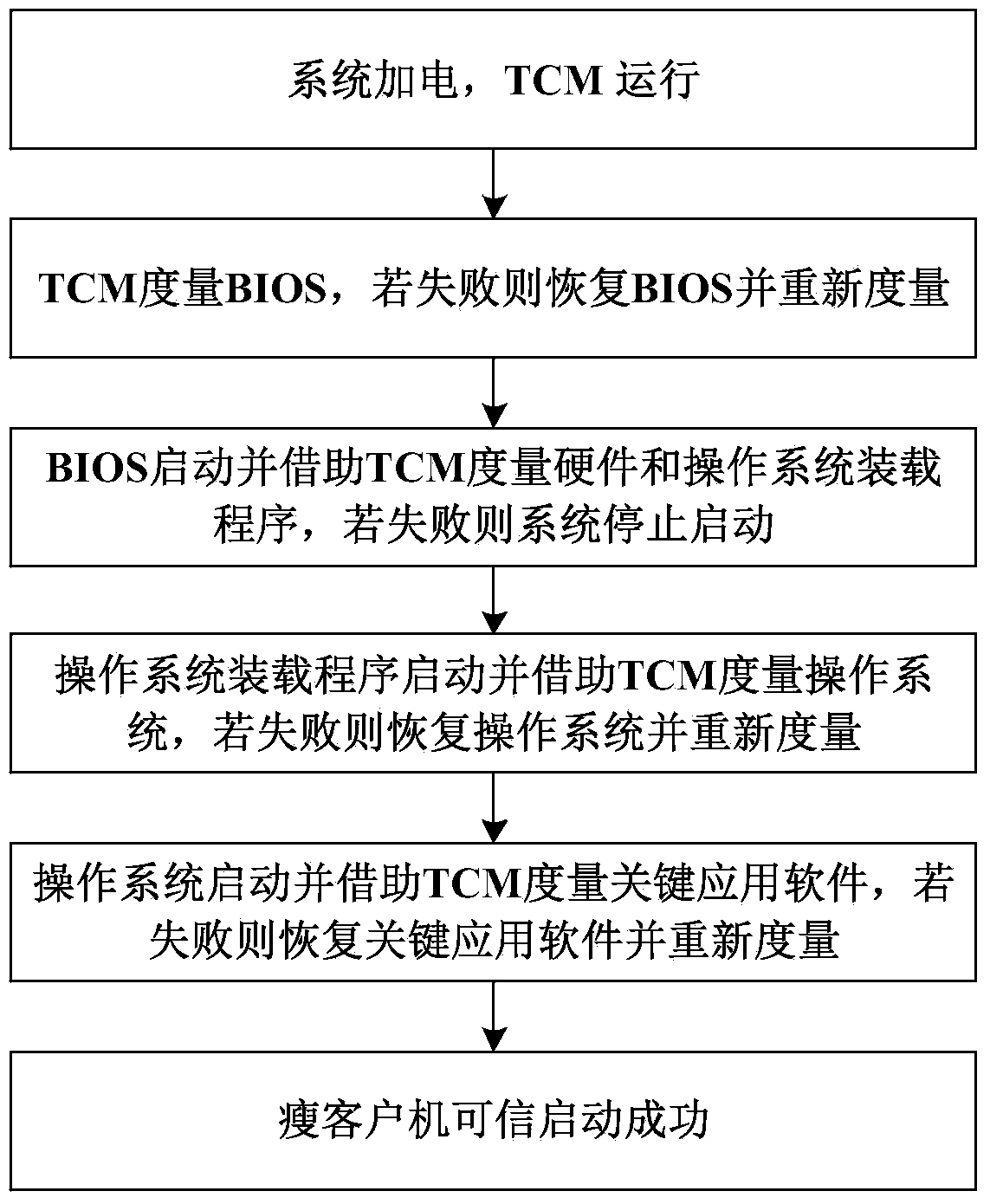
[0029] The trusted cryptographic module TCM is selected as the root of trust of the entire platform to provide the most basic trusted computing services for the entire platform. As the root of trust, TCM can well solve the problem that the BIOS can be illegally tampered with in the chain of trust transfer mechanism and cannot guarantee the trustworthiness of the root of trust. The trusted boot process for a thin client is as follows: image 3 As shown, the method is as follows:
[0030] (1) Under the action mechanism of the trust chain, after the system is powered on, the control right is first passed to the TCM, and the TCM measures the integrity of the BIOS, and stores the me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com