Patents
Literature
36results about How to "Avoid problems like crashes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
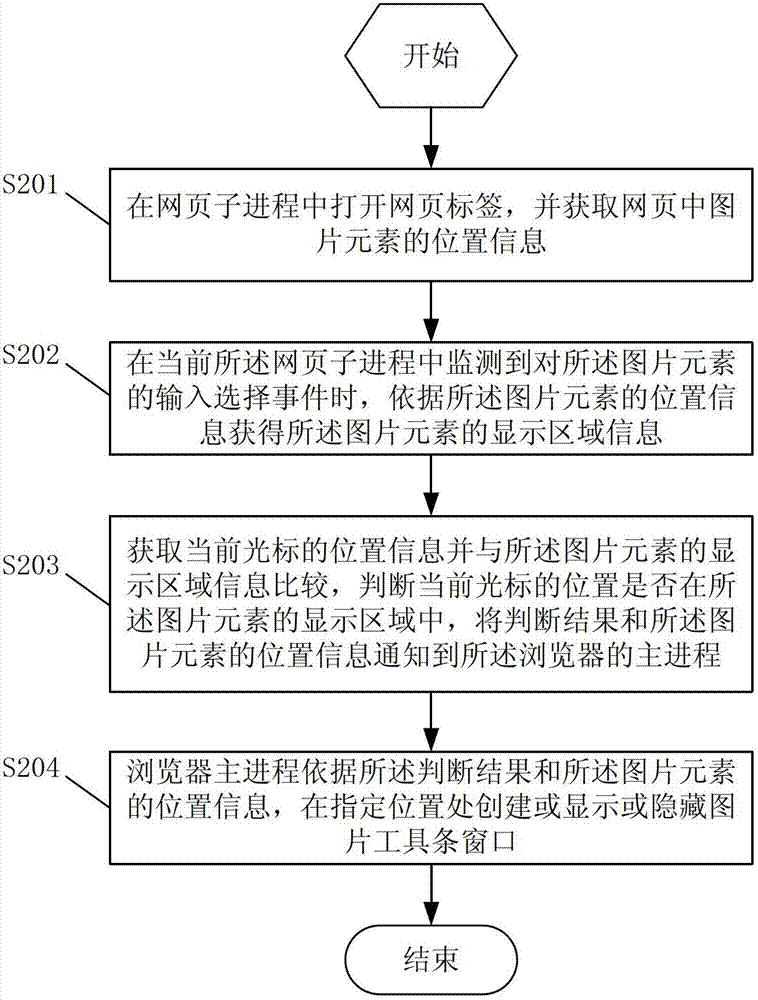
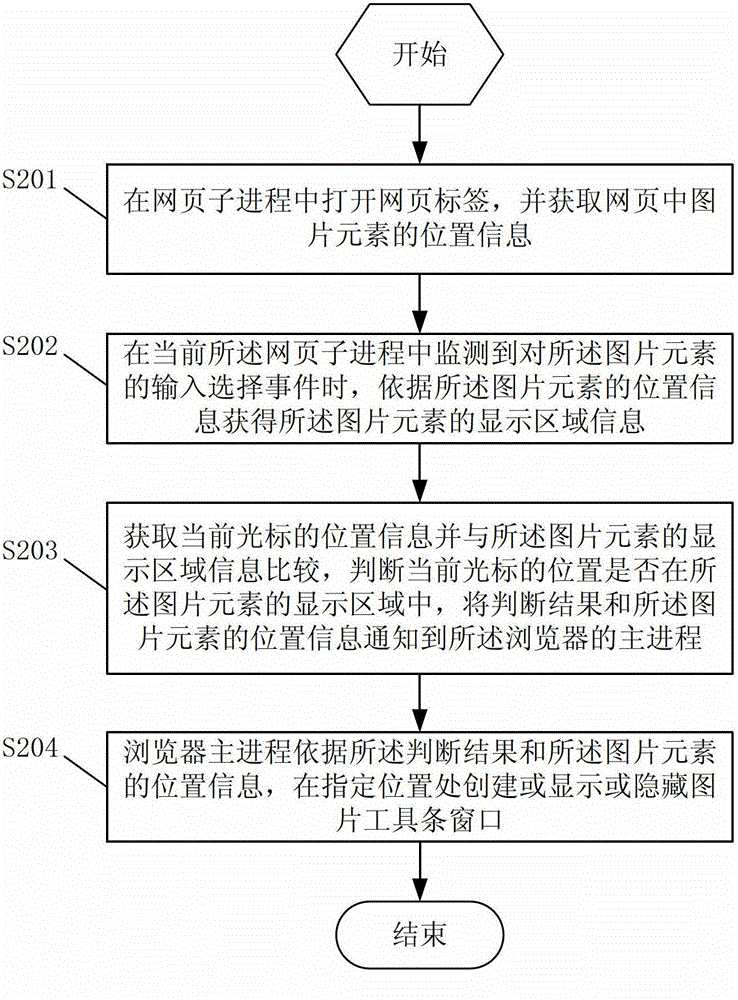
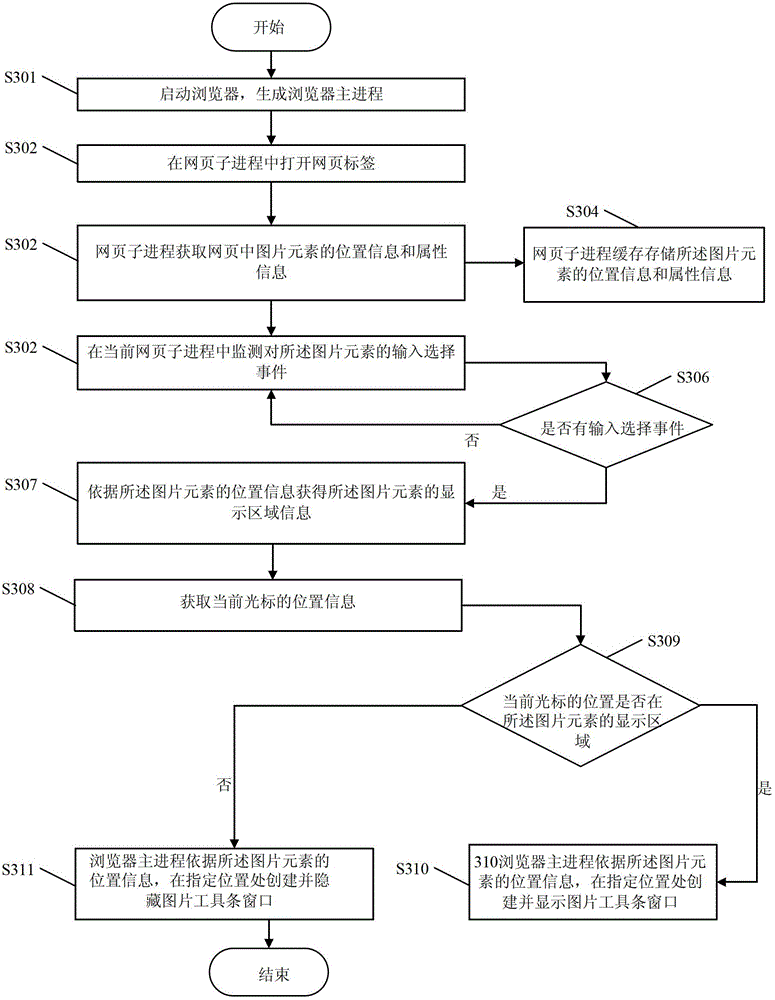
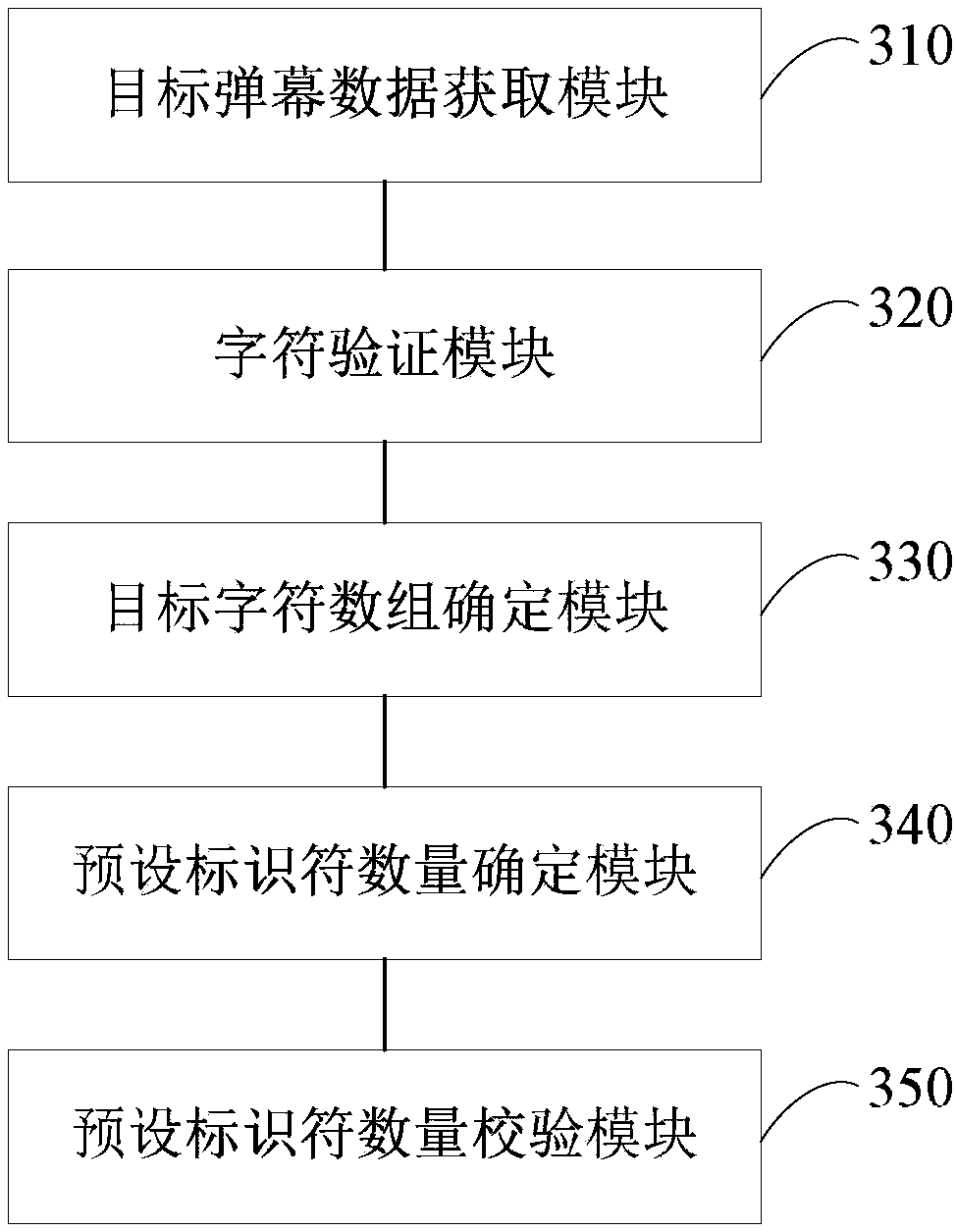
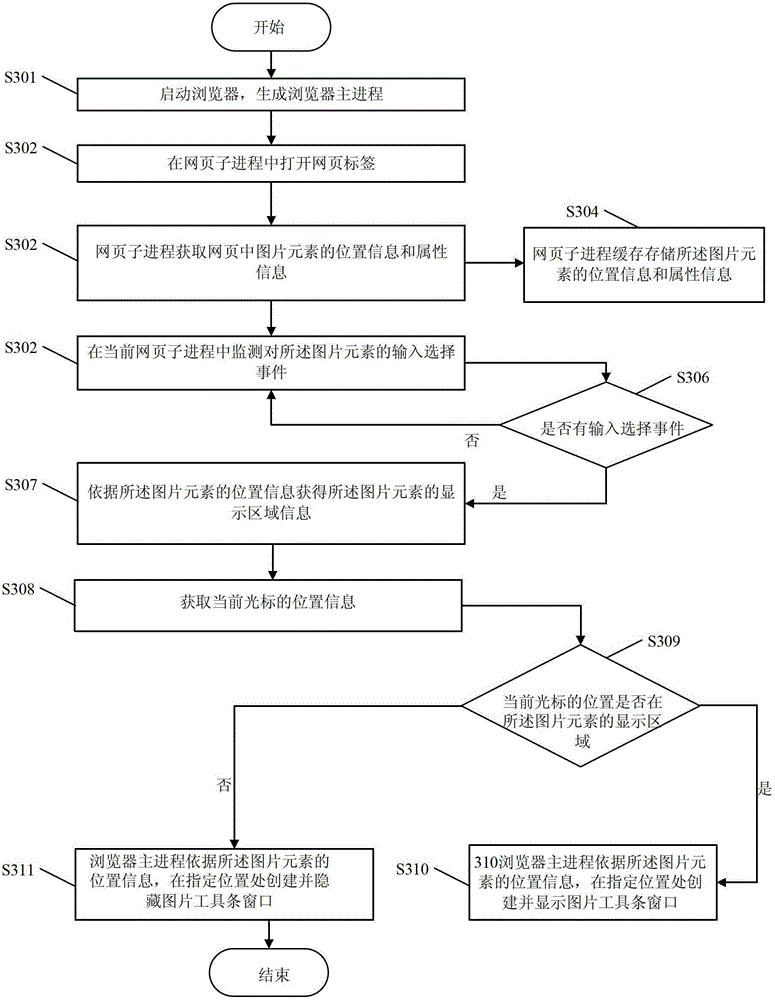
Method and device for loading picture toolbar window
ActiveCN103034686AAvoid problems like crashesImprove processing efficiencySpecial data processing applicationsInput selectionComputer graphics (images)
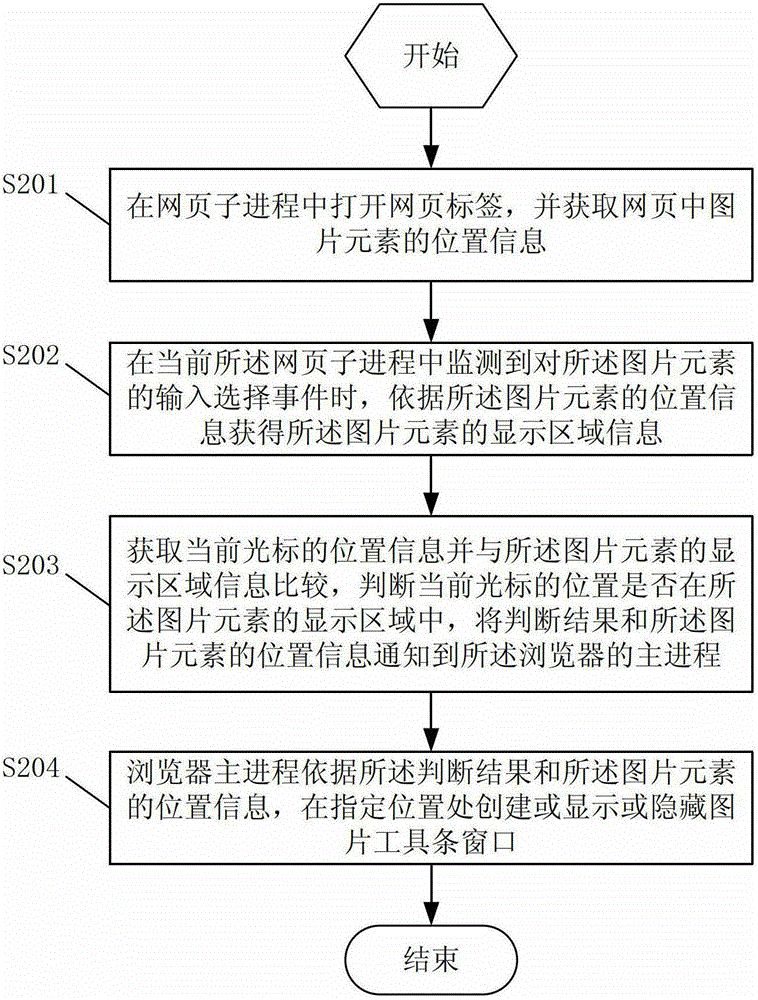
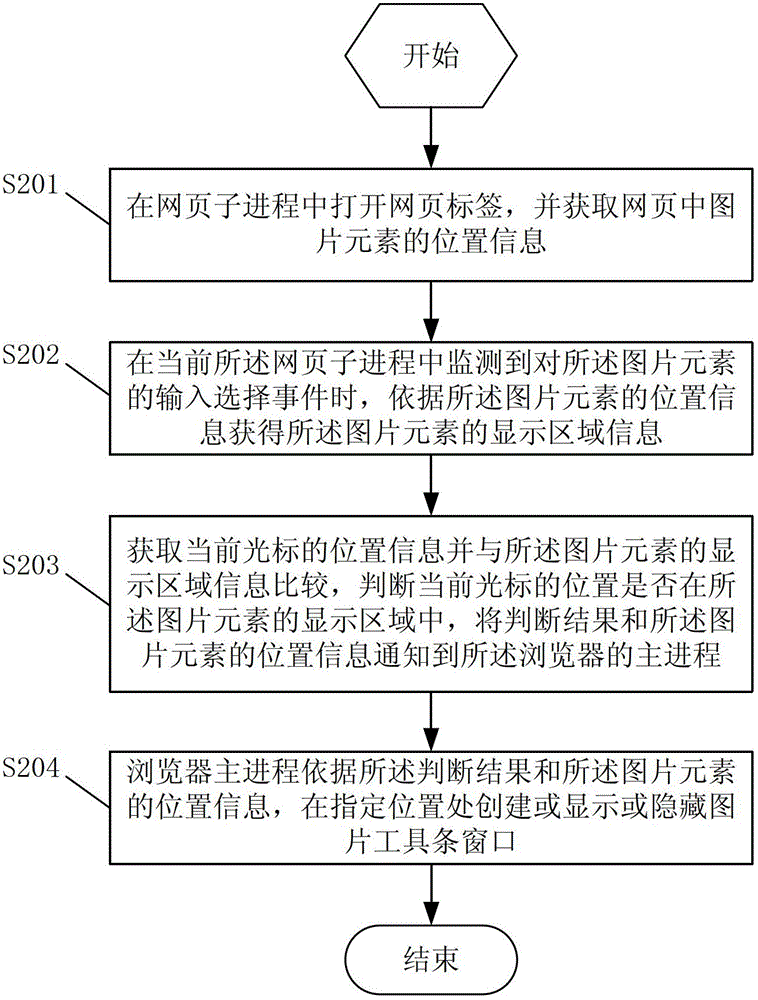
The invention discloses a method and a device for loading a picture toolbar window. The method comprises the following steps that a webpage label is opened in a webpage subprocess, and the position information of picture elements in a webpage is obtained; when an input selection event of the picture elements is monitored in the current webpage subprocess, the display region information of the picture elements is obtained according to the position information of the picture elements; the position information of the current cursor is obtained and is compared with the display region information of the picture elements, whether the position of the current cursor is in the display region of the picture elements or not is judged, and judgment results and the position information of the picture elements are notified to the host process of a browser; and the host process of the browser creates or displays or hides the picture toolbar window in the specified position according to the judgment results and the position information of the picture elements. The method and the device solve the loading misjudgment phenomenon of the picture toolbar window when the relevant processing of the picture elements is executed in the browser.
