Universal safe intelligent terminal starting method
A smart terminal and security boot technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the security threats of smart mobile terminals and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
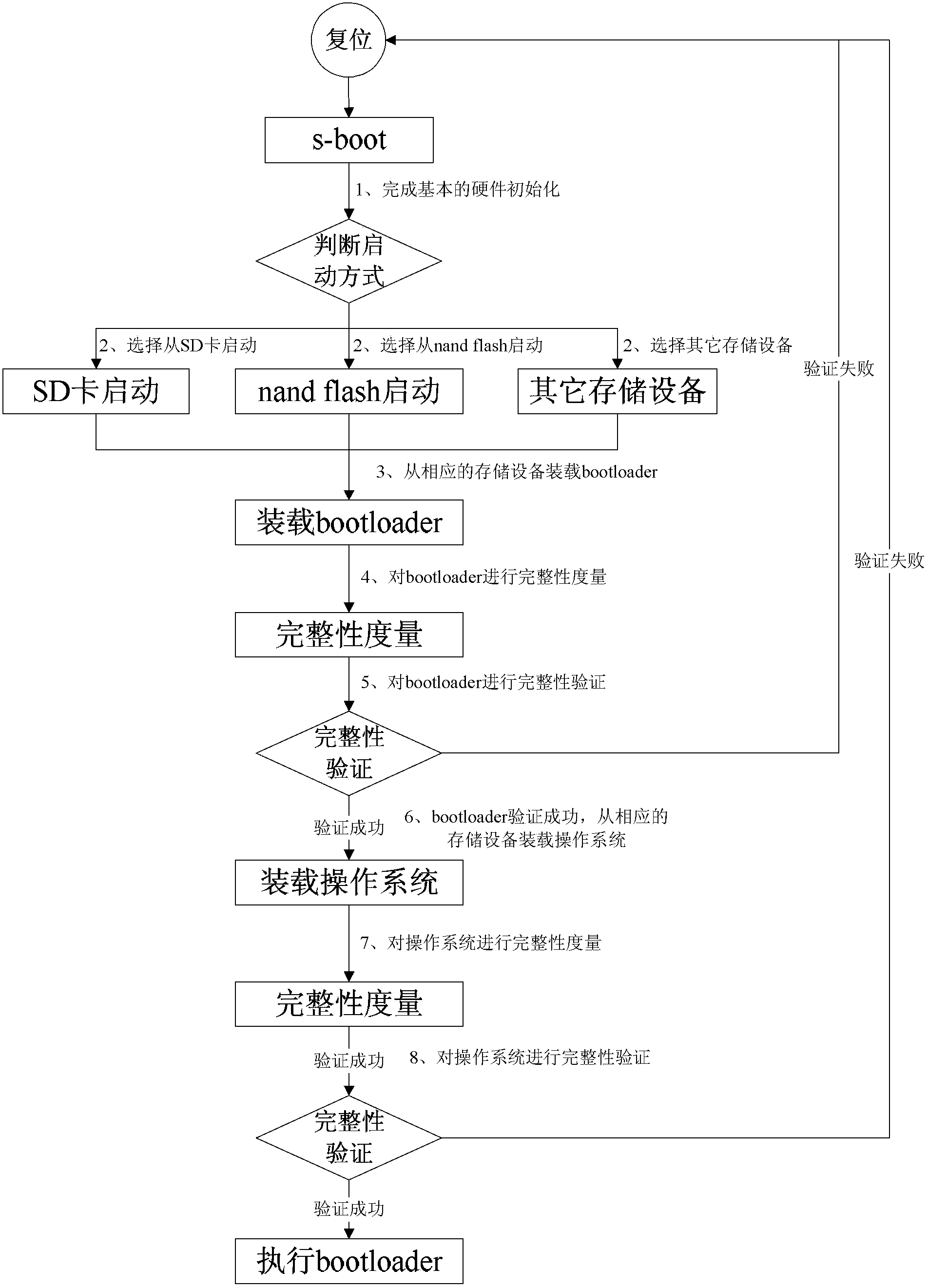
[0026] The following will further describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. It should be understood that the described embodiments are only some of the embodiments of the present invention, not all of them. Based on the embodiments of the present invention, all other embodiments obtained by those skilled in the art without making creative efforts belong to the protection scope of the present invention.
