Data security aggregation method with privacy protection function
A privacy protection and aggregation method technology, applied in the field of data aggregation and fusion algorithms, can solve the problems of network security single point of collapse, difficult to be practical, does not support key update, etc., to improve security performance, ensure privacy, and ensure privacy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
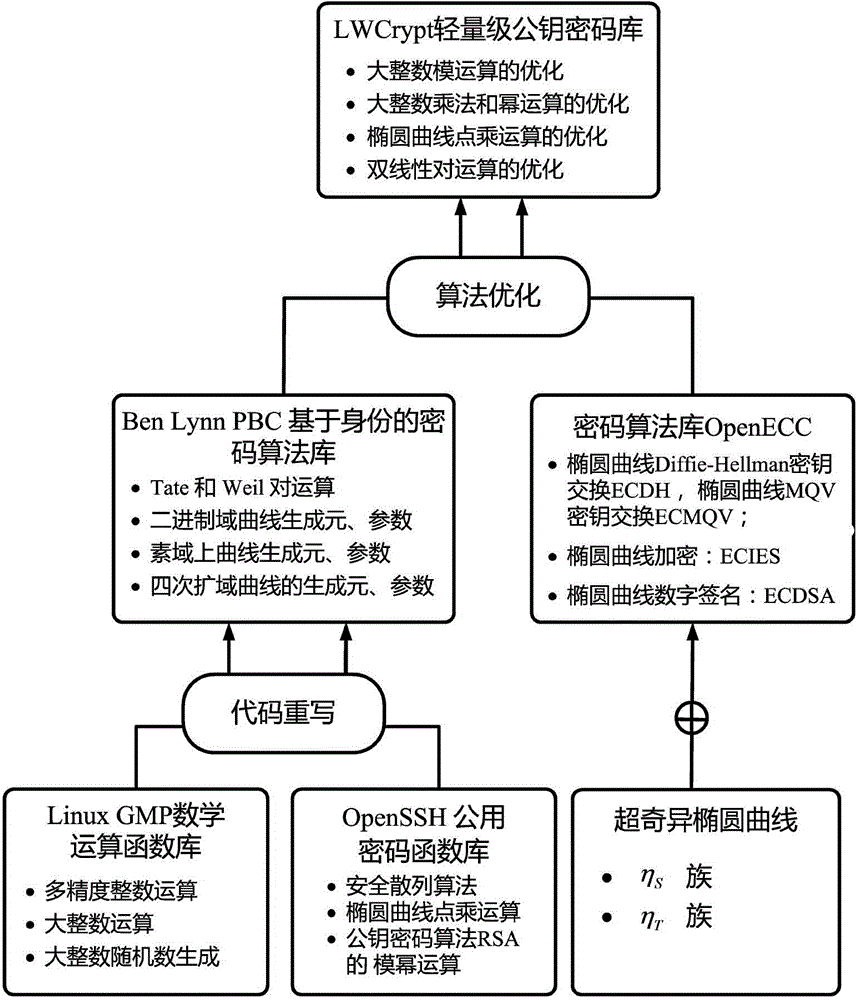
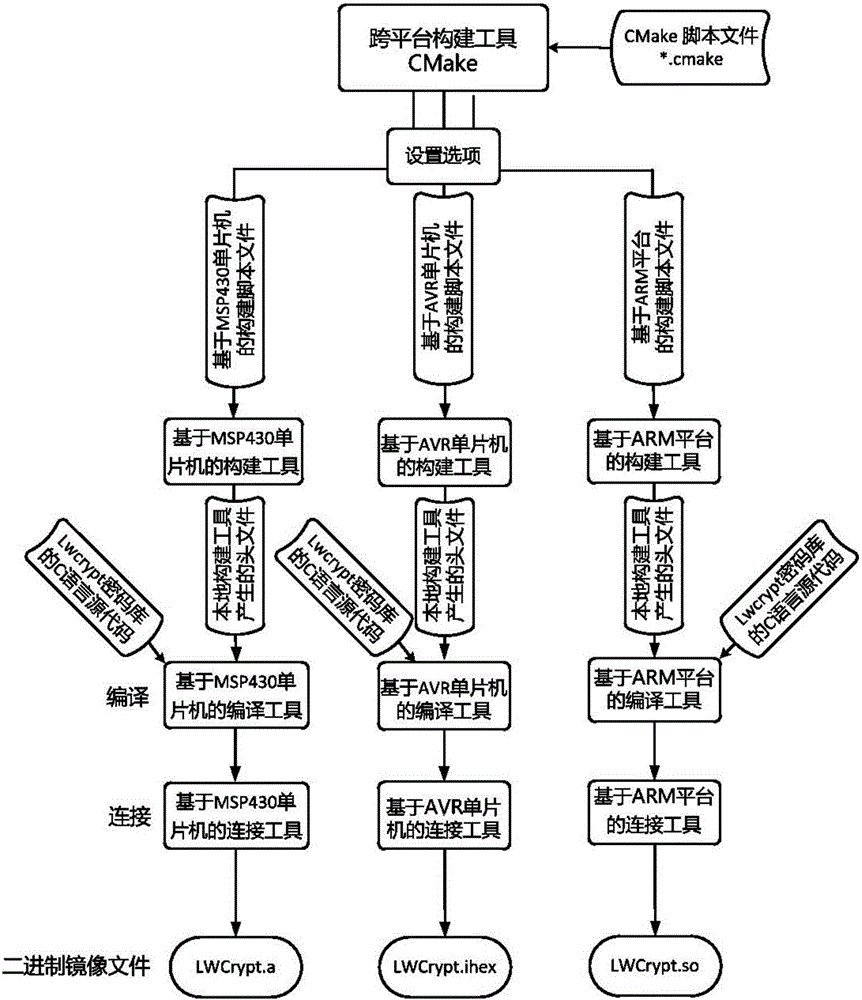
[0022] A data security aggregation method with privacy protection function of the present invention is as follows: in the data aggregation process, an identity-based authentication key negotiation mechanism, a homomorphic encryption mechanism and an aggregation signature mechanism