Cluster group calling key distribution method based on asymmetric encryption system
An asymmetric encryption and clustering technology, applied in key distribution, can solve problems such as storage space and index limitations, and achieve the effect of strong confidentiality and enhanced confidentiality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described in detail through specific embodiments below in conjunction with the accompanying drawings.
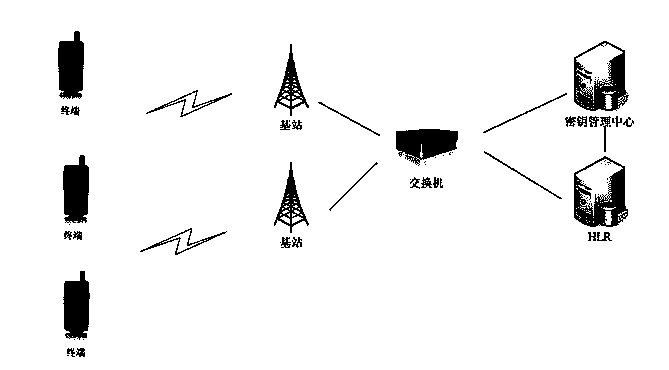
[0018] The network architecture of the wireless trunking communication system corresponding to this embodiment is as follows figure 1 As shown, it includes terminal, base station, switch and key management center. The functions of these components are described as follows:
[0019] Terminal: realizes the terminal function of the wireless trunking communication system network, is the interactive interface for users (not limited to humans, but also machines) to access the system, and provides users with services such as trunking voice.
[0020] Base station: realize the air interface function of the wireless trunking communication system, including the air interface physical layer, MAC layer and network layer functions, and connect users to different business service networks.
[0021] Switch: completes the control and management ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com