Dataflow control method facing virtual desktop and information safety device
A virtual desktop and control method technology, applied in the field of information security, can solve problems such as illegal copying of internal sensitive data, data loss, etc., achieve strong practicability and ease of use, and prevent bypassing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
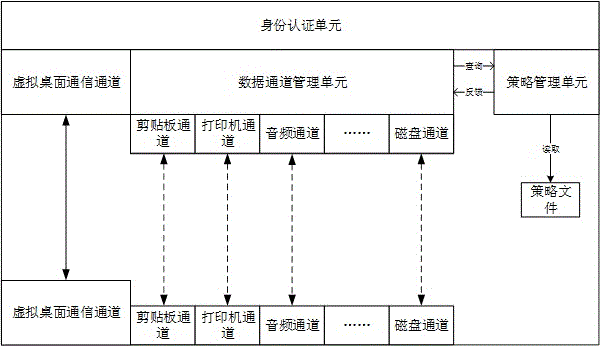
[0040] An information security device capable of effectively preventing data from being stolen, the device comprising:
[0041] One or more servers, implement hardware virtualization technology on the server, virtualize a plurality of virtual machines, and deploy a virtual desktop system on the virtual machines;
[0042] One or more user terminals, the user operates on the terminal operating platform, accesses the virtual desktop system, and sends a data exchange request;
[0043] A hardware gateway, deployed between the virtual desktop and the operating platform;
[0044] The hardware gateway predefines a set of security policies as the basis for data flow control between the virtual desktop and the operating platform;
[0045] The hardware gateway intercepts the data exchange request and suspends the request, and parses the data exchange request to obtain request initiator information, request recipient information, and the data type of the request exchange;
[0046] The h...
Embodiment 2
[0050] A data flow control method applied to virtual desktops, comprising the following steps:
[0051] Add a middleman identity step between the virtual desktop and the operating platform;
[0052] The controlled establishment of a channel is carried out by an intermediary according to a defined policy.
specific Embodiment 2
[0053] Specific embodiment 2 is applied to the implementation of multi-level variable security requirements.
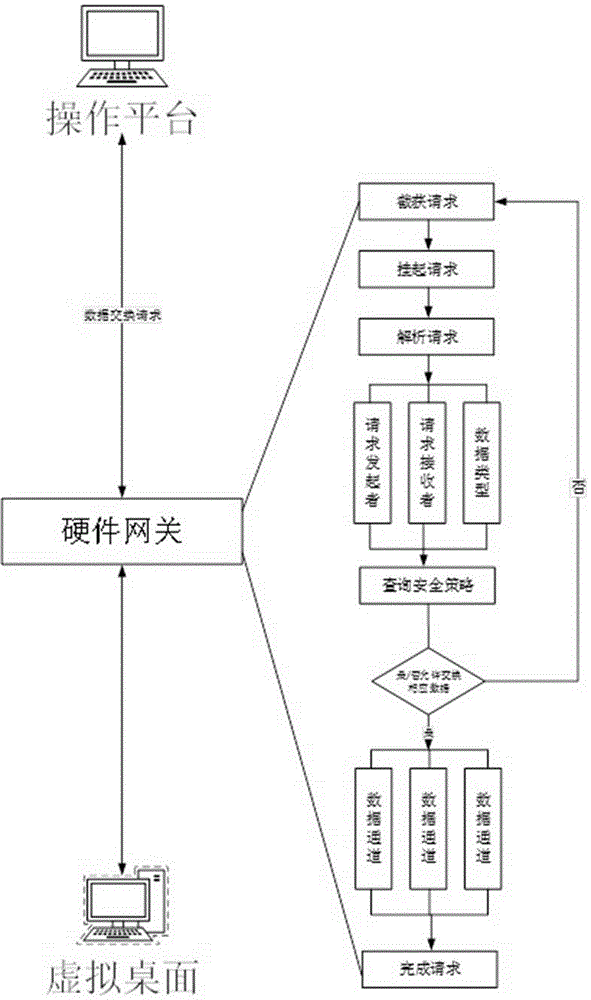
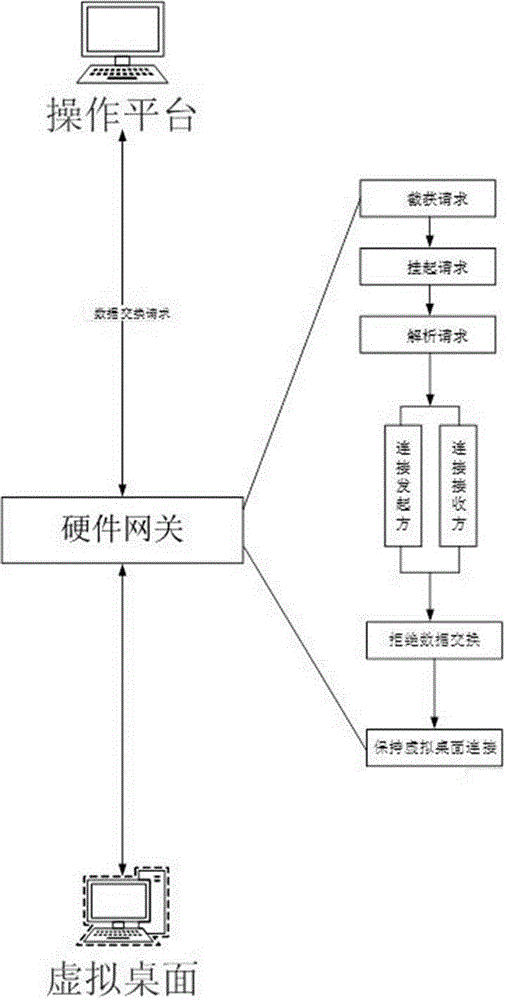
[0054] Such as figure 2 As shown, a virtual desktop-oriented data flow control method includes the following steps:
[0055] S1. The operating platform initiates a data exchange request to the virtual desktop;
[0056] S2. The identity authentication unit of the hardware gateway suspends the data exchange request;
[0057] S2. The identity authentication unit of the hardware gateway starts to parse the data exchange request, obtains the identity of the requester, the data type requested for exchange, that is, the data channel that is applied for establishment, and sends it to the data channel management unit. After receiving it, the data channel management unit will generate a query request , initiate a query to the policy management unit;
[0058] S3. The policy management unit reads a preset security policy;
[0059] S4. If the security policy allows the exchan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com