Design method of integrated circuit and hardware trojan detection method
A technology of integrated circuits and design methods, which is applied in computing, electrical digital data processing, special data processing applications, etc., and can solve problems such as inability to locate hardware Trojan horses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be described in further detail below in conjunction with the embodiments and accompanying drawings, but the embodiments of the present invention are not limited thereto.
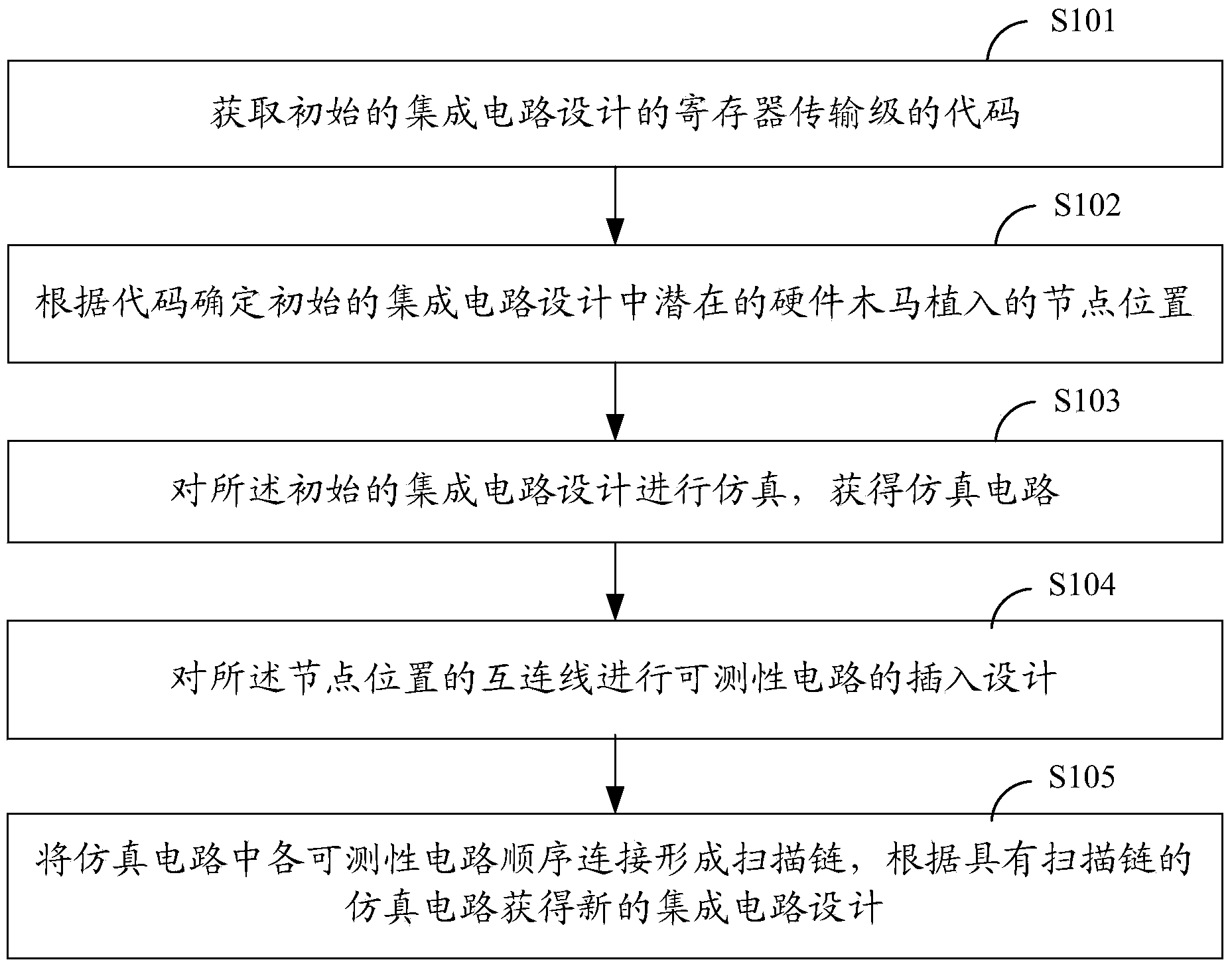
[0024] Such as figure 1 As shown, it is a schematic flow diagram of an embodiment of the design method of the integrated circuit of the present invention, including steps:
[0025] Step S101: Obtain the register transfer level code of the initial integrated circuit design;
[0026] The register transfer level (RTL) code is obtained from the original integrated circuit design, which is generally described in VerilogHDL or VHDL language.
