Hardware-Trojan-resisting circuit design method based on activation probability analysis
A probabilistic analysis and hardware Trojan horse technology, applied in the direction of measuring electricity, measuring electrical variables, instruments, etc., can solve the problems of strong concealment and harmfulness of Trojan horse circuits, and achieve enhanced resistance, enhanced protection, and low hardware overhead Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
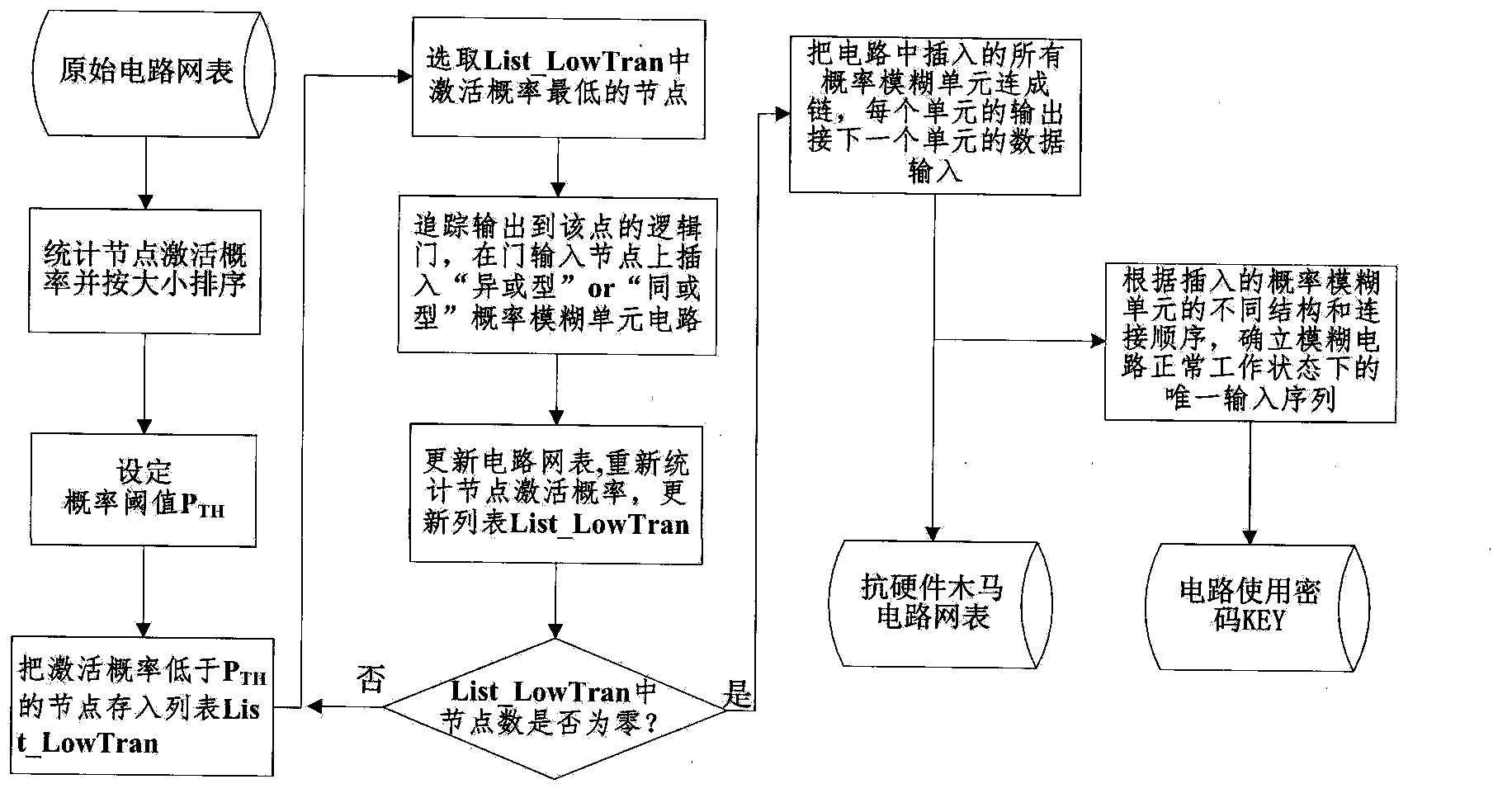
[0030] The anti-hardware Trojan horse circuit design method based on activation probability analysis proposed by the present invention will be described in detail in conjunction with the accompanying drawings and embodiments below.