Owner:BEIJING QIHOO TECH CO LTD
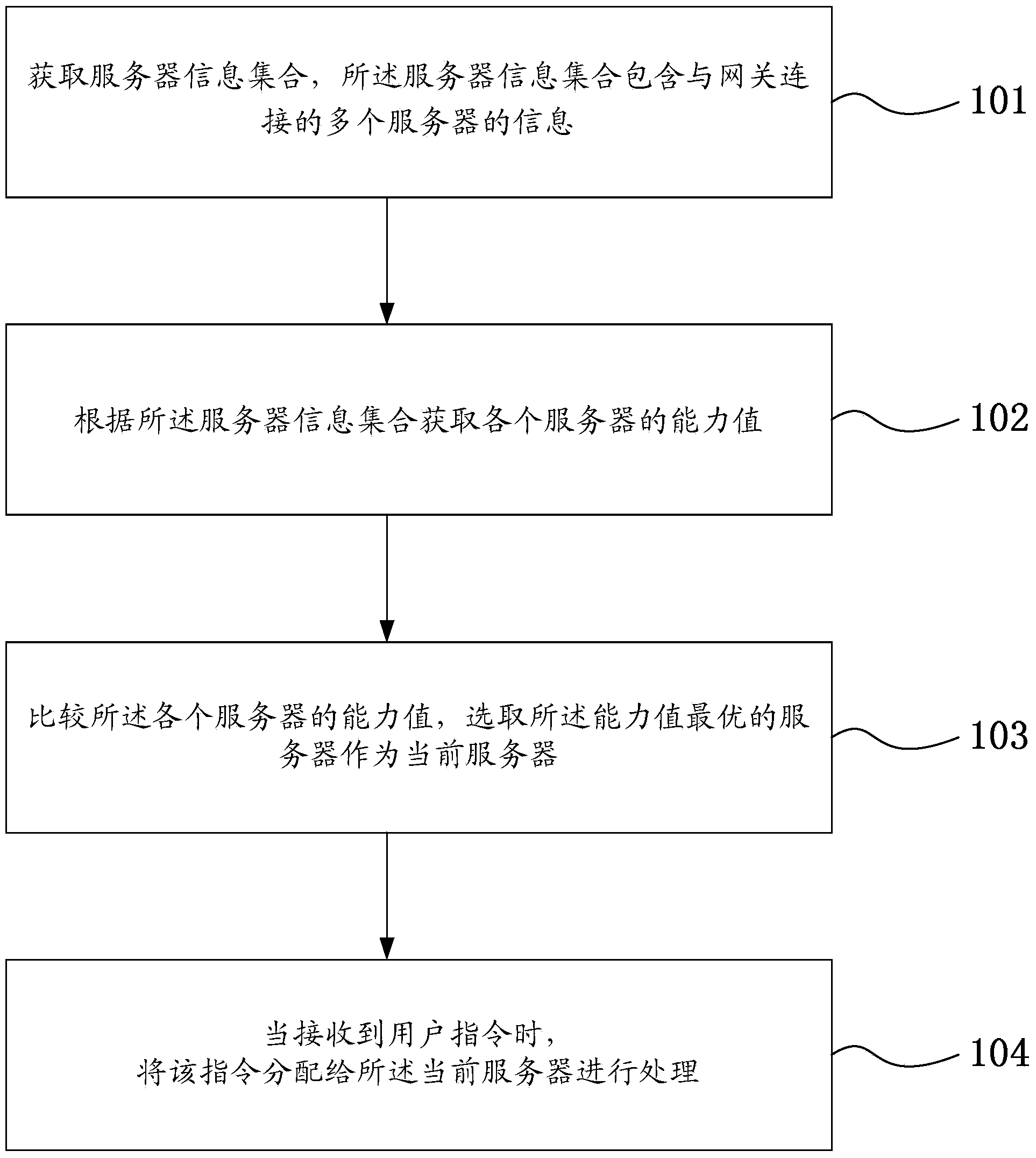
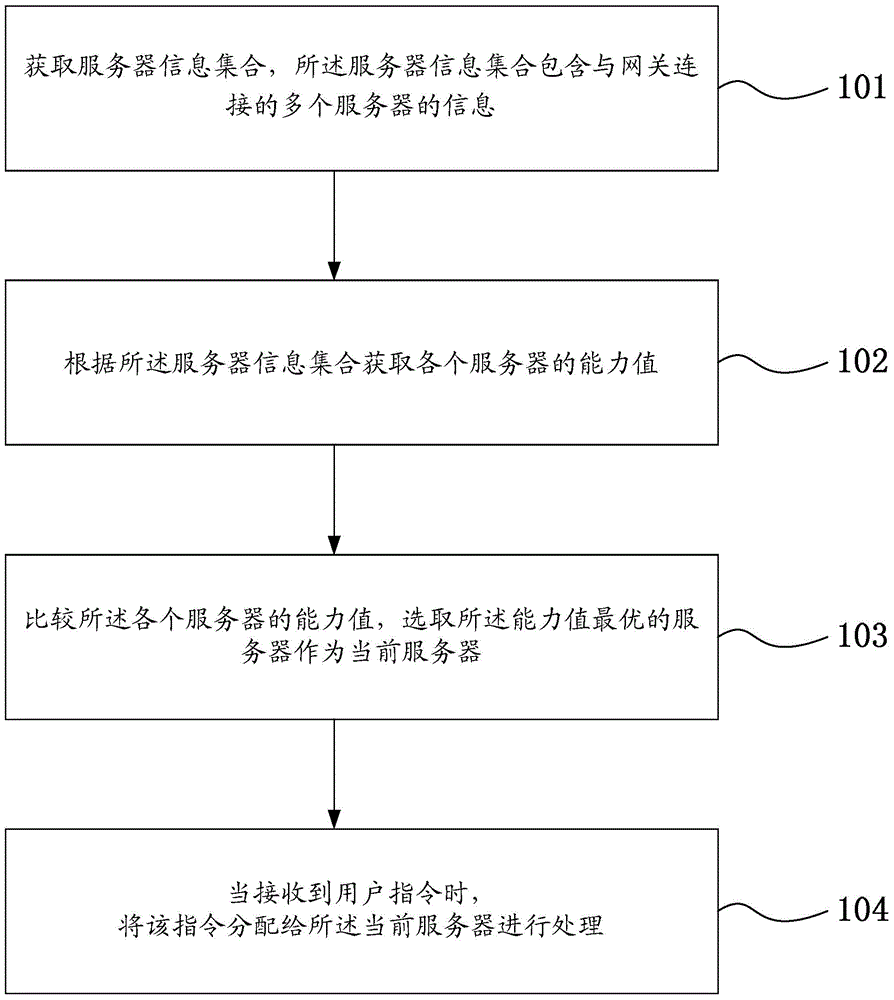
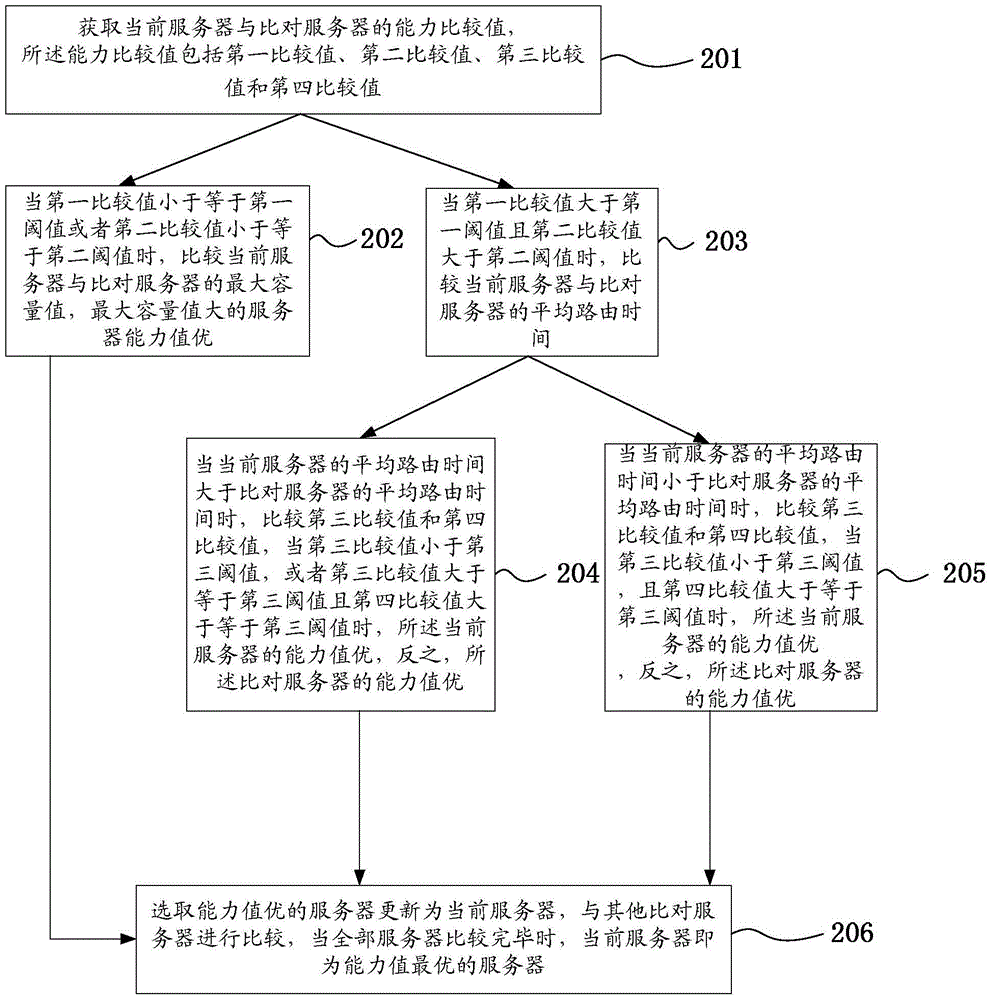
Network scheduling method and gateway
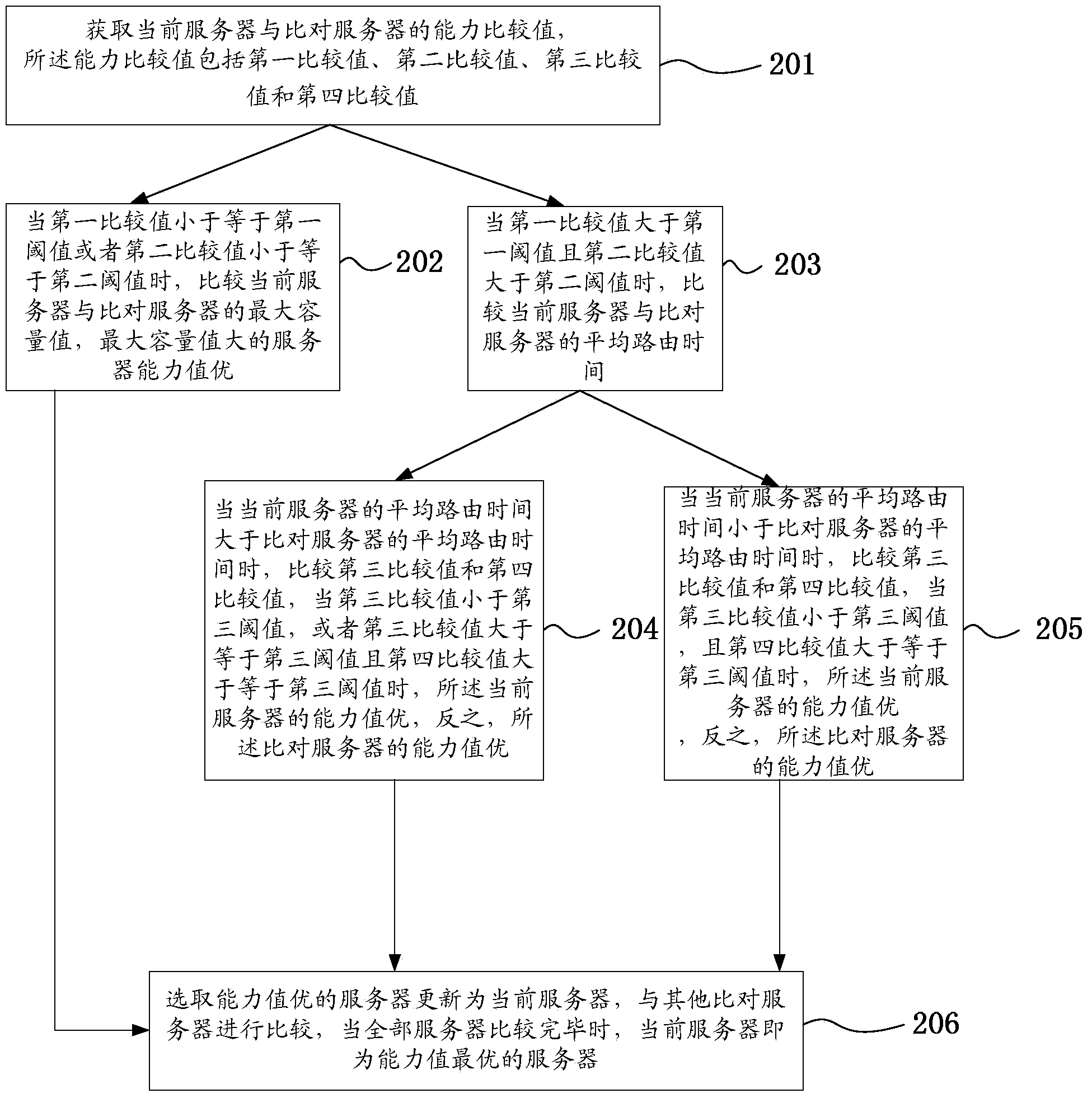
ActiveCN103763206AAbility value is fast and accurateQuick pickNetwork connectionsCapacity valueProcess information
The invention discloses a network scheduling method and a gateway. The method comprises the steps that a server information set is obtained, wherein the server information set comprises information of multiple servers connected to the gateway; the capacity values of all the servers are obtained according to the server information set; the capacity values of all the servers are compared, and the server with the optimal capacity value is selected as a current server; when a user instruction is received, the instruction is assigned to the current server to be processed. According to the network scheduling method and the gateway, by means of obtaining the capacity values of all the servers of the gateway, the server with the optimal capacity value is selected as the current server, servers with large capacity values can be selected dynamically to process information, server resources of the gateway can be reasonably optimized and allocated, the overload phenomenon occurring to certain servers can be prevented from occurring, and the processing efficiency on information by the gateway can be improved.
Owner:北京柏安科技有限公司
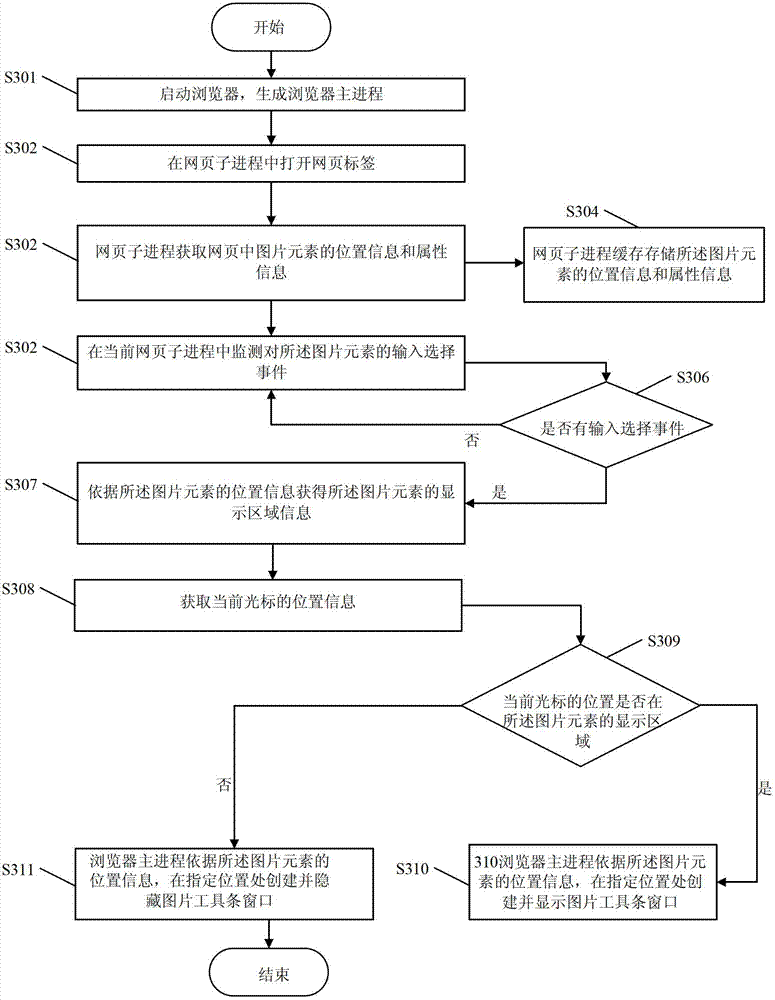
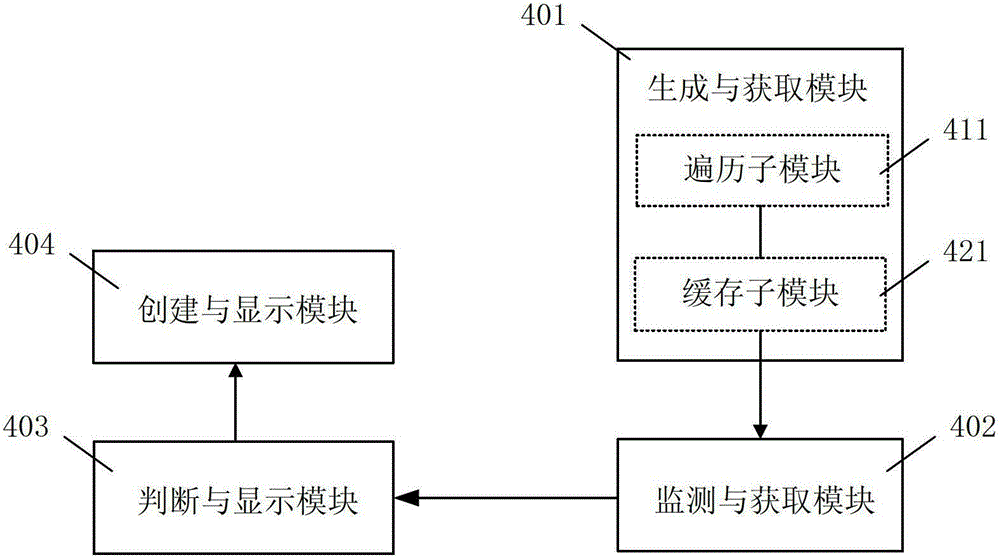
Method and device for loading picture toolbar window
ActiveCN102981876AAvoid problems like crashesImprove processing efficiencyProgram loading/initiatingComputer graphics (images)Start up
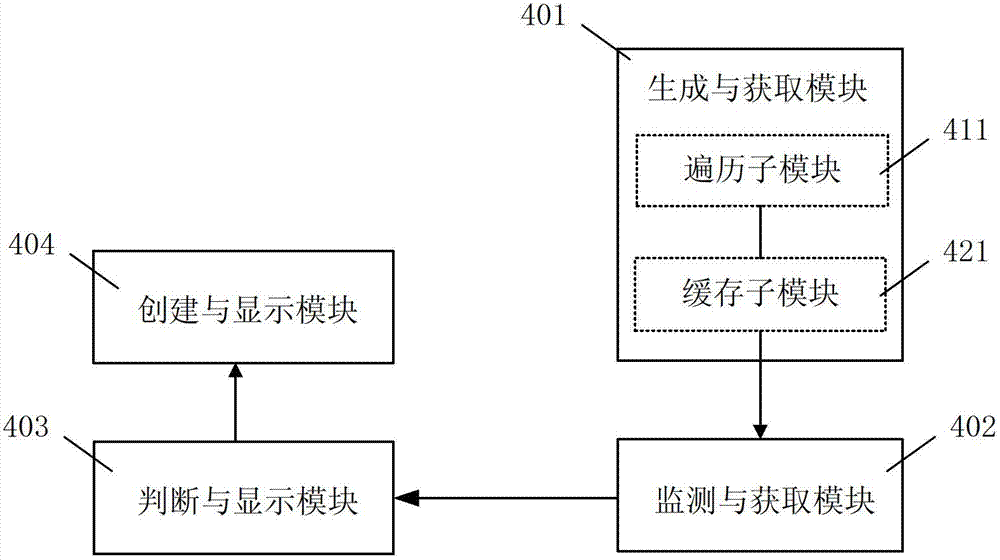
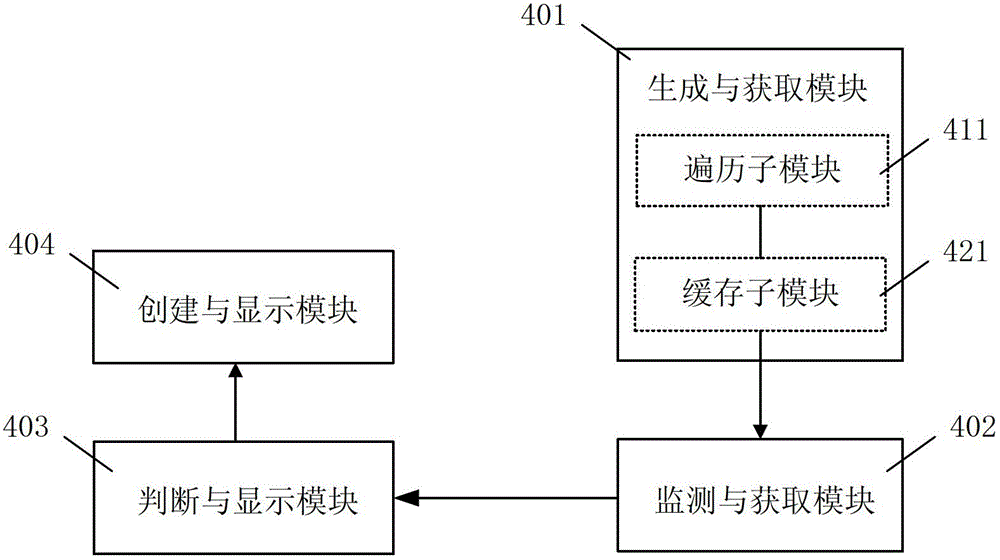
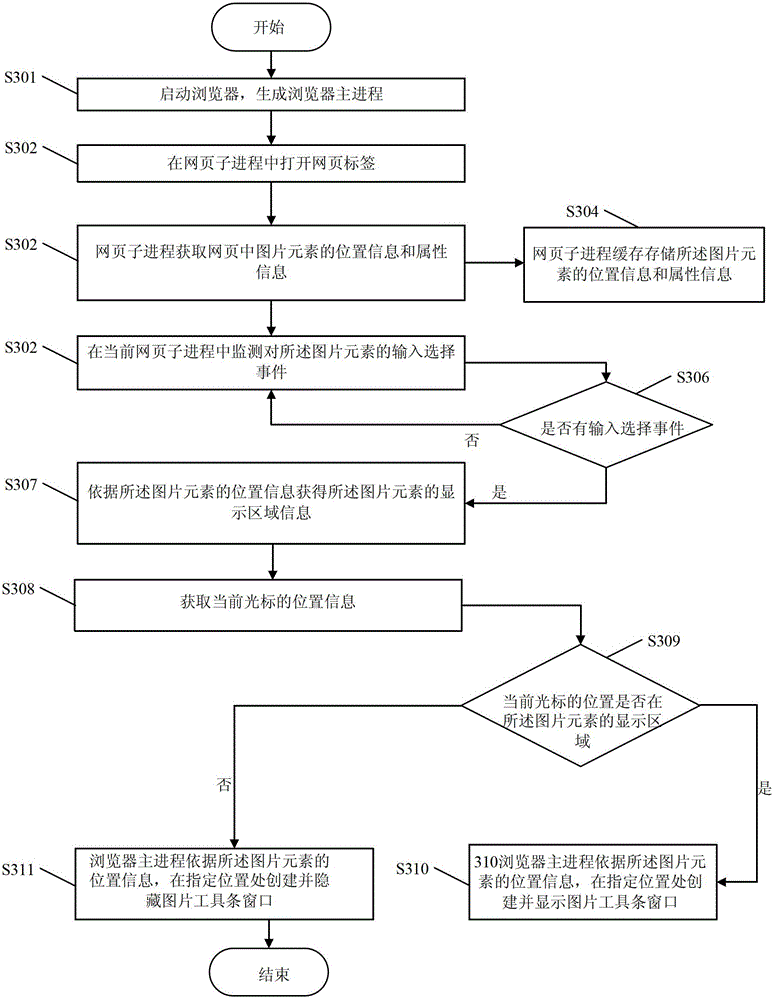
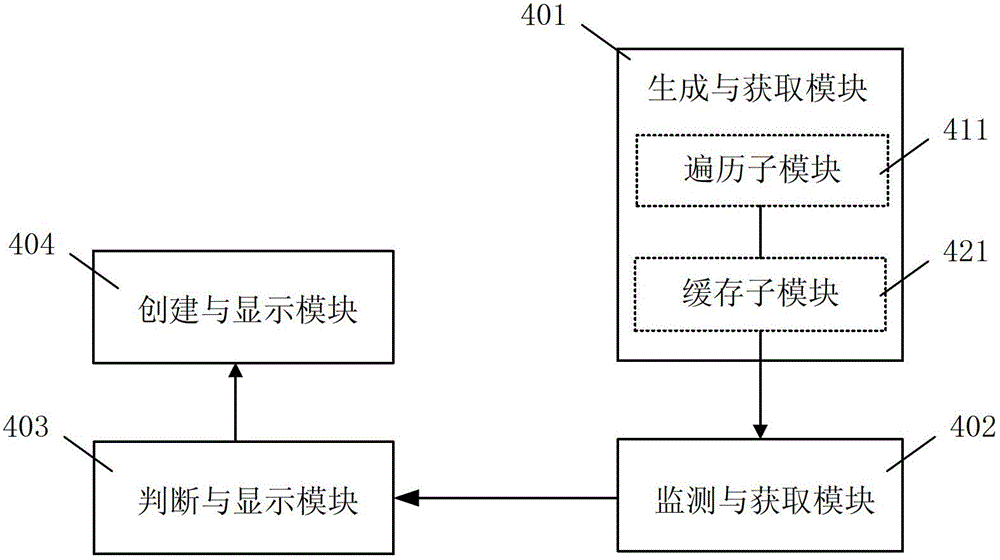
The invention discloses a method and a device for loading a picture toolbar window. The device comprises a generating and acquiring module, a monitoring and acquiring module, a judging and transmitting module and a creating and displaying module, and the method is characterized in that when a browser is started up, a master browser process which corresponds to one or more webpage sub-processes is generated, and the picture toolbar window of the master browser process is used interactively among one or more webpage sub-processes. Due to the adoption of the method and the device, the phenomenon of misjudgment on loading of picture toolbar windows of the browser during relevant processing of picture elements is avoided.
