Secure data storage method and secure data read method based on distributed system infrastructure
A technology for safe data storage and distributed system, applied in the field of cryptography, it can solve the problems of difficult key management, slow encryption and decryption, and inappropriate encryption and decryption, so as to ensure integrity and confidentiality, convenient use and management, Password change convenient effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
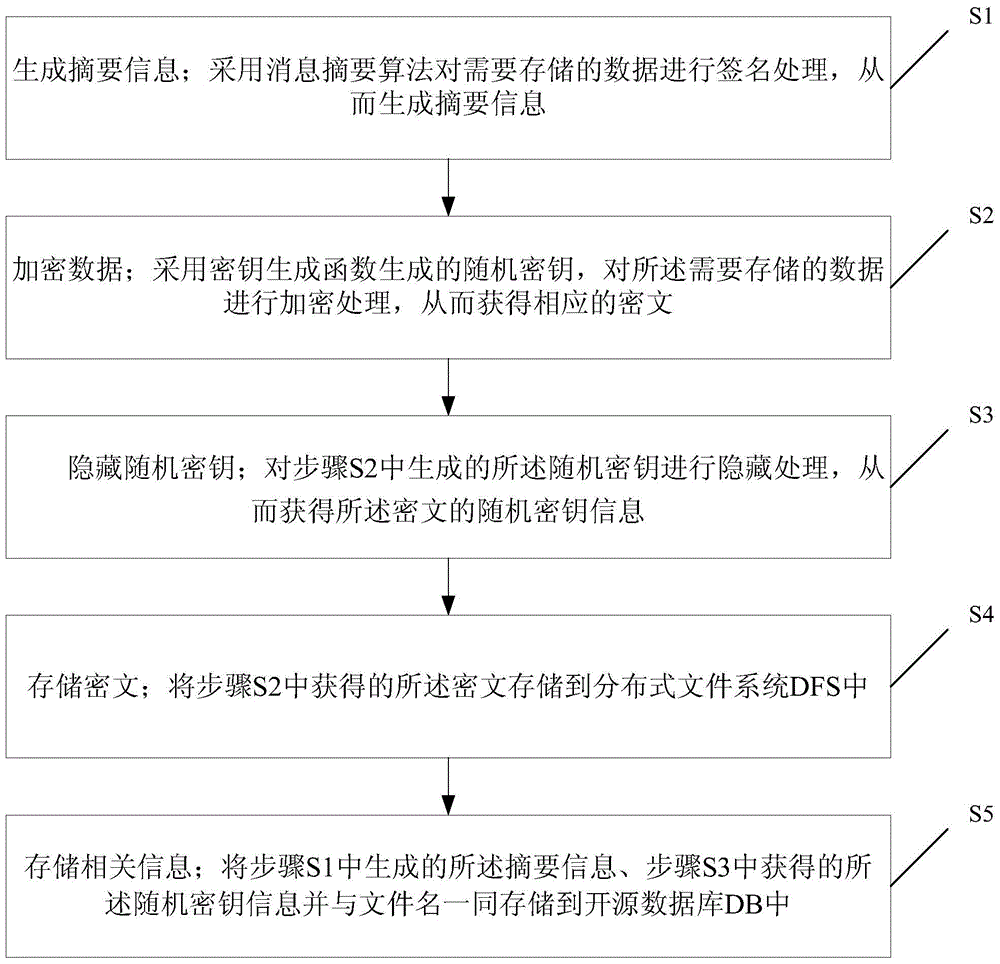
[0054] see figure 1 , is a flow chart of a data security storage method based on a distributed system infrastructure provided by an embodiment of the present invention. The data security storage method based on the distributed system infrastructure includes steps:
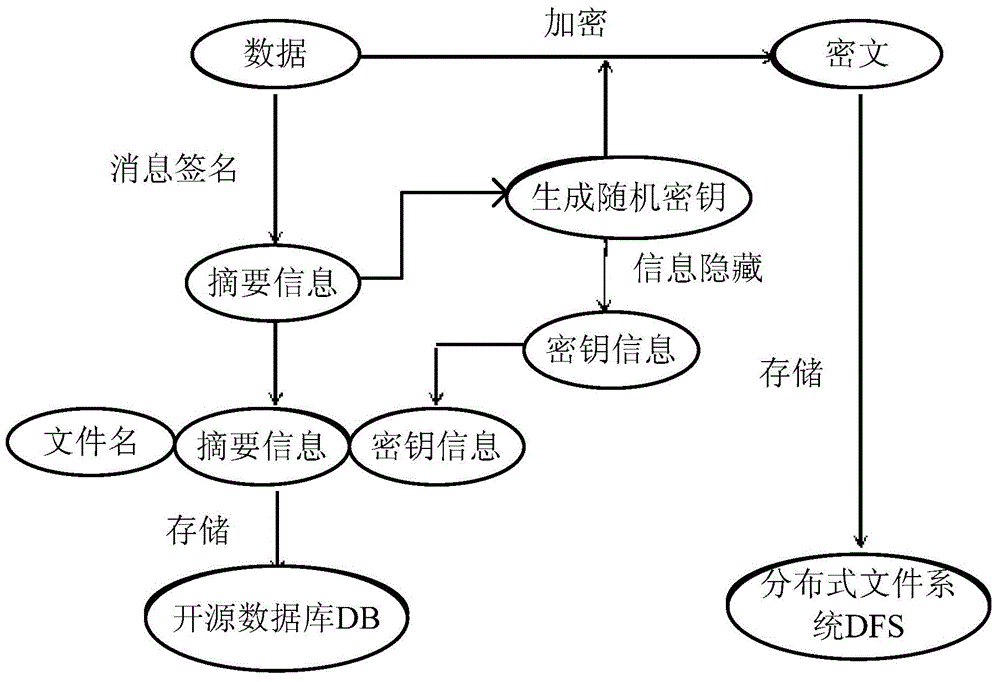
[0055] S1. Generate digest information; use a message digest algorithm to sign the data to be stored, thereby generating digest information;
[0056] S2. Encrypting data; using a random key generated by a key generation function to encrypt the data to be stored, so as to obtain corresponding ciphertext;
[0057] S3. Concealing the random key; performing concealment processing on the random key generated in step S2, so as to obtain the random key information of the ciphertext;
[0058] S4, storing the ciphertext; storing the ciphertext obtained in step S2 in the distributed file system DFS;
[0059] S5. Store relevant information; store the summary information generated in step S1 and the random key information o...