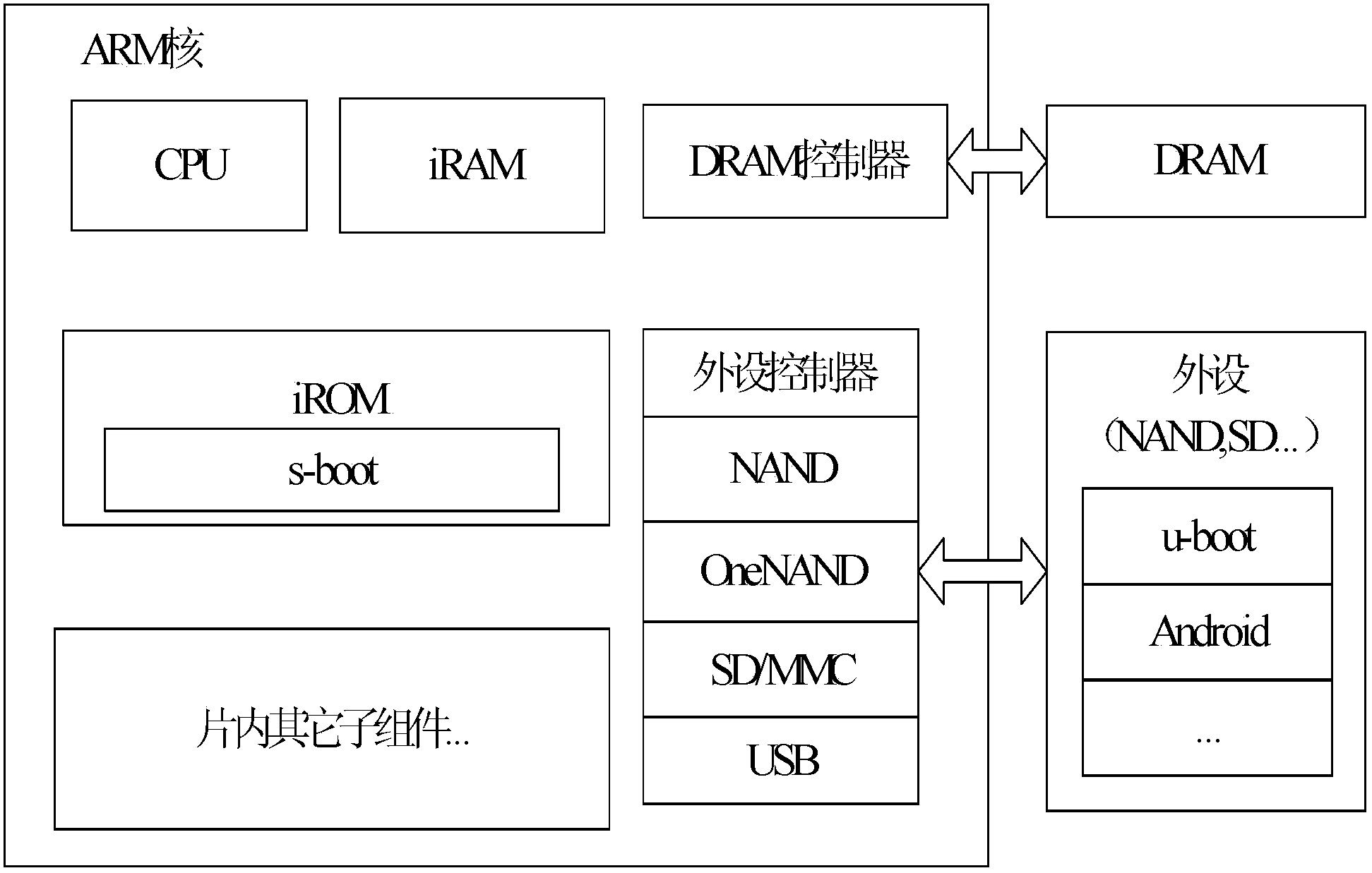
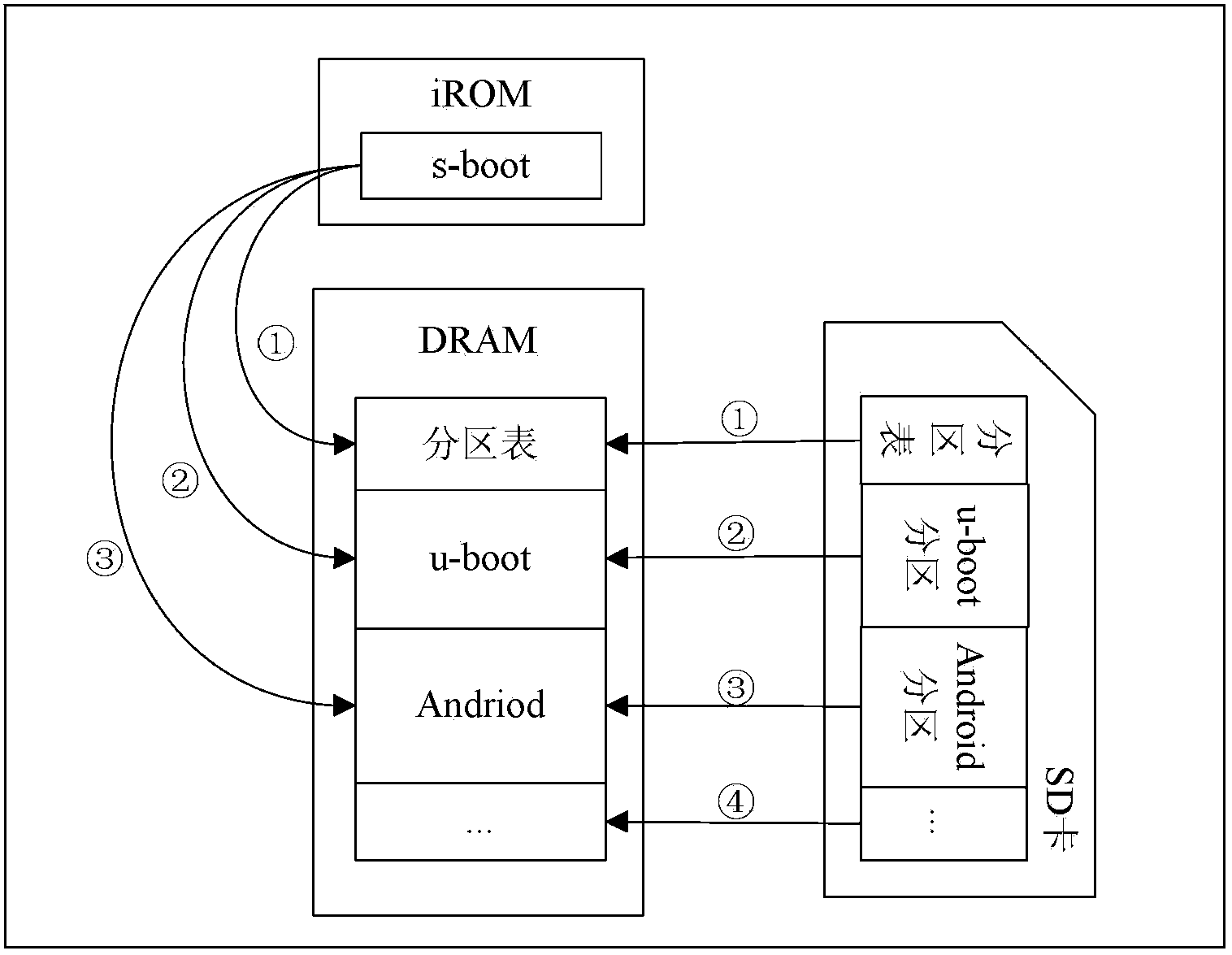
[0027] The system architecture of the embodiment provided by this patent application is as figure 2 As shown, the on-chip ROM, that is, iROM contains the secure boot module s-boot. The s-boot is stored in the iROM in a one-time burning method, which can ensure that the s-boot is not tampered with by malicious programs and maintains its integrity. On-chip RAM, namely iRAM, is a small-capacity static RAM. DRAM and external storage devices (such as nand f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com