A method and system for detecting program vulnerabilities
A detection method and detection system technology, applied in error detection/correction, software testing/debugging, instruments, etc., can solve the problems of waste of manpower and system resources, single source of vulnerabilities, and easy misjudgment, so as to reduce workload and obtain The effect of enriching sources, improving efficiency and testing coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
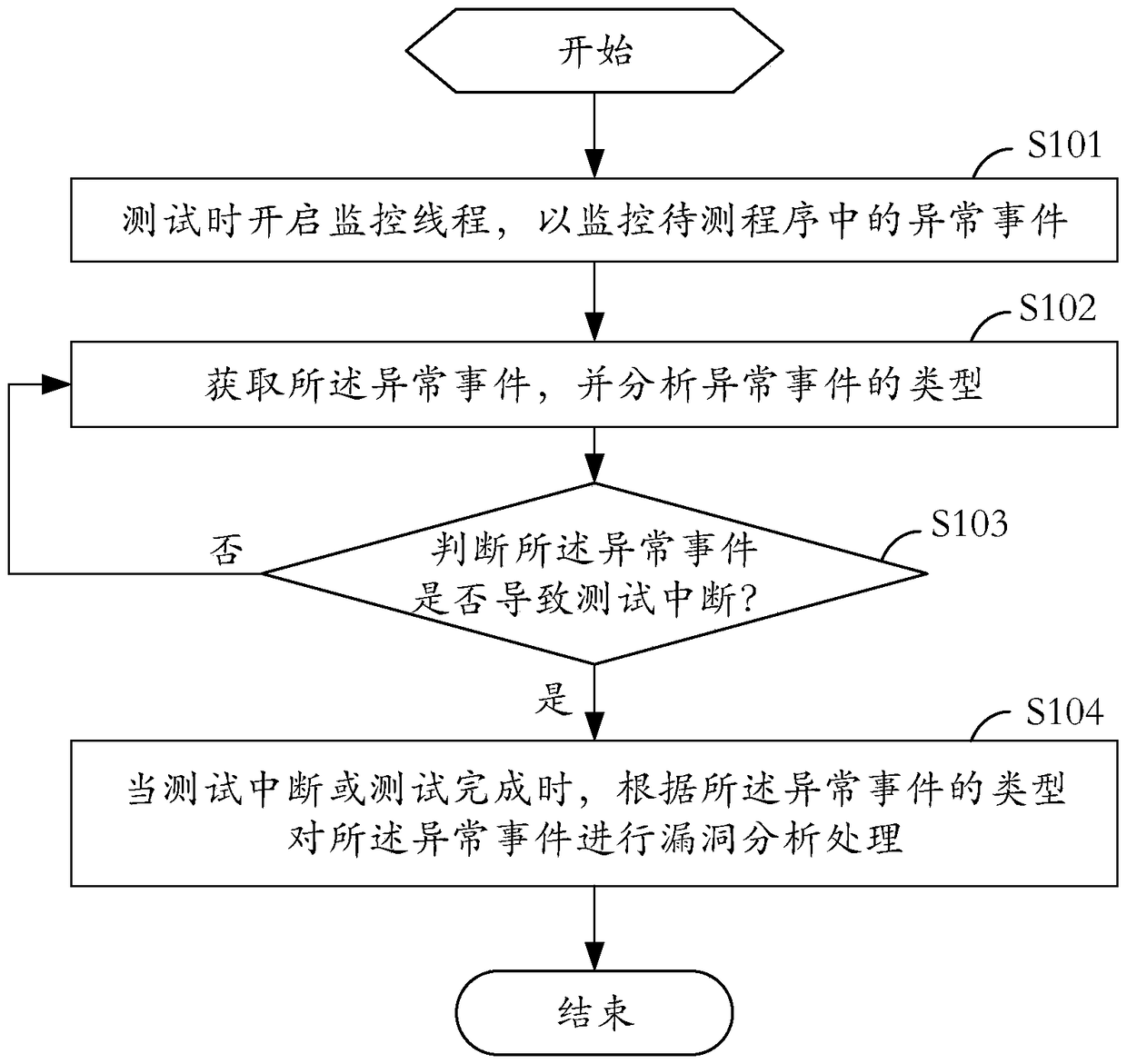
[0027] see figure 1 , is a schematic flowchart of a method for detecting a program vulnerability provided by an embodiment of the present invention.
[0028] The detection method of the program vulnerability includes:
[0029] In step S101, during testing, a monitoring thread is started, and the monitoring thread is used to monitor abnormal events in the program to be tested.
[0030] Wherein, the monitoring thread includes: an interface monitoring thread and a log monitoring thread. The interface monitoring thread is used to monitor the interface of the program to be tested, such as Figure 5A As shown, to analyze whether there is an abnormal event originating from the interface; the log monitoring thread monitors the log of the program to be tested, such as Figure 5B Shown to analyze whether there are abnormal events from logs.
