Sensing original data safety protection method supporting data processing
A technology for data security and data processing, which is applied in transmission systems, climate sustainability, sustainable communication technology, etc., can solve problems such as inability to effectively solve data integrity identification, and meet security protection requirements, low overhead, and realize data security. The effect of privacy protection and integrity verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
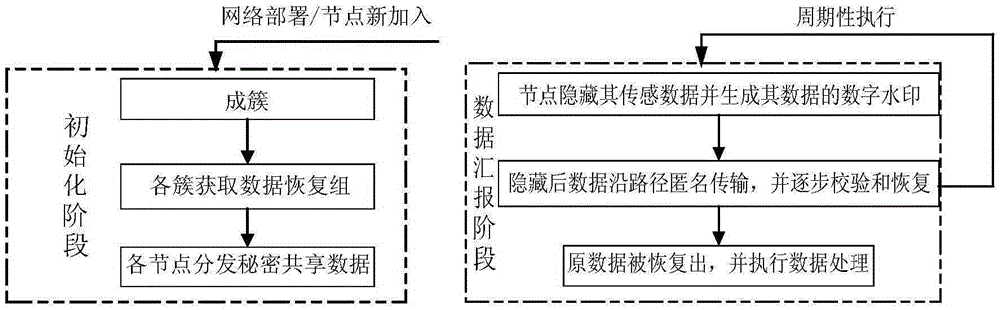
[0028] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
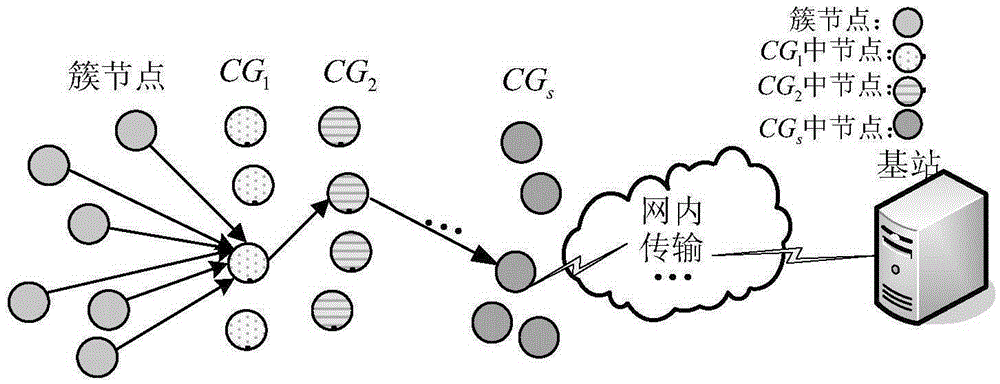
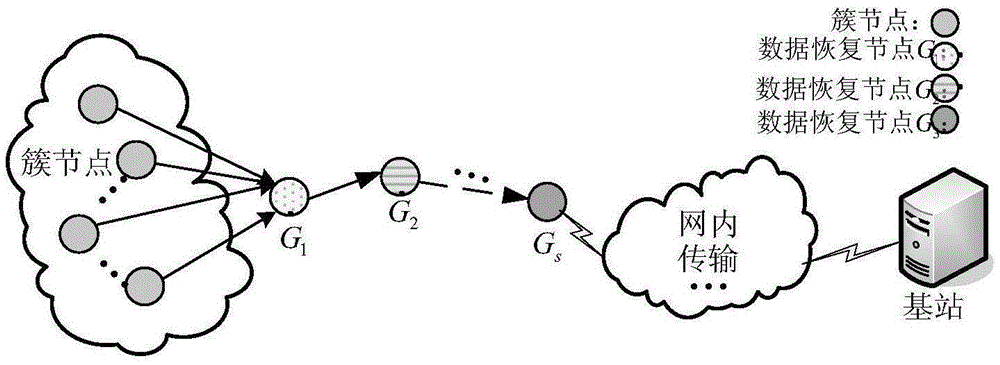
[0029] A security protection method for raw sensing data supporting data processing in the present invention, the system of which is as follows figure 1 As shown, it includes: a cluster node, a data recovery group and a data recovery node, a data processing node and a base station.
[0030] For any cluster node that is μ-hop away from the base station, define its neighbor node that is (μ-1) hop away from the base station as its predecessor node, and the neighbor nodes at the same level are the same number of hops away from the base station; and define “data recovery group” and “data recovery node " means the following:
[0031] Data Recovery Group CG i : For any cluster, the set composed of some nodes randomly selected from the public predecessor nodes of its cluster members is called the data recovery group CG 1 ; called from CG 1 The set composed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com