Control strategy generation method and apparatus
A control strategy and forwarding chip technology, applied in the field of communication, can solve problems such as inability to achieve results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
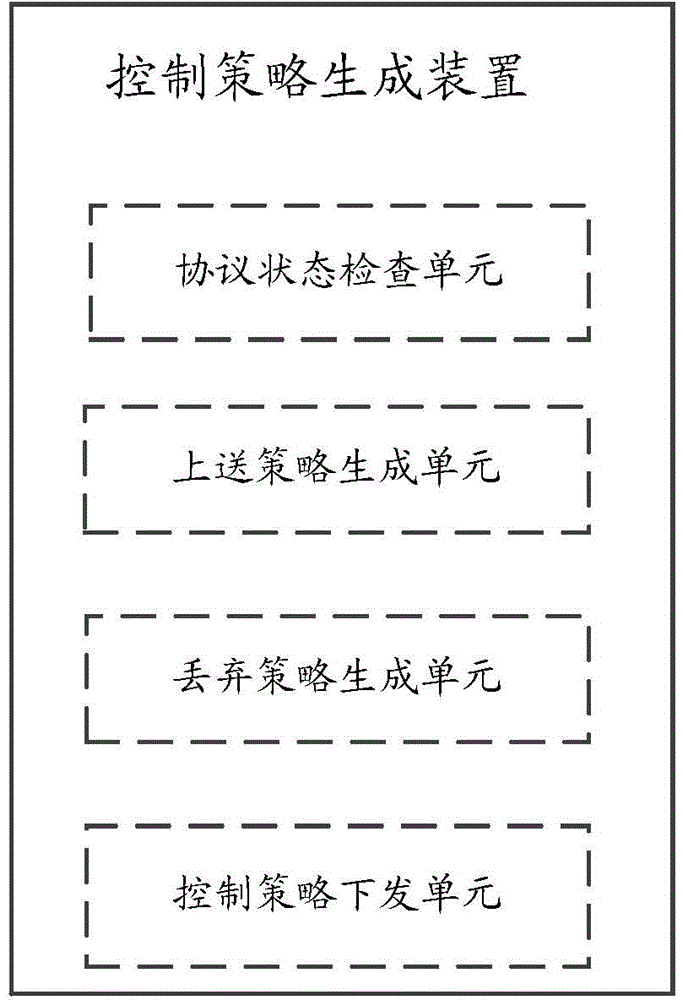
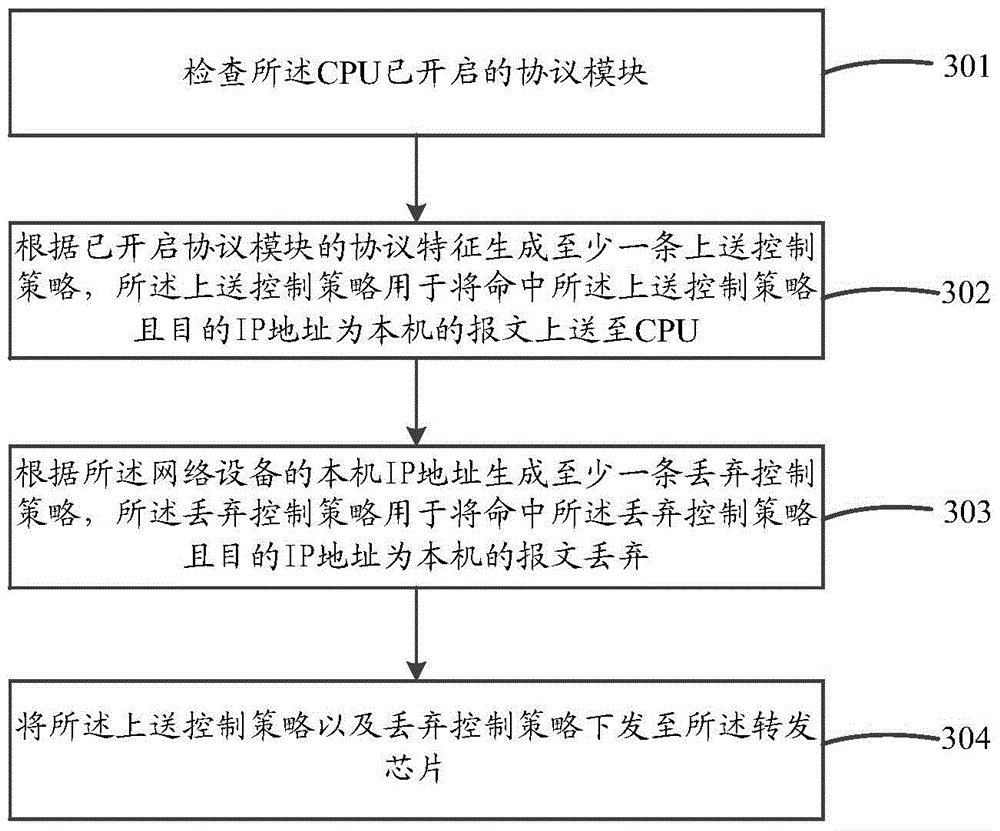
[0018] Aiming at the problems encountered in the prior art, the present invention provides a method and device for generating a control strategy. The method for generating the control strategy generates at least one sending control strategy and at least one discarding control strategy respectively according to the protocol characteristics of the enabled protocol module and