Networking radar anti-cheating interference method based on signal level fusion
A technology of deceptive jamming and signal level fusion, which is applied in the field of networked radar anti-spoofing jamming based on signal level fusion, can solve the problem that the anti-jamming ability cannot be fully exerted, the location of networked radar stations is not ideal, and other information is not effective issues such as the use of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
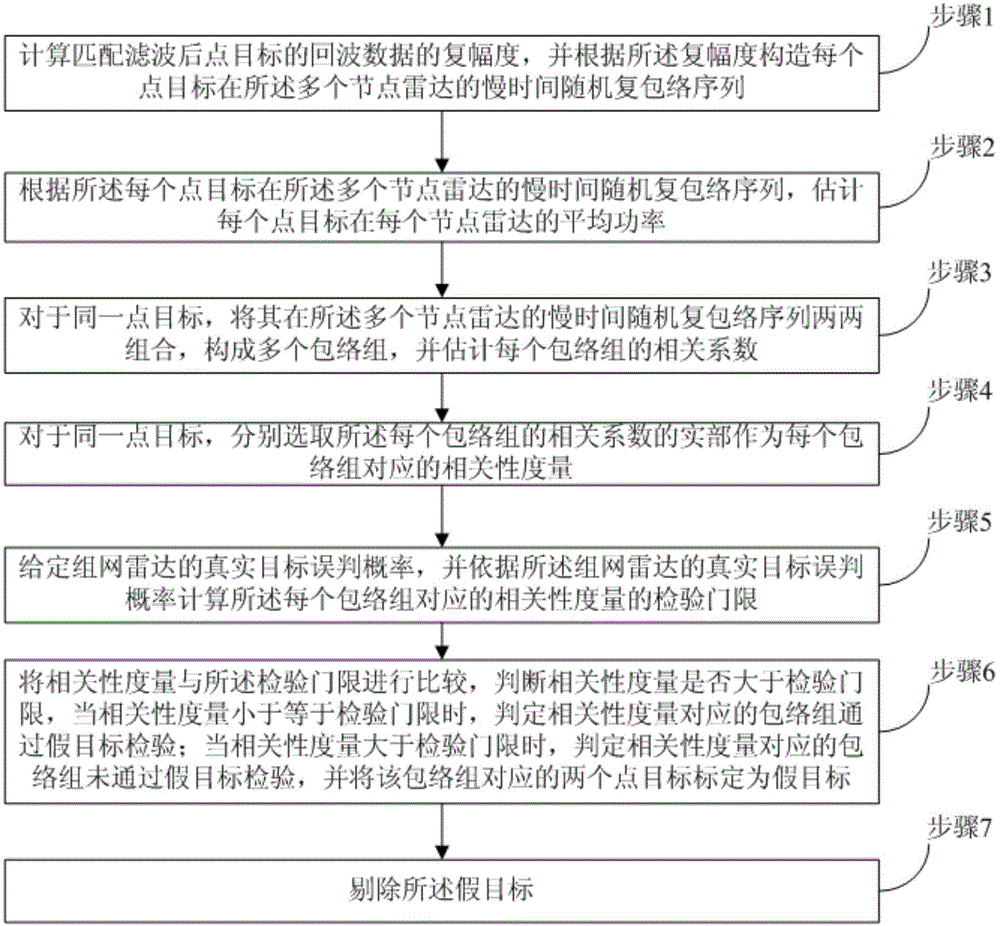
[0064] refer to figure 1 , which shows a flow chart of a method for anti-spoofing jamming of networked radar based on signal level fusion according to an embodiment of the present invention. This embodiment may specifically include the following steps:
[0065] Step 1, calculate the complex amplitude of the echo data of the point target after the matched filtering, and construct the slow-time random complex envelope sequence of each point target in the multiple node radars according to the complex amplitude.
[0066] In this embodiment, it is assumed that the networked radar includes n node radars, where n≥2, and it is assumed that the echo data of the point target after the matched filtering includes P point targets.
[0067] Step 1 described in this embodiment includes the following sub-steps:
[0068] 1a) Assuming that the networked radar includes n node radars, where n≥2, each node radar receives the echo data, and uses the following formula to perform matching filtering ...
Embodiment 2
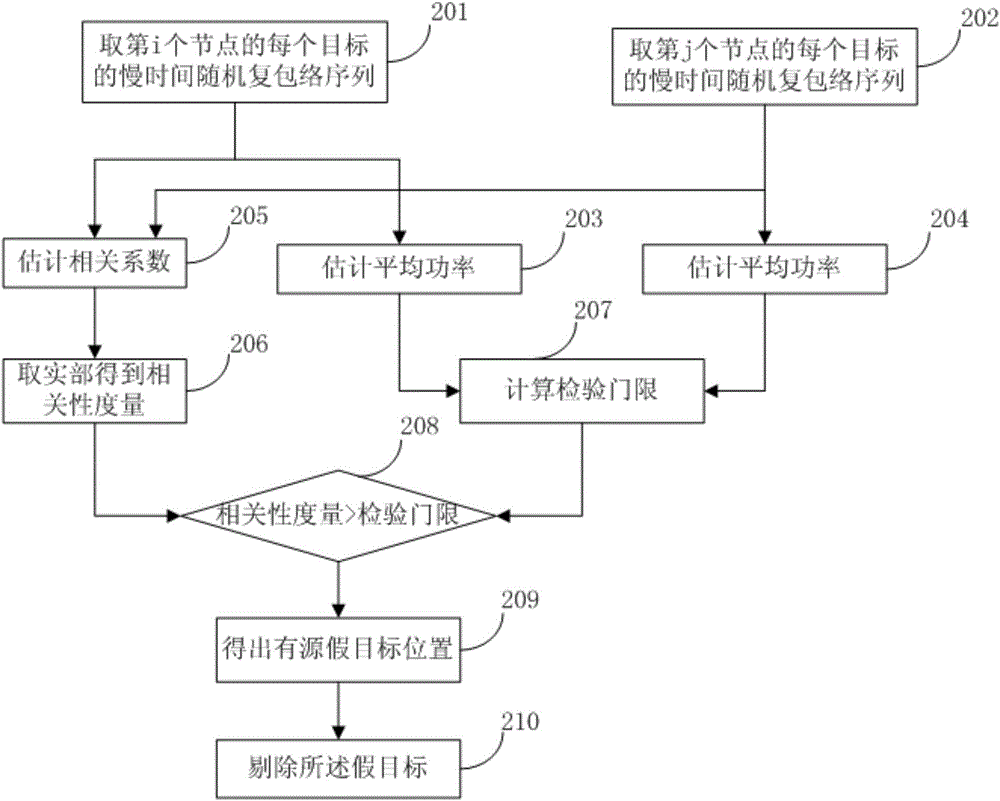
[0124] refer to figure 2 , showing a flow chart of a networked radar anti-spoofing jamming method based on signal level fusion according to an embodiment of the present invention,
[0125] In this embodiment, it is assumed that the networked radar includes n node radars, where n≥2, and it is assumed that the echo data of the point target after the matched filtering includes P point targets.
[0126] This embodiment may specifically include the following steps:
[0127] Step 201, get the slow-time random complex envelope sequence of each target of the i-th node.
[0128] It should be noted that the step 201 corresponds to the step 1 in the first embodiment, and reference may be made to the related description of the step 1 in the first embodiment, which will not be repeated here in this embodiment.
[0129] Step 202, get the slow-time random complex envelope sequence of each target of the jth node.
[0130] It should be noted that the step 202 corresponds to the step 1 in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com