Anti-attack encrypting positioning method and device of wireless sensor network
A wireless sensor and positioning method technology, applied in the field of communication, can solve the problems of performance degradation, positioning system impact, and inability to meet wireless sensor networks, etc., and achieve the effects of low power consumption, integrity protection, high confidentiality and independence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] The following describes the wireless sensor network anti-attack encrypted positioning method according to Embodiment 1 of the present invention.
[0057] (1) Encryption method
[0058] The beacon node BN (beaconnode) generates a ranging message, which contains the ID of the beacon node and the transmission power Pi. Assuming that the binary ranging message that the beacon node BN needs to transmit is k, the encoding process of the transmitter for:
[0059] 1) Carry out Manchester encoding on the ranging message k, that is, m=Manchester(k), to obtain the code word m. The rule is that 1 corresponds to "01" and 0 corresponds to "10". For example, if k="1010", m="01100110" can be obtained.
[0060] 2) Using a pseudo-random modulation method to perform pseudo-random processing on the code word m to obtain a pseudo-random signal, that is, a signal code b, where b=PR(m).
[0061] 3) During the information sending process, the message code b is continuously sent in the form ...
Embodiment 2
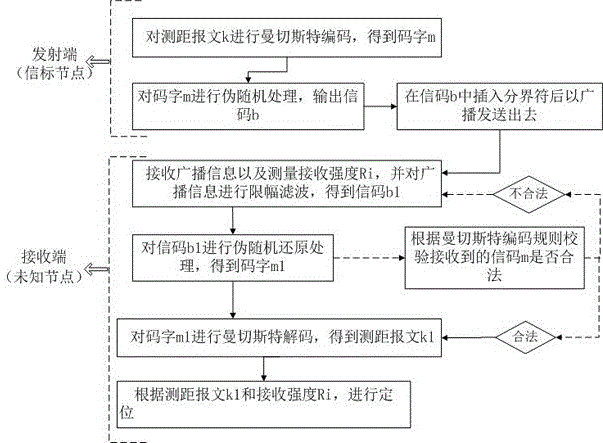
[0076] Such as figure 2 As shown, it is a block flow diagram of the wireless sensor network anti-attack encrypted positioning method according to the second embodiment of the present invention.
[0077] (1) Encryption method
[0078] The beacon node BN (beaconnode) generates a ranging message, which contains the ID of the beacon node and the transmission power Pi. Assuming that the binary ranging message that the beacon node BN needs to transmit is k, the encoding process of the transmitter for:
[0079] 1) Perform Manchester coding on k, that is, m=Manchester(k). The rule is that 1 corresponds to "01" and 0 corresponds to "10", such as k="1010", m="01100110" can be obtained.
[0080] 2) Using a pseudo-random modulation method to perform pseudo-random processing on m to obtain a pseudo-random signal, that is, a signal code b, where b=PR(m).
[0081] 3) In the process of sending information, a delimiter is inserted into the signal code b and then sent out at regular interv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com