Near field communication authentication method based on U/SIM card authentication response and time-limited feedback
An authentication response and near-field communication technology, which is applied in wireless communication, near-field transmission system, protocol authorization, etc., can solve the problem that the security of near-field communication cannot be guaranteed, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
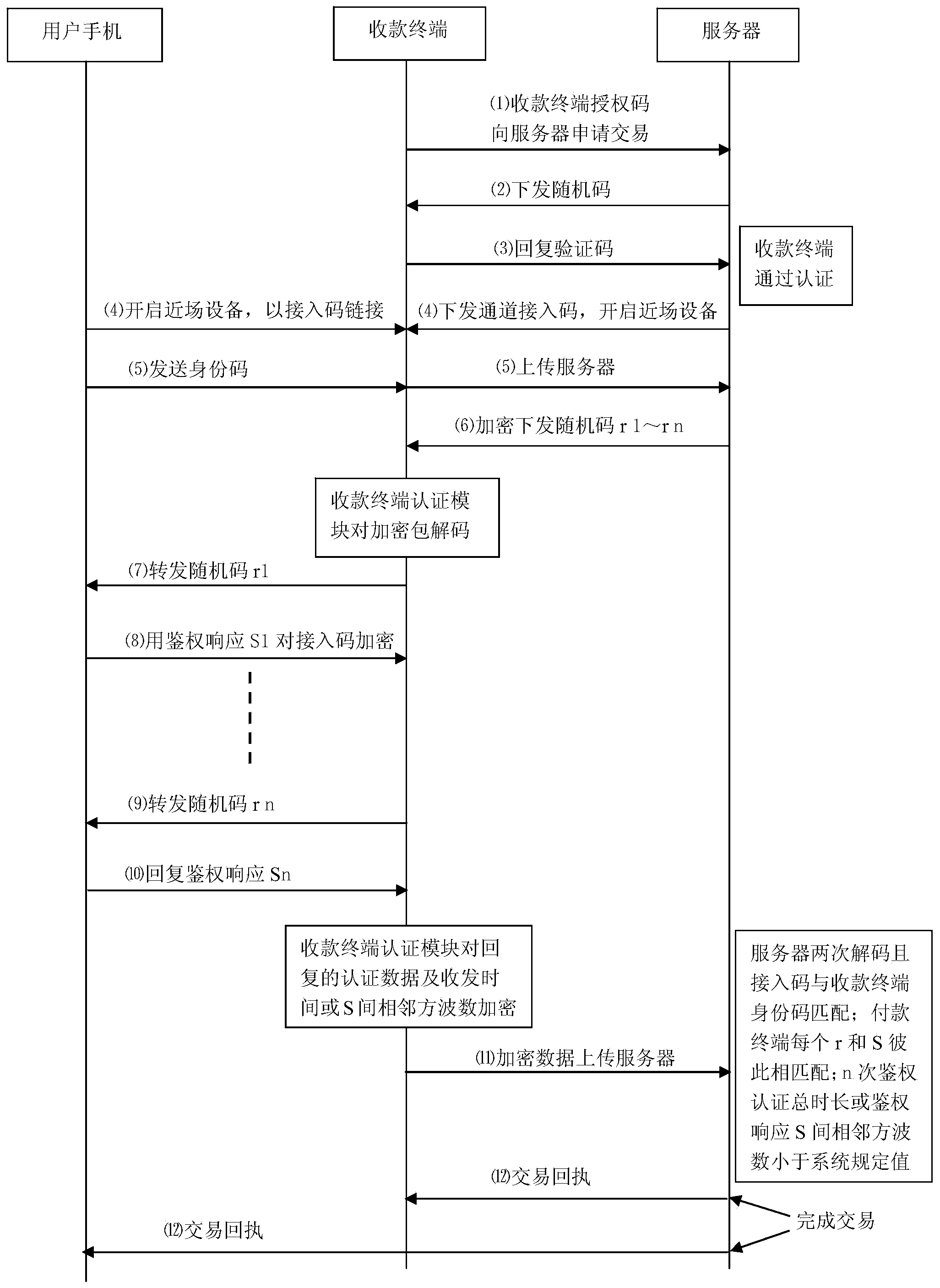
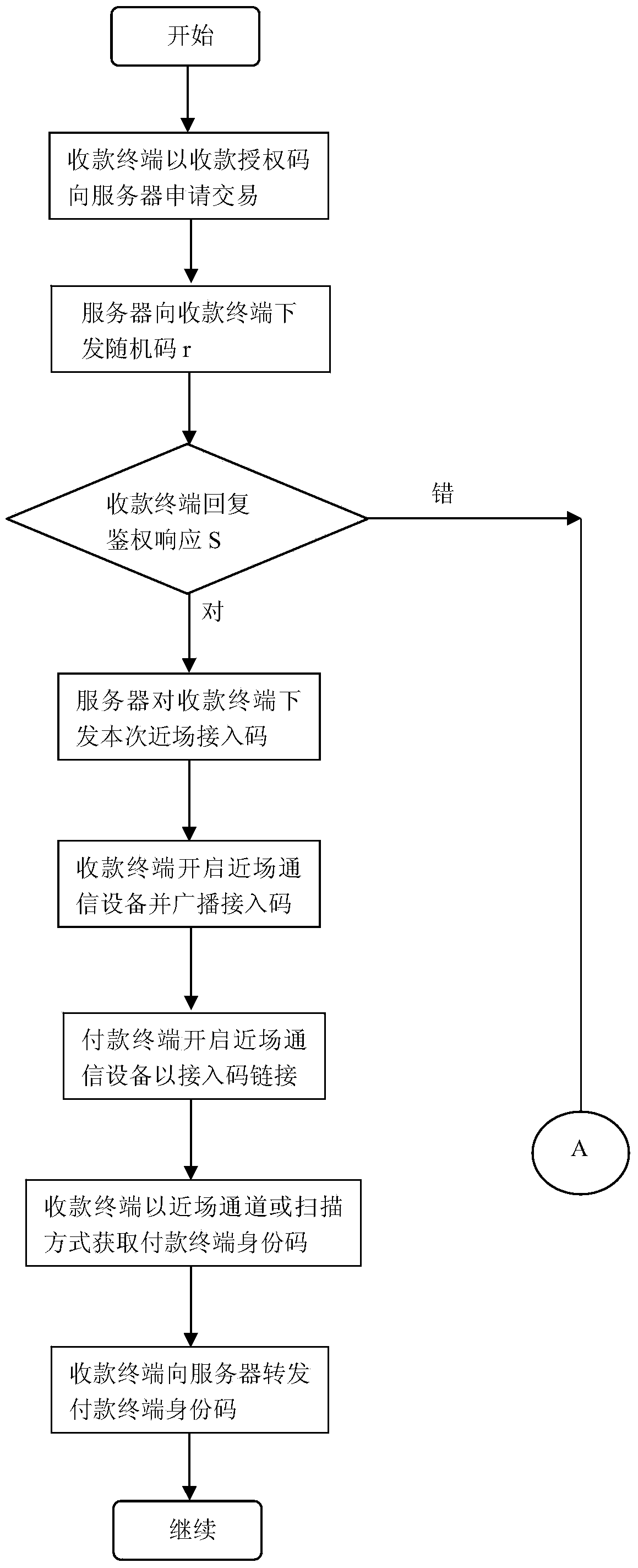
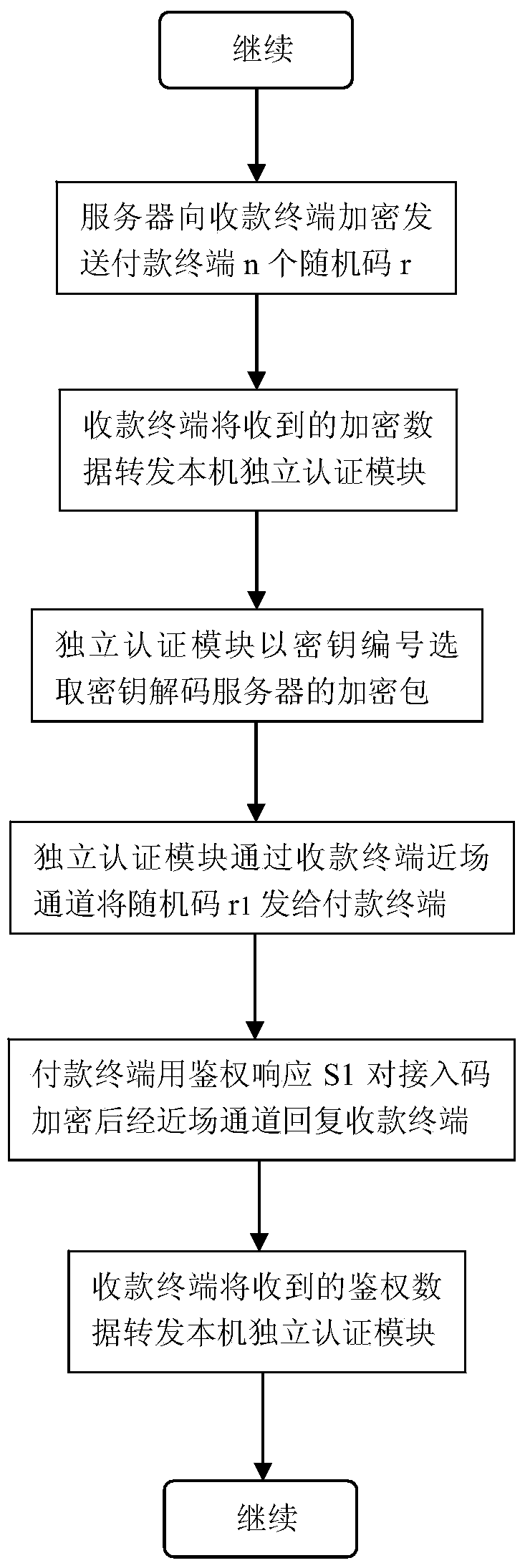
[0067] This type of collection terminal is distributed to merchants after passing the inspection by banks or financial institutions. Merchants need to pass the audit to obtain the transaction port and transaction authorization code. The special collection terminal is an independent communication terminal with built-in independent clock, CPU processor and communication transceiver module, and its external communication interface has wired broadband and mobile wireless air interface. The random code and its verification code used only to verify the identity or qualification of the payment terminal are pre-solidified in the special collection terminal, as well as the encryption key, key number and encryption algorithm used in the transaction authentication link. The database corresponding to the terminal authorization code also contains random codes and verification codes, as well as encryption keys, key numbers, and encryption algorithms. A square wave generator that responds to...
Embodiment 2
[0072] When a mobile terminal is used as a collection terminal, its transaction port still needs to be provided by the payment provider after review. As mentioned above, due to the complex communication environment of the mobile phone terminal, the round-trip time with the server is uncertain, so the hacker terminal can use this point to collude with the receiving user to delay the reply time to the server synchronously to create the illusion of network delay. Its purpose is to gain valuable time for the hacker terminal to obtain the U / SIM card authentication response S from the virus terminal in the remote user. For this reason, it is necessary to add a separate independent hardware authentication module that has nothing to do with the mobile communication system, or a USB / earphone hole plug-in / plug-in on the U / SIM or SD card or card sticker of the mobile payment terminal to accurately define and protect The sending and receiving time node of authentication data. The hardwar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com