Image encryption method based on chaotic system and insertion-deletion model
A technology of chaotic systems and encryption methods, applied in image data processing, image data processing, instruments, etc., can solve problems such as biochemical reaction models that are not considered, and achieve the effects of resisting attacks, ensuring high security, and high parallel computing capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] The embodiments of the present invention are implemented on the premise of the technical solutions of the present invention, and detailed implementation methods and specific operation processes are given, but the protection scope of the present invention is not limited to the following embodiments.
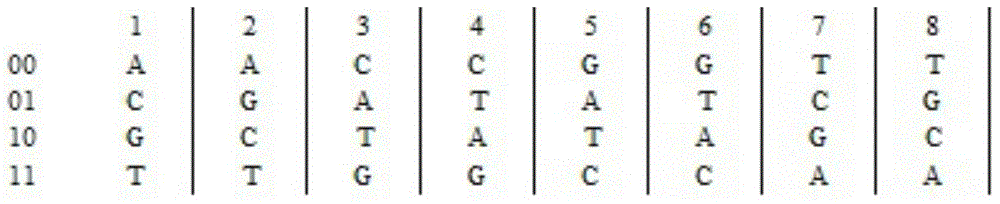
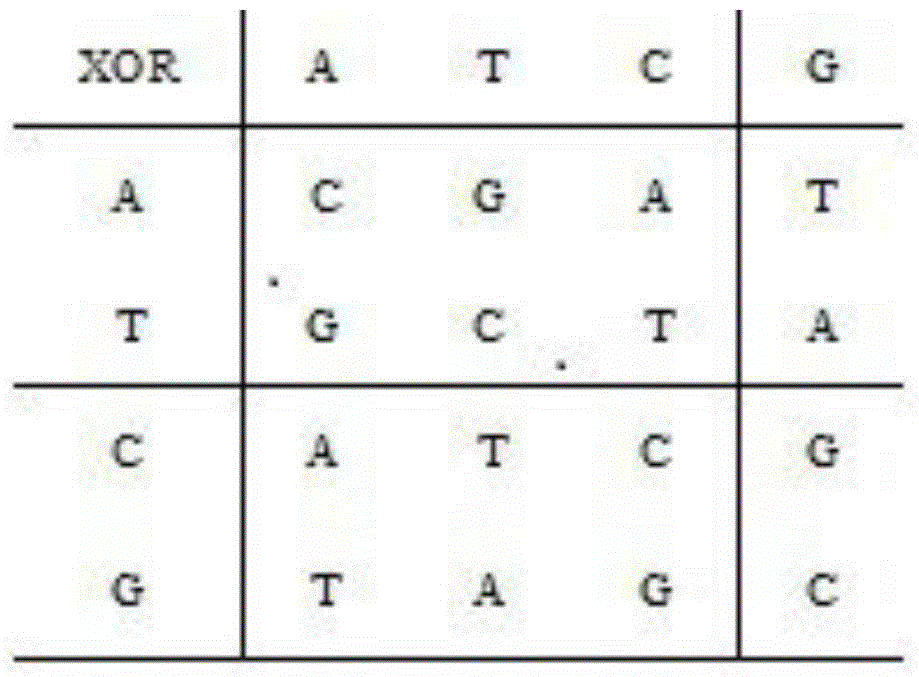
[0051] Step 1: Convert the original grayscale of size (m,n) picture The image is converted into a binary matrix; according to the second rule of DNA sequence encoding, the binary matrix is encoded, and a DNA sequence matrix DA with a size of (m, n×4) can be obtained;
[0052] Step 2: Given any initial value x 0 ,y 0 ,z 0 , and then add them to the Hamming distance, Hamming inverse distance, and Hamming complement distance converted to decimals between 0-1 to get a new initial value x 1 ,y 1 ,z 1 , at x 1 ,y 1 ,z 1 and system parameters σ, ρ, β, use the Lorenz chaotic map to generate three chaotic sequences x=(x 1 ,x 2 ,...,x 4n ), y=(y 1 ,y 2 ,...,y 4n ), z=...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com