Storage cross-site attack script vulnerability detection method, device and system
A vulnerability detection and scripting technology, which is applied in transmission systems, computer security devices, instruments, etc., can solve the problems of no automatic detection tools, storage of XSS vulnerability attack web pages without direct echo features, etc., and achieve high detection efficiency and accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
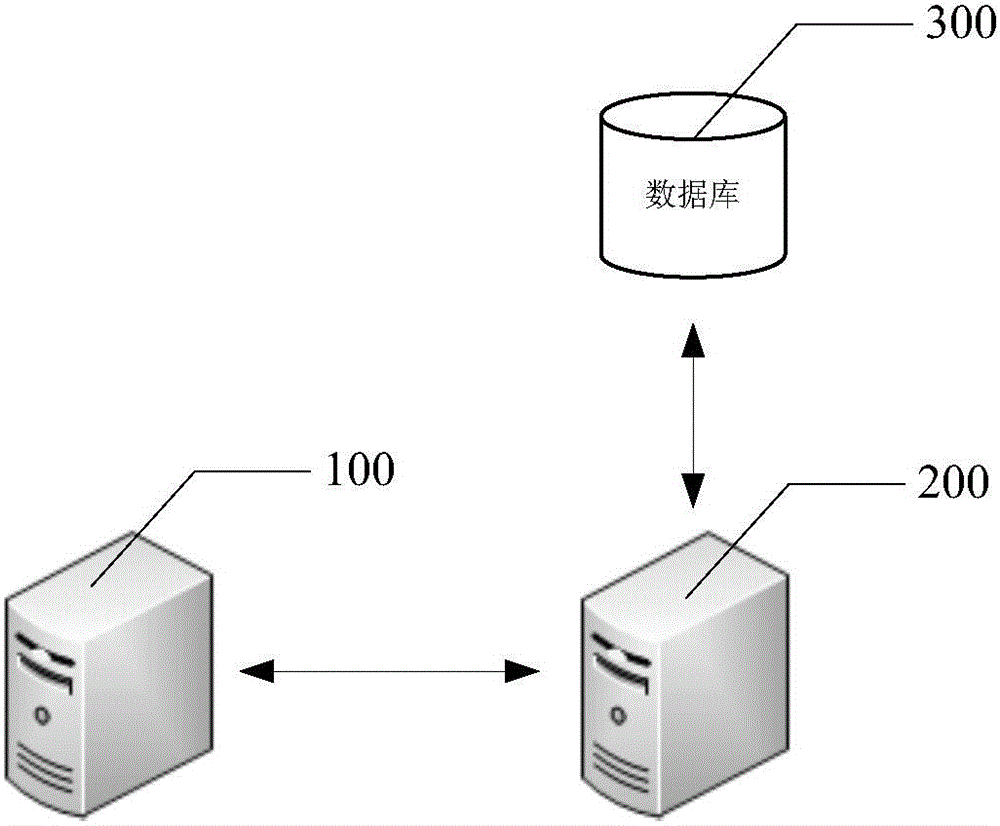
[0026] This embodiment provides a stored cross-site attack script vulnerability detection method, refer to Figure 4 , the above method includes the following steps:
[0027] Step S110, acquiring parameters to be detected of the target webpage.
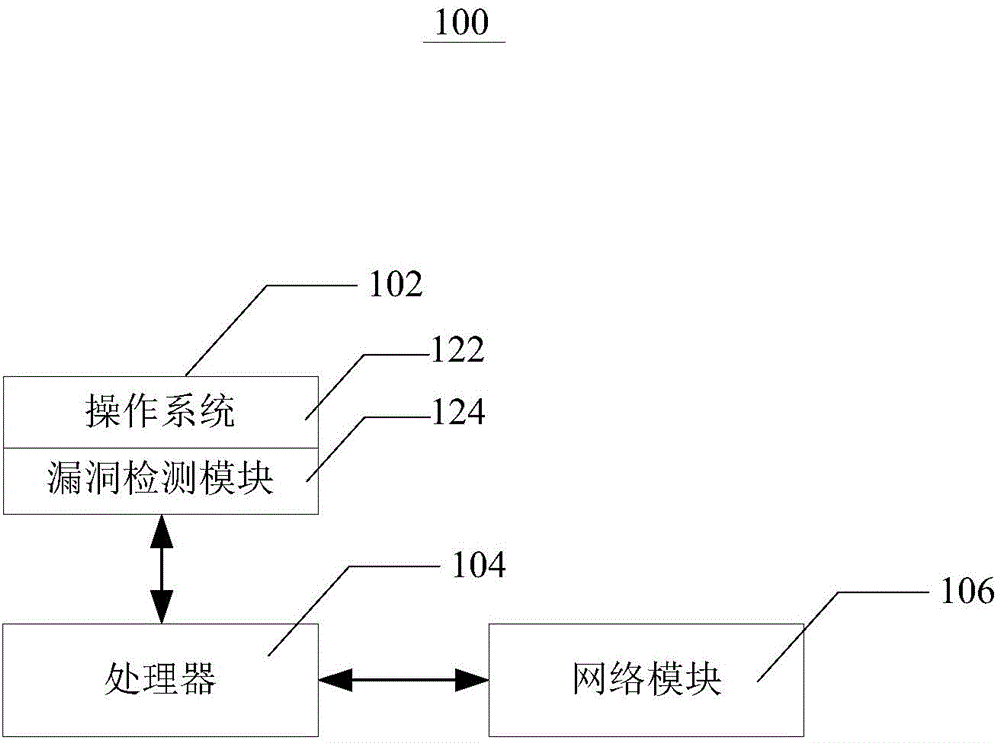
[0028] The target webpage refers to a webpage corresponding to a URL (Uniform Resource Locator, URL), such as "http: / / www.test.com / publish.php". It can be understood that a webpage is generated by one or more scripts in the website server (such as the website server 200 ) and returned to the client (such as the vulnerability detection server 100 ). In order to interact with the web server, the front-end webpage will have multiple parameters, which can be submitted to the web server through POST or GET. Specifically, the parameters and their values may be submitted to the website server through a Javascript script or a form (Form). After receiving the request, the web server will process these parameters, and the values of some ...