[0031] The monitoring thread is also used to record the abnormal event and the source of the abnormal event, and the source includes: an inter...
Embodiment 2
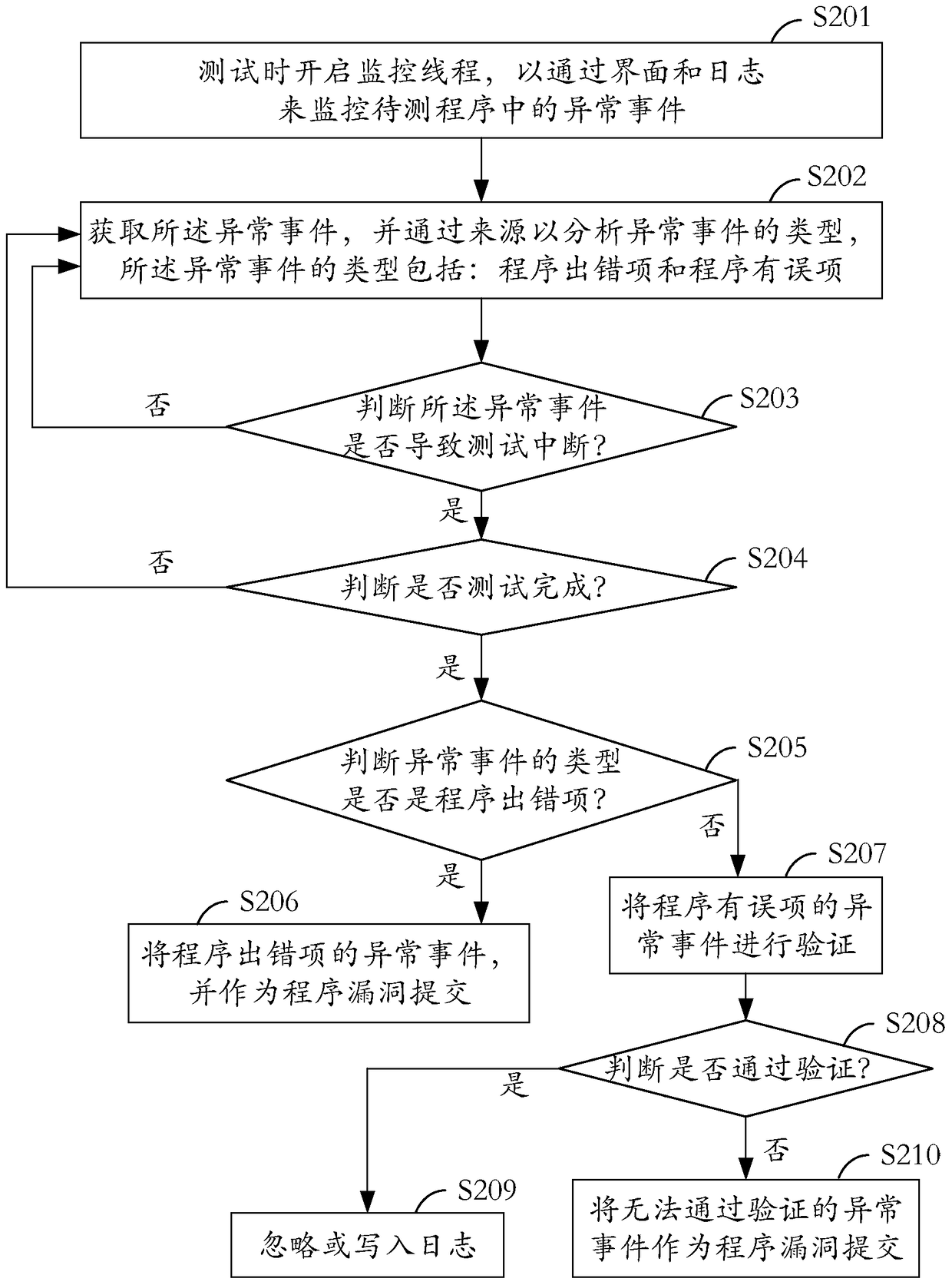
[0045] see figure 2 , is a schematic flowchart of a method for detecting a program vulnerability provided by an embodiment of the present invention.
[0046] The detection method of the program vulnerability includes:
[0047] In step S201, a monitoring thread is started during testing, so as to monitor abnormal events in the program under test through the interface and logs.
[0048] Specifically, this step includes:
[0049] (1) Open monitoring thread during test, described monitoring thread comprises: interface monitoring thread and log monitoring thread, monitor simultaneously through interface and log, make the acquisition source of abnormal event abundant, accurate, and need not manual intervention;
[0050] (2) monitor the interface of the program under test through the interface monitoring thread, such as Figure 5A As shown, to analyze whether there is an abnormal event originating from the interface, for example: whether there is an error keyword in the interface...