Owner:BEIJING QIHOO TECH CO LTD
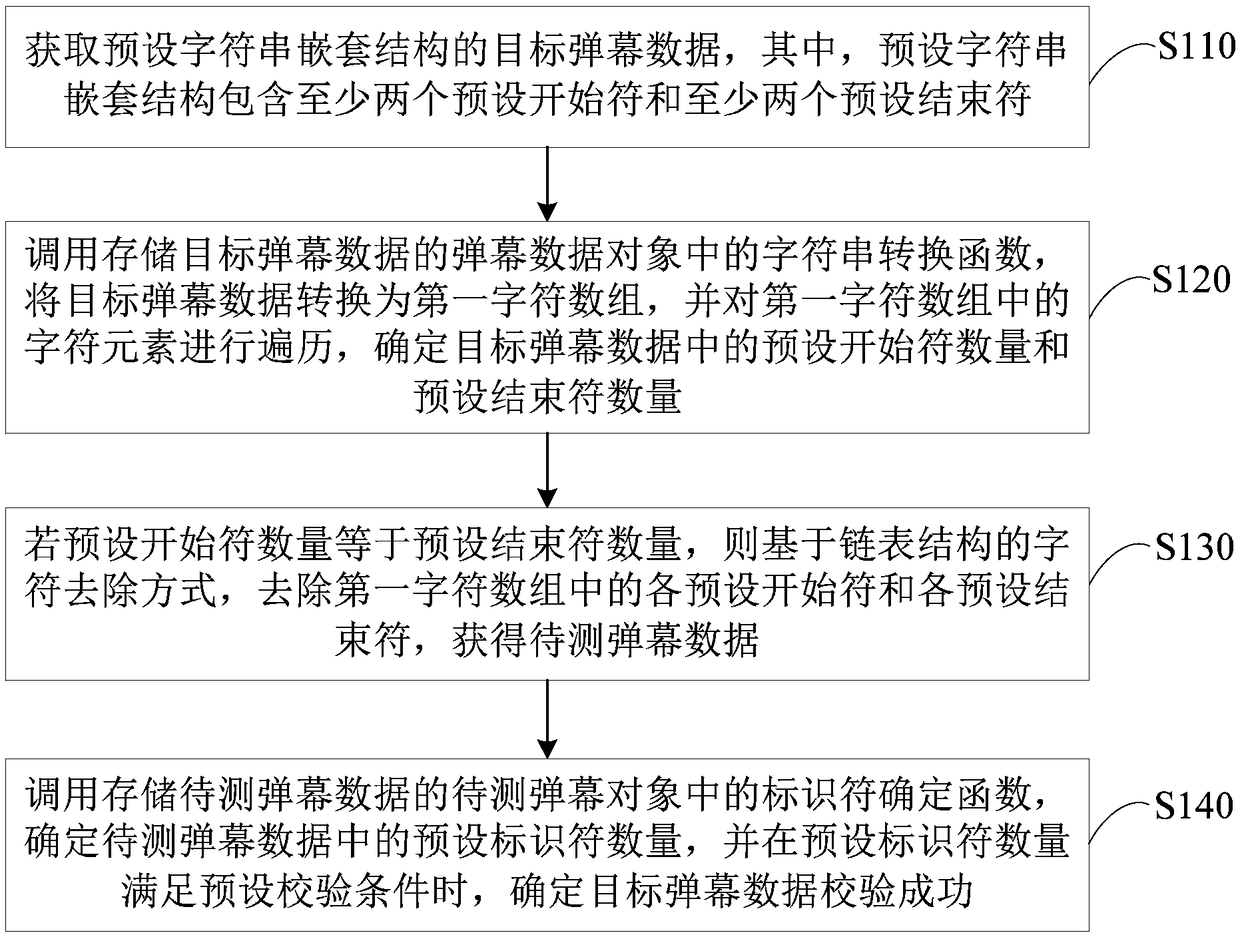
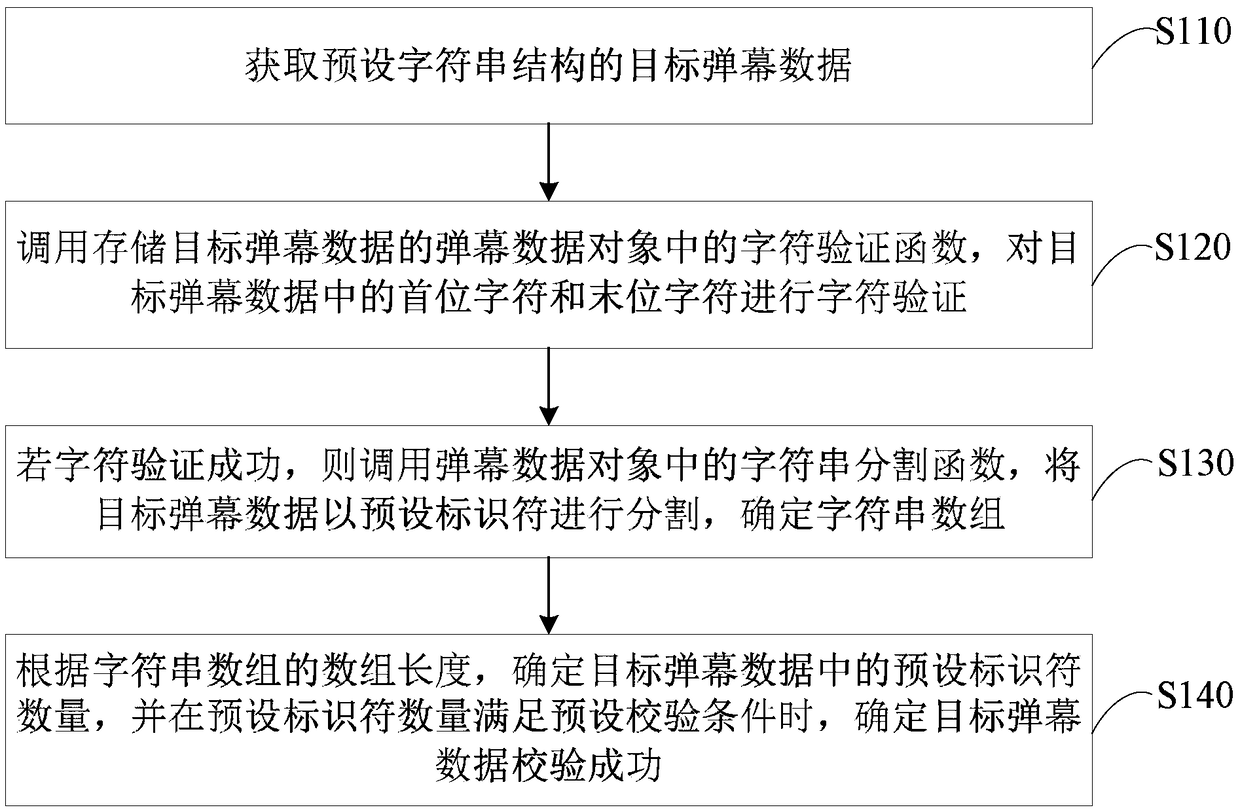
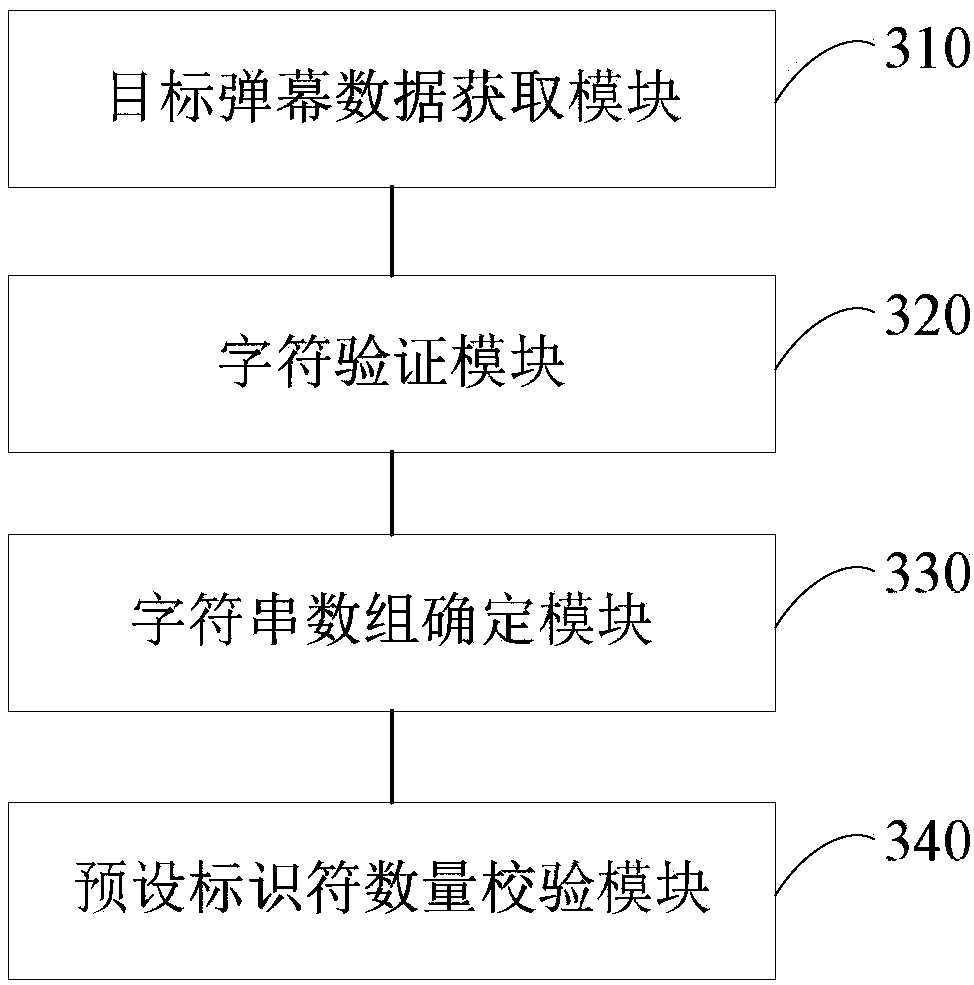
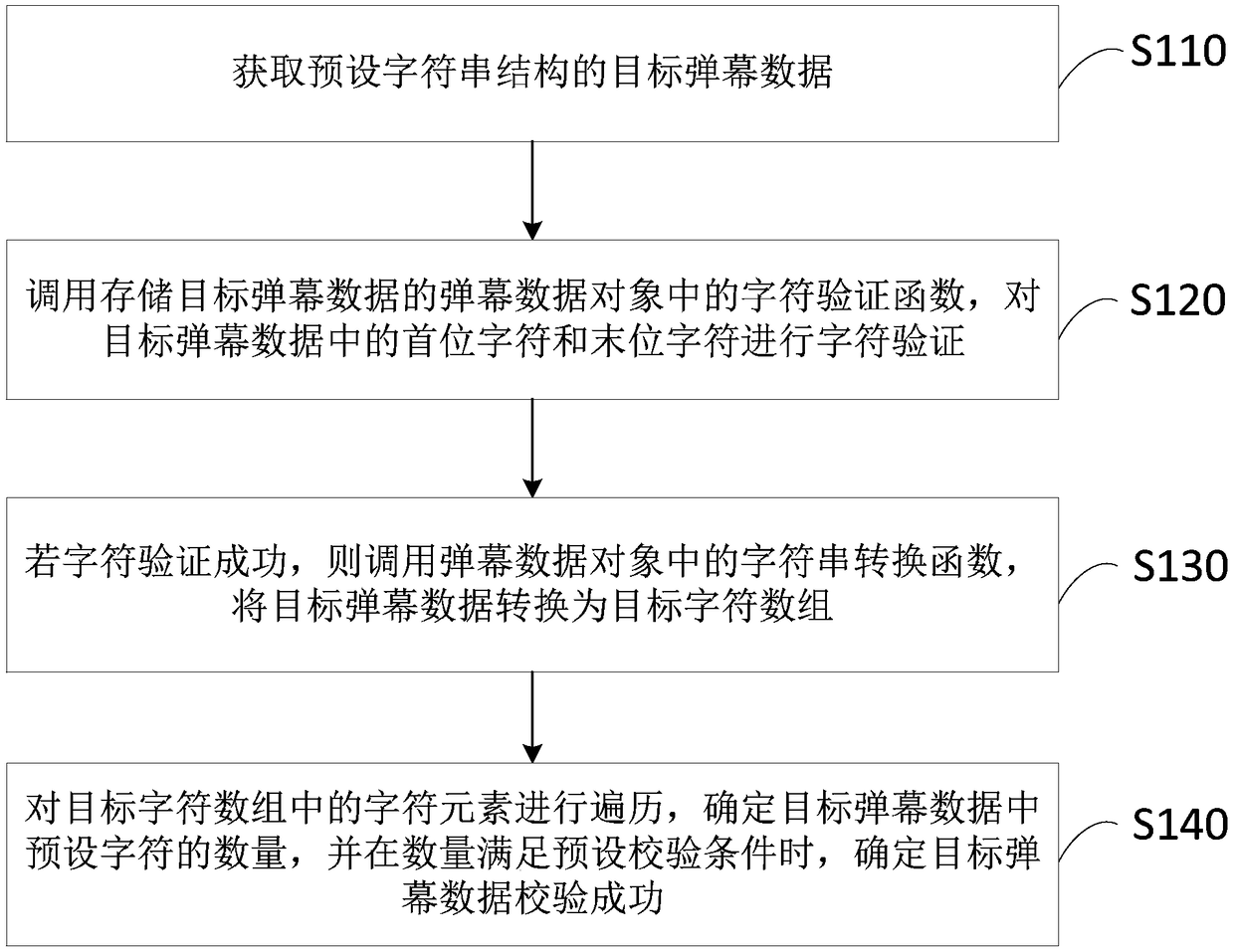
Barrage verification method, device, terminal and storage medium based on character segmentation
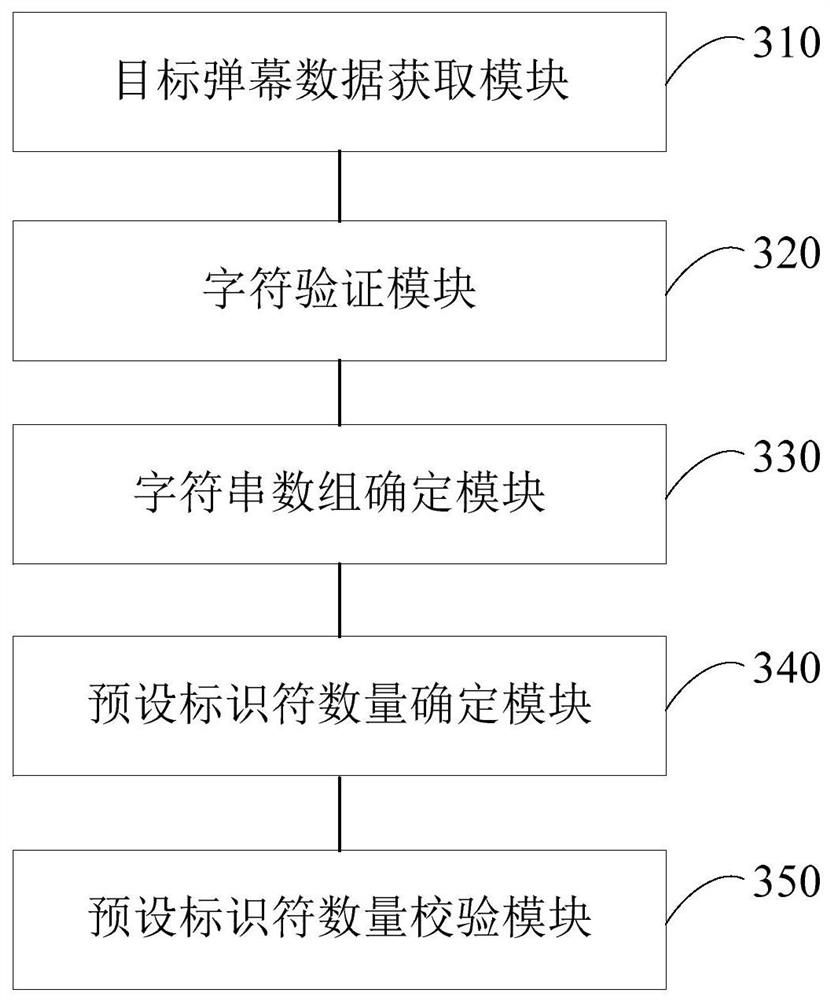
ActiveCN109299719AImprove test efficiencyAvoid problems like crashesCharacter and pattern recognitionArray data structureProjectile
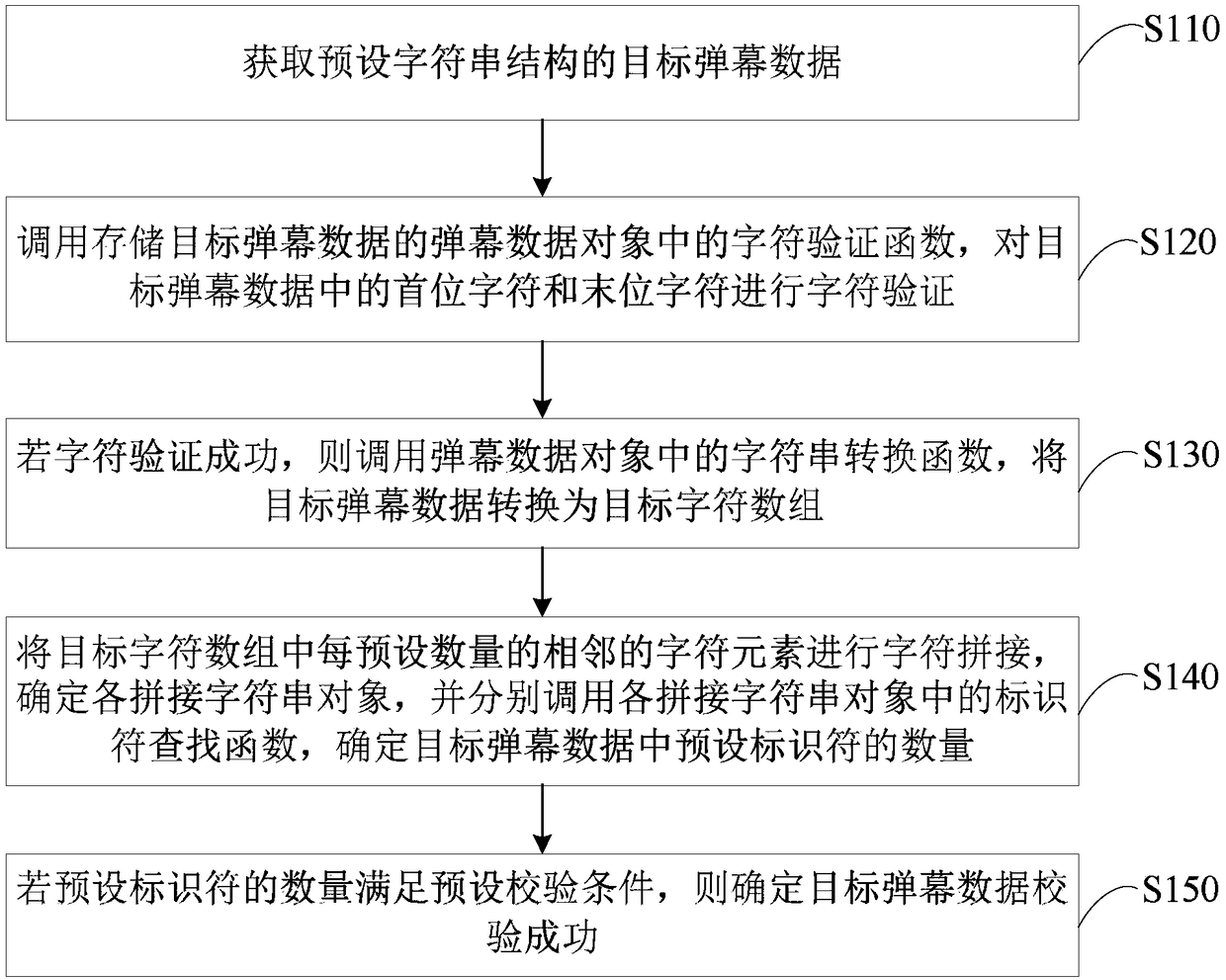
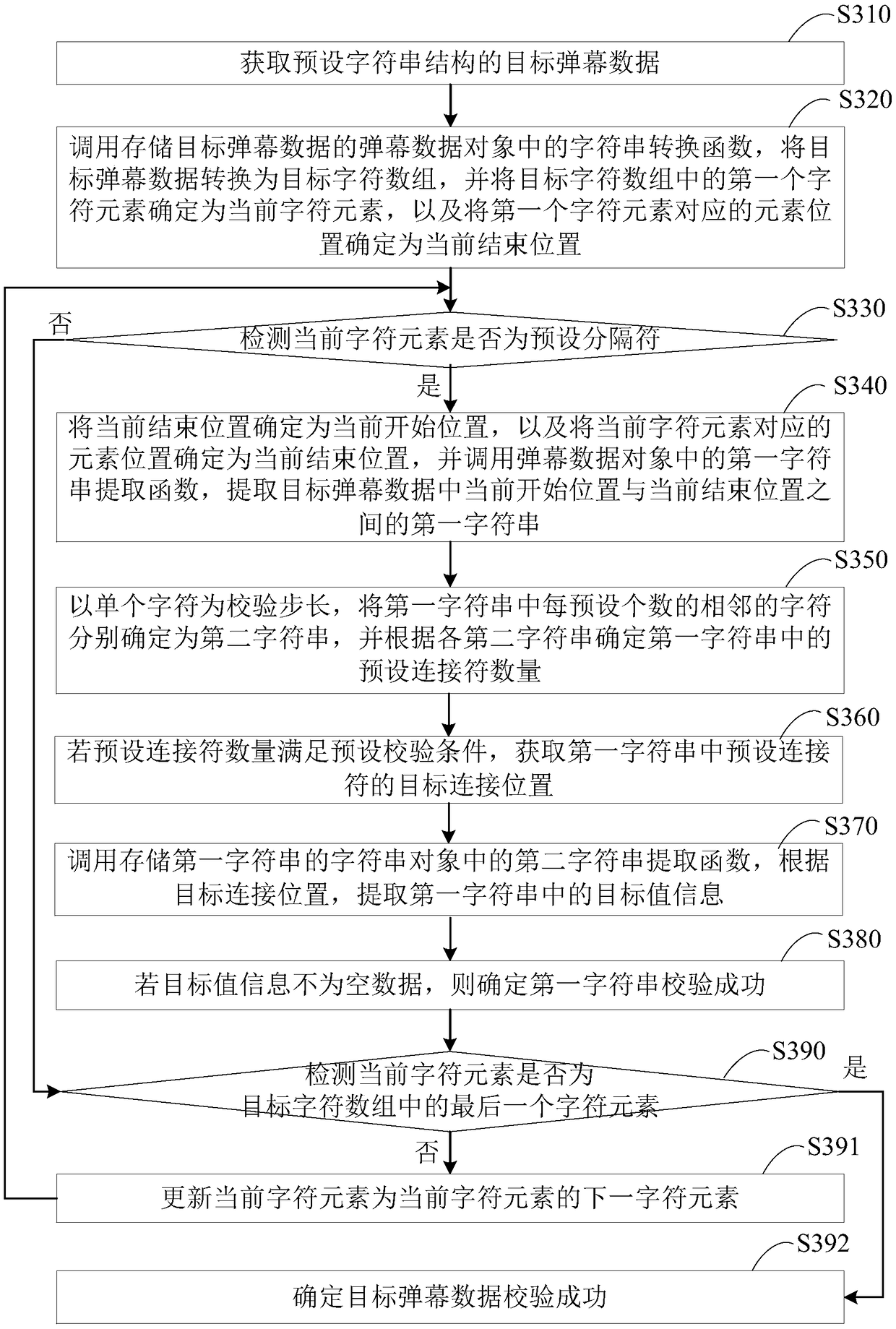
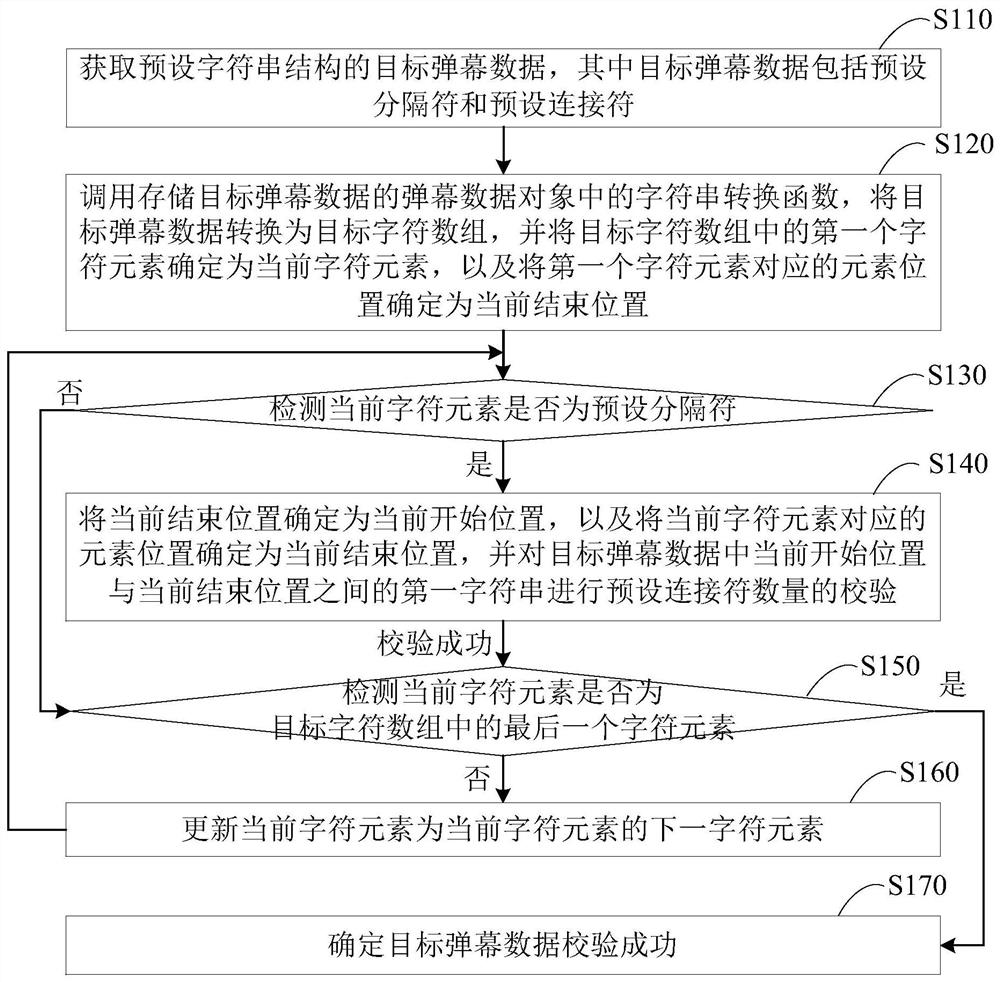
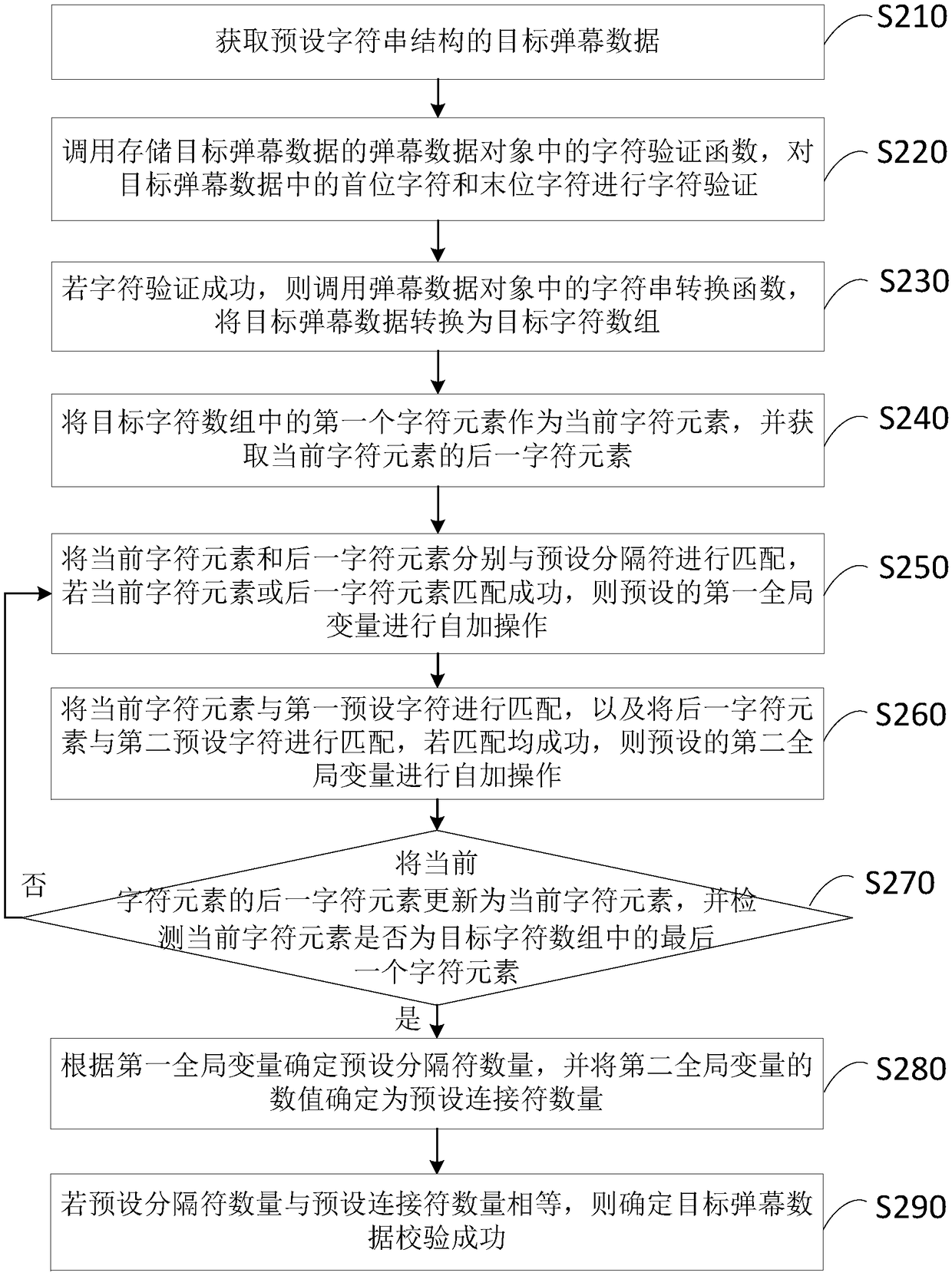
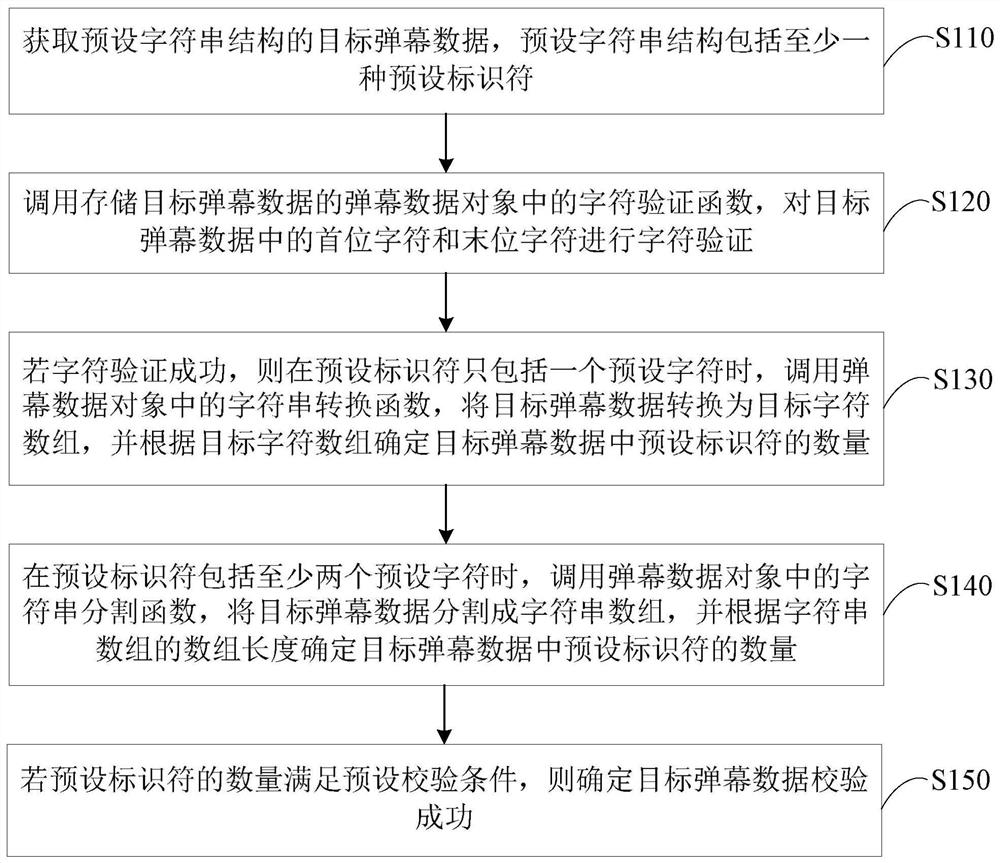
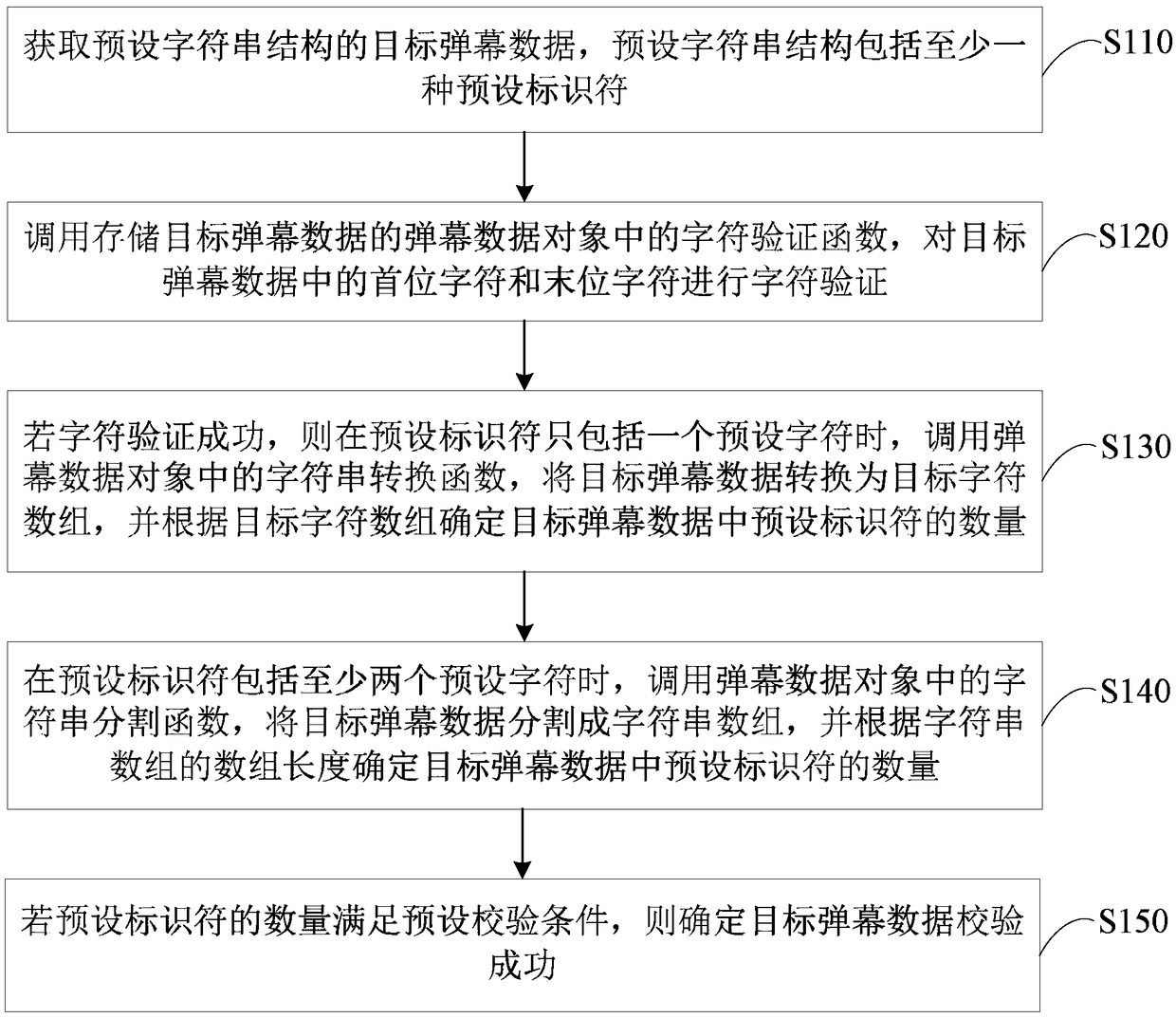
The embodiment of the invention discloses a barrage verification method, a device, a terminal and a storage medium based on character segmentation. The method comprises the following steps of: acquiring target barrage data of a preset string structure; The character verification function is called to verify the character of the target barrage data. If the character verification is successful, thecharacter string segmentation function is called, the target barrage data is segmented with a preset separator, the first character string array is determined, and each first character string elementin the first character string array is stored in a corresponding character string object. Calling a string splitting function in each string object, splitting each first string element with a preset connector, and determining each second string array; If the array length of each second string array satisfies the preset check condition, it is determined that the target barrage data check is successful. Through the technical proposal of the embodiment of the invention, the integrity of the projectile screen data can be checked, thereby ensuring that the projectile screen data can be normally analyzed.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
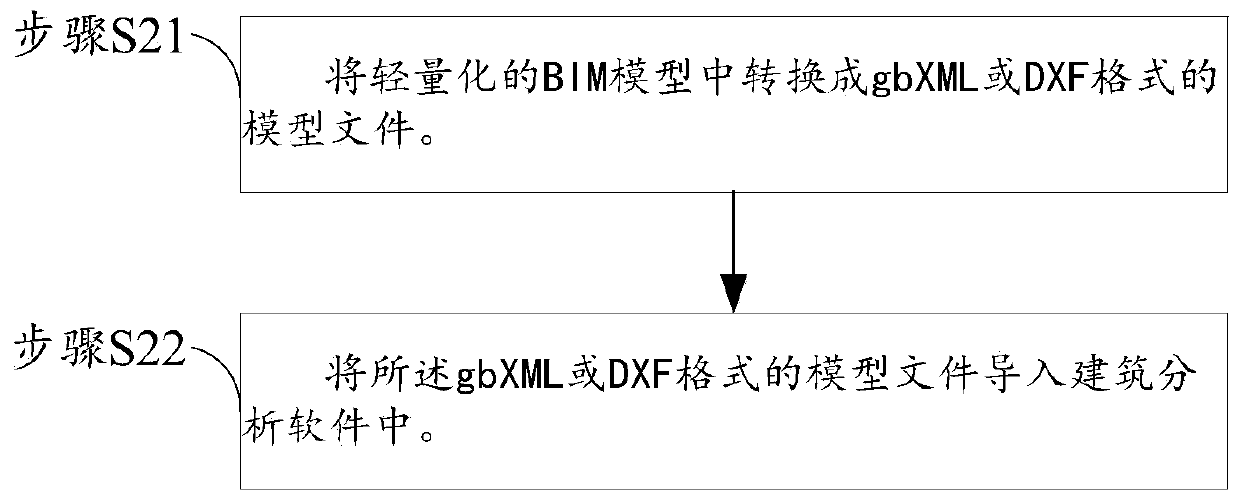
Building analysis method and system based on lightweight BIM model
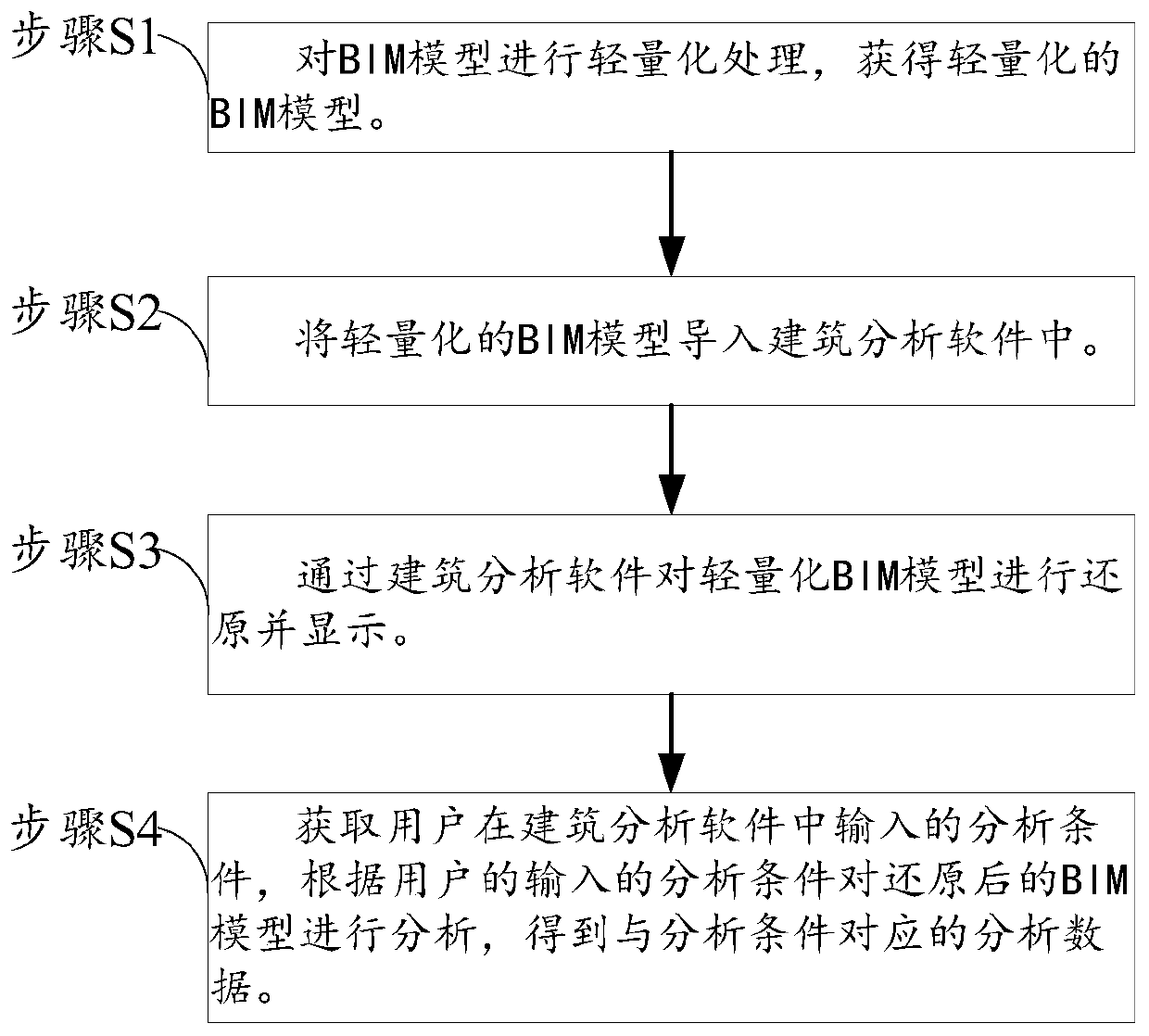
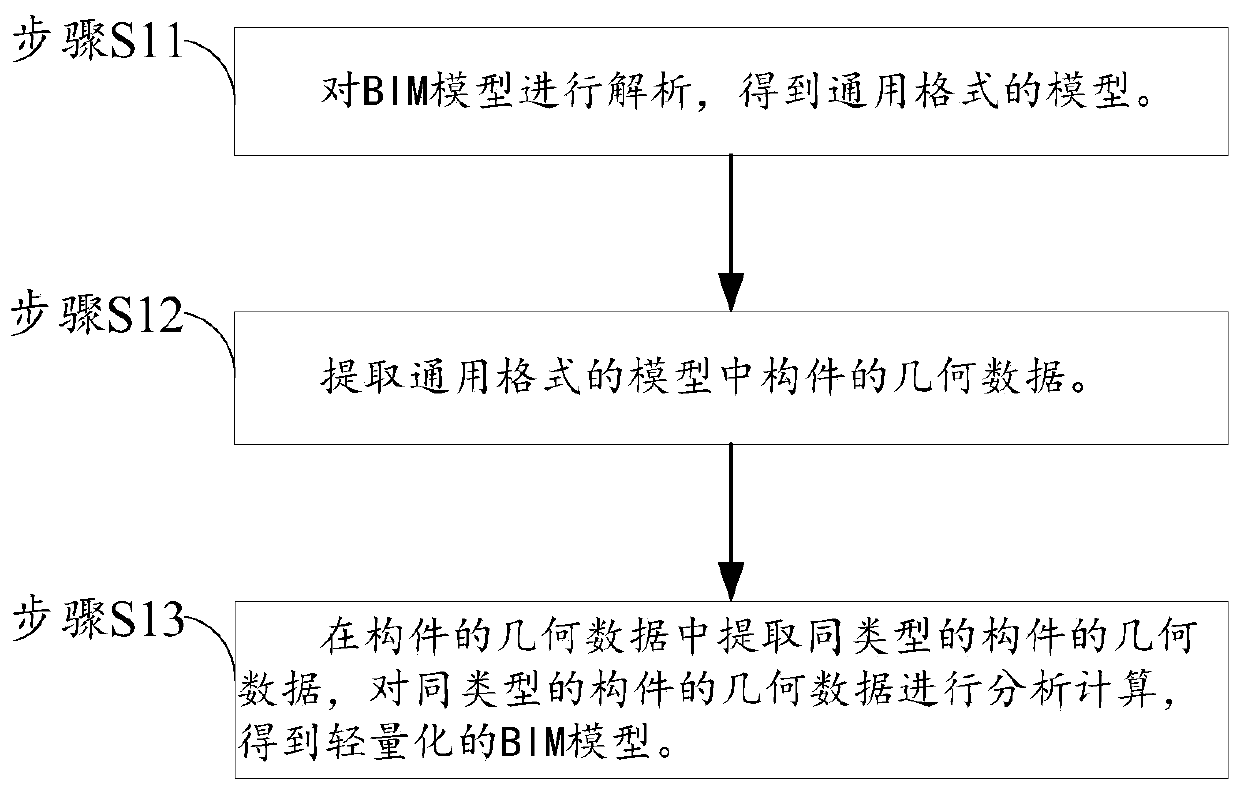
PendingCN111080791AImprove analysis efficiencyAvoid CatonGeometric CADDesign optimisation/simulationAnalysis methodInformation model
Owner:深圳市万翼数字技术有限公司
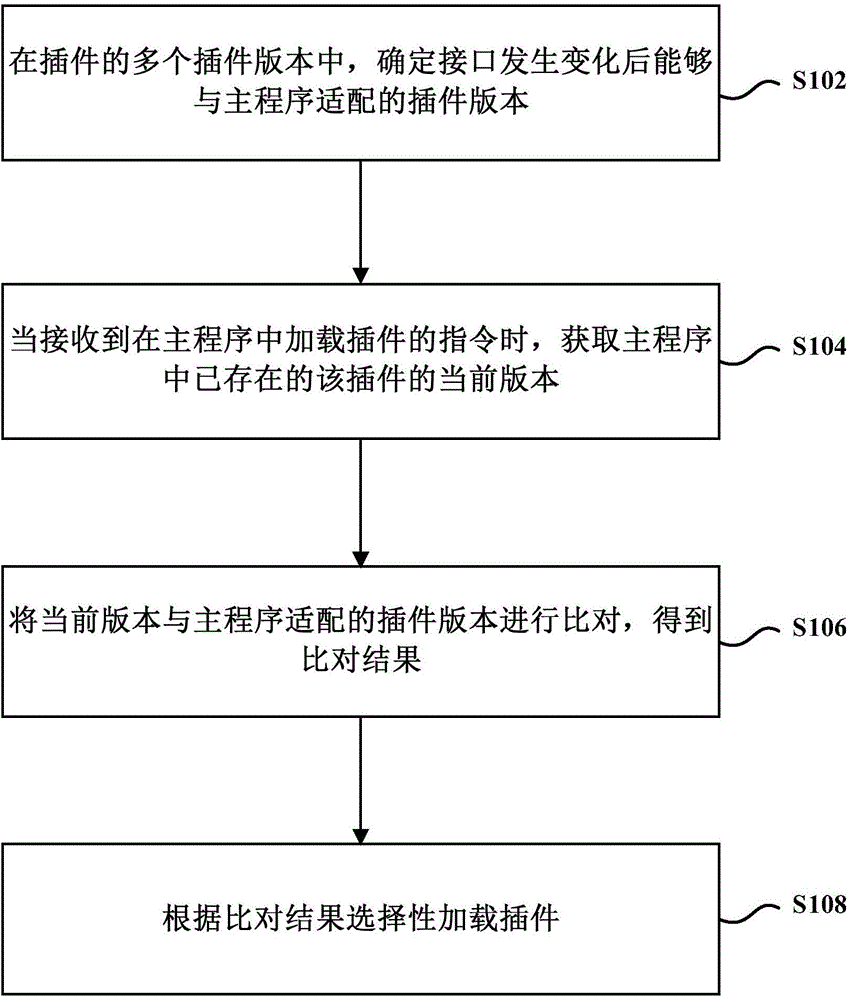
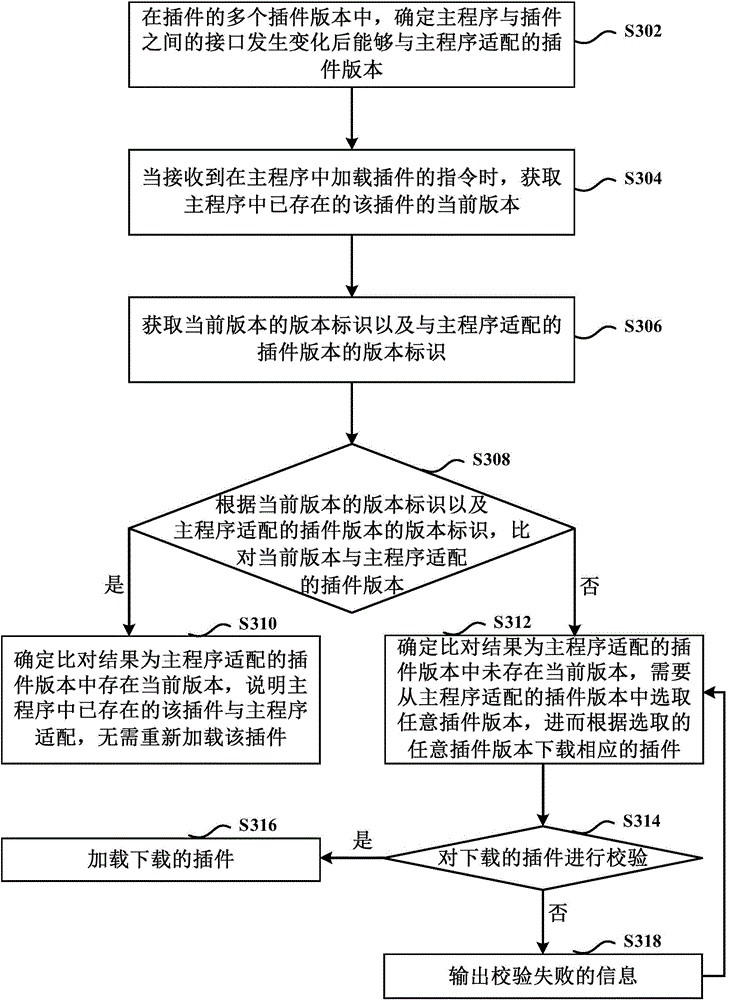
Plug-in loading method, device and equipment
ActiveCN106155709AImprove the comparison rateAvoid incompatibilityProgram loading/initiatingComputer engineering
Owner:北京世界星辉科技有限责任公司
Method and device for verifying barrage data and terminal
ActiveCN109348304AAvoid problems like crashesImprove test efficiencyNatural language data processingSelective content distributionArray data structureAlgorithm
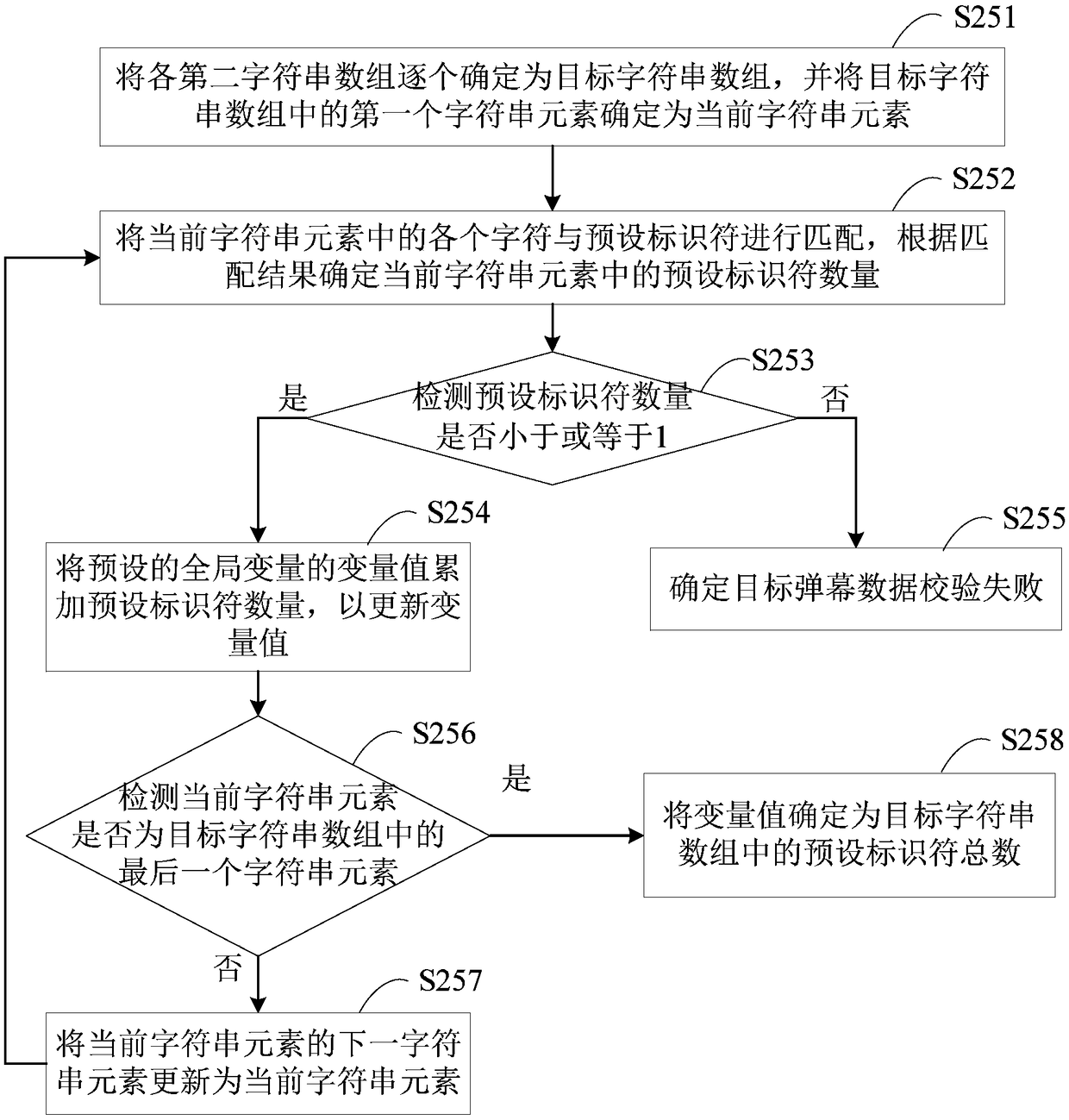
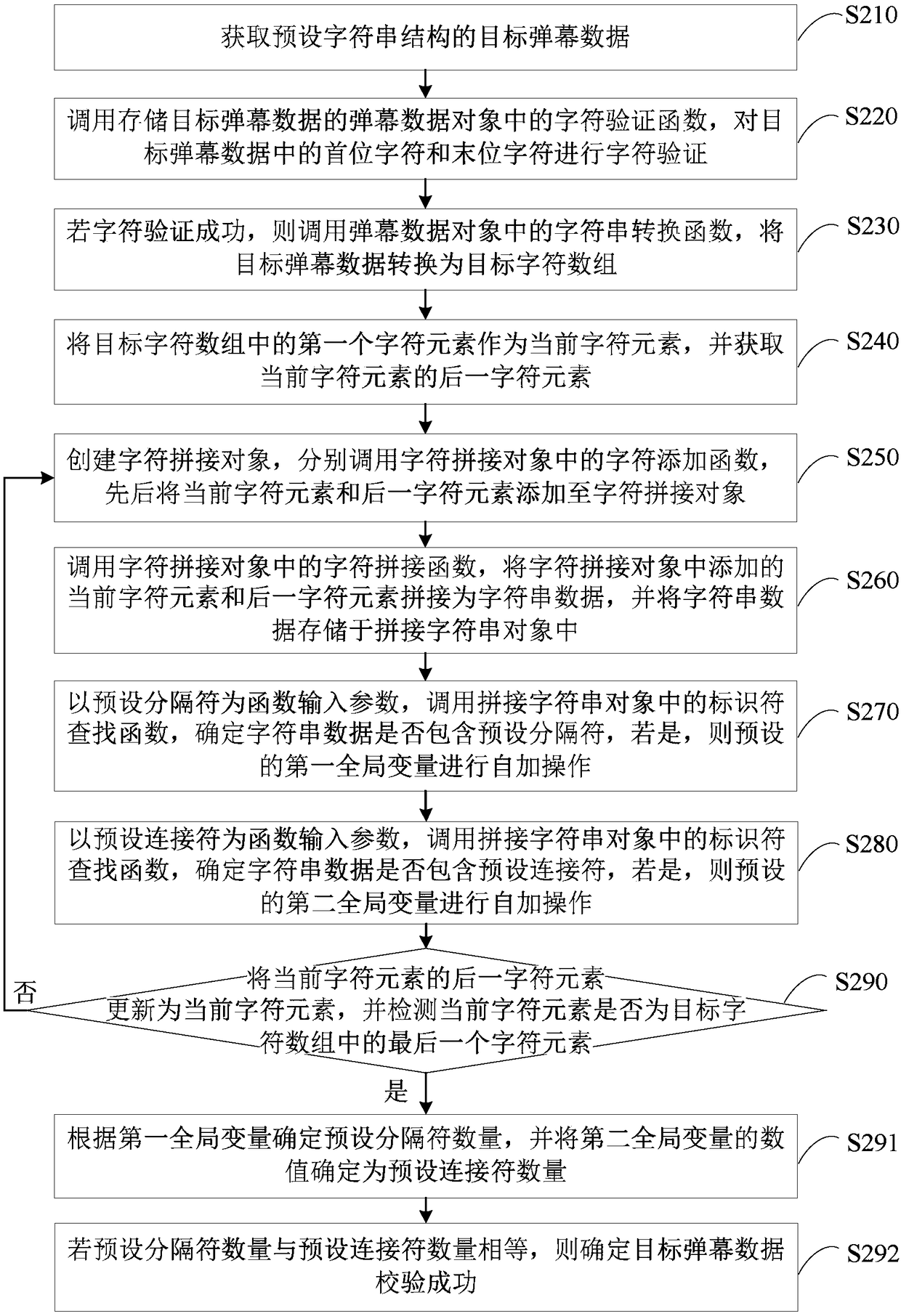
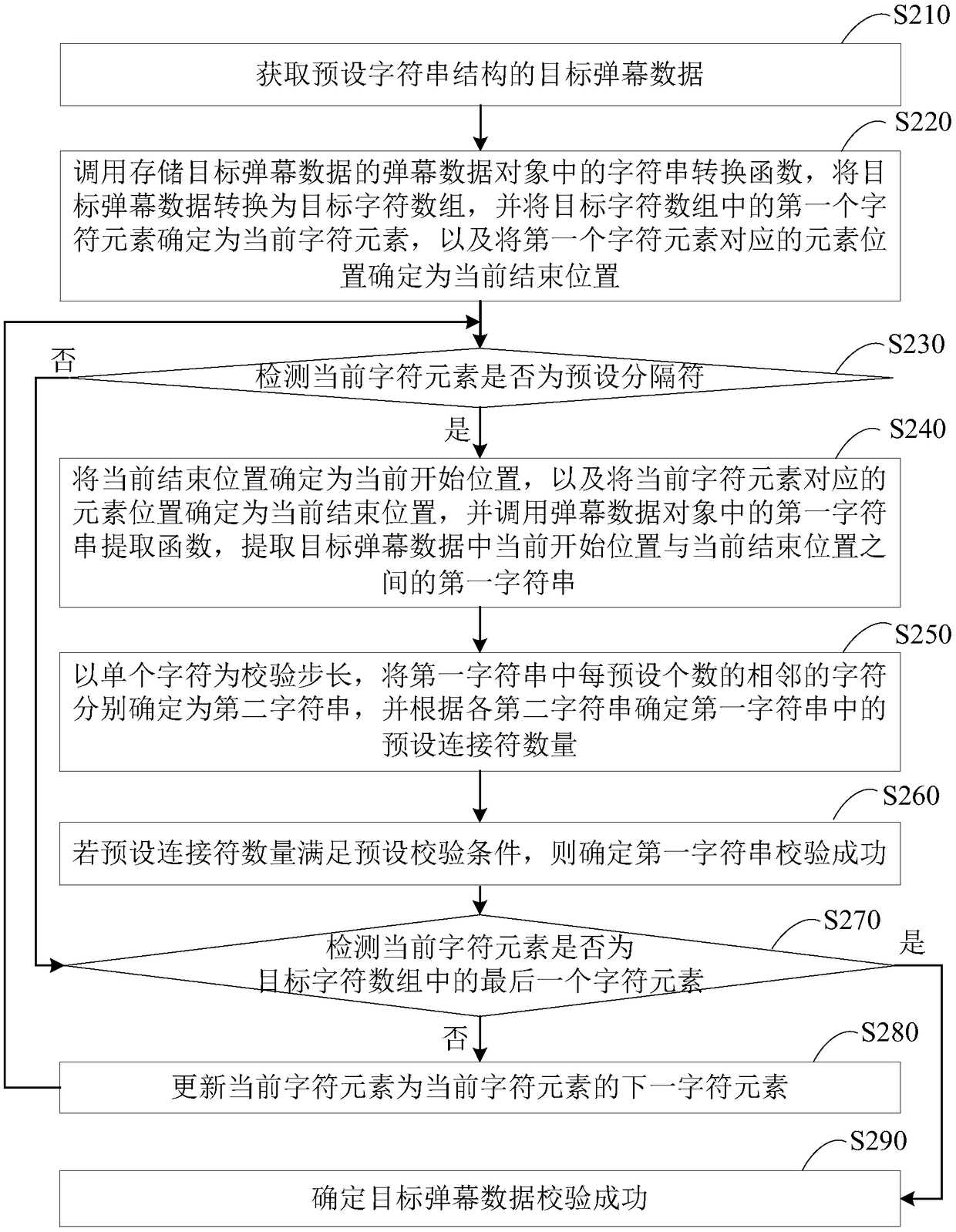
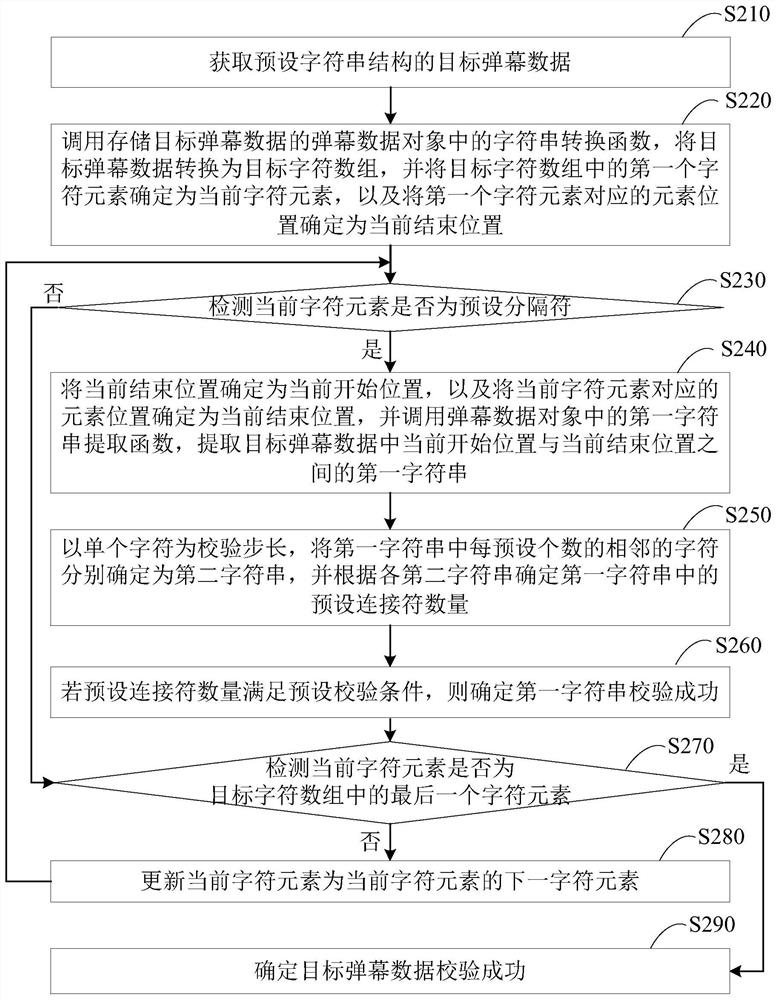
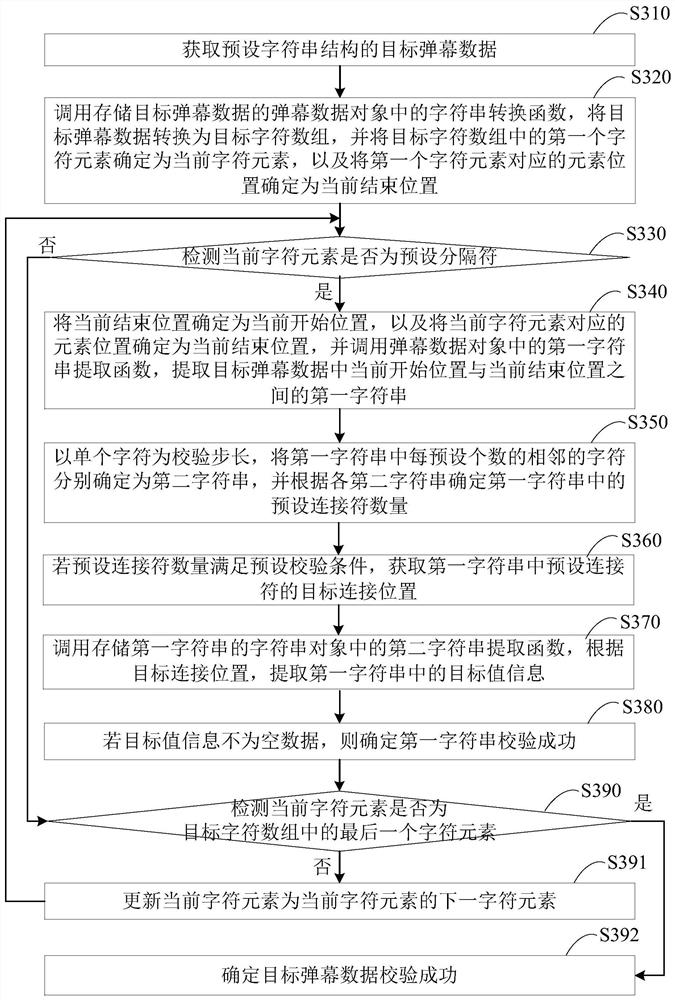
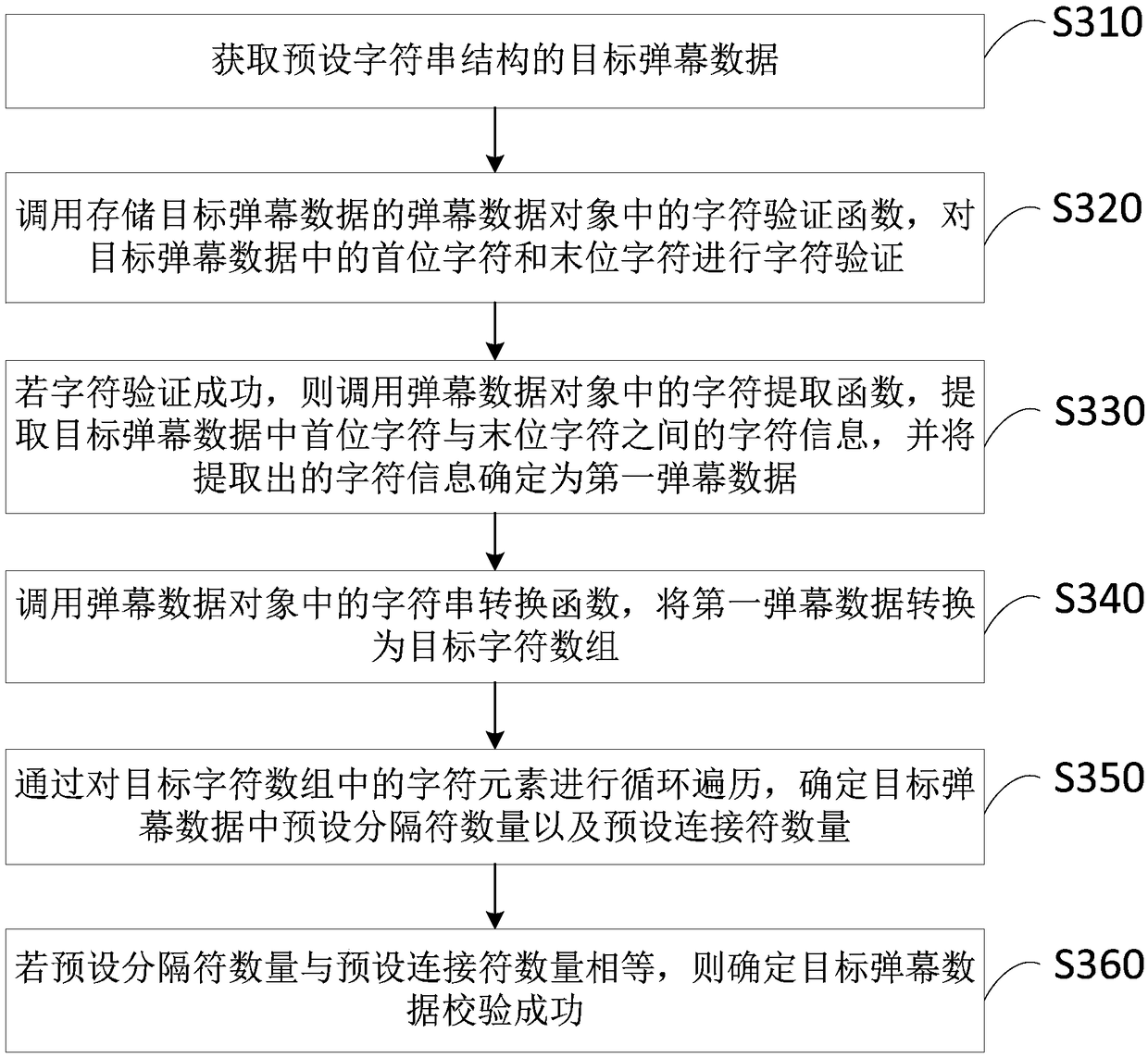
The embodiments of the invention disclose a method and a device for verifying barrage data and a terminal. The method comprises: acquiring target barrage data of a preset character string structure; calling a character verification function in a barrage data object storing the target barrage data, and performing character verification on the first character and the last character in the target barrage data; if the character verification succeeds, calling a character string conversion function in the barrage data object to convert the target barrage data into a target character array; performing character splicing on each preset number of adjacent character elements in the target character array, determining each spliced character string object, and calling an identifier search function ineach spliced character string object respectively to determine a number of preset identifiers in the target barrage data; and if the number of preset identifiers satisfies a preset verification condition, determining that the verification of the target barrage data succeeds. Through the technical solution, the integrity of the barrage data can be verified to avoid the problems of system crash andthe like on the client.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Image toolbar window loading method and device