no. 2 example
[0049] The present embodiment provides a stored cross-site attack script vulnerability detection method, which is used to detect possible XSS vulnerabilities in a website to be detected. refer to Figure 5 , the above method includes the following steps:
[0050] Step S210, acquiring the target webpage.
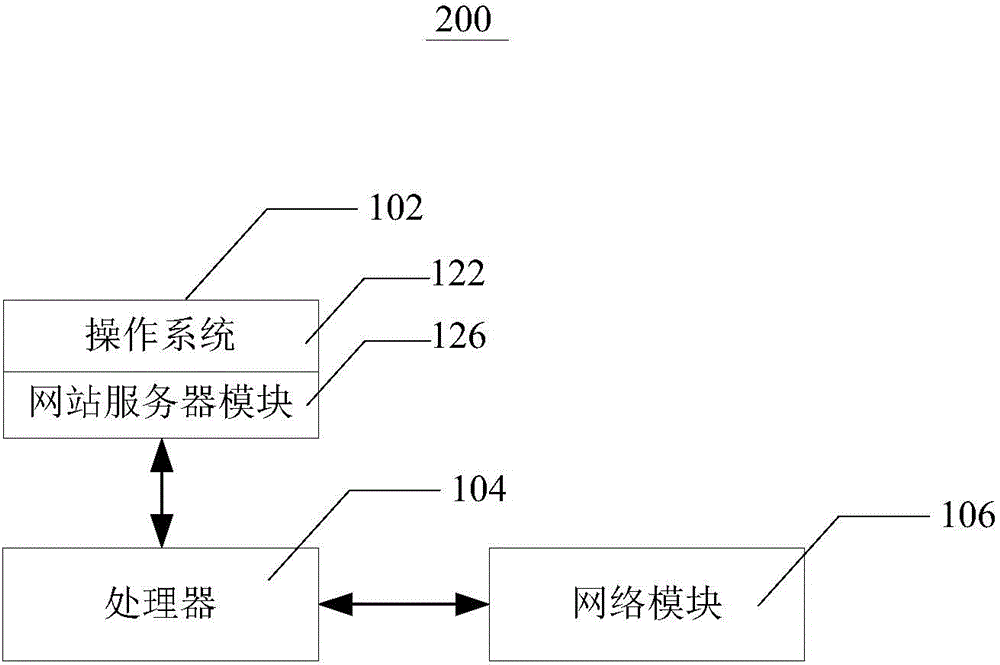
[0051] Initially, the target webpage may be, for example, an entrance webpage of the website to be detected. For the entry page, it should contain links to other pages within the site. After the detection of the portal webpage is completed, the webpages pointed to by these links may be detected again, and the webpages pointed to by these links may be called sub-webpages of the current webpage. For example, the entrance page of the website www.test.com is www.test.com / index.php, and the entrance page contains three links: www.test.com / channel1.php, www.test.com / channel2.php, and www.test.com / channel3.php. It can be understood that the sub-webpage still includes the link o...
no. 3 example
[0080] The present embodiment provides a stored cross-site attack script vulnerability detection method, which is used to detect possible XSS vulnerabilities on one or more websites to be detected. refer to Figure 7 , the above method includes the following steps:
[0081] Step S310, submitting the feature string.
[0082] Specifically, obtain the webpages to be detected from one or more websites, obtain the parameters to be detected for each webpage, generate feature strings for each parameter to be detected, and submit the generated feature strings to the corresponding web server. The specific process can also refer to the foregoing embodiments.
[0083] The submitted feature string contains characters that can trigger a stored cross-site scripting attack. If the corresponding website has an XSS vulnerability, part of the content of the above feature string, such as the unique identifier, will be stored in the database.
[0084] Step S320, after waiting for a predetermi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com