Continuous data protection method
A data protection and data technology, applied in the field of data protection in the field of information security, can solve problems such as data change and loss, and achieve the effect of rapid verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0118] The present invention will be described in further detail below in conjunction with the accompanying drawings.
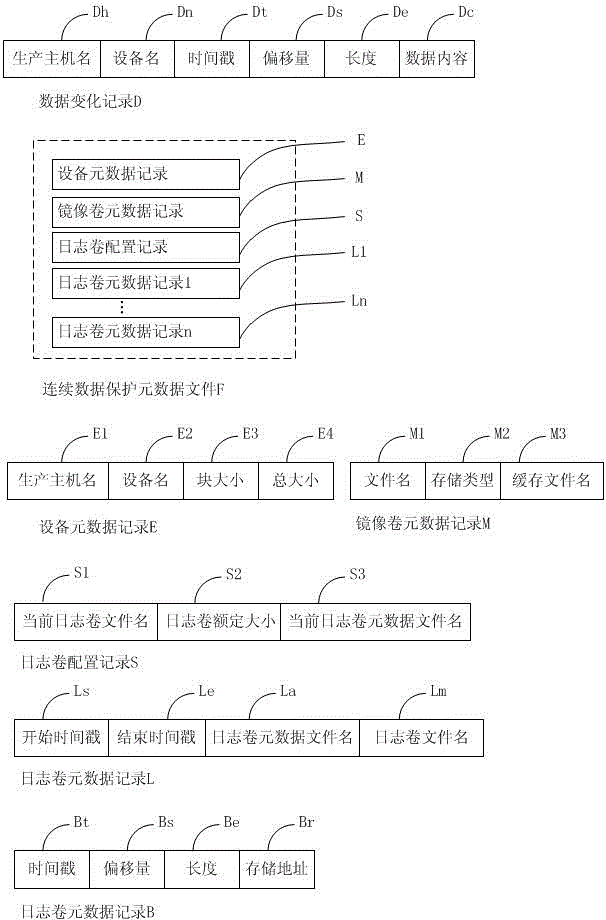
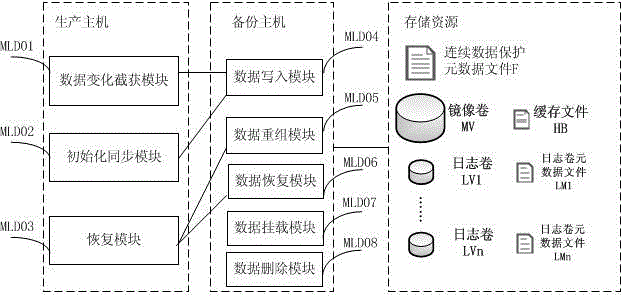
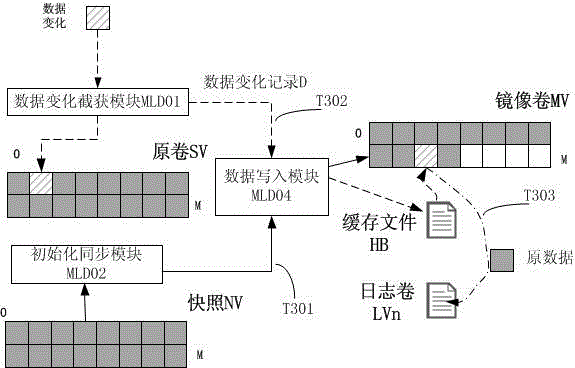
[0119] The data structure diagram of the data change record and continuous data protection metadata file of the present invention is as follows figure 1 shown.
[0120] The data change record D is used to describe the data change of a certain block device. Among them, the production host name Dh is used to describe the host name that needs continuous data protection, which can uniquely identify a host, which can be UUID, host identifier or any other identifier that can confirm the uniqueness in the system; the device name Dn is used to describe The name of a block device to be protected on the host; the timestamp Dt is used to describe the time point when the data change occurs; the offset Ds is used to describe the initial address of the data change, which is relative to the starting point of the block device The starting address is 0; the length De is u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com