ActiveCN102981876BAvoid problems like crashesImprove processing efficiencyProgram loading/initiatingComputer graphics (images)Computer module
The invention discloses a method and a device for loading a picture toolbar window. The device comprises a generating and acquiring module, a monitoring and acquiring module, a judging and transmitting module and a creating and displaying module, and the method is characterized in that when a browser is started up, a master browser process which corresponds to one or more webpage sub-processes is generated, and the picture toolbar window of the master browser process is used interactively among one or more webpage sub-processes. Due to the adoption of the method and the device, the phenomenon of misjudgment on loading of picture toolbar windows of the browser during relevant processing of picture elements is avoided.
Owner:BEIJING QIHOO TECH CO LTD
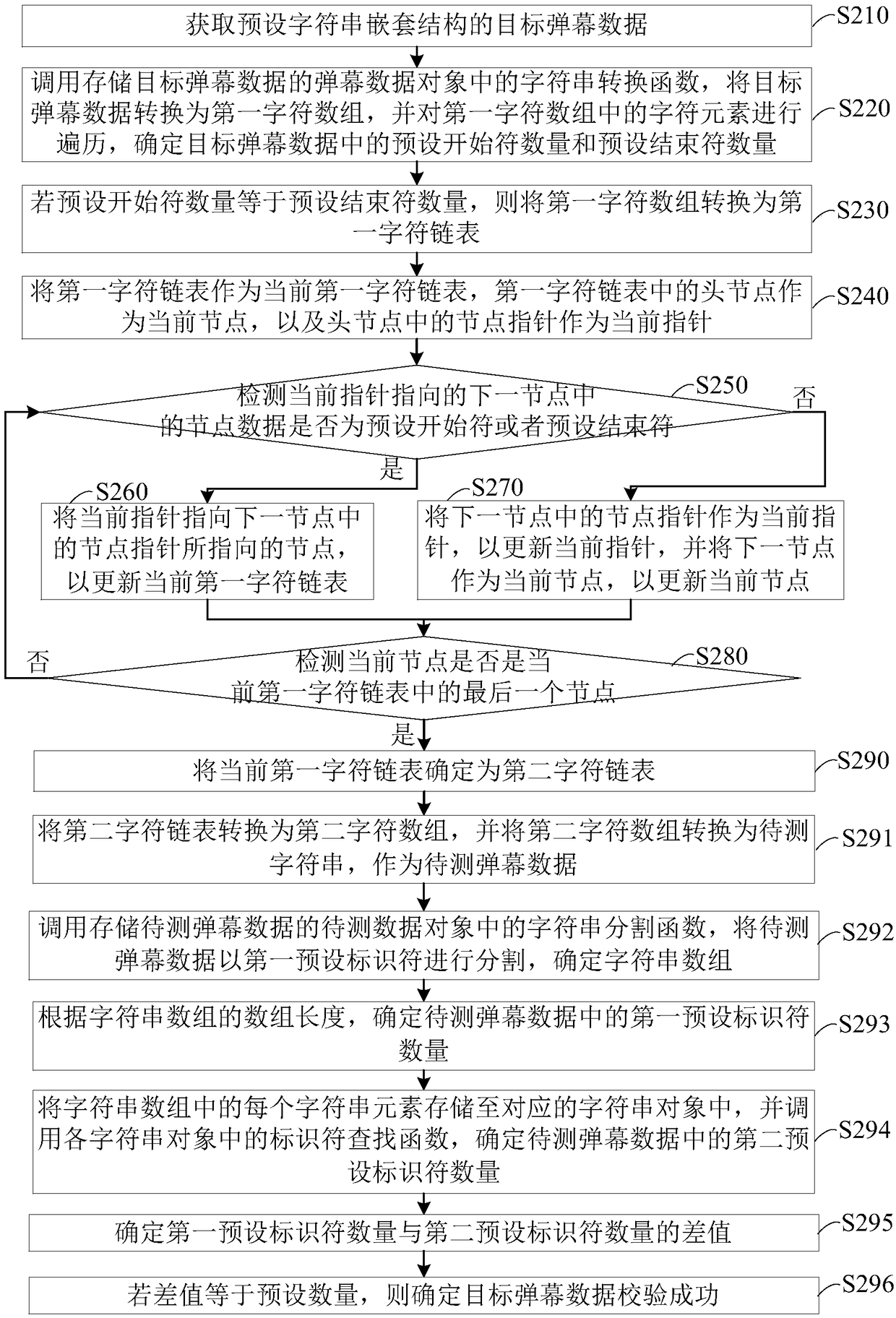
Bullet screen verification method and bullet screen verification device based on chain table mode, and terminal and storage medium
ActiveCN109379640AAvoid system crashImprove the efficiency of barrage testingNatural language data processingSelective content distributionData conversionData verification
The embodiment of the invention discloses a bullet screen verification method and a bullet screen verification device based on a chain table mode, and a terminal and a storage medium. The method comprises the following steps: acquiring target bullet screen data of a preset character string nested structure; calling a character string conversion function, converting the target bullet screen data into a first character array, traversing character elements in the first character array, and determining the number of preset start symbols and the number of preset end symbols in the target bullet screen data; if the number of the preset start symbols is equal to the number of the preset end symbols, based on a symbol removing mode of a chain table structure, removing each preset start symbol andeach preset end symbol in the first character array, and obtaining to-be-checked bullet screen data; and calling an identifier determination function, determining the number of preset identifiers in the to-be-checked bullet screen data, and when the number of the preset identifiers satisfies a preset verification condition, confirming that target bullet screen data verification is successful. Through the method, the device, the terminal and the storage medium provided by the technical scheme of the embodiment of the invention, the integrity verification can be executed for the bullet screen data of the nested structure.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Integrity checking method and device for bullet screen data, terminal and memory medium
ActiveCN109413450AImplement integrity checksAvoid problems like crashesDigital data information retrievalSelective content distributionArray data structureComputer terminal
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Checking methods and device for bullet screen data, terminal and memory medium
ActiveCN109413506AAvoid problems like crashesImprove test efficiencyNatural language data processingSelective content distributionArray data structureComputer terminal
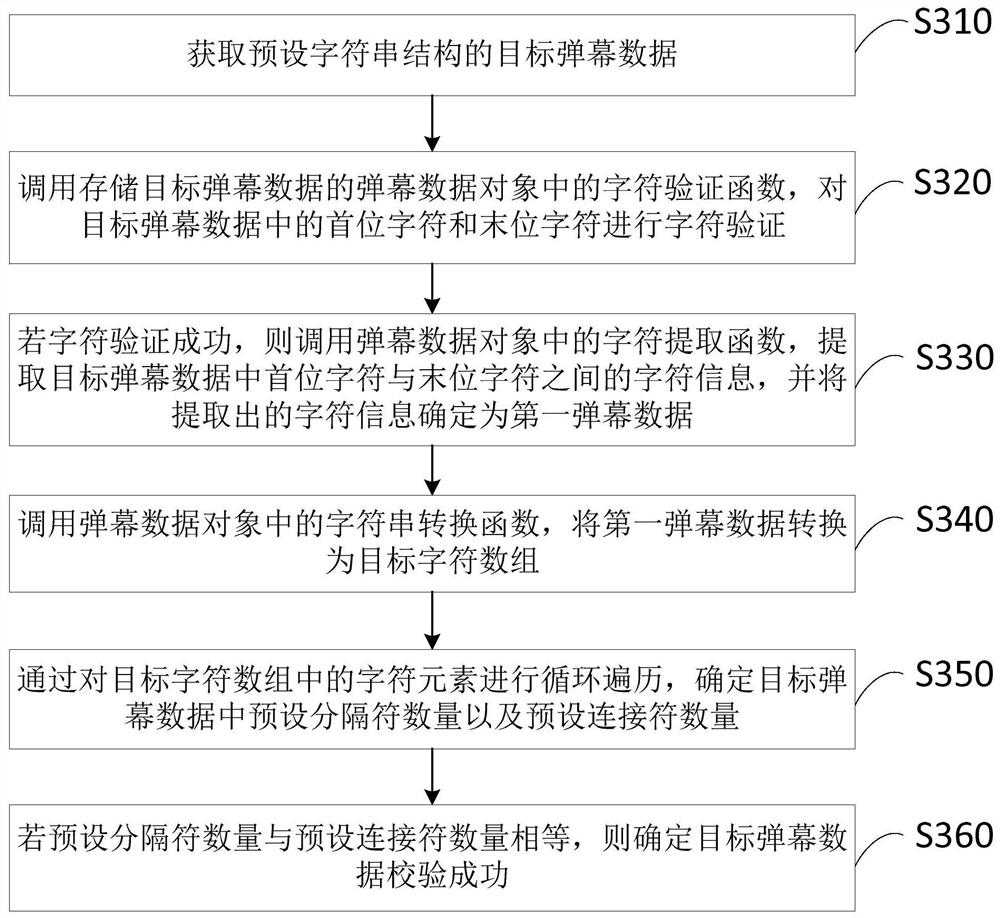
