Signal-level fusion networking radar anti-cheating interference method under object signal correlation
A signal-level fusion and deceptive jamming technology, applied in the radar field, can solve the problems of not being able to fully utilize the advantages of radar networking, other information not being used effectively, and affecting the deceptive jamming of networking radars.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
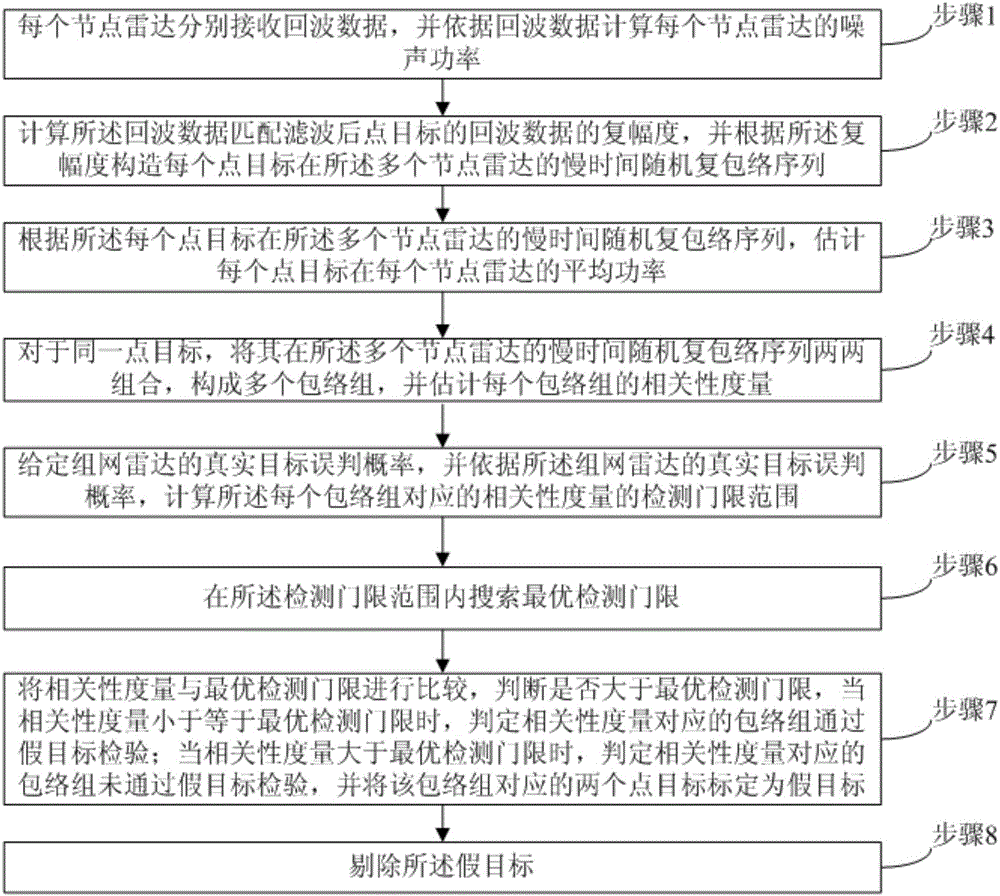
[0078] refer to figure 1 , which shows an embodiment of the present invention, a networked radar anti-spoofing jamming method based on target signal correlation and signal level fusion. This embodiment may specifically include the following steps:
[0079] Step 1, each node radar receives echo data respectively, and calculates the noise power of each node radar according to the echo data.
[0080] In this embodiment, it is assumed that the networked radar includes n node radars, where n≥2, and it is assumed that the echo data of the point target after the matched filtering includes P point targets.
[0081] Said step 1 includes the following sub-steps:
[0082] 1a) It is assumed that the networked radar includes n node radars, where n≥2, and each node radar receives echo data;
[0083] It should be noted that the networked radar system in this embodiment includes n node radars, n≥2, and each node radar receives echo data that does not contain signals, that is, each node rada...
Embodiment 2
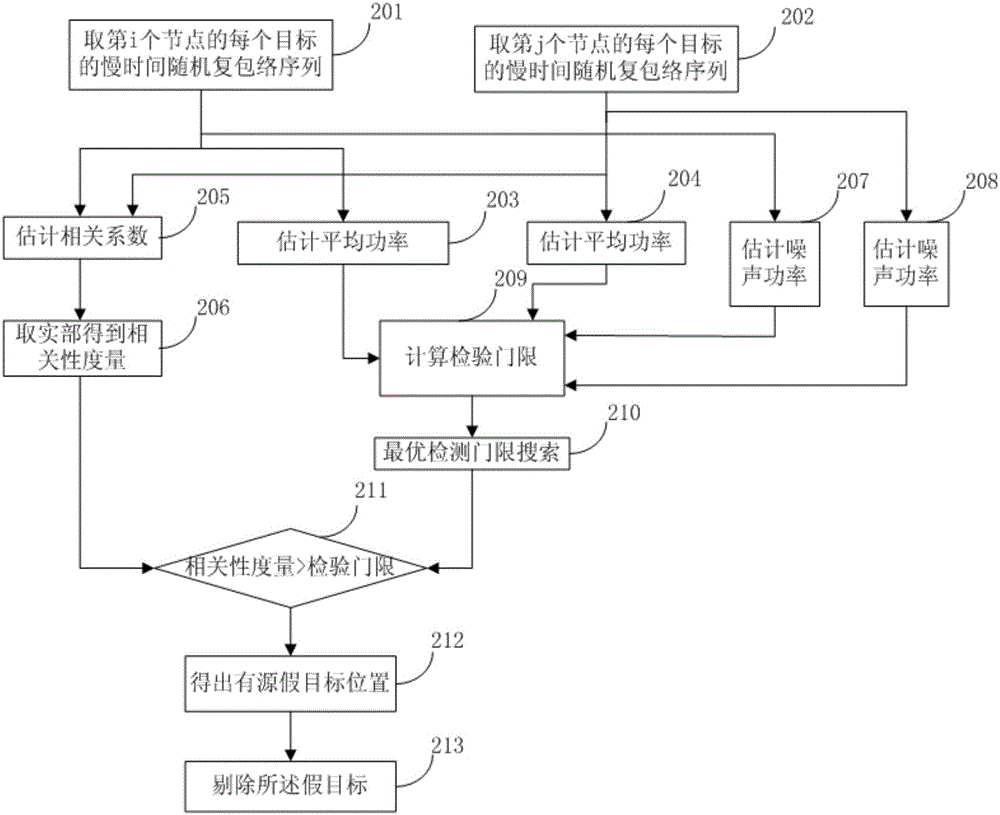
[0154] refer to figure 2 , which shows an embodiment of the present invention, a networked radar anti-spoofing jamming method based on target signal correlation and signal level fusion. This embodiment may specifically include the following steps:
[0155] Step 201, get the slow-time random complex envelope sequence of each target of the i-th node.
[0156] It should be noted that the step 201 corresponds to the step 2 in the first embodiment, and reference may be made to the relevant description of the step 2 in the first embodiment, which will not be repeated here in this embodiment.
[0157] Step 202, get the slow-time random complex envelope sequence of each target of the jth node.
[0158] It should be noted that the step 202 corresponds to the step 2 in the first embodiment, and reference may be made to the related description of the step 2 in the first embodiment, which will not be repeated here in this embodiment.
[0159] Step 203, estimating the average power;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com