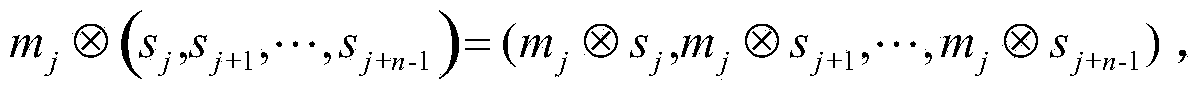Efficient generic Hash function authentication scheme suitable for quantum cryptography system
A quantum cryptography and scheme technology, which is applied in user identity/authority verification and key distribution, can solve the problems of large number of keys, reduced security, and low implementation efficiency, and achieves low resource consumption, guaranteed security, and novel design methods Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings.
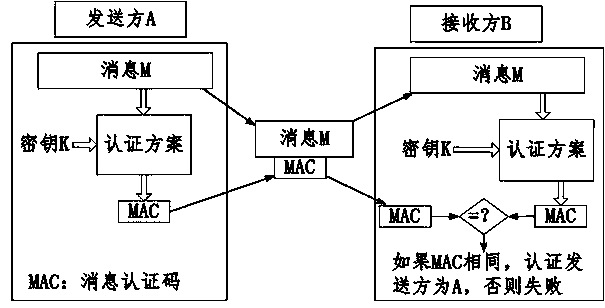
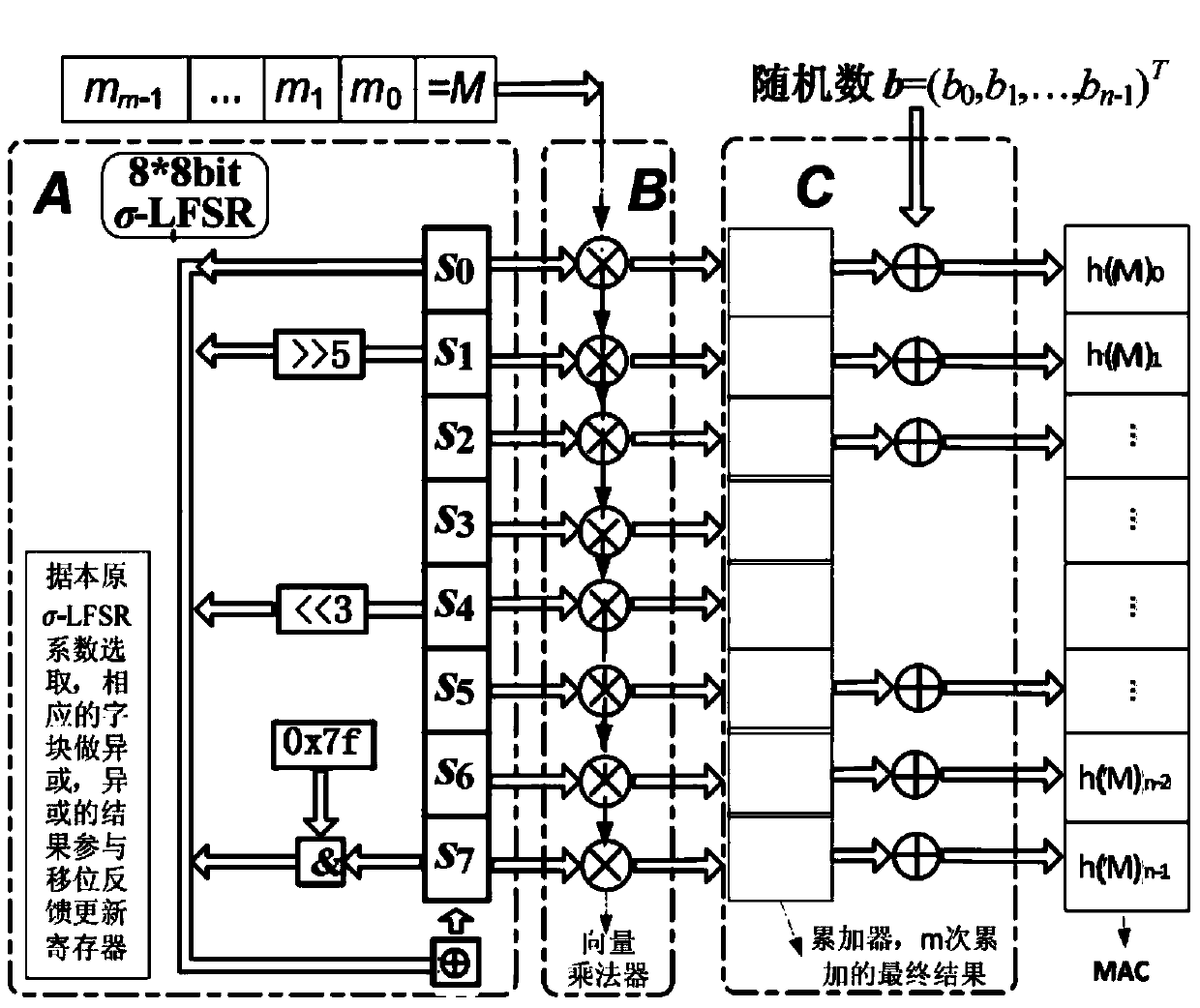
[0039] The present invention is an identity authentication scheme. The scheme adopts a word-based design method. After the scheme completes the initialization of the shared key and the word linear feedback shift register, the authentication message is converted to Carry out vector multiplication with the register state in turn, and accumulate through the accumulator, and finally XOR with the random number to obtain the message authentication code, and then send the authentication message and the message authentication code to the other party to achieve the function of identity authentication.
[0040] Describe technical scheme of the present invention in detail below
[0041] 1. The overall framework of the program
[0042] The overall framework of the program is divided into three parts:
[0043]Component A: a word-based σ-linear feedback ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com