The embodiments of the invention provide checking methods and device for bullet screen data, a terminal and a memory medium. A method comprises the steps of obtaining target bullet screen data of a preset character string structure; calling a character verification function in a bullet screen data object for storing the target bullet screen data, and carrying out character verification on a firstcharacter and a final character in the target bullet screen data; calling a character string segmentation function in the bullet screen data object if the character verification is successful, segmenting the target bullet screen data according to preset identifiers, and determining a character string array; determining the number of the preset identifiers in the target bullet screen data accordingto array length of the character string array, and determining that the target bullet screen data is checked successfully when the number of the preset identifiers satisfies a preset checking condition. Through application of the technical scheme provided by the embodiments of the invention, integrity checking can be carried out on the bullet screen data, so the bullet screen data is guaranteed to be normally analyzed, and the problem that system crash occurs in a client is avoided.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Module and related electronic equipment for improving the fault tolerance rate of pop-out
InactiveCN108491245AImprove fault toleranceImprove experienceNon-redundant fault processingExecution for user interfacesFault toleranceComputer module
The invention provides a module for improving the fault tolerance rate of a pop-out. The module comprises a first fault-tolerant processing unit used for processing abnormal events in a pop-out calling component. The first fault-tolerant processing unit can be used for executing the following steps: judging whether the pop-out calling component is empty; judging whether the pop-out calling component is in the destroying stage and judging whether the pop-out calling component is already destroyed or not. The module may also include a feedback unit for feeding back an abnormal event and a secondfault-tolerant processing unit for processing an abnormal event of the pop-out logic and / or a third fault-tolerant processing unit for processing a memory leak event of the pop-out. The abnormal event processed by the three fault-tolerant processing units provided by the module is incremental step-by-step, so that abnormal event processing at the application layer, the system level and the spatial memory layer is realized, and the fault-tolerant capability of the pop-out is greatly enhanced. The invention also relates to an electronic device comprising the above module.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
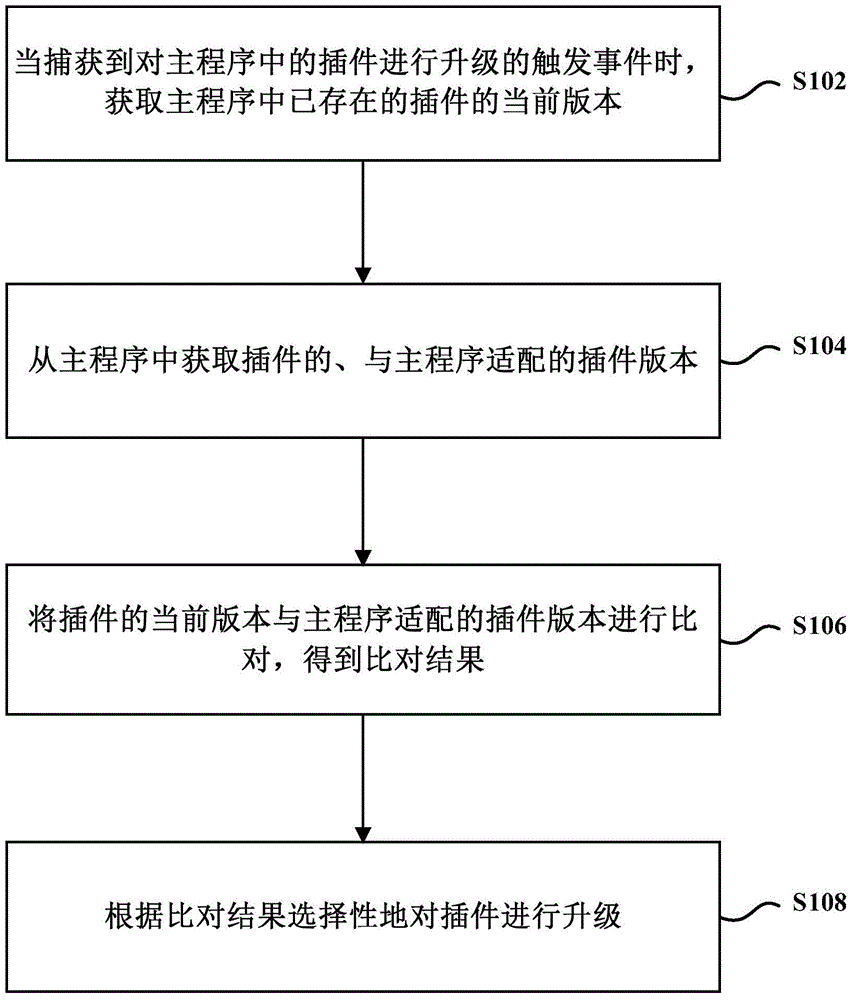
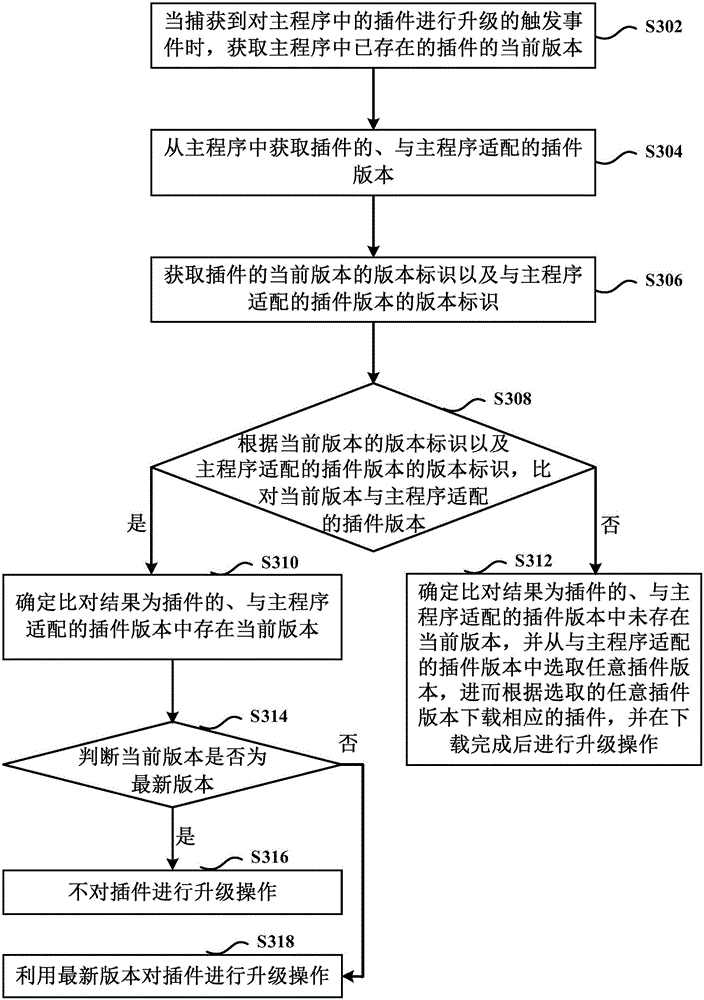
Plug-in upgrade method and device
ActiveCN104699511BGuaranteed normal interactionAvoid problems like crashesProgram loading/initiatingUpgradeComputer engineering
Owner:BEIJING ANYUNSHIJI TECH CO LTD
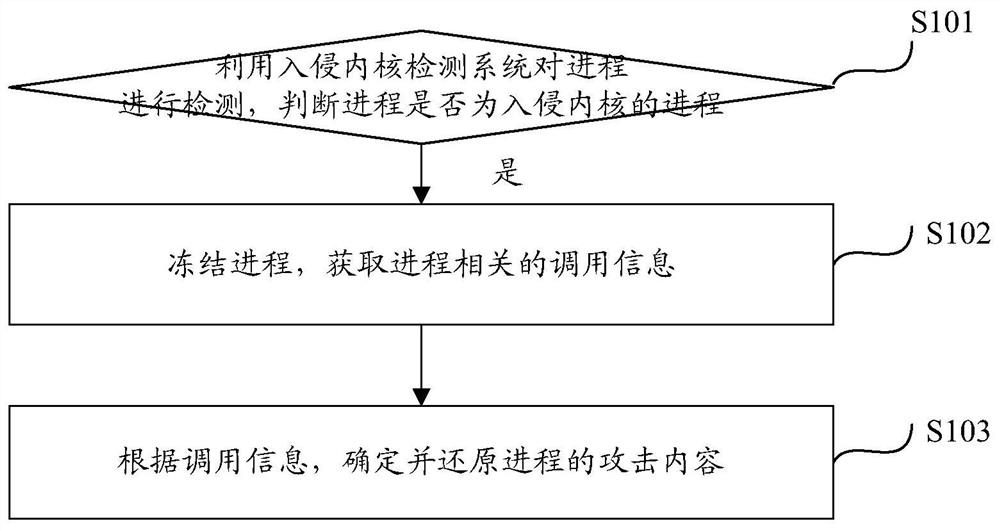
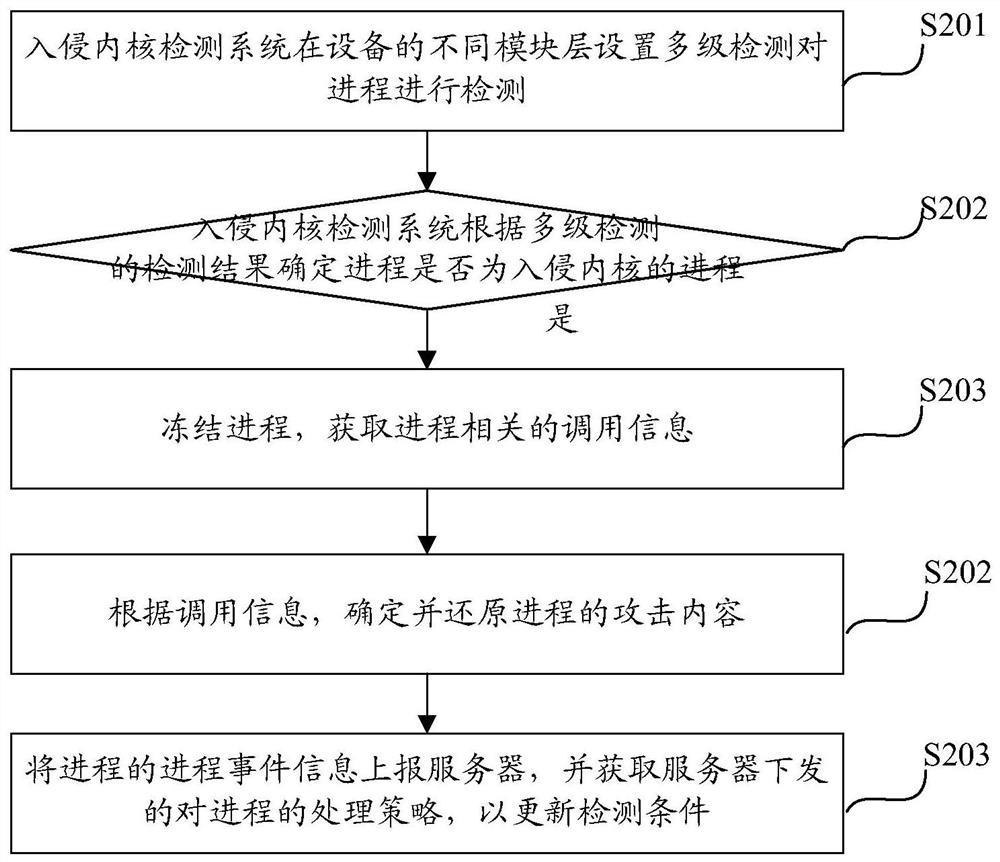
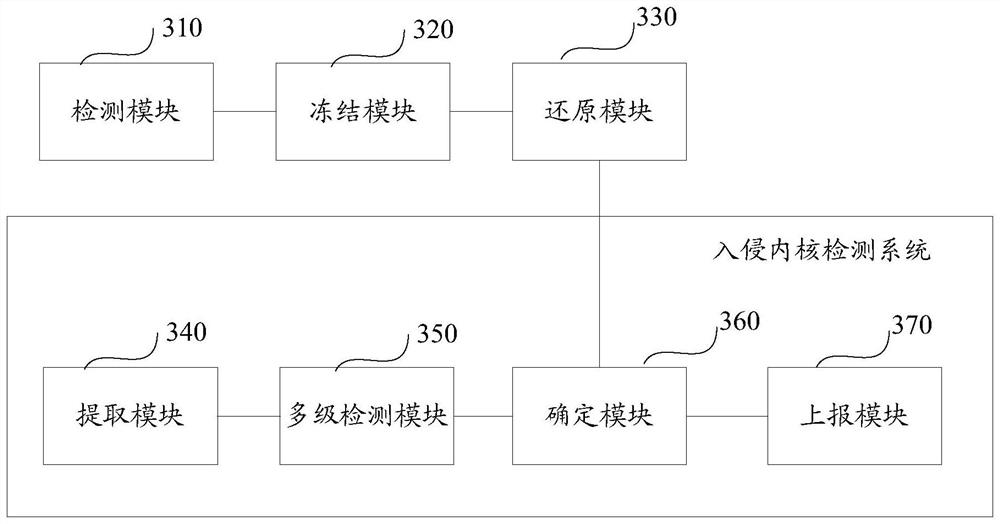
Intrusion kernel defense method and device, computing equipment and computer storage medium
PendingCN112307469AAvoid problems like crashesPlatform integrity maintainanceAttackEquipment computers
The invention discloses an intrusion kernel defense method and device, computing equipment and a computer storage medium, and the method comprises the steps: carrying out the detection of a process through an intrusion kernel detection system, and judging whether the process is the process of an intrusion kernel or not; if yes, freezing the process, and obtaining calling information related to theprocess; and determining and restoring the attack content of the process according to the calling information. After the process invading the kernel is detected, the process is frozen, so that the process is kept in the current state, currently occupied resources are not released, and attacks cannot be continued. For the frozen process, the calling information of the process is acquired and analyzed, and the attack content of the process is determined and restored, so that the content modified by the attack is recovered, and the problems of system crash and the like are avoided.