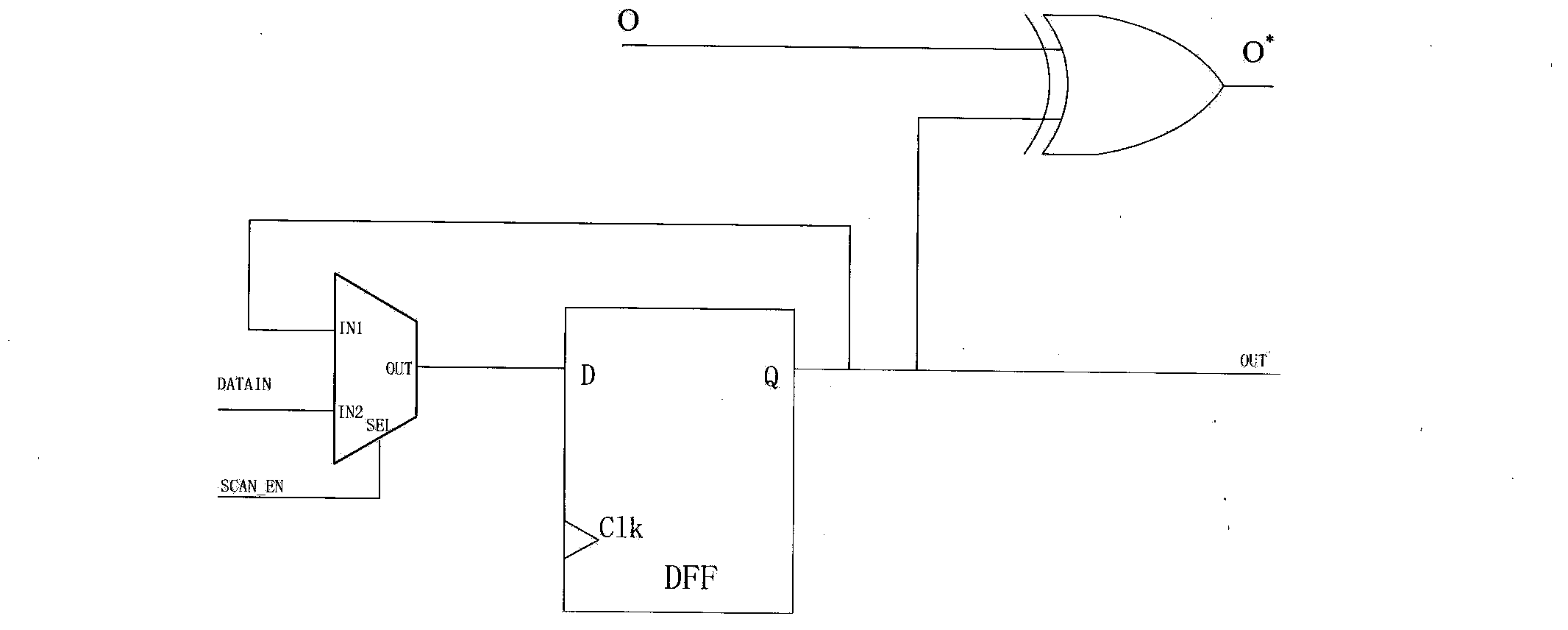
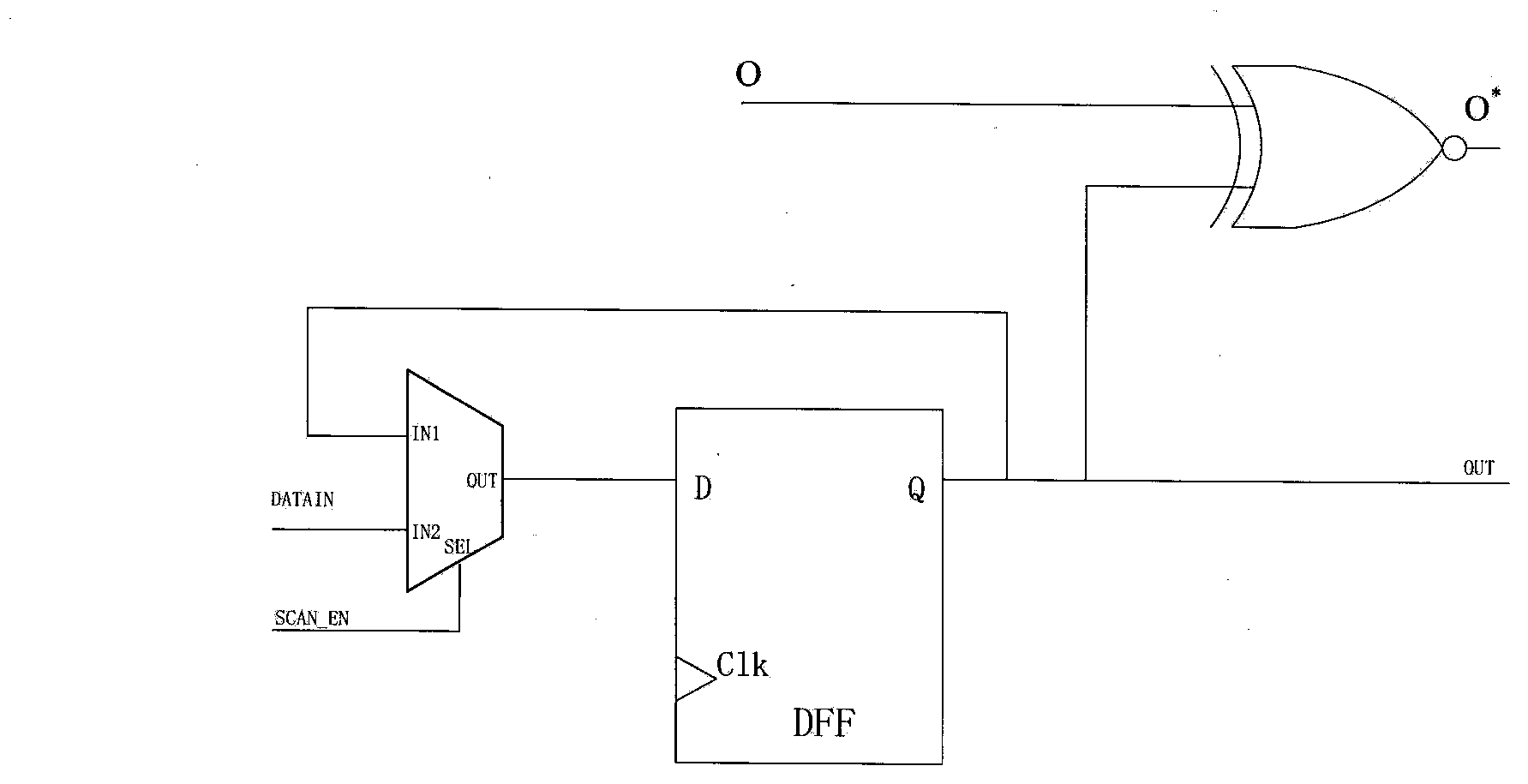
[0031] The present invention provides a circuit module capable of changing the jump probability of circuit nodes—probabilistic fuzzy unit, which is divided into two structures of exclusive-or type and same-or type, such as figure 2 and image 3 .
[0032] In order to make the implanted hardware Trojan escape the conventional test, the malicious party will choose a node with a low activation probability in the circuit to implant the hardware Trojan. The probabilistic fuzzy unit was invented based on the design psychology of the malicious party, and its function is to interfere with the judgment of the activation probability of the circuit node by a third party who is not authorized to use the circuit. here to Figure 7 The circuit in is taken a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com