Security protocol authentication method based on mobile RFID system
A technology of security protocols and authentication methods, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of short service life, low efficiency, and the system being vulnerable to illegal attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
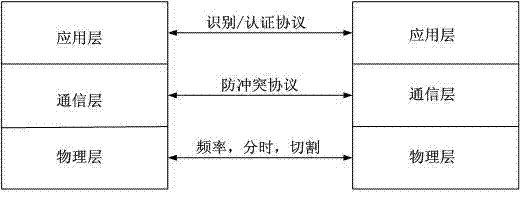
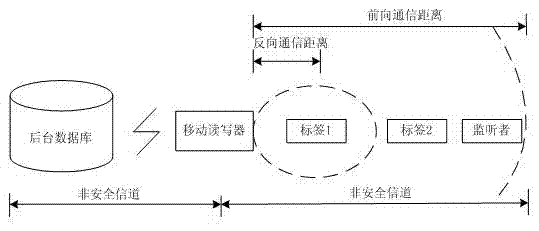
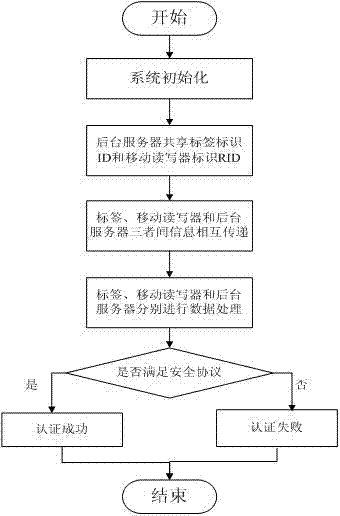
[0057] The present invention is aimed at the two-way authentication protocol based on the dynamic ID and the Hash function mechanism under the environment of the mobile RFID system, and the overall flow of the system image 3 , in the authentication protocol, the tags, mobile readers, and background servers are transmitted in ciphertext, which effectively protects the security of information, and ensures that attackers cannot be eavesdropped, tracked, Fake and replay.
[0058] Below in conjunction with embodiment, refer to Figure 4 , describe the specific implementation steps of the present invention:
[0059] protocol initial conditions
[0060] In the initial stage of the agreement, the server database stores the information of tags and mobile readers, mainly including ,in Indicates the ID value of the previous successful authentication, Indicates that generated during this authentication process Value, the initial value is the random key shared by the database an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com