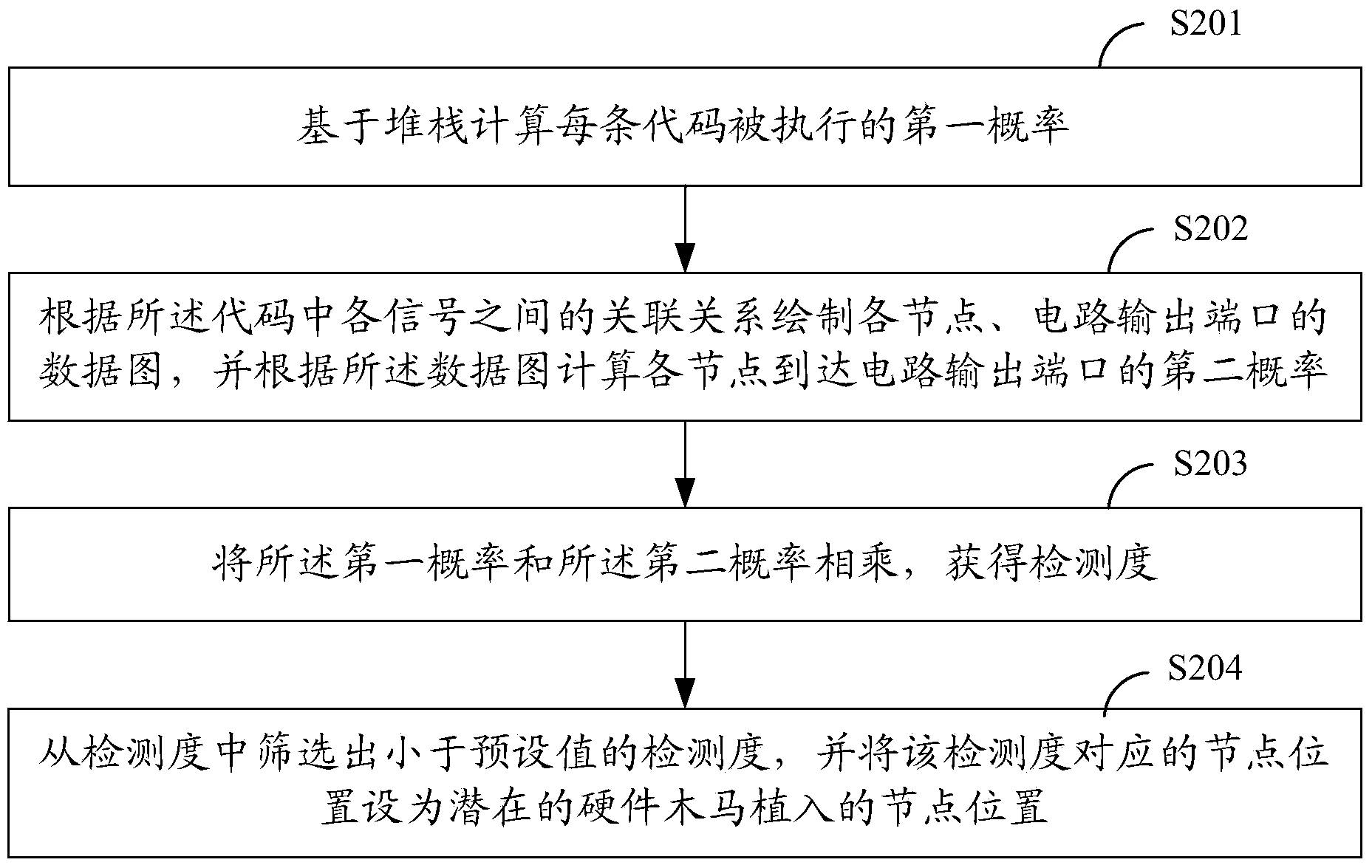
[0027] Step S102: Determine the node positions of potential hardware Trojan implants in the initial integrated circuit design according to the code;
[0028] In order to achieve a concealed effect, hardware Trojans often use nodes with very low activity inside the circuit as their trigger conditions, making it difficult to be activated and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com