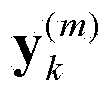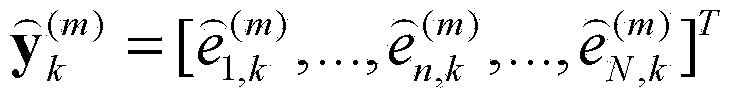Steady GNSS anti-spoofing method based on particle filter
A particle filtering and anti-spoofing technology, applied in radio wave measurement systems, satellite radio beacon positioning systems, measurement devices, etc., can solve the problem of pseudo-range information misleading receivers, large deviations in positioning results, inability to resist forwarding spoofing and anti-spoofing. cheating etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0046] Specific Embodiment 1: A particle filter-based robust GNSS anti-spoofing method in this embodiment is specifically prepared according to the following steps:
[0047] Step 1. Complete the initialization of the two variables. First, determine the initial state of the user, and evenly distribute m initial state vector particles in the field of the initial state of the user evenly distributed over x 0 In the field; at the same time, set the count value of the number of iterations to k=1; according to the user's initial state vector particle The user state vector particle at k=1 can be obtained
[0048] x 1 ( m ) = x 0 ( m ) + v 1 ( m ) + f ...
specific Embodiment approach 2
[0082] Specific implementation mode two: the difference between this implementation mode and specific implementation mode one is: in step three, according to the calculation of step two Calculate the observed pseudorange between the user and the nth satellite is given by:
[0083] (1) Through the user's state vector particle at the kth moment Calculate the observed pseudorange
[0084]
[0085] Among them, (x n,k ,y n,k ,z n,k )(n=1,2,...,N) represents the position coordinates of the nth satellite at the k moment; (x U,k ,y U,k ,z U,k ,δt U,k ) represents the user’s state vector particle at the kth moment The state of , including the user's state vector particle at the kth moment 3D position (x U,k ,y U,k ,z U,k ) and the clock bias δt relative to the nth satellite U,k ;
[0086] (2) True pseudorange ρ n,k It is directly measured by the pseudorange measurement circuit of the receiver, assuming that the number of visible satellites is N, and the influe...
specific Embodiment approach 3
[0089] Specific implementation mode three: the difference between this implementation mode and specific implementation mode one or two is that in step five, according to the update observation vector Calculate unnormalized particle weights The process is:
[0090] (1) Establish a discrete-time particle filter model as:
[0091] x k ( m ) = x ( m ) k - 1 + v ( m ) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com