Malicious software identification method
An identification method and malware technology, applied in the field of petroleum machinery, can solve problems such as low efficiency, and achieve the effects of solving low efficiency, reducing time and calculation amount, and improving virus detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
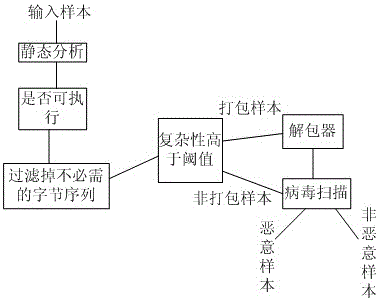
[0035] Please refer to figure 1 , the application provides a malware identification method, the method comprising:
[0036] Step 1: Input a sample, perform static analysis on the sample, and obtain analysis data;
[0037] Step 2: Perform complexity calculation based on the analysis data to obtain complexity data;
[0038] Step 3: Determine whether the complexity data is greater than the threshold, if the complexity data is greater than or equal to the threshold, send the sample to the unpacker to extract the obfuscated code, and send the extracted sample to the virus scanning system Perform scanning and identification; if the complexity data is less than the threshold, the sample is directly sent to the virus scanning system for scanning and identification.
[0039] The technical effect of the present application is: accurately distinguish between packaged (or obfuscated) and non-packaged (or non-confused) executable files in a simple and fast manner, and has the function of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com