FPGA-based hard disk encryption and decryption system
A hard disk encryption and hard disk technology, applied in the electronic field, can solve the problems of complex peripheral circuits, key generation methods and authentication methods with low security, and achieve the effect of simplifying peripheral circuits and reducing volume
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
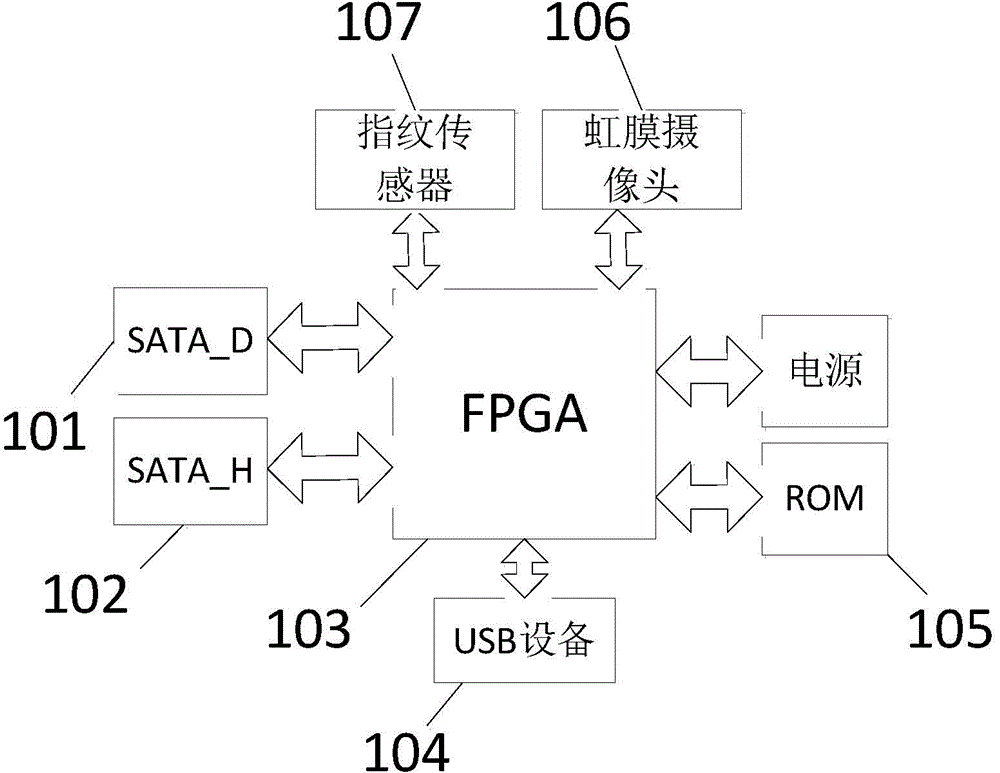
[0070] Such as figure 1 with 2 Shown, a kind of hard disk encryption system based on FPGA, is used for encrypting the data that obtains from host computer (computer), and the data after encrypting is stored in hard disk, comprises FPGA and authentication input module, and FPGA comprises processor, key Decryption circuit and data encryption circuit. The key decryption circuit and data encryption circuit are described by IP core or HDL hardware programming language; the FPGA-based hard disk encryption system can also include a read-only memory ROM for storing data or algorithms related to system work. The processor can be a high-performance ARM processor. The main responsibilities of the ARM processor are two: one is to play a master role, coordinate the work of the entire system, and make the system perform at its maximum performance; the other is to use it for system certification.
[0071] The authentication input module is used to receive the user's input authentication; ...
Embodiment 2
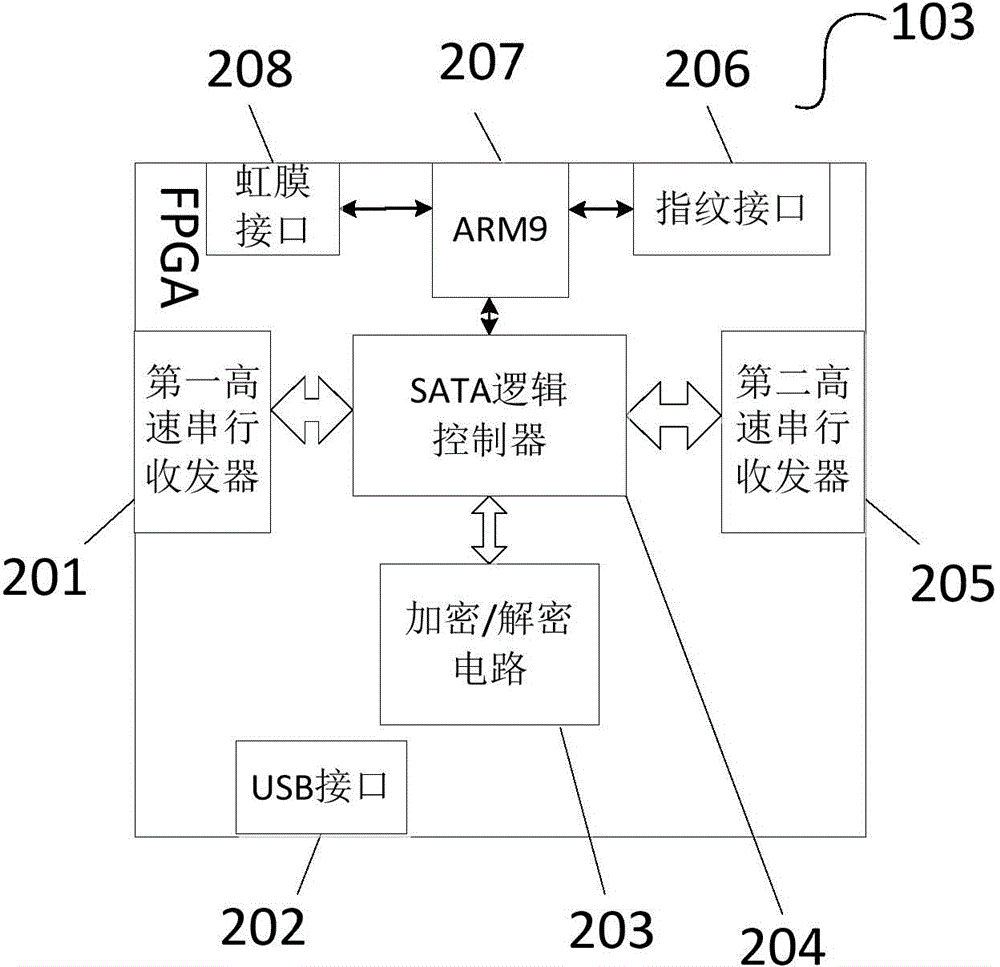
[0099] With the rapid development of technology in the information age and the rapid update of electronic products, encryption and decryption algorithms, fingerprint recognition and other software need to be constantly updated to meet new needs and challenges, so as to obtain the highest security, so the