A traceability-based user information authentication method
An authentication method and technology for user information, applied in transmission systems, electrical components, etc., can solve the problems of passwords being easily peeped by others, low stability, and difficult to remember.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The specific embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings.
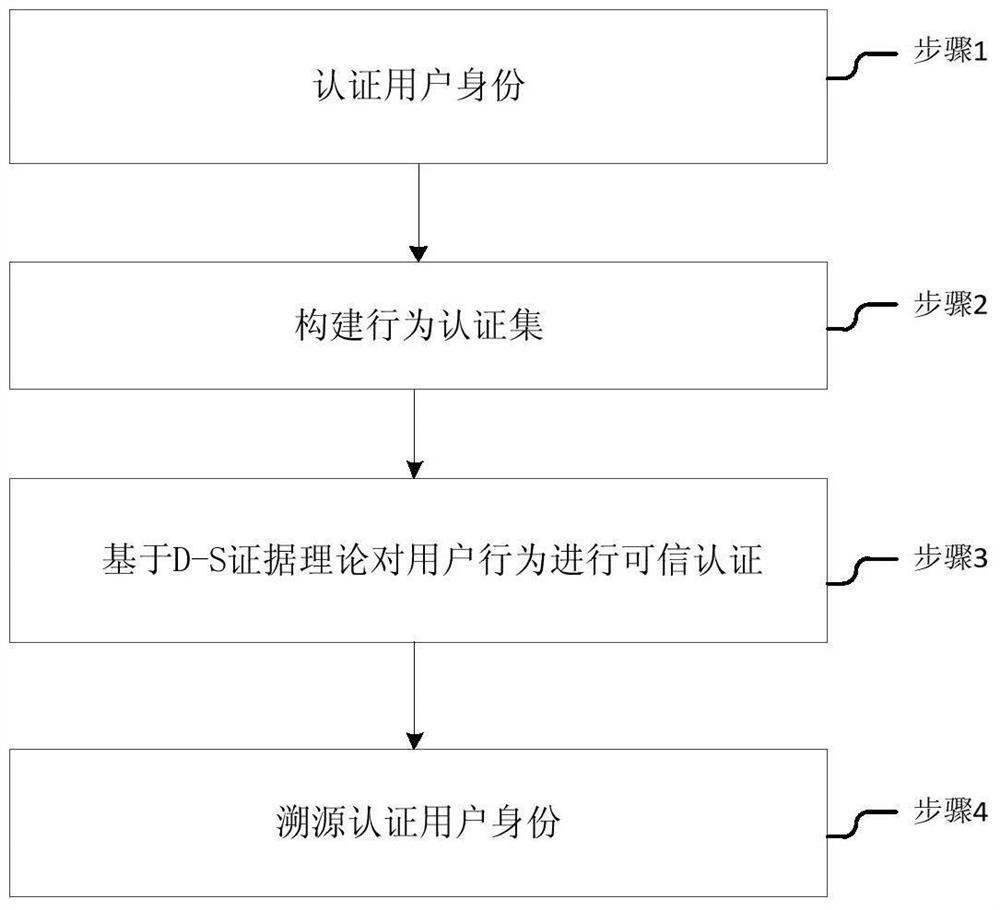
[0041] Such as figure 1 As shown, a user information authentication method based on traceability, the method includes the following steps:
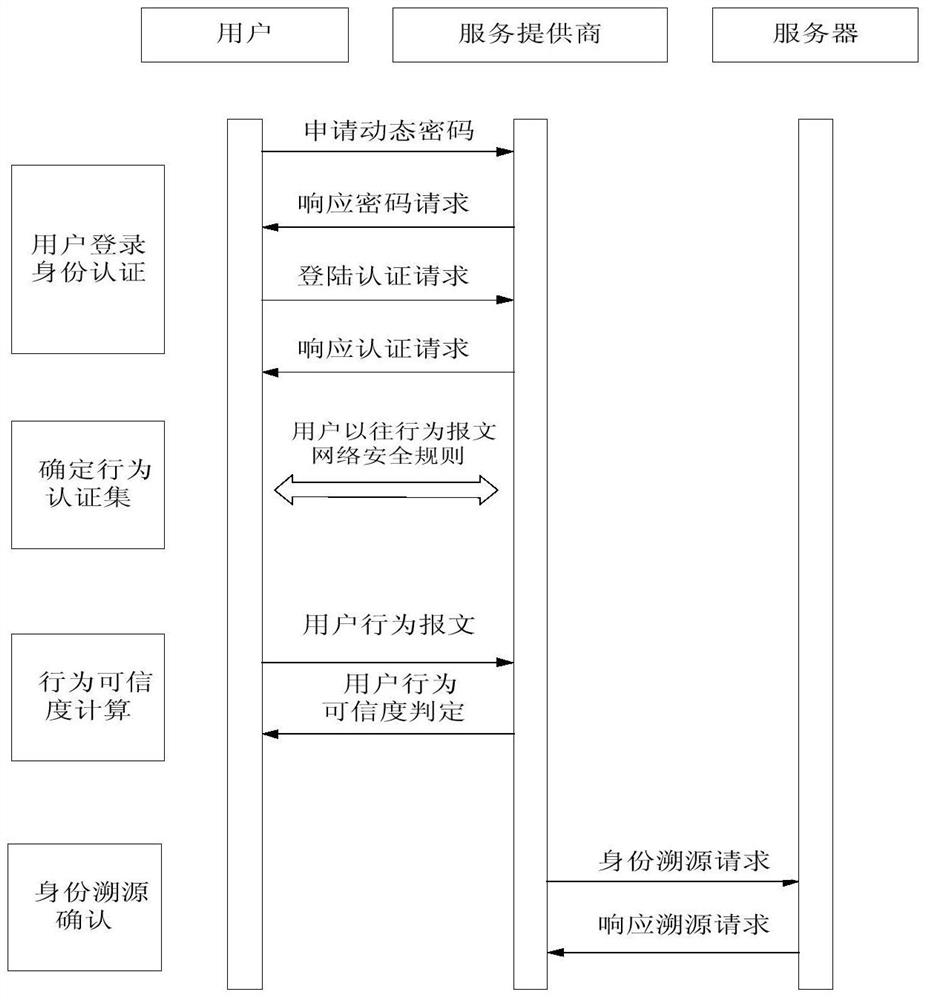
[0042] 1) authentication user identity; step 1) in, authentication user identity comprises, the user sends a request message to server, after server receives this message, extracts the user IP address that it contains and the negation operation rule of binary number;
[0043] Use the inversion operation rule to invert the user's IP address bit by bit, generate a dynamic password, and return the receipt to the user;
[0044] After the user obtains the dynamic password, fill in the user name and dynamic password and submit them to the server for authentication. If the authentication is successful, the user is allowed to enter the network system and go to step 2); otherwise, the login fails.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com