the IP address of the network device by checking the opening status of the protocol module of the CPU protocol stack, and sends them out to the forwarding chip to control the forwarding chip to send the received local message to the CPU or discard it.
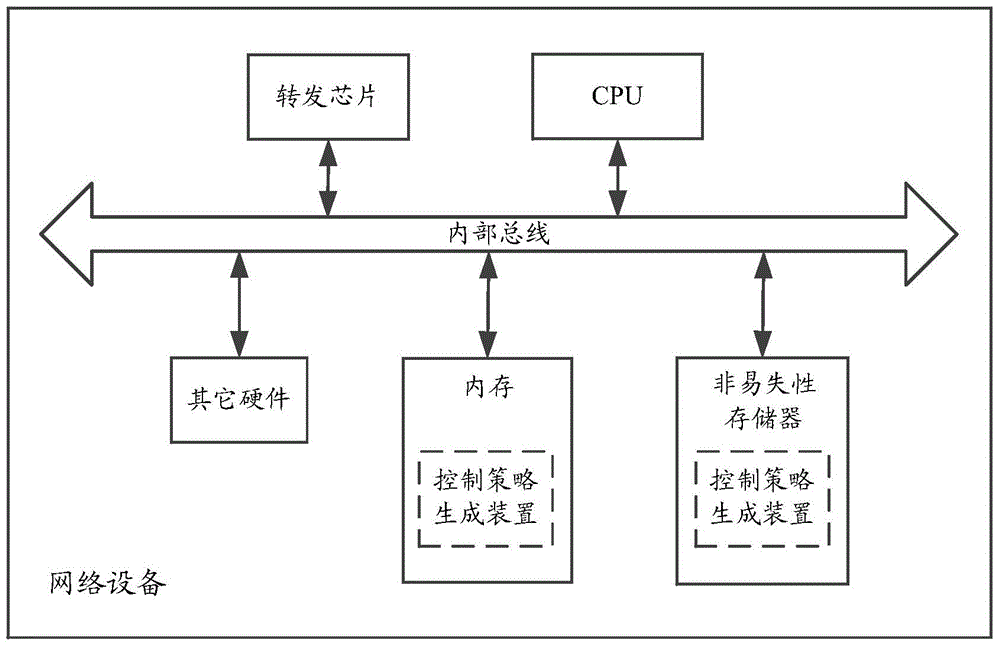
[0019] Please refer to figure 1 , the control policy generation device provided by the present invention is applied to network equipment, the network equipment can be switches and routers, etc., the basic hardware environment of the network equipment includes CPU, forwarding chip, memory, non-volatile memory and other hardware. figure 2 It is a schematic di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com