Owner:BEIJING QIHOO TECH CO LTD
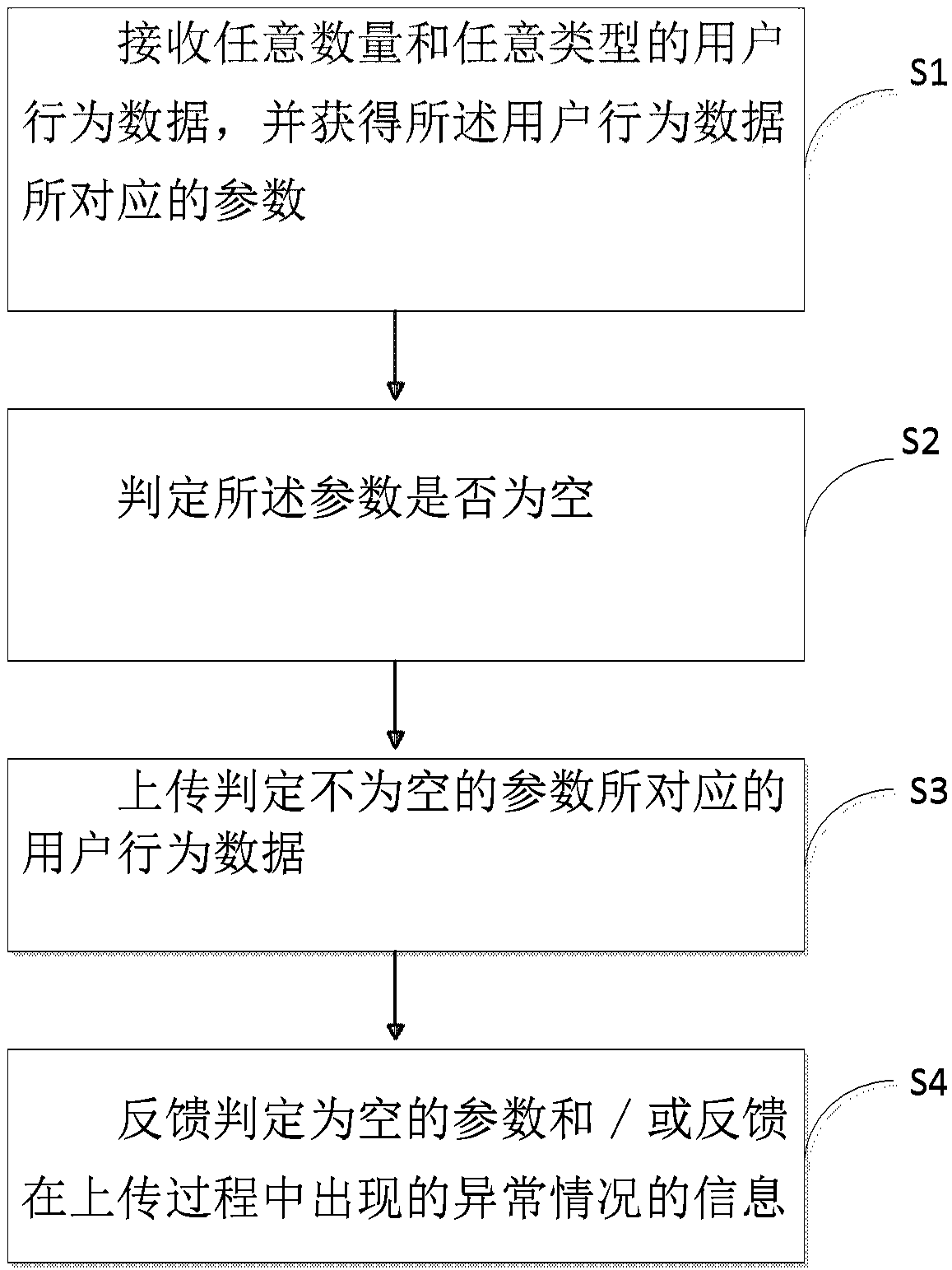
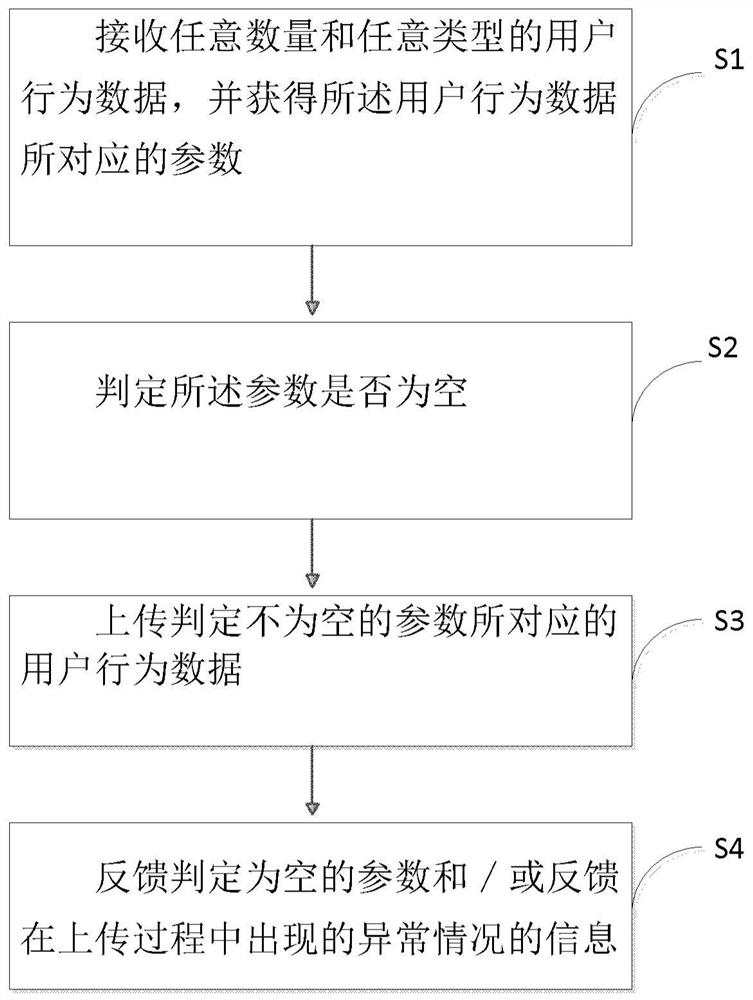
Point making module and method for processing user behavior data and computer readable storage medium
ActiveCN108536438AReduce in quantityImprove good performanceCreation/generation of source codeComputer moduleComputer engineering
The invention provides a point making module for processing user behavior data. The point making module comprises a data receiving unit, an empty judging unit, an uploading unit and a feedback unit, wherein the data receiving unit is used for receiving user behavior data of any number and any type through a custom function and acquiring parameters corresponding to the user behavior dada under thecustom function; the empty judging unit is used for judging whether or not the parameters are empty; the uploading unit is used for uploading the user behavior data corresponding to non-empty parameters judged by the empty judging unit; the feedback unit is used for feeding back empty parameters judged by the empty judging unit and / or abnormal condition information occurring during the uploading process of the uploading unit. The invention further relates to a related point making method for processing the user behavior data and a related computer readable storage medium.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Integrity verification method, device, terminal and storage medium for barrage data
ActiveCN109413450BImplement integrity checksAvoid problems like crashesDigital data information retrievalSelective content distributionData translationSoftware engineering
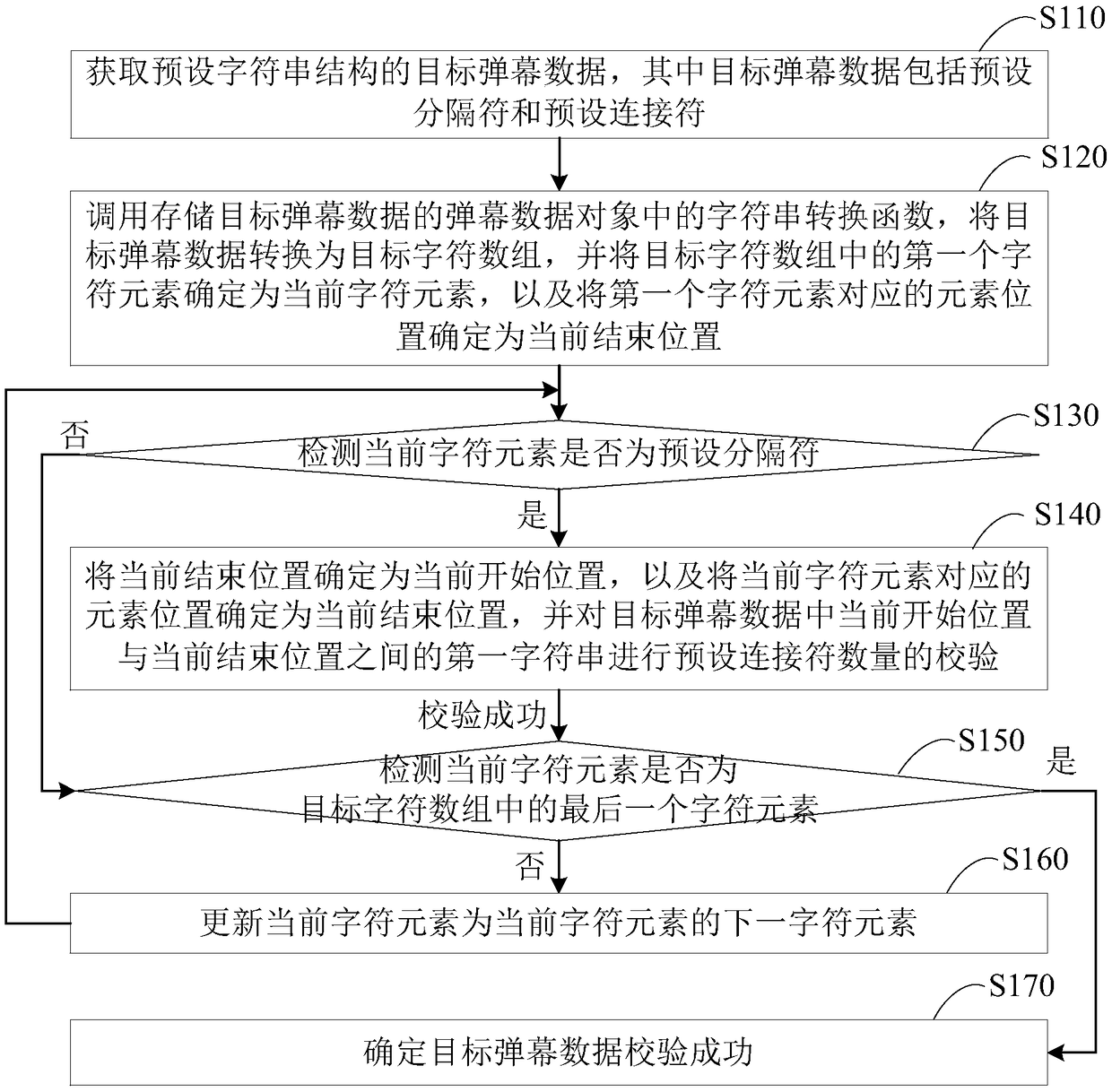
The embodiment of the present invention discloses a method, device, terminal and storage medium for checking the integrity of bullet chat data. The method includes: converting the target bullet chat data with a preset character string structure into a target character array, and The first character element in the array is used as the current character element; check whether the current character element is a preset delimiter, if so, use the current end position as the current start position, and use the position of the current character element as the current end position, for the current start Check the first character string between the position and the current end position; if not, or if the first character string is verified successfully, then if the current character element is not the last character element in the target character array, update the current character element, and Returns the operation of detecting whether the current character element is a preset separator; when the current character element is the last character element, it is determined that the verification of the target bullet chat data is successful, so as to perform an integrity check on the bullet chat data.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
A verification method, device, terminal and storage medium for barrage data
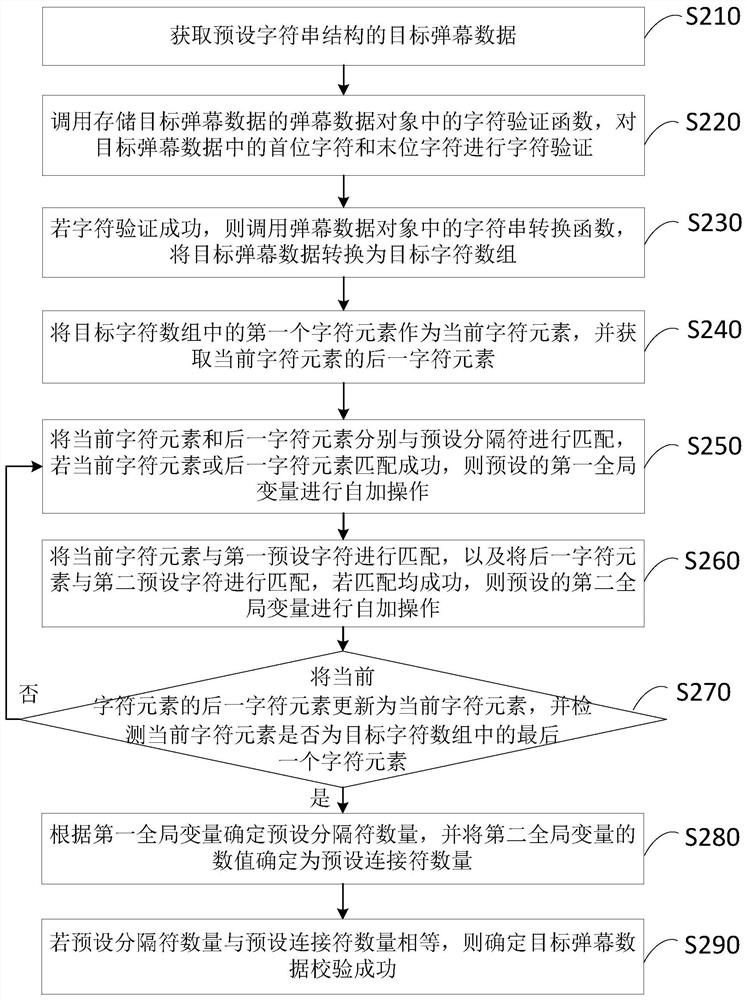
ActiveCN109413505BAvoid problems like crashesImprove test efficiencyVideo data queryingNatural language data processingIdenticonDatabase
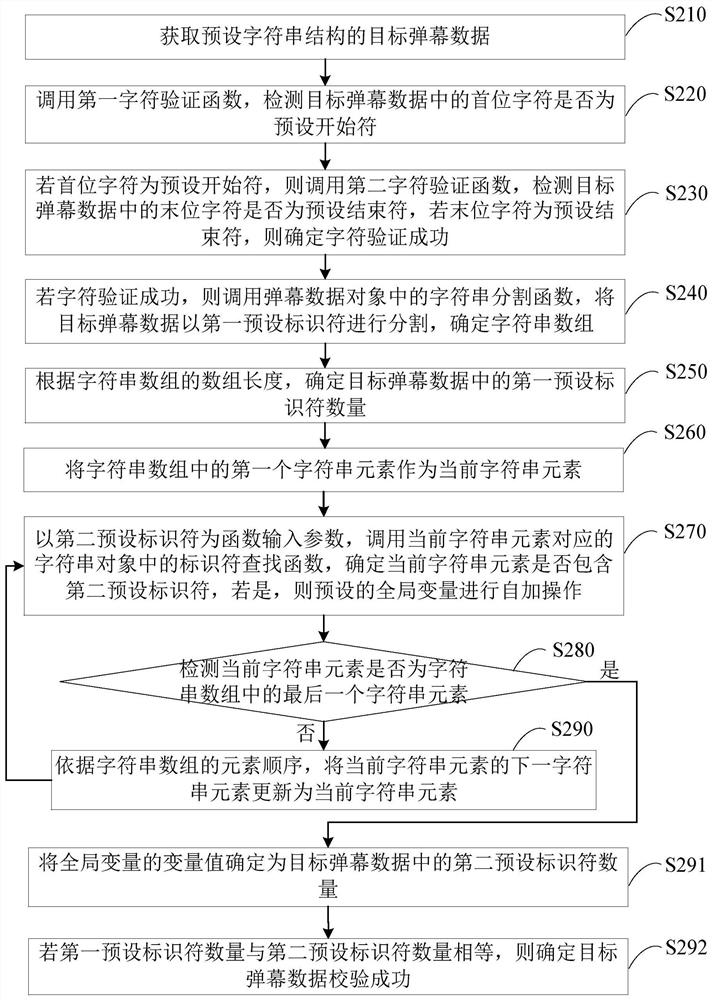
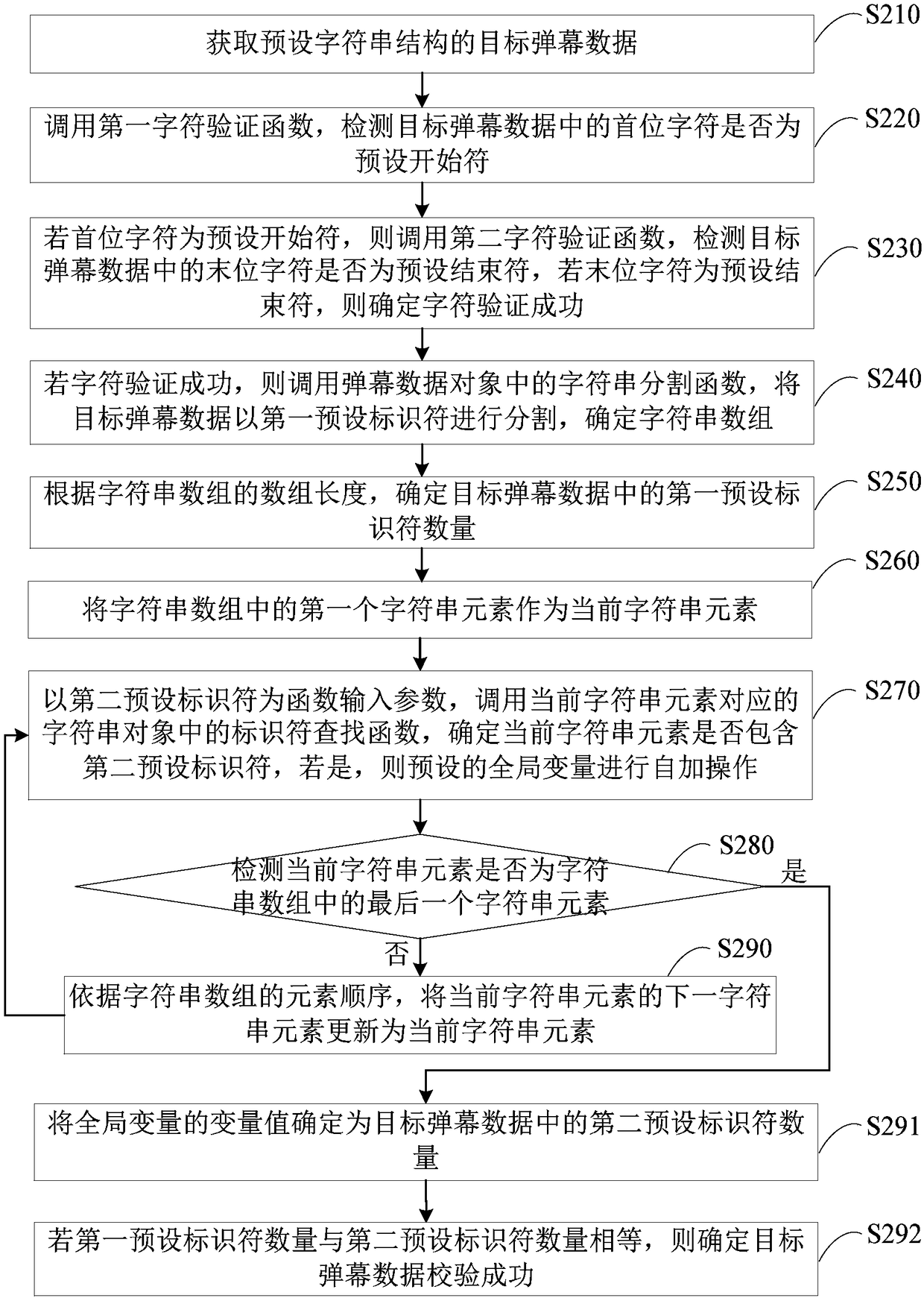
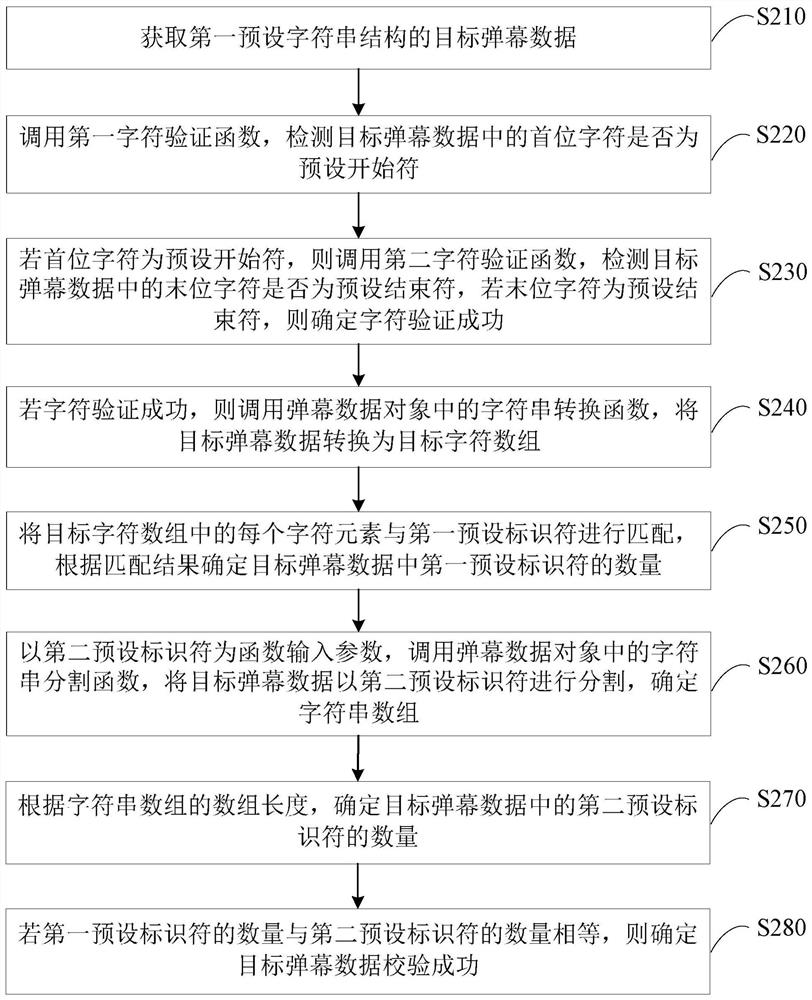
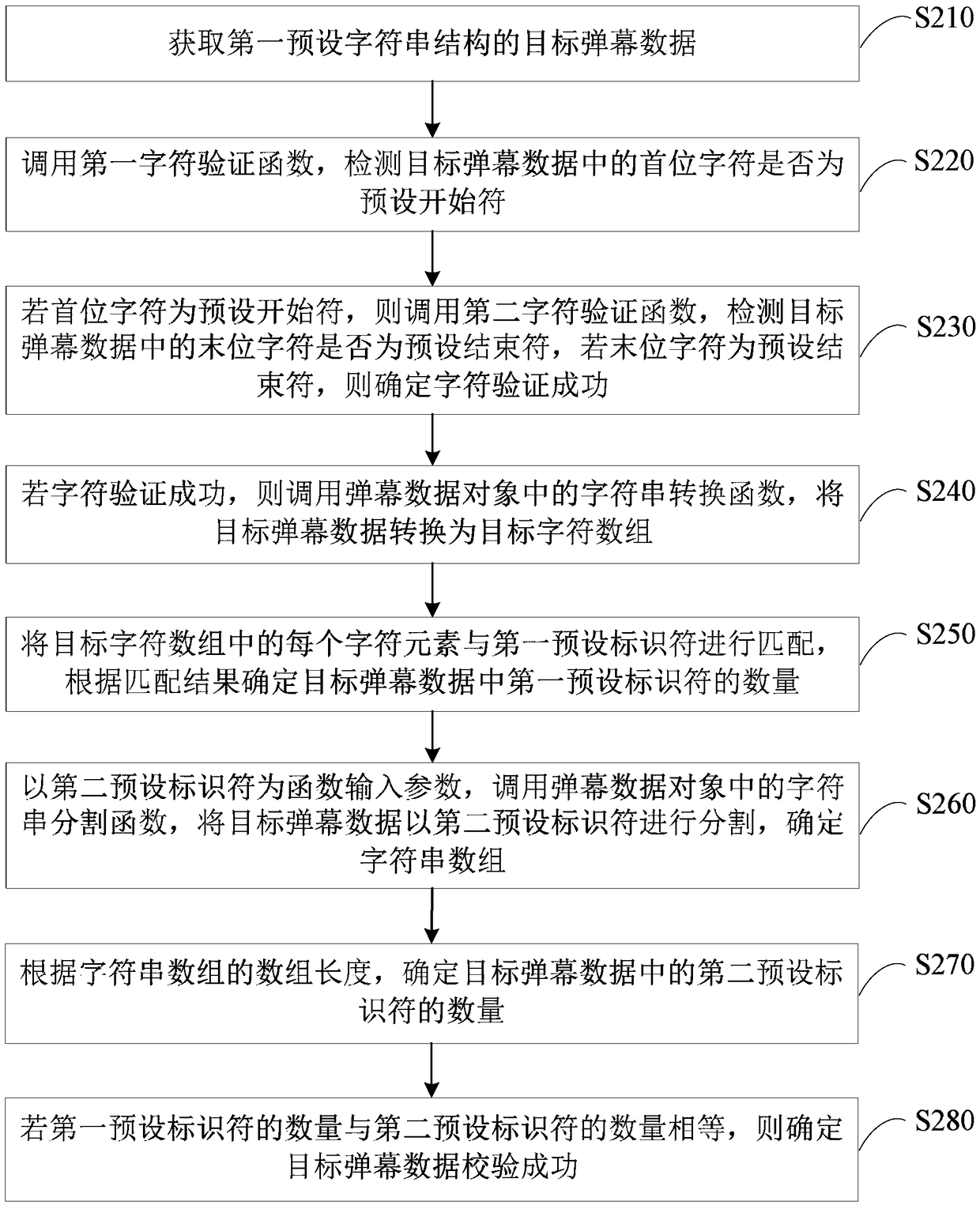