Embodiment 3
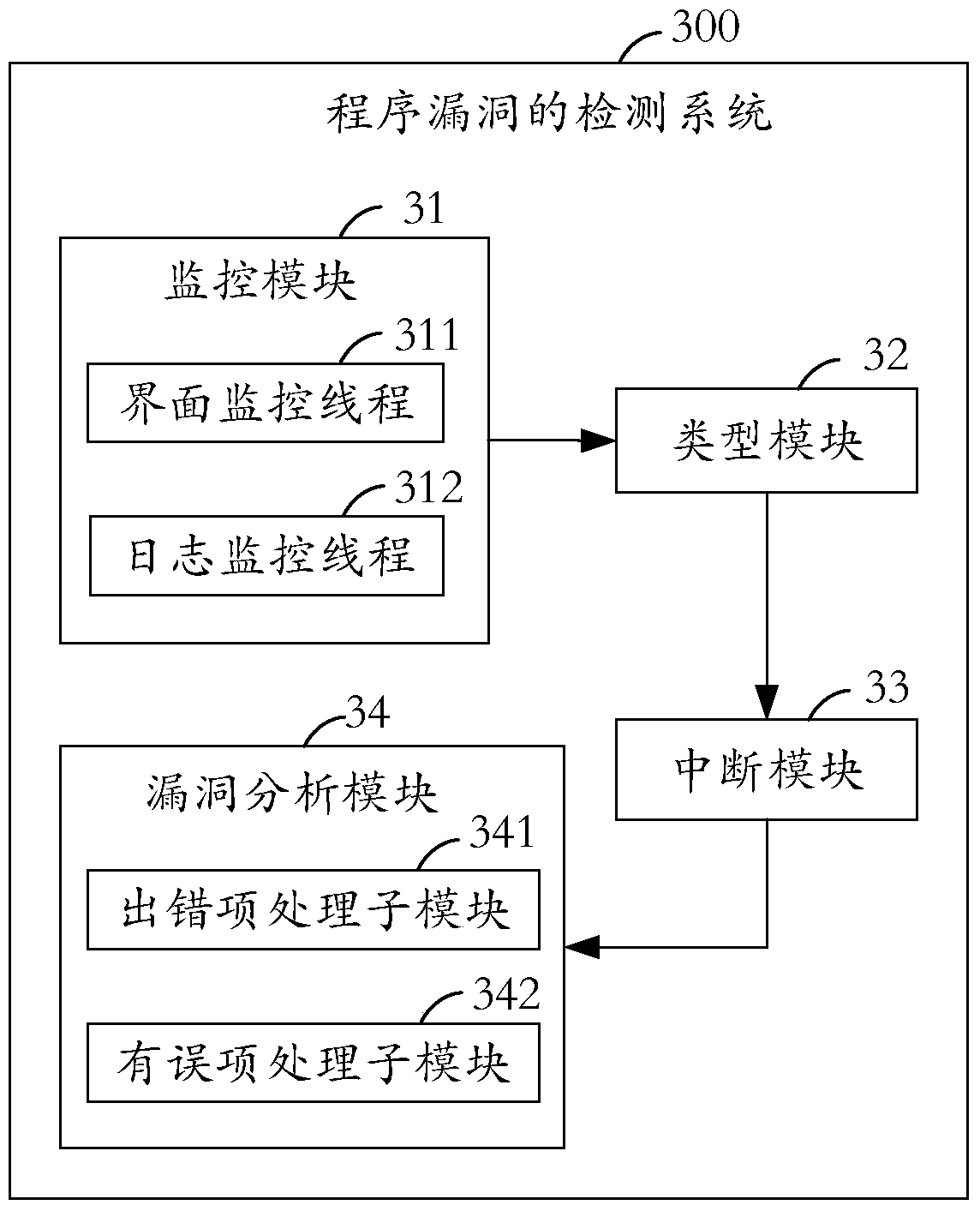
[0082] see image 3 , is a block diagram of a program vulnerability detection system provided by an embodiment of the present invention.
[0083] The program vulnerability detection system 300 includes: a monitoring module 31 , a type module 32 , an interruption module 33 , and a vulnerability analysis module 34 .
[0084] The monitoring module 31 is used for starting a monitoring thread during testing, and the monitoring thread is used for monitoring abnormal events in the program to be tested.
[0085] Wherein, the monitoring thread 31 includes: an interface monitoring thread 311 and a log monitoring thread 312 .
[0086] Specifically, the interface monitoring thread 311 is used to monitor the interface of the program to be tested, such as Figure 5A Shown to analyze whether there are abnormal events originating from the interface. The log monitoring thread 312 monitors the log of the program to be tested, such as Figure 5B Shown to analyze whether there are abnormal ev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com