Virtualization-based credible server trust chain construction method
A construction method and server technology, which is applied to the construction method of trusted server trust chain, belongs to the field of server information trustworthy construction, can solve problems such as difficult defense against malicious threats, and achieve the effect of ensuring integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described in conjunction with the accompanying drawings.
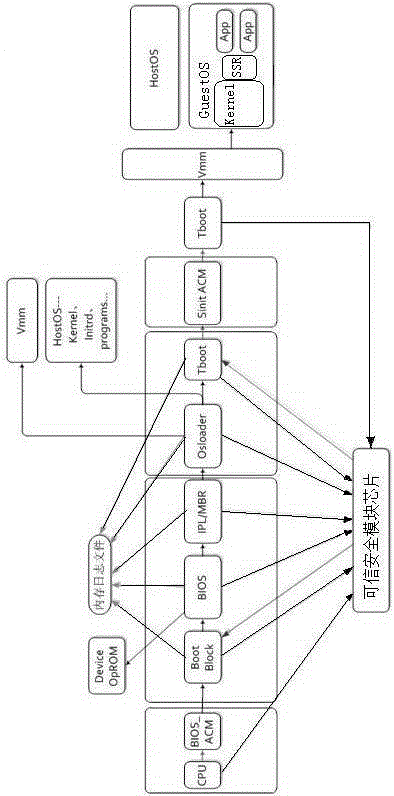
[0020] A trusted server trust chain system based on virtualization, with the TPM security chip on the main board of the server as the root of trust, and VMM as the Xen platform, including trusted hardware layer, trusted virtualization layer, trusted OS layer and management platform;
[0021] Trusted hardware layer: Based on the TPM security chip, the trust chain from server power-on to OS startup is constructed by using BIOS, boot operating system OSLoader and TBoot components for trusted detection.
[0022] Trusted virtualization layer: including the server and management side, statically measure the VMM, VM image and files in the VM image through the security module of Xen, such as OSKernel, application layer measurement components, etc., and carry out policies and logs on the files under Xen , keys and other management; support centralized management based on B / S architec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com