Android application safety analysis method based on sensitive behavior identification
An analysis method and security technology, applied in computer security devices, platform integrity maintenance, instruments, etc., can solve problems such as information not involved in code hiding, false negatives, low code coverage, etc., to improve accuracy, improve The effect of detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
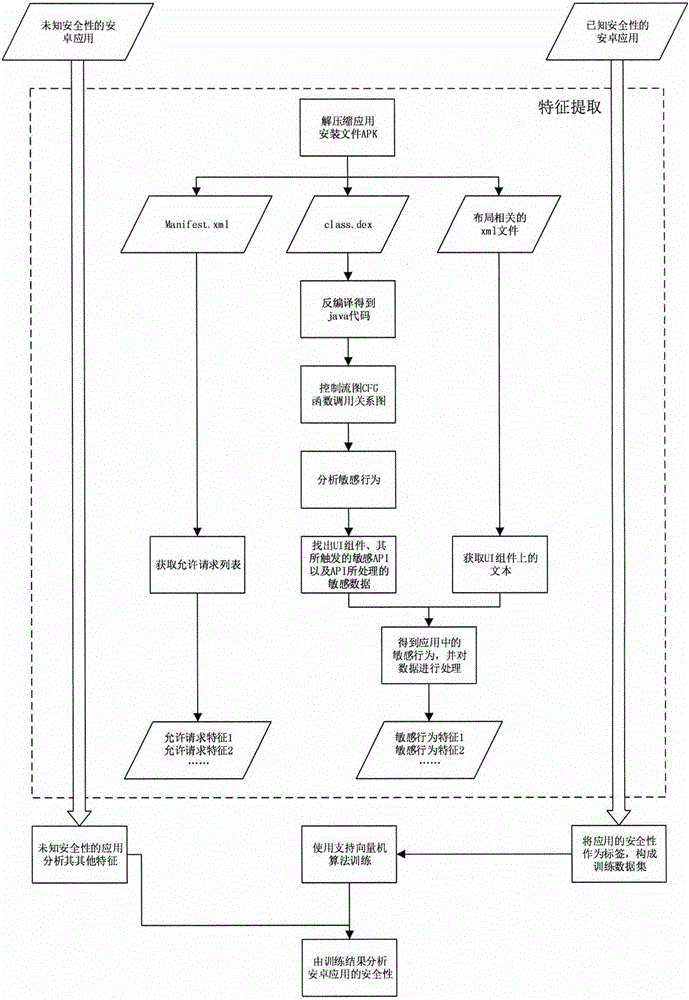
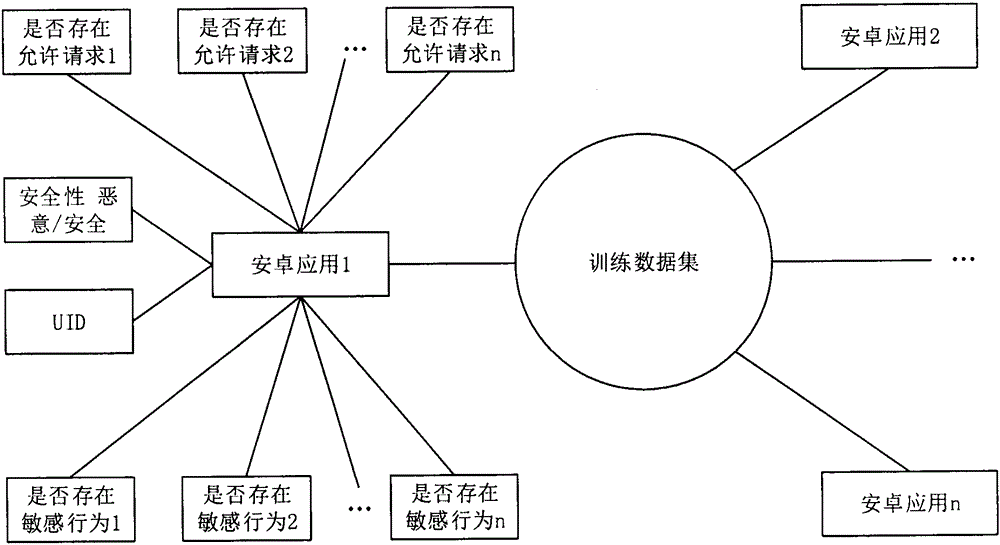
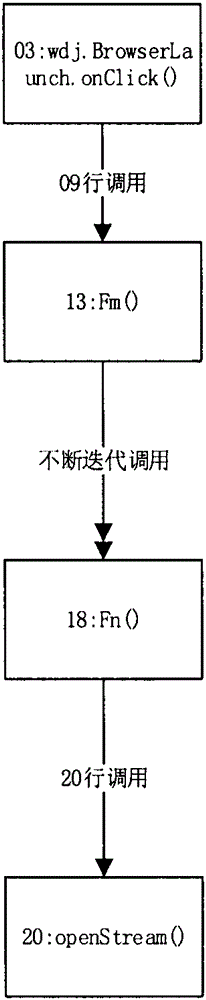
[0057] Process flow of the present invention such as figure 1 As shown, the main part is the feature extraction using the sensitive behavior analysis method. What needs to be done is to obtain the data that can be used by the support vector machine algorithm by analyzing the installation file APK of the Android application. For Android applications with known security, its features are obtained through analysis and organized as a training data set; for Android applications with unknown security, features other than security can be obtained through feature analysis, and these features are combined with data training As a result, its safety is predicted.
[0058] Step 1: The APK file cannot be analyzed directly, and Manifest.xml, class.dex, and layout.xml files related to the layout need to be obtained after decompression. These files cannot be directly used as the input for the next step of analysis. We need to use the tool dex2jar (http: / / sourceforge.net / projects / dex2jar / ) to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com