Secure pairing method for intelligent wearable equipment and other equipment
A wearable device and intelligent technology, applied in the field of information security, can solve problems such as value discounts, complicated operation of personal passwords, eavesdropping of personal passwords, etc., to achieve the effect of facilitating life and broadening the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further described below in conjunction with the accompanying drawings.
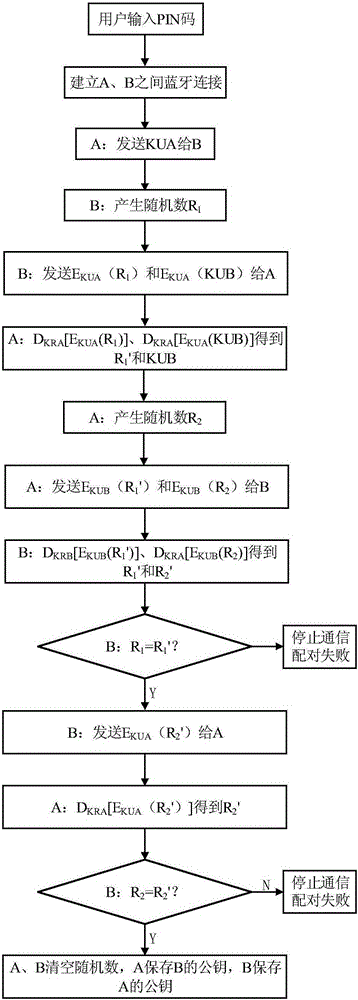
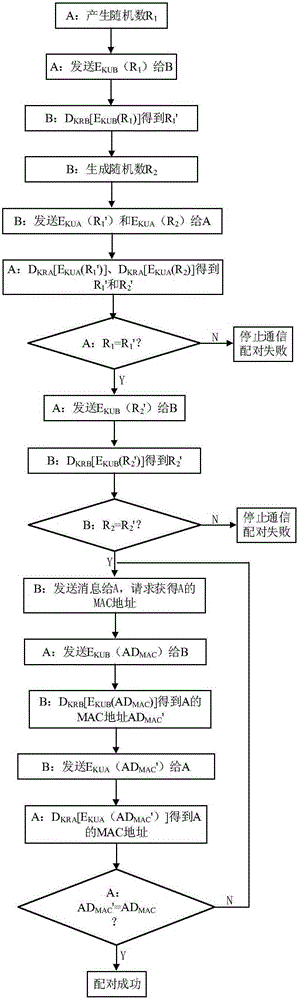
[0043] The invention provides a safe pairing method between an intelligent wearable device and other devices. The method includes three parts: key generation before the first pairing, personal password setting for the first pairing, public key exchange and automatic routine pairing; The paired personal password is set to exchange the public keys of both parties to complete the first authentication of both devices.
[0044] This method is based on the PKI asymmetric key system, and uses encrypted random numbers to verify the identities of both parties; the ROM of the smart wearable device or its paired device must have an encrypted area, the key area, which denies all external access.
[0045] The key pair generation process before the first pairing is as follows:
[0046] Before the first pairing, a key pair needs to be generated. The user enters the personal password...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com