The embodiment of the present invention discloses a method, device, terminal and storage medium for verifying barrage data. The method includes: acquiring target barrage data with a preset character string structure; calling a barrage data object that stores target barrage data The character verification function in the target bullet chat data performs character verification on the first character and the last character in the target bullet chat data; if the character verification is successful, the string segmentation function in the bullet chat data object is called to convert the target bullet chat data into the first preset Set the identifier to divide and determine the string array; according to the array information of the string array, determine the first preset identifier number and the second preset identifier number in the target barrage data; if the first preset identifier number and the second preset number of identifiers satisfy the preset verification condition, it is determined that the verification of the target barrage data is successful. Through the technical solution of the embodiment of the present invention, the integrity check can be performed on the barrage data, thereby ensuring that the barrage data can be parsed normally.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
A method and device for loading a picture toolbar window
ActiveCN103034686BAvoid problems like crashesImprove processing efficiencySpecial data processing applicationsInput selectionComputer graphics (images)
The invention discloses a method and a device for loading a picture toolbar window. The method comprises the following steps that a webpage label is opened in a webpage subprocess, and the position information of picture elements in a webpage is obtained; when an input selection event of the picture elements is monitored in the current webpage subprocess, the display region information of the picture elements is obtained according to the position information of the picture elements; the position information of the current cursor is obtained and is compared with the display region information of the picture elements, whether the position of the current cursor is in the display region of the picture elements or not is judged, and judgment results and the position information of the picture elements are notified to the host process of a browser; and the host process of the browser creates or displays or hides the picture toolbar window in the specified position according to the judgment results and the position information of the picture elements. The method and the device solve the loading misjudgment phenomenon of the picture toolbar window when the relevant processing of the picture elements is executed in the browser.
Owner:BEIJING QIHOO TECH CO LTD
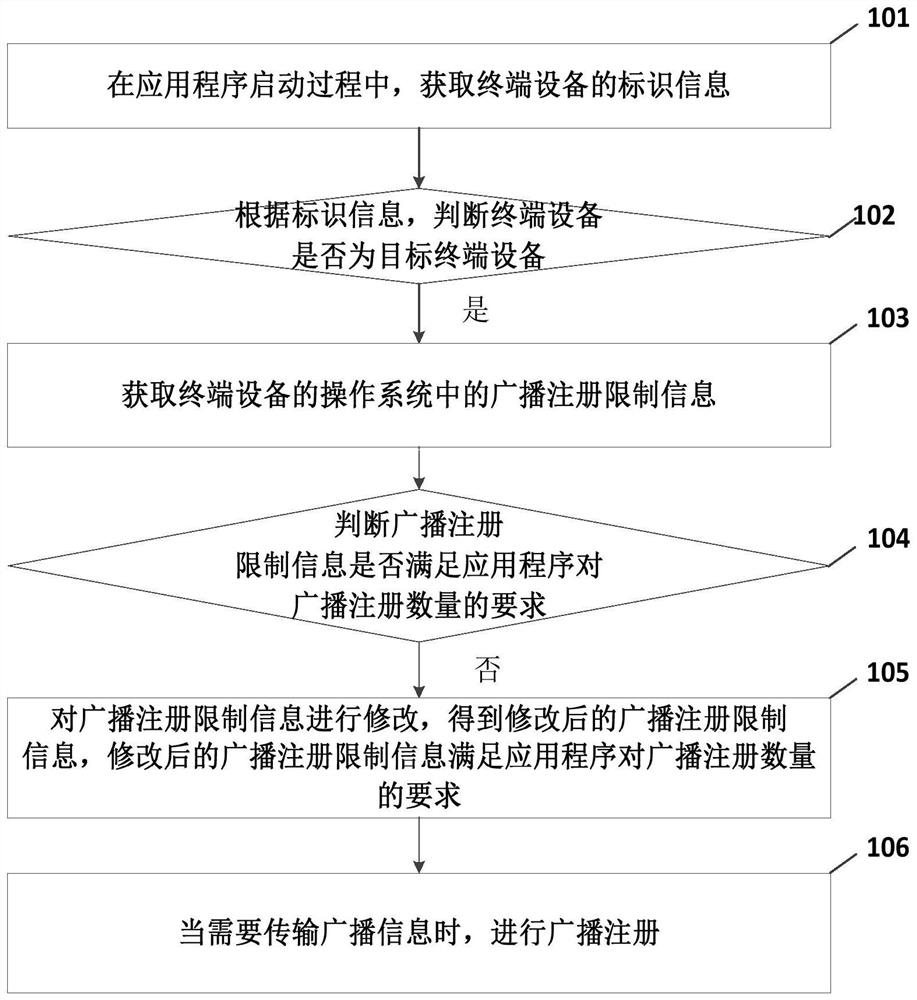
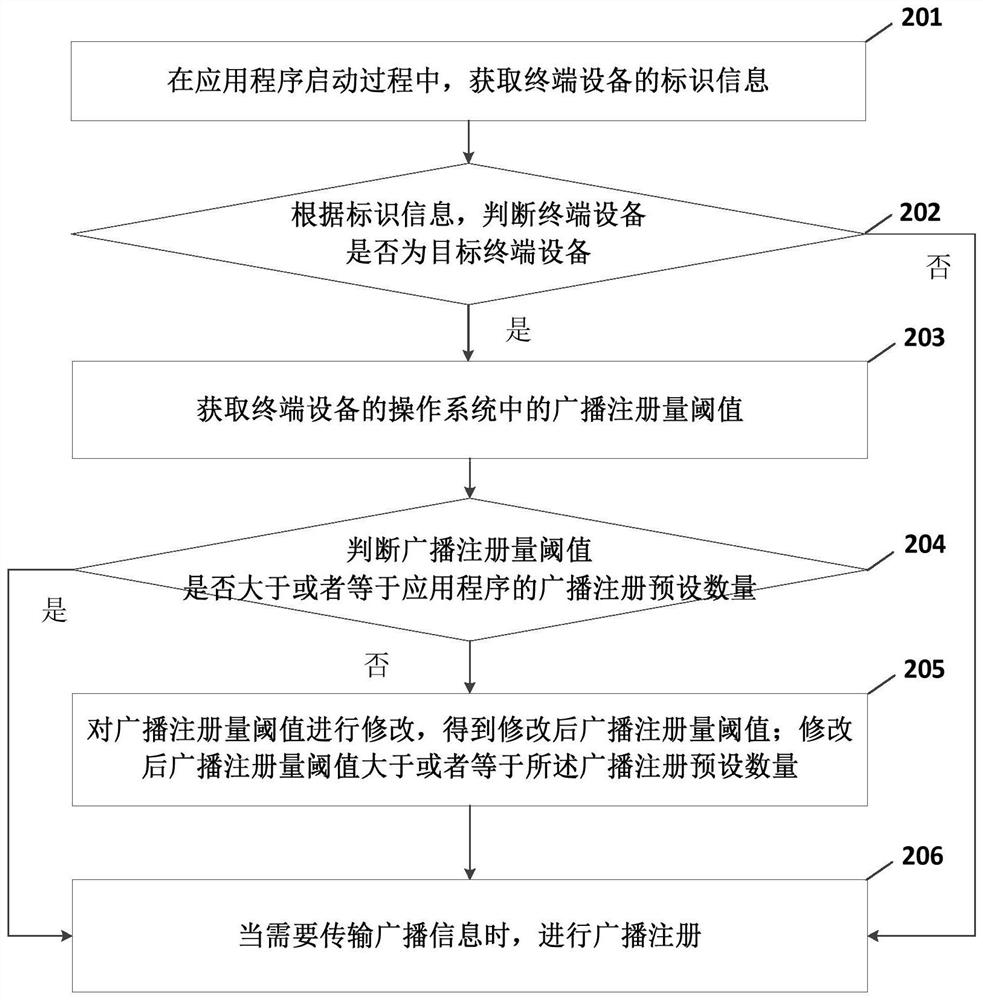
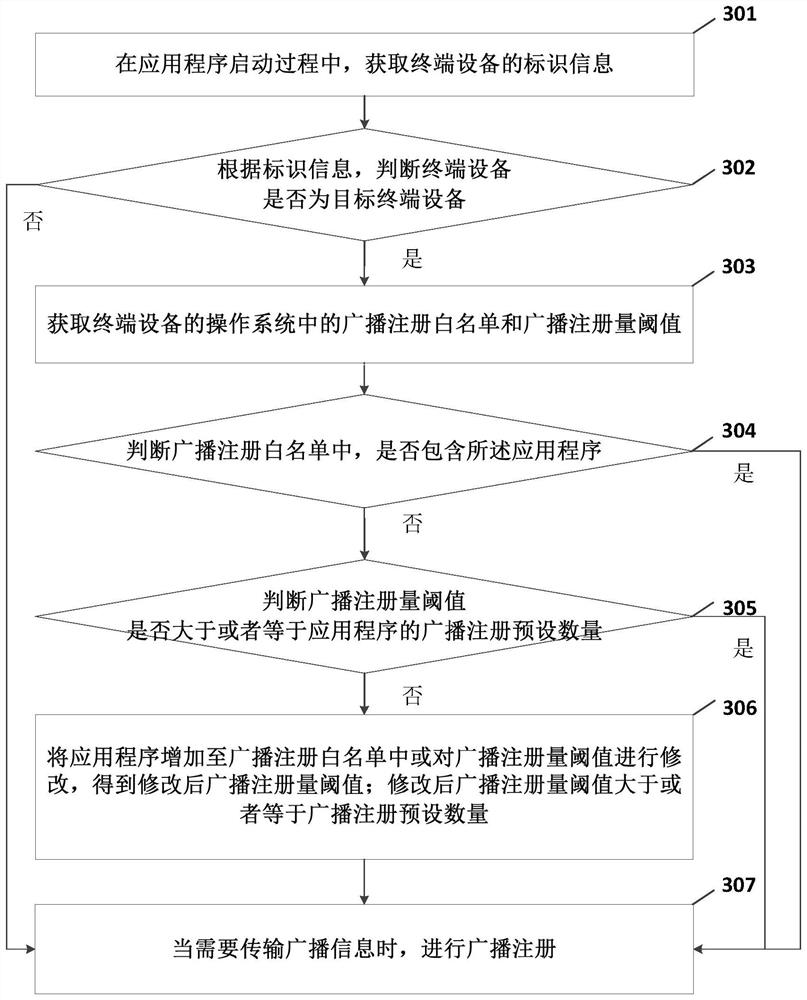
Application program broadcast registration method, device, equipment and medium
ActiveCN110209513BImprove experienceAvoid problems like crashesInterprogram communicationOperational systemTerminal equipment
Embodiments of the present invention provide a broadcast registration method and device for an application program, a terminal device, and a storage medium. During the startup process of the application program, the identification information of the terminal device is obtained; and the terminal device is judged according to the identification information Whether it is the target terminal device; if so, obtain the broadcast registration restriction information in the operating system of the terminal device; determine whether the broadcast registration restriction information meets the requirements of the application program for the number of broadcast registrations; The registration restriction information is modified to obtain the modified broadcast registration restriction information; when the broadcast information needs to be transmitted, the broadcast registration is performed. In the embodiment of the present invention, for a terminal device that has broadcast registration restriction information, and the restriction information does not meet the requirements of the application program for the number of broadcast registrations, the broadcast registration restriction information can be modified to the broadcast registration restriction information that meets the requirements. experience.
