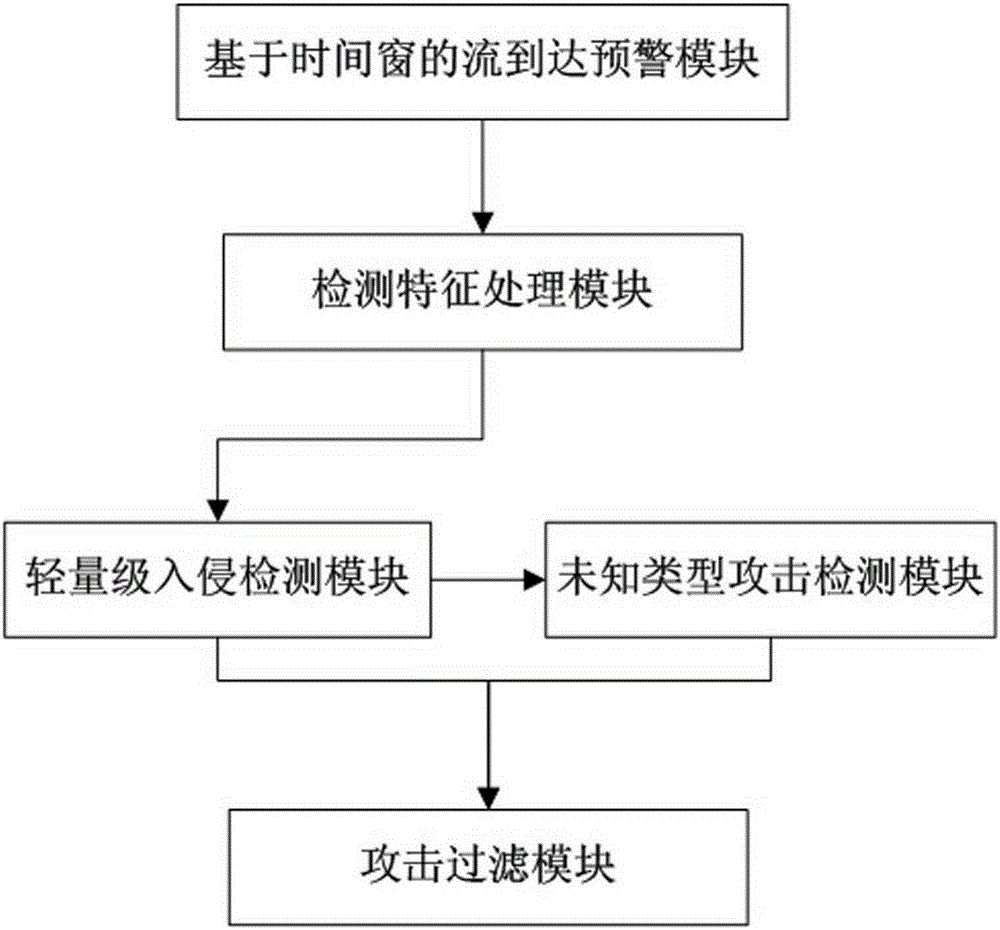
DoS/DDoS attack detecting and filtering method based on light-weight intrusion detection
A technology for intrusion detection and attack detection, applied in electrical components, transmission systems, etc., can solve problems such as limited redundant information, excessive consumption of detection resources, and unresolved problems of unknown attack detection, so as to improve the detection effect, The effect of accurate real-time processing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
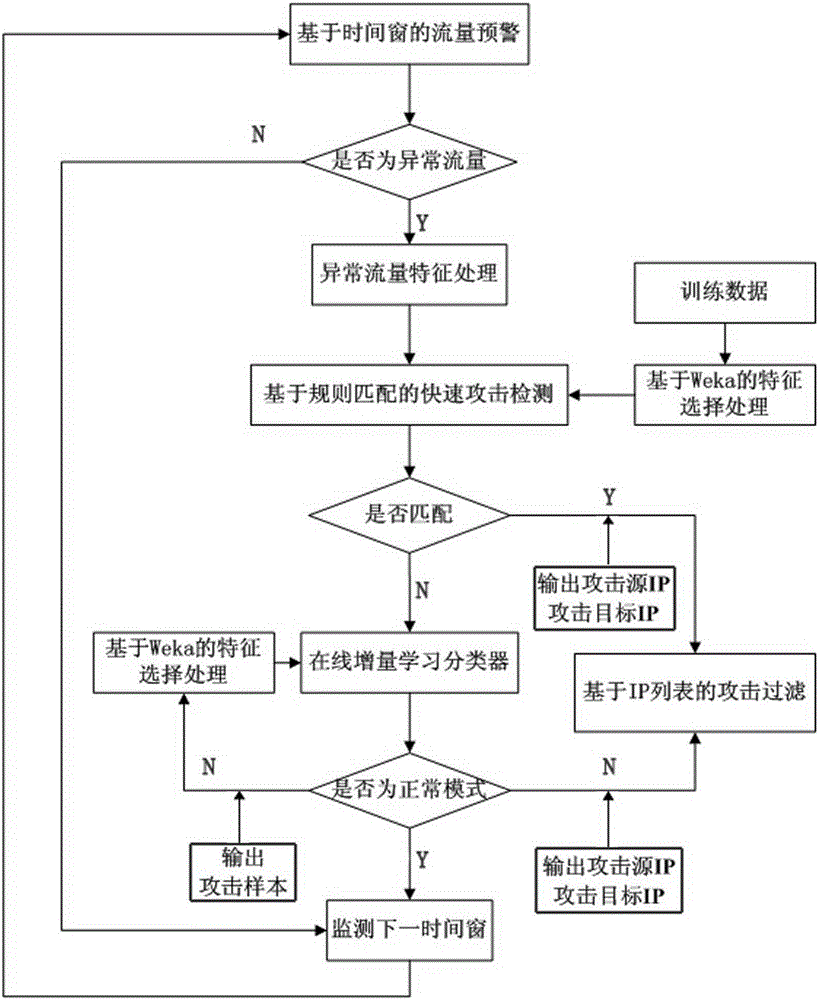
[0019] The DoS / DDoS attack detection and filtering method based on lightweight intrusion detection of the present invention will be further explained below with reference to the accompanying drawings and specific embodiments:
[0020] As attached figure 1 As shown, the DoS / DDoS attack detection and filtering process of the present invention is divided into:
[0021] 1. Traffic warning based on time window
[0022] Update and monitor the arrival of traffic in time windows one by one, and define the window length t of the time window according to the defense target processing capability W And flow number threshold Δ 0 , When there is a sudden access or a surge in traffic and reaches the threshold Δ 0 When there is abnormal traffic in this window, the subsequent detection and filtering mechanism is triggered.
[0023] 2. Abnormal flow characteristics processing
[0024] The abnormal traffic in step 1 is processed as a sequence of detection characteristic samples for use in subsequent steps...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com