Anti-attack method and circuit implementation based on dynamically changing the storage location of intermediate data
An intermediate data, dynamic change technology, applied in encryption devices with shift register/memory, key distribution, can solve the problems of high power consumption, dynamic power consumption, high power consumption, etc., achieve low area cost and resist power consumption attacks , the effect of effective power attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] Below in conjunction with accompanying drawing and specific embodiment, further illustrate the present invention, should be understood that these embodiments are only for illustrating the present invention and are not intended to limit the scope of the present invention, after having read the present invention, those skilled in the art will understand various aspects of the present invention Modifications in equivalent forms all fall within the scope defined by the appended claims of this application.
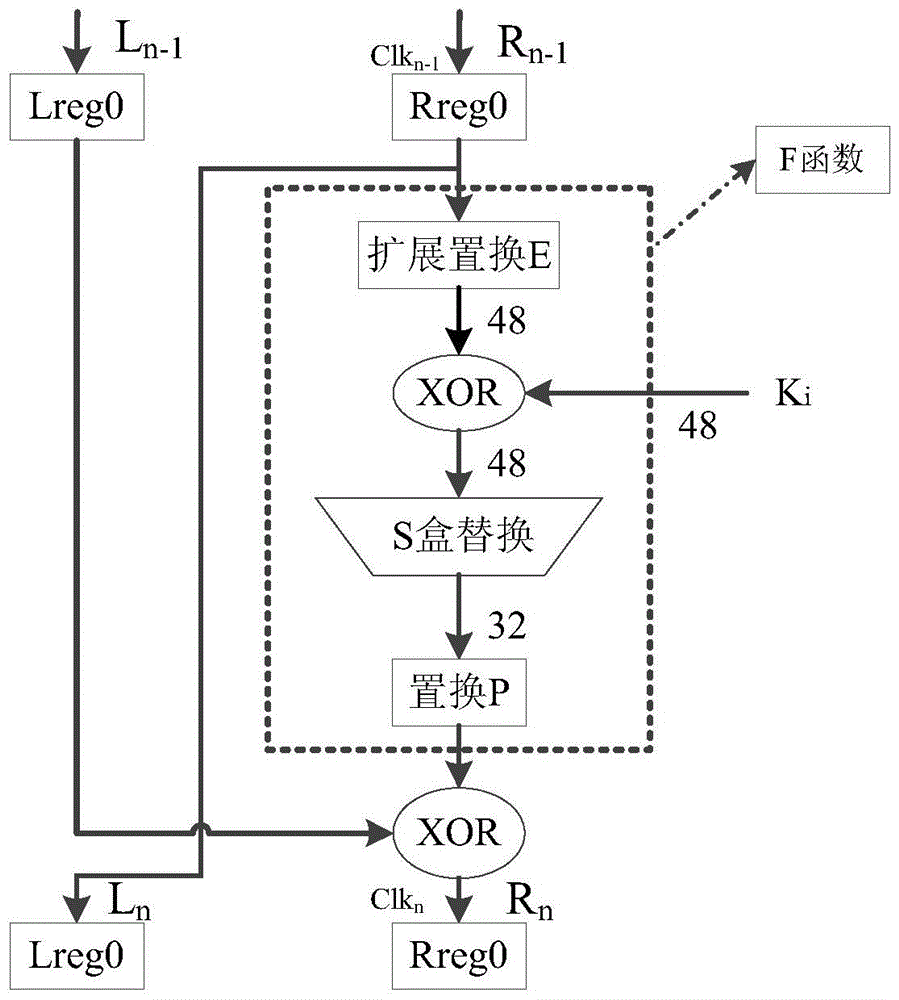
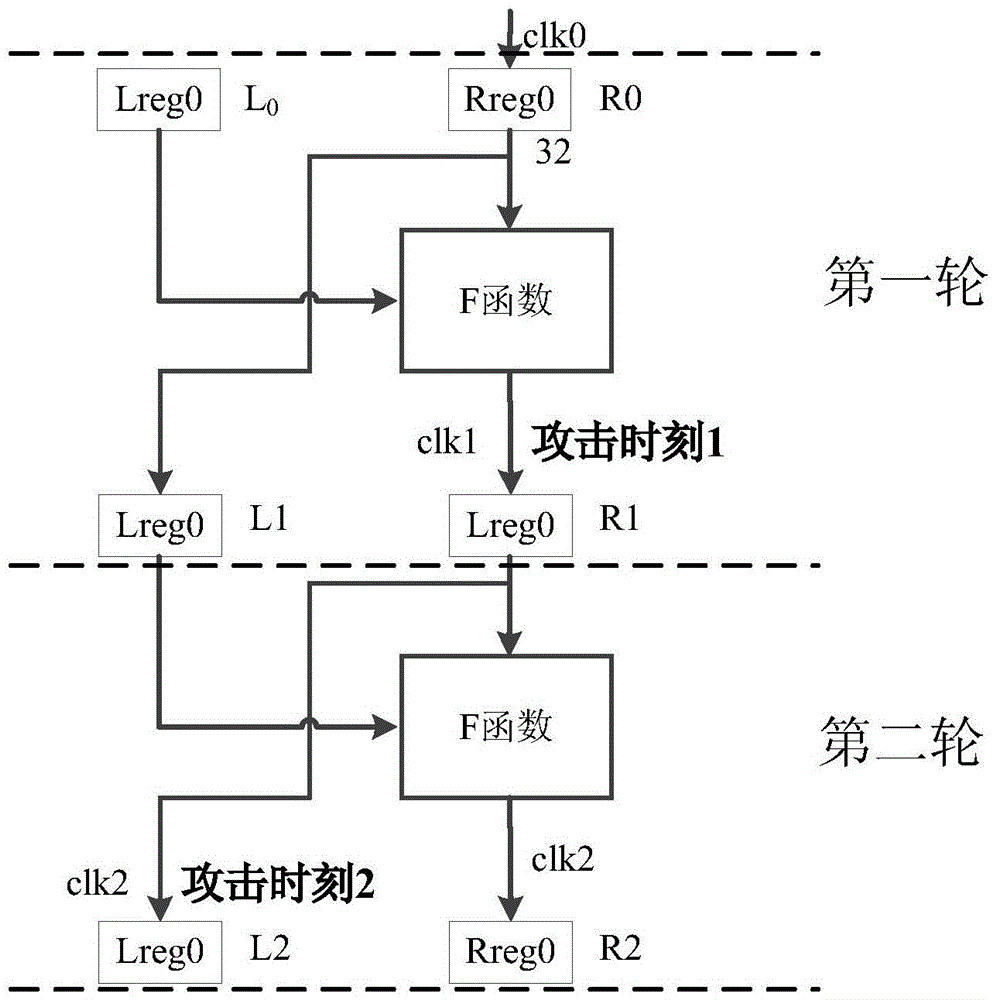
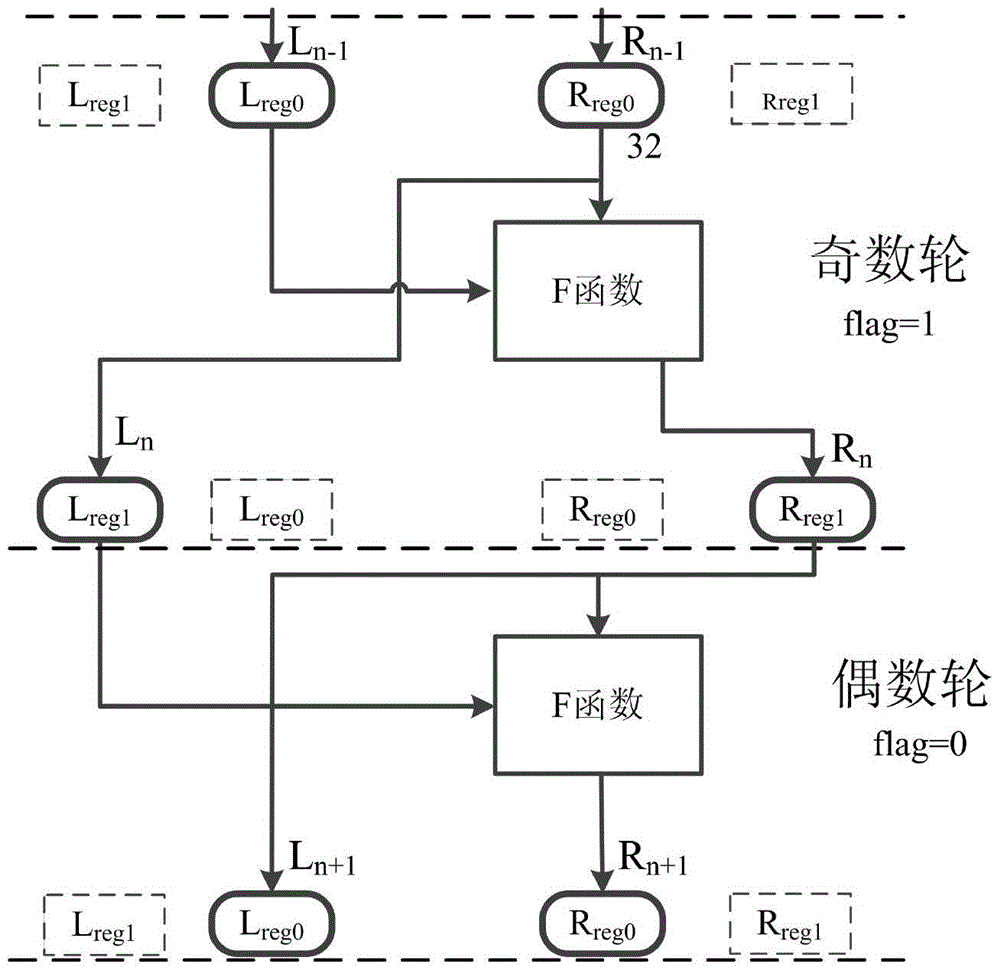
[0051] Such as figure 1 As shown, the encryption process of DES can be divided into three stages:
[0052] 1. The 64-bit plaintext realizes the bit rearrangement of the plaintext through the initial replacement of the IP, and at the same time divides the 64-bit plaintext into L 0 and R 0 two parts. L 0 is the first 32 bits of plaintext after bit rearrangement, R 0 It is the last 32 bits of plaintext.
[0053] 2. Perform 16 rounds of iterative operations. The 16 ite...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com