Safe data transmission method and LTE access network system
A transmission method and data security technology, applied in the field of mobile communications, can solve problems such as limited macro network coordination and interaction, inability to meet the business needs of large data volume and high mobility, and achieve security performance, reliable joint transmission services, and ease The effect of the message payload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
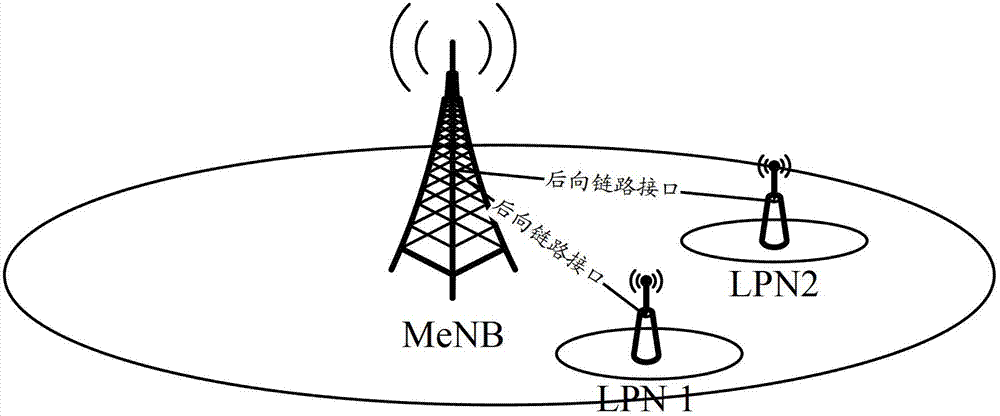
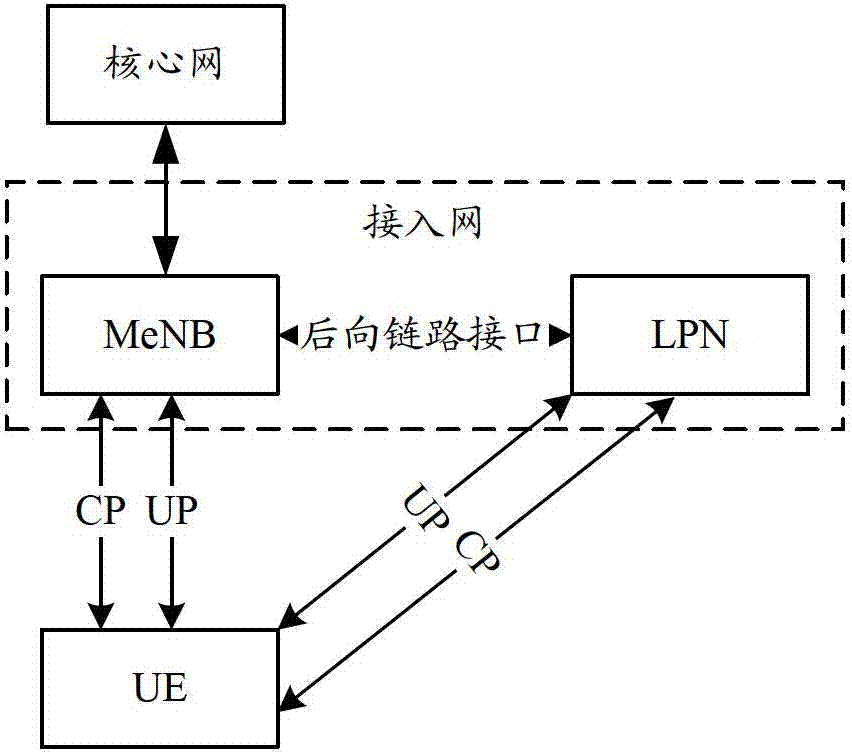
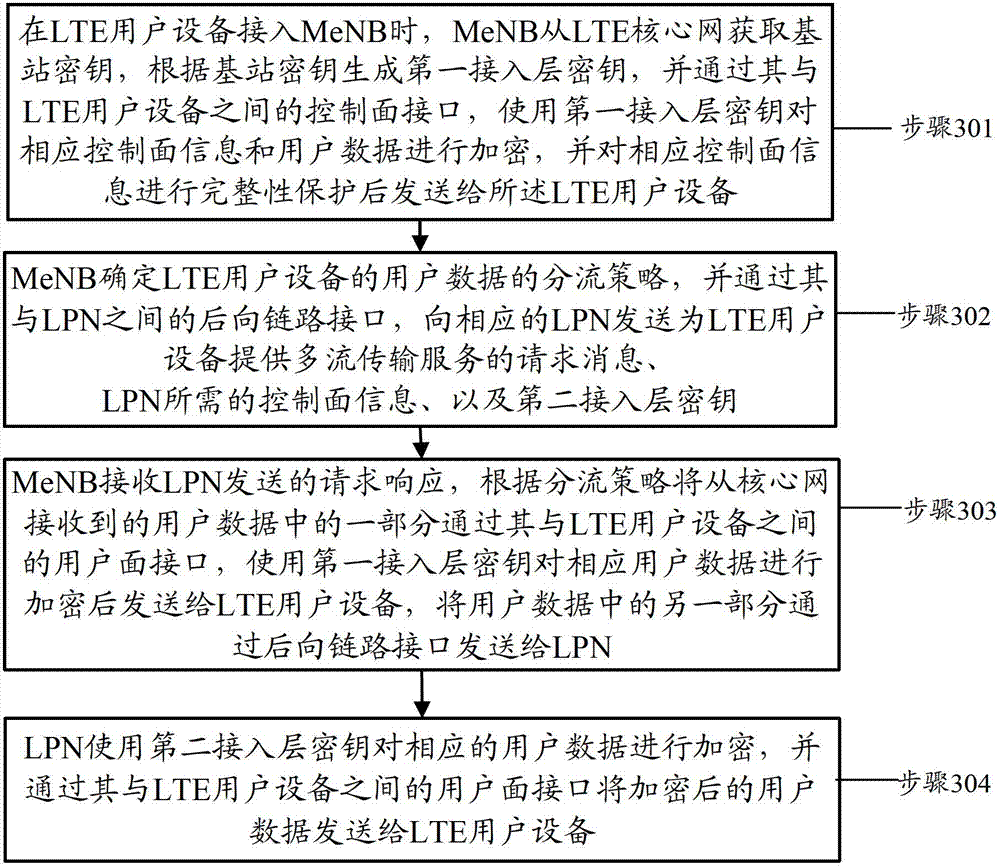
[0065] Example 1: MeNB and LPN are deployed in the network, these two nodes constitute the access network of the system architecture of the present invention, and the LPN undertakes the transmission of offloaded data. During the preparation process for the network side to decide to provide the cross-base station multi-stream joint transmission service for the UE, the MeNB transmits the AS Key to the LPN so that it can perform security protection functions. Image 6 is a signaling flow chart of Example 1 of the embodiment of the present invention, such as Image 6 As shown, it specifically includes the following processing:
[0066] Step 1: The UE accesses the macro cell established by the MeNB according to the existing LTE process, and establishes a CP connection (RRC Connection) that can transmit control plane information and an UP connection that can transmit user data. MeNB obtains KeNB from the core network, derives AS Key (including UP Key and RRC Key) based on this, and...
example 2
