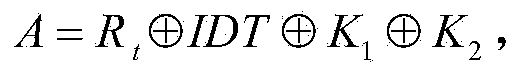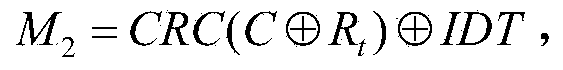RFID lightweight-class bidirectional authentication method based on CRC coding
A two-way authentication, lightweight technology, applied in the field of radio frequency identification, can solve the problem of easily exceeding the limit of label resources, and achieve the effect of reducing encryption complexity and improving security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
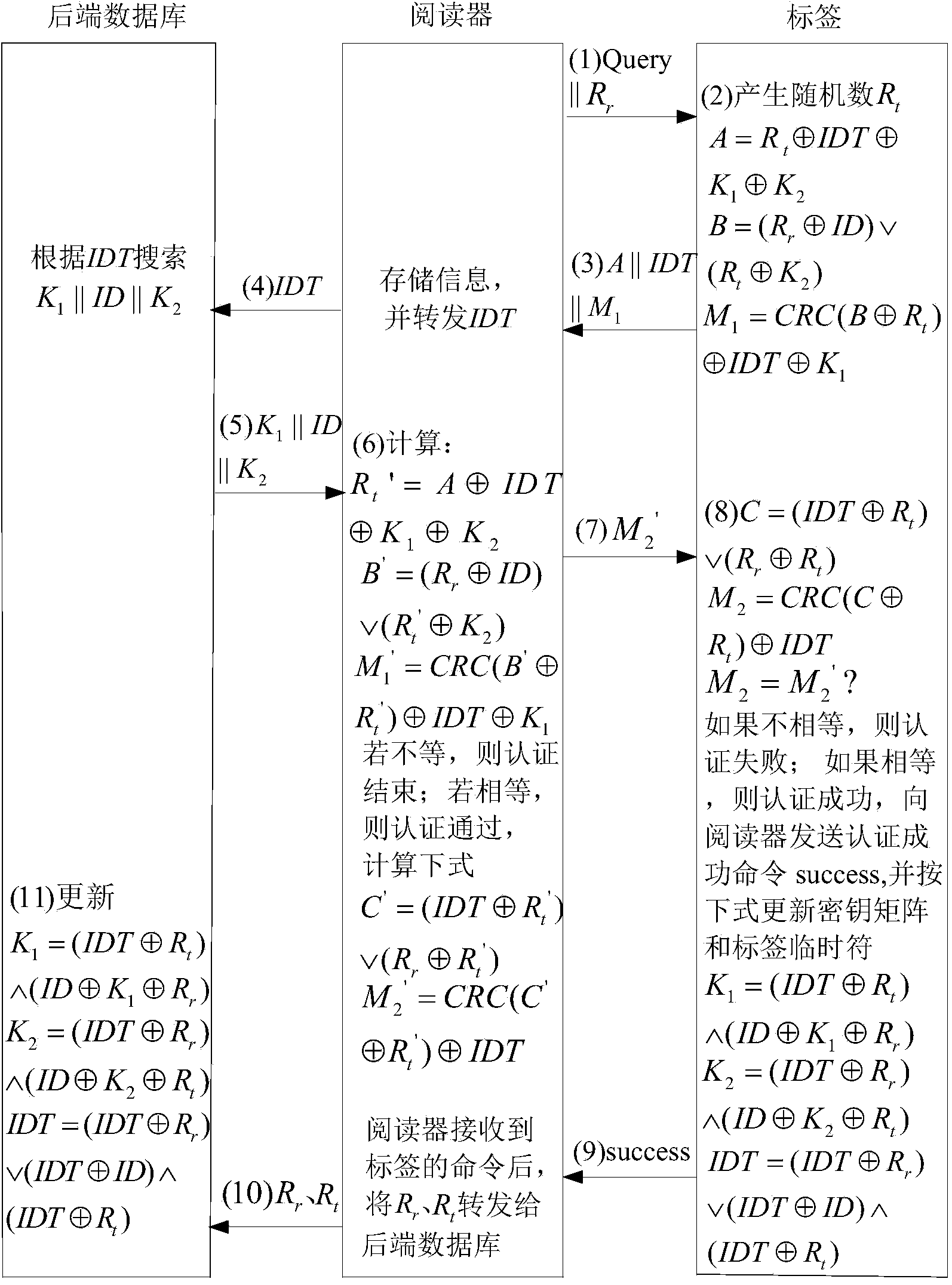
[0047] The protocol of the present invention includes three stages of system initialization, mutual authentication, and key information update. The specific interaction process between the background database, reader, and tag in the protocol is described as follows:
[0048] 1. RFID system initialization
[0049] When the RFID system is initialized, the server or manufacturer assigns each tag a globally unique identity code ID with a length of 64 bits, and a 64-bit tag temporary identifier IDT that replaces its operation in order to ensure the confidentiality of the ID. And a key matrix K with 1 row and 64 columns 1 、K 2 . At the same time, record the tag's unique identification code ID and its IDT in one-to-one correspondence with the shared key matrix K in the back-end database 1 、K 2 , and then attach the label to the object to be identified.
[0050] 2. System certification process
[0051] RFID system security certification process such as figure 1 As shown, the st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com