encryption and decryption system also needs to be updated in real time. The system also includes a system update module, which is also integrated in the FPGA chip 103 for implementation. The latest firmware can be updated through the system update module without replacing the entire hardware system, which greatly saves costs. In one embodiment of the present invention, the system update module adopts the USB interface 202, and the USB interface 202 is used for firmware update of the whole system. This interface also does not need a dedicated USB interface chip, there are abundant logic resources in the FPGA, and the application of HDL hardware programming language can completel...
Embodiment 3
[0107] The embodiment of the present invention also provides an FPGA-based solid-state disk encryption and decryption method, which is used to encrypt and decrypt the data transmitted between the host and the hard disk. The authentication, data exchange, and encryption and decryption involved in the system are all integrated in one FPGA. It is completed on the chip, and each module is described by IP core or HDL hardware programming language. details as follows:
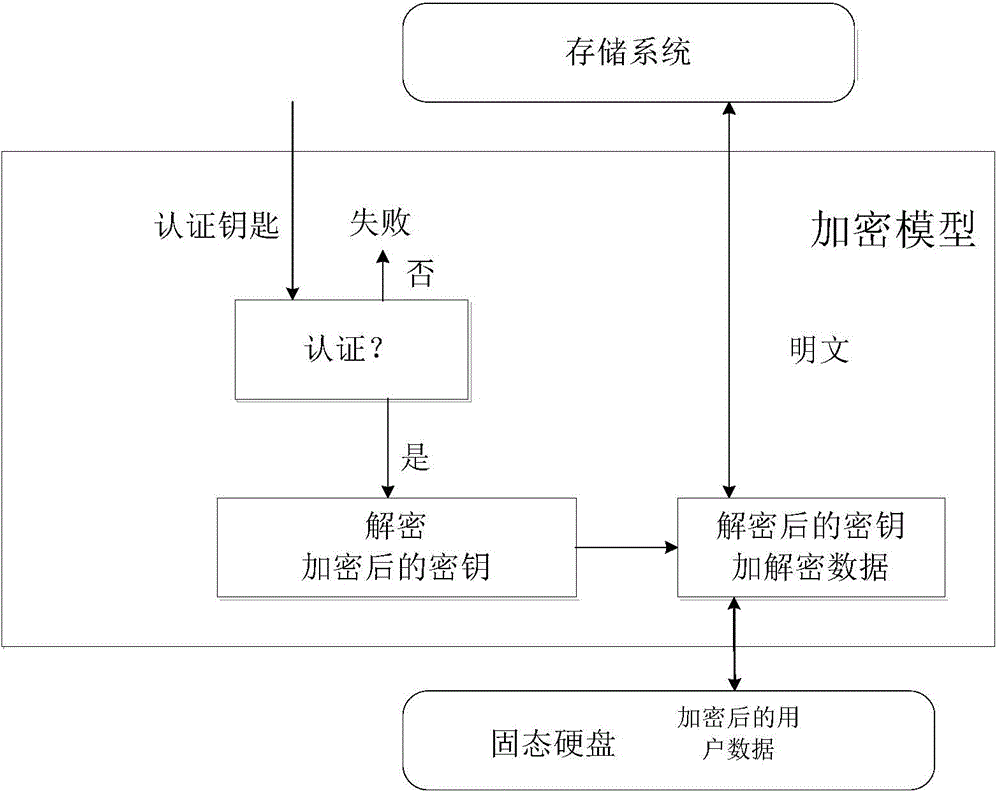
[0108] S101. Authentication, performing authority authentication on the user, and if the authority authentication is passed, the decryption key is used for encryption and decryption;
[0109] If the authentication is passed, the Encrypted Encryption Key (encrypted key) in the system is decrypted; if the authentication fails, the system cannot work normally. Once the Encrypted Encryption Key is decrypted to Clear Encryption Key (the key in the decrypted state), the key can be used in this system to perform normal enc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com