Creditability verification method for routers in wireless ad hoc network
A wireless self-organizing network and verification method technology, applied in the field of router trusted verification and privacy protection system, can solve the problems of privacy protection difficulty and topology structure variability, and achieve good privacy protection, good applicability, and protection of private information. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
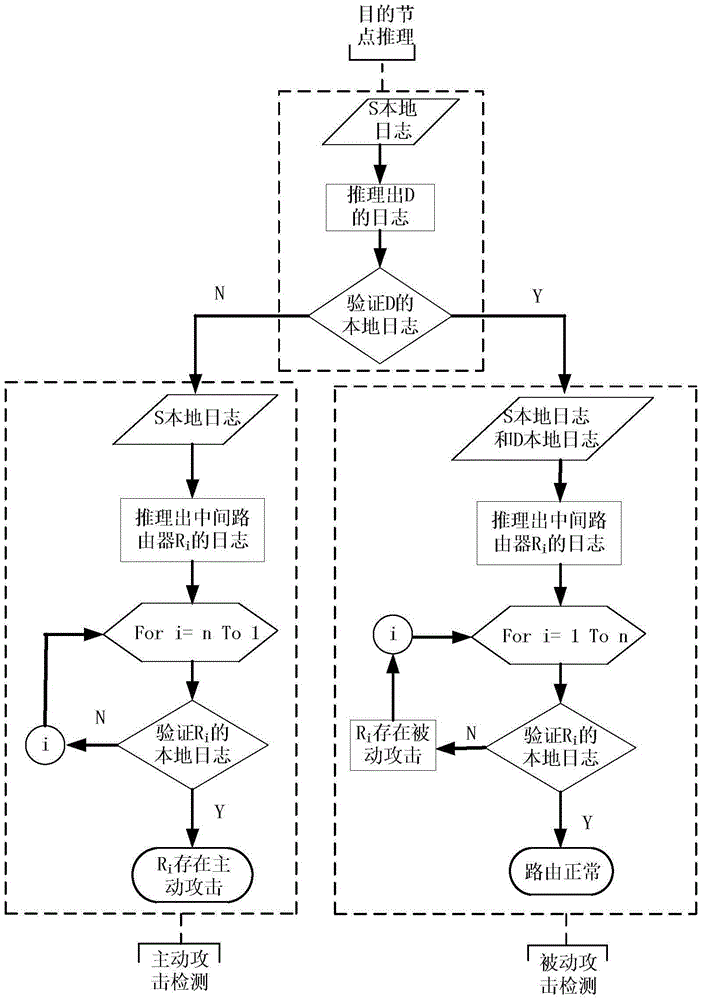
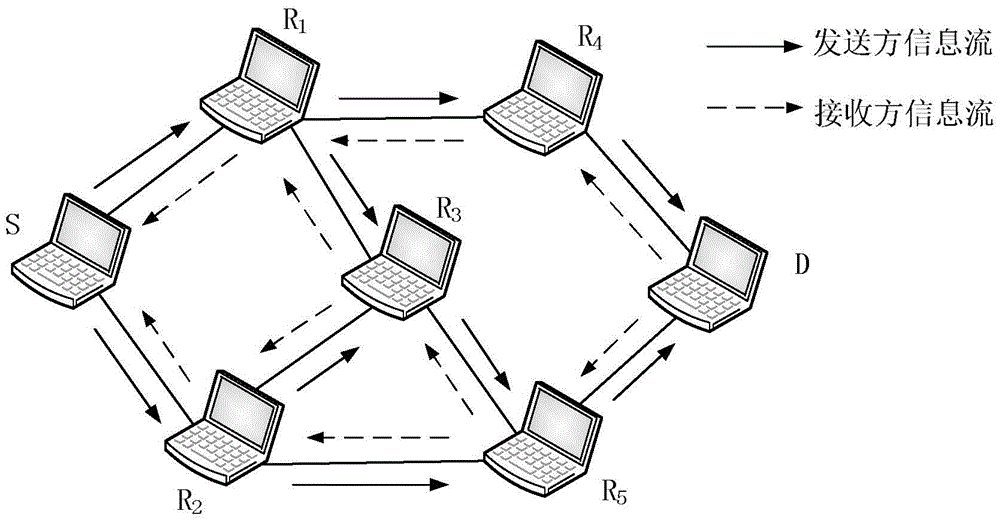
[0032] Based on the existing wireless router communication, the present invention combines the characteristics of the wireless network, network resource management, network security requirements, etc., obtains the correct router log information through formal reasoning, and encodes the router log information, and then uses the password The log information is verified using the Merkle HashTree, which effectively ensures the security of router communication in the wireless network and the requirements of attack detection.
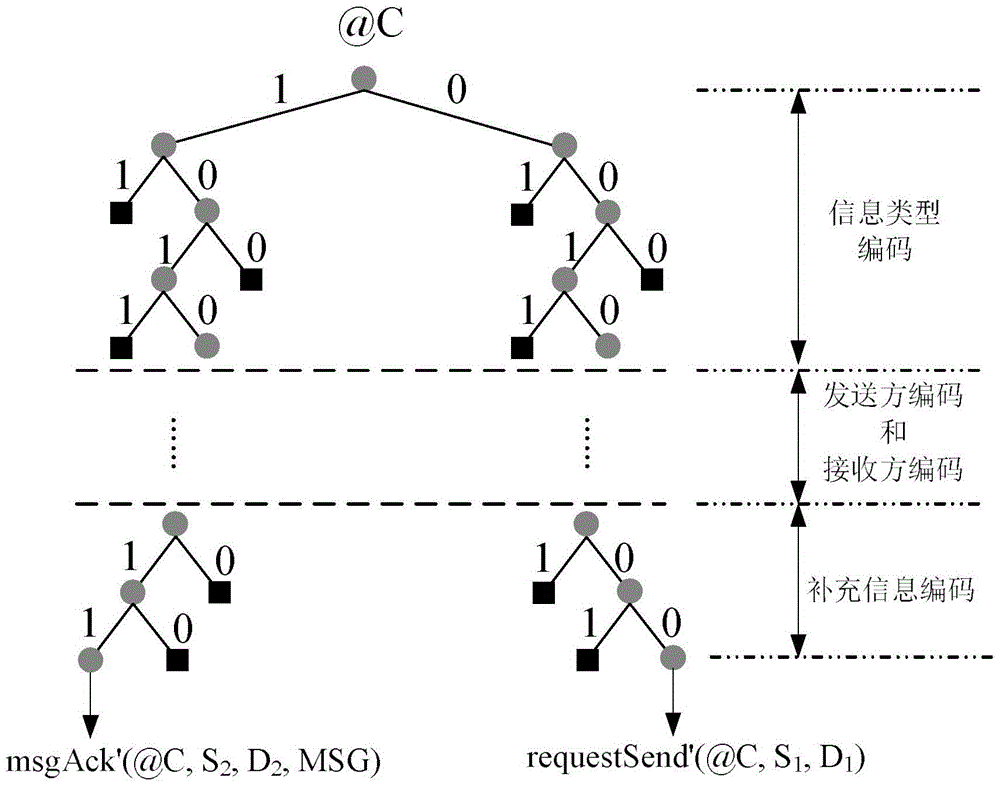
[0033] In the present invention, the log information reasoning of the receiver and the intermediate forwarding router is carried out according to the handshake protocol communication rules for transmitting messages between nodes in the wireless ad hoc network, and the communication rules are described using NDlog syntax, as shown in Table 1.
[0034] Table 1 Communication rules
[0035]
[0036] In Table 1, there are 10 inference rules, where C represents ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com