Embodiment 2
[0064] see image 3 , is a flow chart of a data security storage method based on a distributed system infrastructure provided by an embodiment of the present invention. The data security storage method based on the distributed system infrastructure of the present embodiment includes steps:
[0065] S1. Generate digest information; use a message digest algorithm to sign the data to be stored, thereby generating digest information;
[0066] In this step, it is preferable to use various attributes of the data to be stored and a random padding number to generate the summary information; wherein, the attributes include user password information, so that when the user modifies the password information, the random password The key information changes accordingly, but there is no need to re-encrypt all ciphertexts, which improves efficiency and reduces complexity. In addition, for users and systems, only key information needs to be managed, which simplifies key management. Using ra...
Embodiment 3
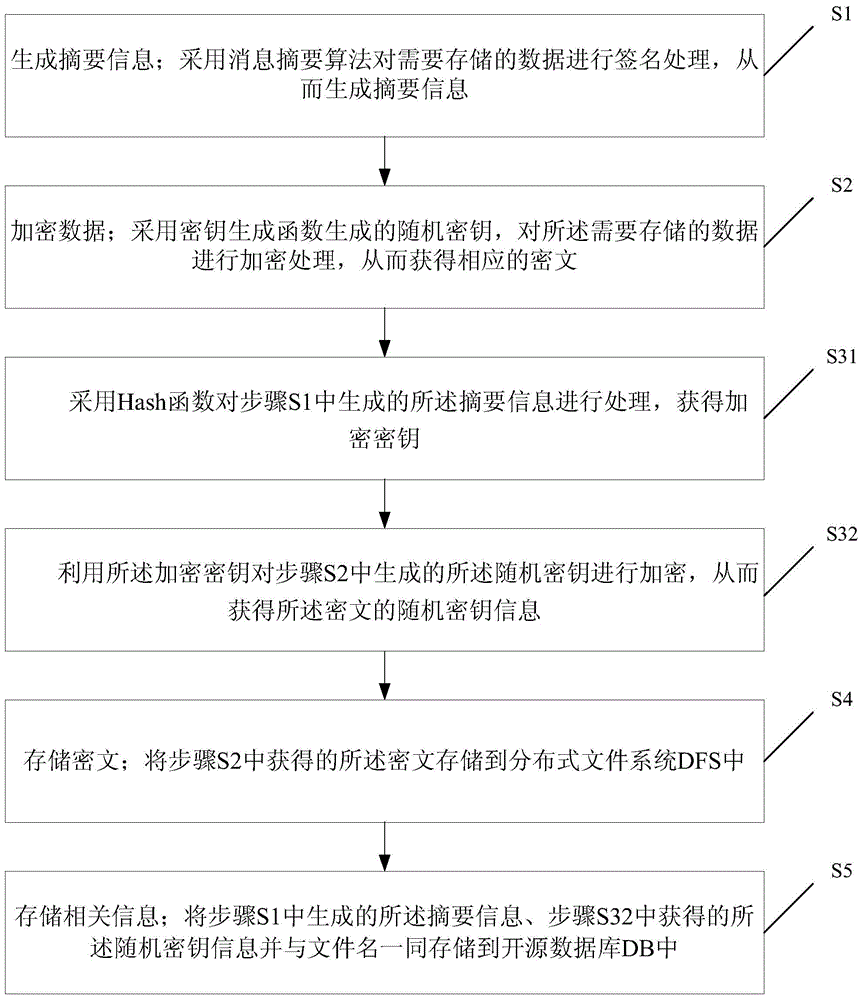
[0074] see Figure 5 , is a flow chart of a data security storage method based on a distributed system infrastructure provided by an embodiment of the present invention. The data security storage method based on the distributed system infrastructure of the present embodiment includes steps:
[0075] S1. Generate digest information; use a message digest algorithm to sign the data to be stored, thereby generating digest information;
[0076] In this step, preferably, the summary information is generated by using various attributes of the data to be stored and a random filling number; wherein, the attributes include user password information.
[0077] S2. Encrypting data; using a random key generated by a key generation function to encrypt the data to be stored, so as to obtain corresponding ciphertext;
[0078] S31. Adopt the SHA encryption algorithm to digest the various attributes of the data to be stored and a random padding number to obtain a digest value (byte array), and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com