[0073] Example 2: The deployment scenario is the same as that of Example 1. When the MeNB and the LPN provide joint transmission services for the UE, if the MeNB side updates the key, it needs to notify the LPN of the updated key so that it can effectively perform the security protection function. Figure 7 It is the signaling flowchart of Example 2 of the embodiment of the present invention, such as Figure 7 As shown, it specifically includes the following processing:
[0074] Step 1. In the system architecture of the embodiment of the present invention, wireless connections are respectively established between the UE, the MeNB and the LPN, so as to obtain a cross-base station multi-stream joint transmission service. There are CP and UP connections between UE and MeNB in the same existing technology; this example takes only UP connection between UE and LPN as an example, the data transmitted between LPN pair and UE is based on the UP Key (KUPenc) obtained from MeNB and A...
example 3
[0081] Example 3: The deployment scenario is the same as that of Example 1. In the architecture where the MeNB and the LPN provide the cross-base station multi-stream joint transmission service for the UE, this embodiment takes the establishment of CP and UP connections between the LPN and the UE as an example. During the preparation process of the multi-stream service or when there is a key update requirement on the network side, the MeNB needs to transmit the ASKey to the LPN so that it can perform security protection functions. Figure 8It is the signaling flowchart of Example 3 of the embodiment of the present invention, such as Figure 8 As shown, it specifically includes the following processing:
[0082] Step 1. When the MeNB decides to provide cross-base station multi-stream transmission services for UEs accessing its cell, it transmits the necessary UE context and other information to the LPN through the Backhaul interface, such as carried in the "bearer establishmen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com