Method of client authorization and authentication based on b/s architecture system
A system client, S architecture technology, applied in the field of client authorization and authentication based on B/S architecture, to avoid potential security risks, avoid phishing, and reduce the probability of installation permissions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be described in further detail below through examples, and the following examples are explanations of the present invention and the present invention is not limited to the following examples.
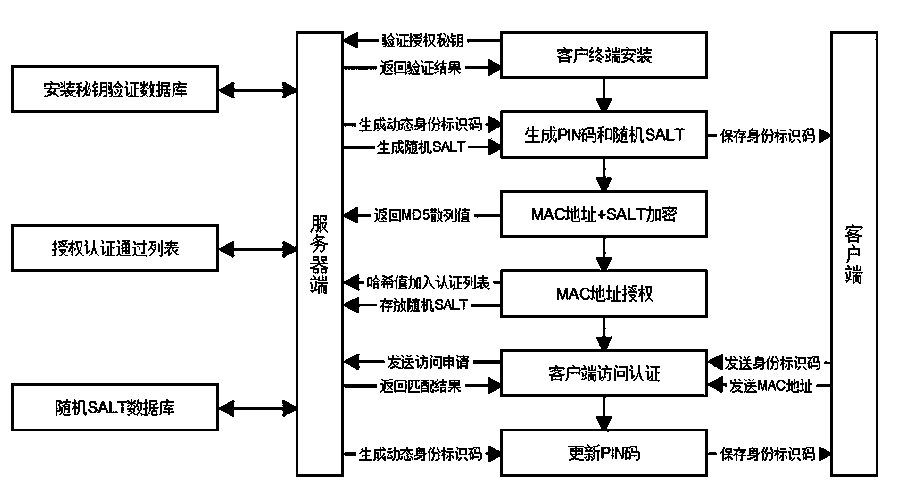
[0029] As shown in the figure, a method for client authorization and authentication based on B / S architecture system of the present invention comprises the following steps:
[0030] 1 Client terminal installation.
[0031] When installing the client terminal on the host, the user can obtain and install the client terminal software only by using the unique key to authenticate the authorized identity. When installing a client terminal, the user applies for a unique key to the server. After the server passes the verification, it sends the unique key to the client terminal in the installation key verification database. The key authentication time is 24 hours. If the software installation fails, you need to re-apply for a new authorization key. The key must...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com