Owner:BEIJING KINGSOFT INTERNET SECURITY SOFTWARE CO LTD
Bullet screen data checking method, bullet screen data checking device, terminal and storage medium
ActiveCN109348305ANormal parsingAvoid problems like crashesSelective content distributionArray data structureSoftware engineering
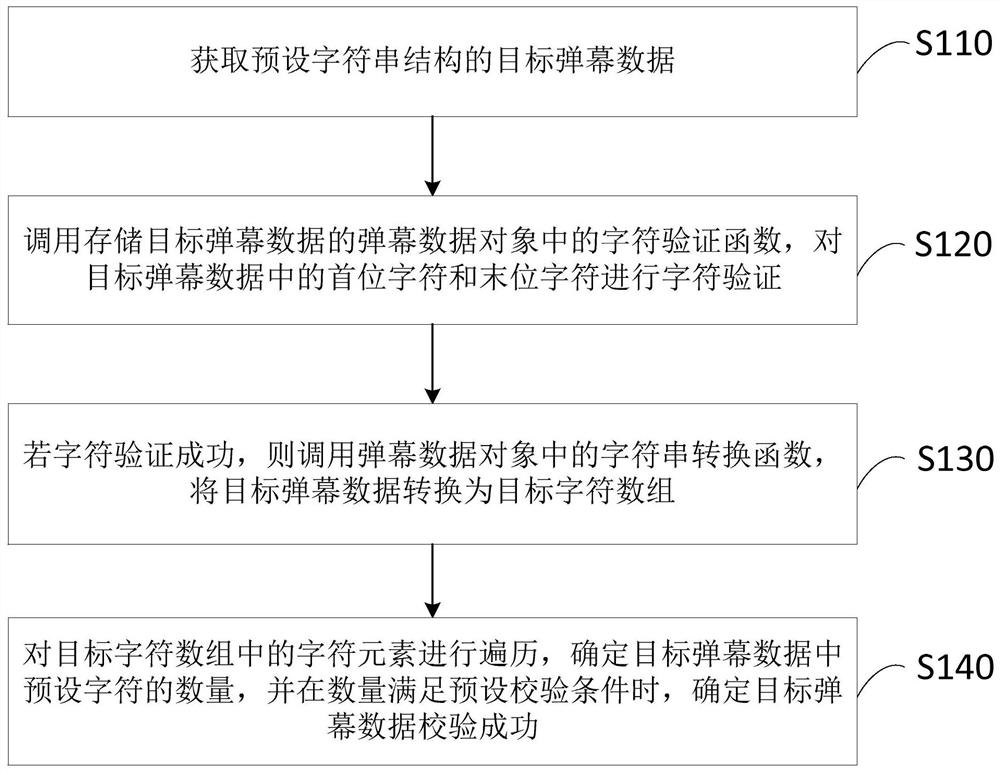
The embodiment of the invention discloses a bullet screen data checking method, a bullet screen data checking device, a terminal and a storage medium. The method comprises the steps of: obtaining thetarget bullet screen data of a pre-set character string structure; calling a character verification function in a bullet screen data object storing the target bullet screen data, and performing character verification on the first character and the last character in the target bullet screen data; if character verification is successful, calling a character string conversion function in the bullet screen data object, and converting the target bullet screen data to the target character array; and, traversing character elements in the target character array, determining the number of pre-set characters in the target bullet screen data, and, when the number satisfies the pre-set checking condition, determining that the target bullet screen data check is successful. By means of the technical scheme in the embodiment of the invention, integrity checking on the bullet screen data can be carried out; therefore, the bullet screen data can be normally analyzed; and the problems, such as the system breakdown of a client side, are avoided.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Method and apparatus for verifying bullet screen data, terminal and storage medium
ActiveCN109413505AAvoid problems like crashesImprove test efficiencyVideo data queryingNatural language data processingArray data structureComputer terminal
The embodiment of the invention discloses a method and apparatus for verifying bullet screen data, a terminal and a storage medium. The method comprises the following steps: obtaining target bullet screen data of a preset character string structure; calling a character verification function in a bullet screen data object storing the target bullet screen data to perform character verification on the first character and the last character in the target bullet screen data; if the character verification is successful, calling a character string segmentation function in the bullet screen data object to segment the target bullet screen data via first preset identifiers, and determining a character string array; determining the number of first preset identifiers and the number of second preset identifiers in the target bullet screen data according to the array information of the character string array; and if the number of first preset identifiers and the number of second preset identifiers meet preset verification conditions, determining that the verification of the target bullet screen data is successful. Through the technical scheme of the embodiment of the invention, integrity verification can be performed on the bullet screen data, thereby ensuring that the bullet screen data can be normally parsed.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
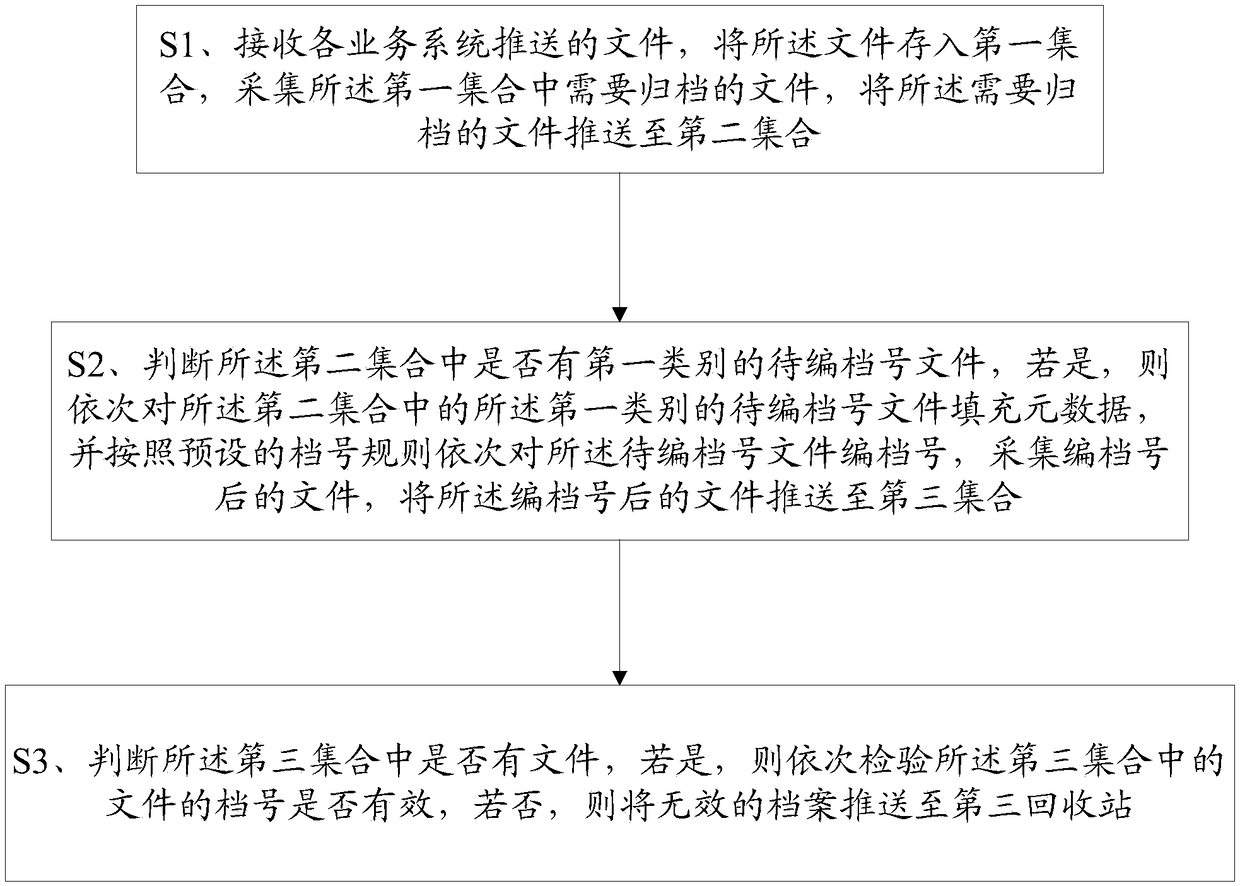
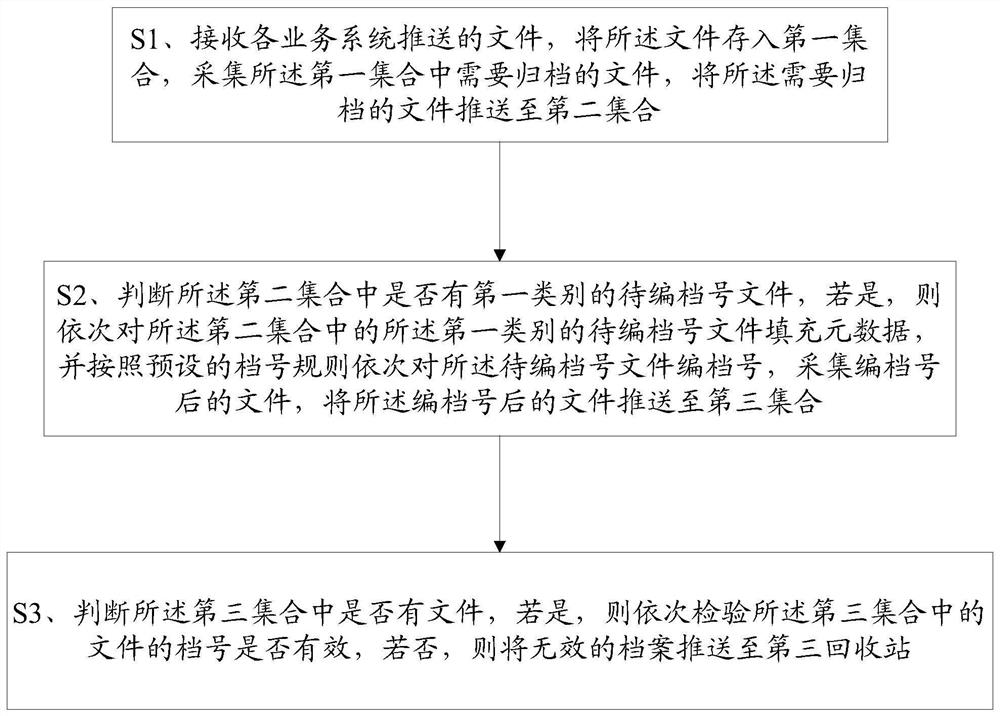
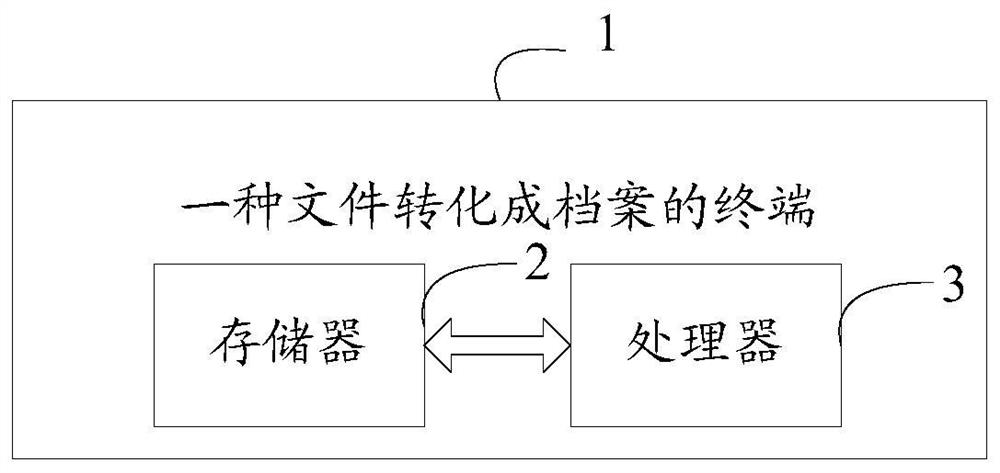
Method for converting files into archives and terminal
ActiveCN108388633AEasy to organizeImprove work efficiencySpecial data processing applicationsArchive fileMetadata
The invention provides a method for converting files into archives and a terminal. The method comprises the following steps: receiving files pushed by each business system, storing the files into a first set, collecting the files needing to be archived in the first set, and pushing the files needing to be archived to a second set; judging whether the to-be-archived files of the first category exist in the second set, if yes, sequentially filling the to-be-archived files of the first category in the second set with metadata, sequentially archiving the to-be-archived files according to the preset archive number rule, collecting the archived files, and pushing the archived files to a third set; and judging whether files exist in the third set or not, if yes, sequentially inspecting whether the archive numbers of the files in the third set are valid or not, and if no, pushing the invalid archives to a third recycle bin, thereby completing the conversion from the files into the archives. The whole conversion process from the files into the archives is standardized, systematized and efficient and is low in cost.
Owner:FUJIAN RONGJI SOFTWARE ENG CO LTD
A network scheduling method and gateway
ActiveCN103763206BImplement automatic repairAvoid problems like crashesNetwork connectionsCapacity valueProcess information
Owner:北京柏安科技有限公司
Dotting module, method and computer readable medium for processing user behavior data
ActiveCN108536438BReduce in quantityImprove good performanceCreation/generation of source codeBehavioral dataHuman–computer interaction
The present invention provides a dotting module for processing user behavior data, which includes: a data receiving unit for receiving any amount and any type of user behavior data through a user-defined function, and obtaining the user behavior under the user-defined function The parameter corresponding to the data; the empty judging unit, used to determine whether the parameter is empty; the upload unit, used to upload the user behavior data corresponding to the parameter that is determined not to be empty by the empty judging unit; and the feedback unit, used to send to The console feeds back information about the parameters determined to be empty by the empty judging unit and / or the abnormal situation that occurs during the uploading process of the uploading unit. The present invention also relates to a related method for processing user behavior data and a related computer-readable storage medium.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
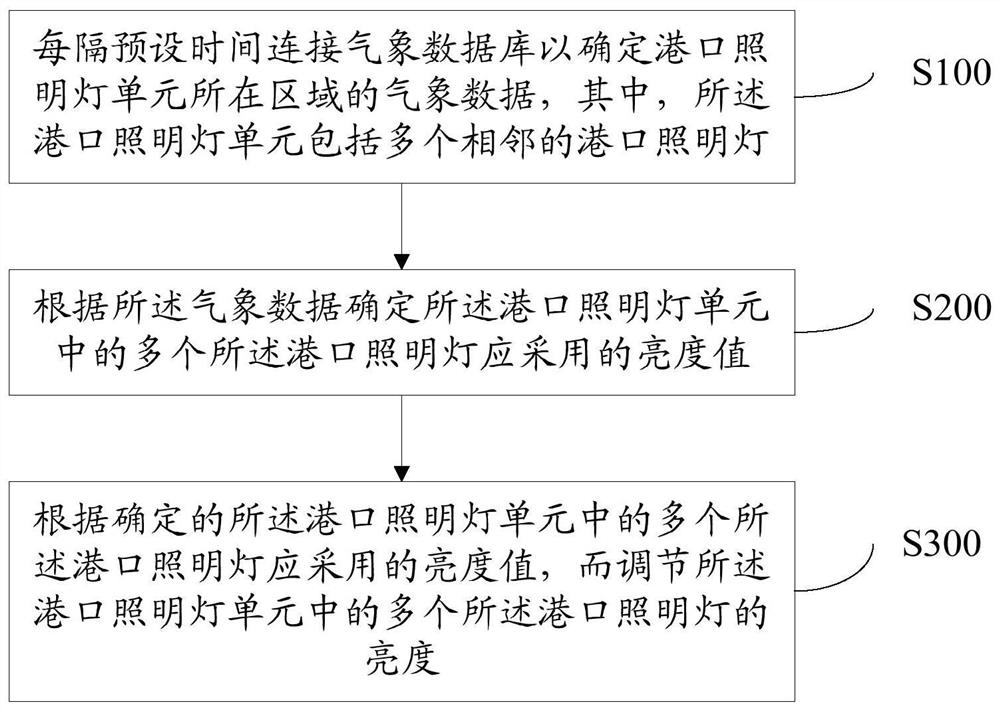
Brightness adjustment method and device for a port lighting lamp
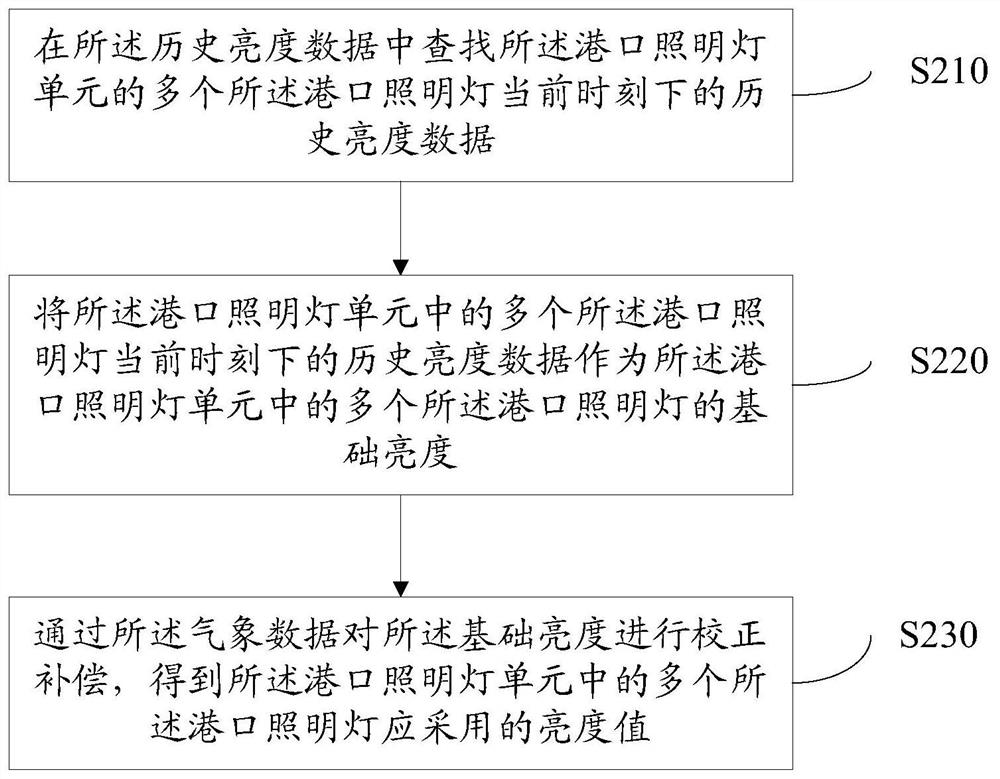
ActiveCN109195276BLow operation and maintenance costsHigh speedElectrical apparatusEnergy saving control techniquesEngineeringAtmospheric sciences
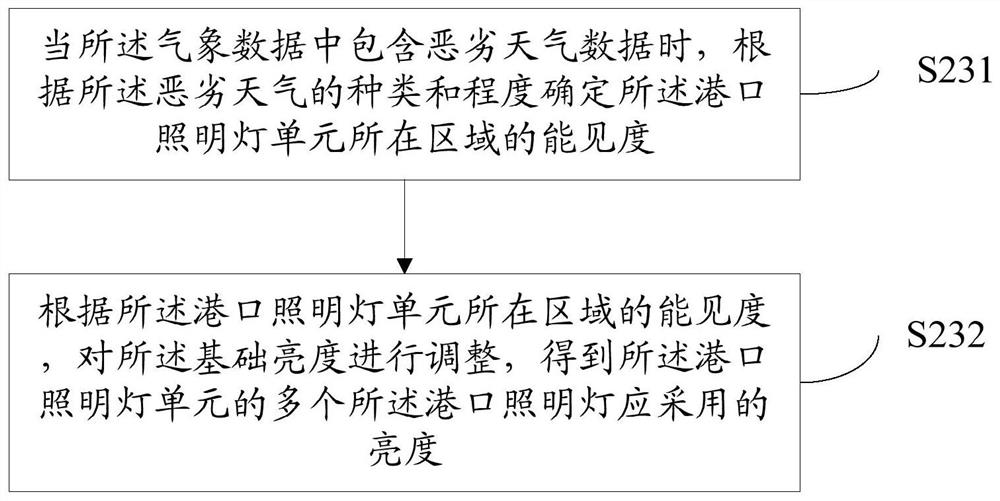
The invention discloses a method for adjusting the brightness of a harbor lighting lamp. The method comprises: connecting a meteorological database every preset time to determine the meteorological data of an area where a port lighting lamp unit is located, wherein the harbor lighting lamp unit comprises a plurality of adjacent port lighting lamps; determining brightness values to be used for a plurality of the port lighting lamps in the port lighting unit according to the meteorological data; adjusting the brightness of a plurality of the port lights in the port light unit according to the determined brightness value to be used for the plurality of the port lights in the port light unit. By the method, problems such as data transmission speed reduction and server crash caused by accessingthe meteorological database by each port lighting lamp can be effectively avoided; the invention not only can flexibly adjust the brightness of the lighting lamp unit of the port, save energy and protect environment, but also can fully utilize the existing meteorological data resources, and greatly reduce the operation and maintenance cost of the lighting lamp of the port.
Owner:江苏省发明协会 +1
Method and terminal for converting files into files
ActiveCN108388633BEasy to organizeImprove work efficiencyDigital data information retrievalSpecial data processing applicationsEngineeringDatabase
The invention provides a method for converting files into archives and a terminal. The method comprises the following steps: receiving files pushed by each business system, storing the files into a first set, collecting the files needing to be archived in the first set, and pushing the files needing to be archived to a second set; judging whether the to-be-archived files of the first category exist in the second set, if yes, sequentially filling the to-be-archived files of the first category in the second set with metadata, sequentially archiving the to-be-archived files according to the preset archive number rule, collecting the archived files, and pushing the archived files to a third set; and judging whether files exist in the third set or not, if yes, sequentially inspecting whether the archive numbers of the files in the third set are valid or not, and if no, pushing the invalid archives to a third recycle bin, thereby completing the conversion from the files into the archives. The whole conversion process from the files into the archives is standardized, systematized and efficient and is low in cost.
Owner:FUJIAN RONGJI SOFTWARE ENG CO LTD
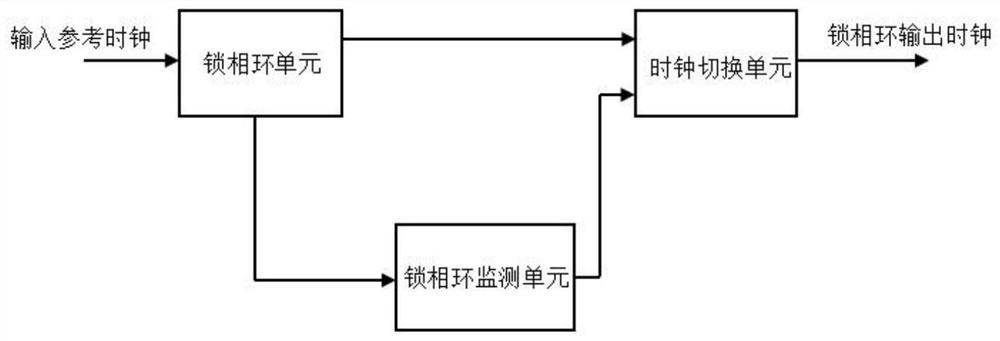
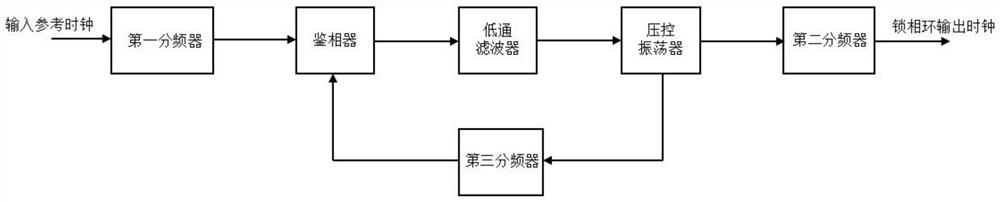
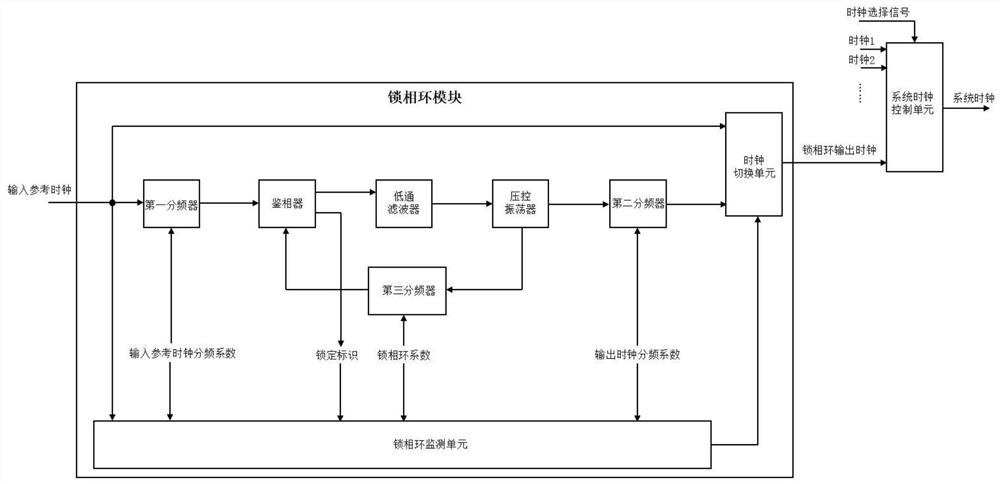
High-reliability phase-locked loop module and switching method of output clock of phase-locked loop module
InactiveCN112104358ARealize automatic switchingAvoid overheadPulse automatic controlSystem failureEmbedded system
A high-reliability phase-locked loop module comprises a phase-locked loop unit, a phase-locked loop monitoring unit and a clock switching unit, the phase-locked loop unit is connected to the phase-locked loop monitoring unit, and the output of the phase-locked loop monitoring unit and the output of the phase-locked loop unit are respectively connected to the clock switching unit. The phase-lockedloop monitoring unit is used for monitoring the working state or parameters of the phase-locked loop unit, and the clock switching unit is used for switching the output clock of the phase-locked loopmodule according to the monitoring result of the phase-locked loop monitoring unit. According to the technical scheme, automatic switching of the output clock of the phase-locked loop can be achieved,power consumption is reduced, cost is saved, the problems of system faults, breakdown and the like caused by phase-locked loop unlocking and jittering of the input reference clock of the phase-lockedloop can be avoided, and the stability and reliability of the system are greatly improved.
Owner:苏州云途半导体有限公司
A verification method, device and terminal for barrage data
ActiveCN109413451BImprove test efficiencyAvoid problems like crashesDigital data information retrievalSelective content distributionComputer hardwareProgramming language
The embodiment of the invention discloses a method, device and terminal for verifying barrage data. The method includes: obtaining target bullet chat data with a preset character string structure; calling a character verification function in the bullet chat data object storing the target bullet chat data, and performing character verification on the first character and the last character in the target bullet chat data; If the character verification is successful, when the preset identifier includes only one preset character, call the string conversion function in the bullet chat data object to determine the number of preset identifiers in the target bullet chat data; when the preset identifier includes When there are at least two preset characters, call the string segmentation function in the bullet chat data object to determine the number of preset identifiers in the target bullet chat data; if the number of preset identifiers meets the preset verification conditions, determine the target The barrage data verification is successful. Through the technical solution of the embodiment of the present invention, the integrity check can be performed on the barrage data, thereby ensuring that the barrage data can be parsed normally.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Verification method and device for barrage data, and terminal
ActiveCN109413451AImprove test efficiencyAvoid problems like crashesDigital data information retrievalSelective content distributionObject storeComputer terminal
The embodiment of the invention discloses a verification method and device for barrage data, and a terminal. The method comprises the steps of: acquiring target barrage data with a preset character string structure; calling a character verification function in a barrage data object storing the target barrage data, and carrying out character verification on a first character and a last character inthe target barrage data; if character verification is successful, when each preset identifier only includes one preset character, calling a character string conversion function in the barrage data object, and determining the number of the preset identifiers in the target barrage data; when each preset identifier includes at least two preset characters, calling a character string segmentation function in the barrage data object, and determining the number of the preset identifiers in the target barrage data; and if the number of the preset identifiers meets a preset verification condition, determining that the target barrage data is successfully verified. By the technical scheme of the embodiment of the invention, the barrage data can be subjected to integrity verification so as to ensurethat the barrage data can be normally parsed.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
A verification method, device, terminal and storage medium for barrage data
ActiveCN109348305BNormal parsingAvoid problems like crashesSelective content distributionComputer hardwareData transformation
The embodiment of the invention discloses a verification method, device, terminal and storage medium of barrage data. The method includes: obtaining target bullet chat data with a preset character string structure; calling a character verification function in the bullet chat data object storing the target bullet chat data, and performing character verification on the first character and the last character in the target bullet chat data; If the character verification is successful, call the string conversion function in the bullet chat data object to convert the target bullet chat data into the target character array; traverse the character elements in the target character array to determine the preset characters in the target bullet chat data Quantity, and when the quantity satisfies the preset verification conditions, it is determined that the verification of the target barrage data is successful. Through the technical solution of the embodiment of the present invention, the integrity check of the bullet chat data can be performed, so as to ensure that the bullet chat data can be parsed normally, and avoid problems such as system crash of the client.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com