are adopted; the privacy in the data aggregation process can be solved and confidentiality, and reduce the impact on system operating efficiency while ensuring system security; the specific methods are:
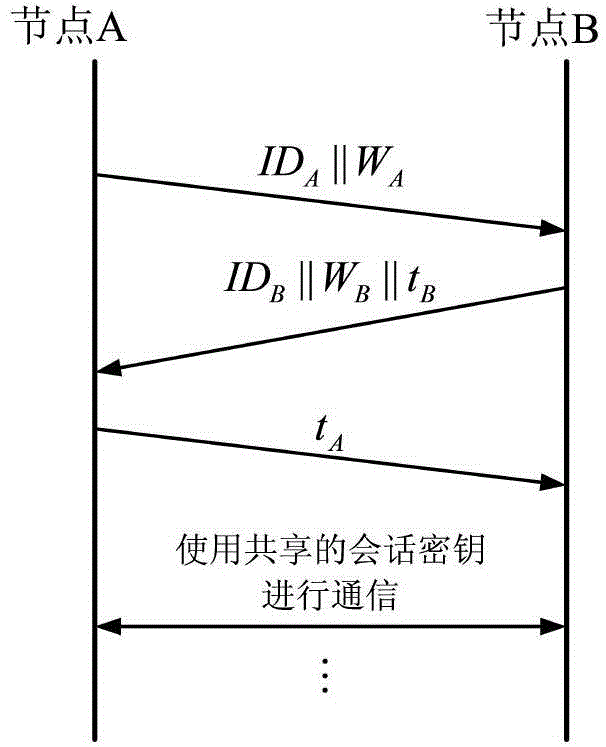
[0023] 1) Establish an identity-based key negotiation mechanism with authentication: Deploy an identity-based private key generator PKG at the base station, and the base station imports public parameters for each node, node identity ID i (can be the MAC address of the node), and the private key s of the node i ; After the initialization is completed, the node performs key agreement through the identity-based lightweight implicit authentication key establishment algorithm TinyIBAK;
[0024] 2) Estab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com