Information network attack-oriented vulnerability node evaluation method for power grid
An information network and vulnerability technology, applied in the field of power grid cyber-physical systems, can solve problems such as relay protection error actions, economic losses, false control of PMU & SCADA systems, etc., to ensure information security and stable operation, and the analysis results are objective and accurate. Comprehensive effect of the structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
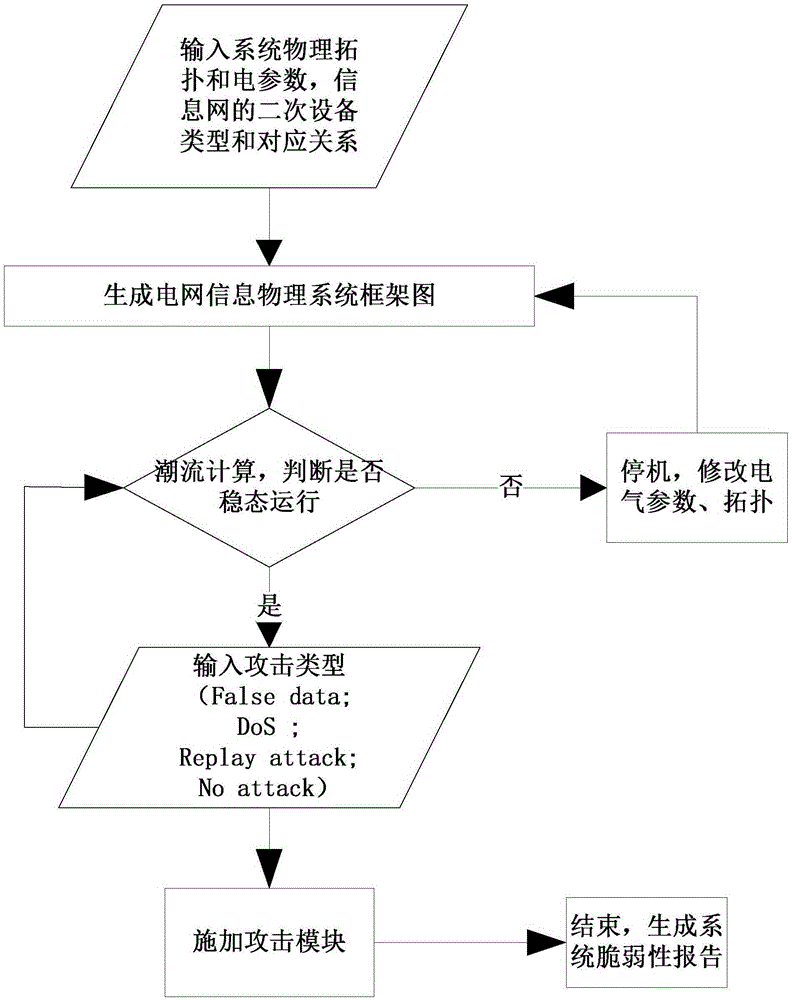
[0037] The present invention will be described in detail below with reference to the accompanying drawings, and the objects and effects of the present invention will become more apparent.
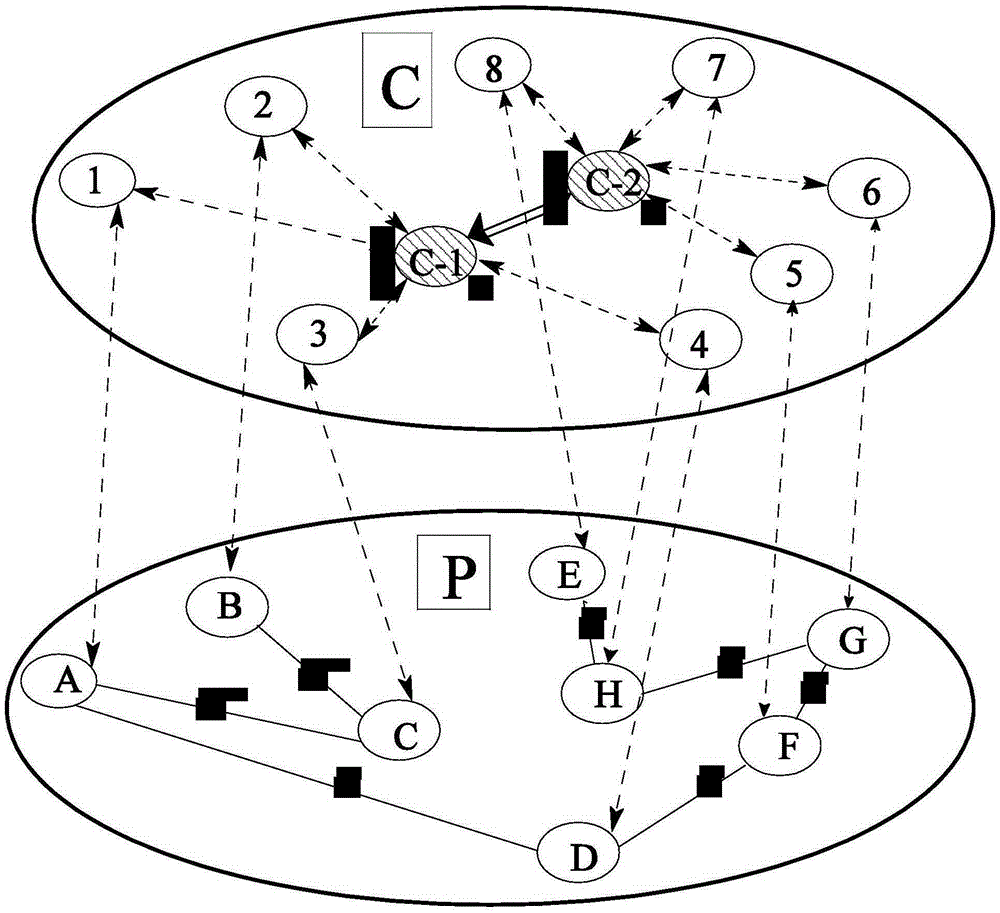
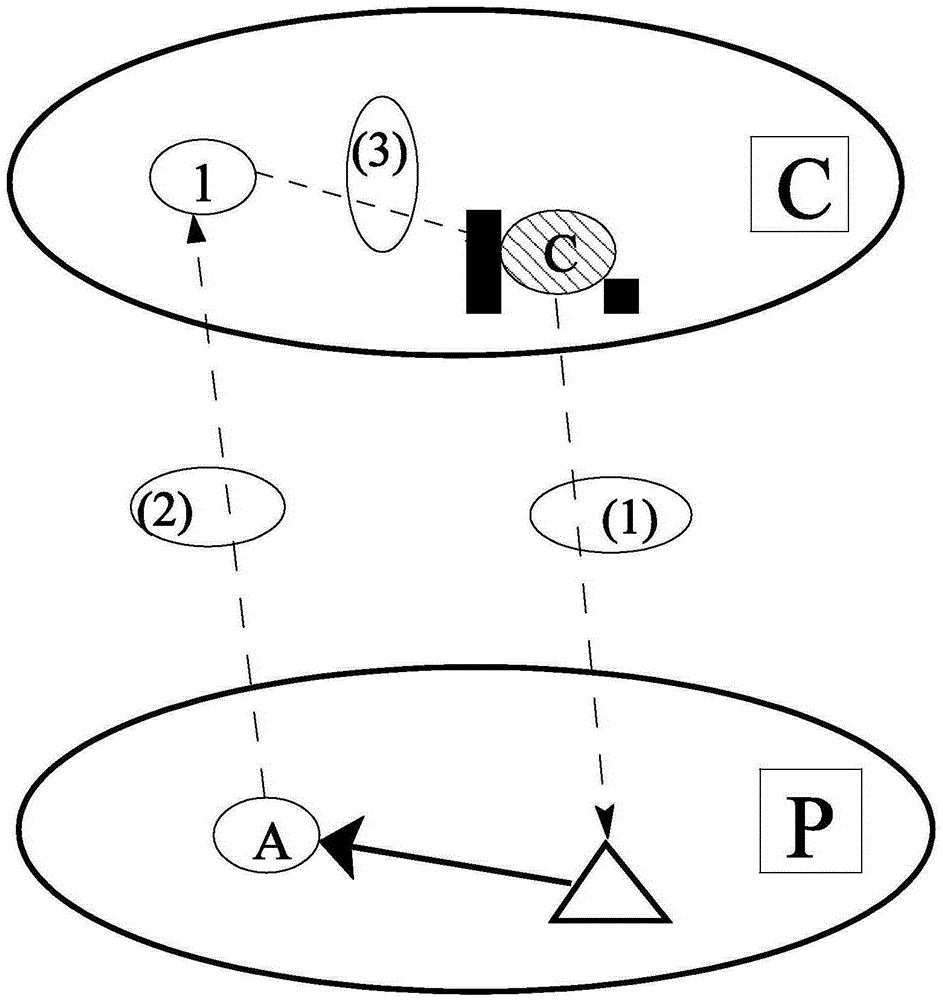
[0038] figure 1 It is a schematic diagram of the topology structure of the power cyber-physical system. The system presents a two-layer network topology, including the components of the power physical network and the power information network, as well as gateways and routers that ensure the interconnection of the two networks.
[0039] The lower nodes A to H are the power physical network nodes, representing generators, transformers and load nodes. The undirected solid lines between the nodes are transmission lines, and the black squares on the connection line are circuit breakers. The entire lower network represents the power physical network system. Correspondingly, the upper nodes 1 to 8 are information network nodes, representing various secondary equipment of the power grid, includin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com