ROP (Return-Oriented Program) protection method based on attack tree
An attack tree and protection program technology, applied in the field of ROP protection based on attack tree, can solve the problems of inappropriate use and high overhead, and achieve the effects of low overhead, improved protection effect, and improved protection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
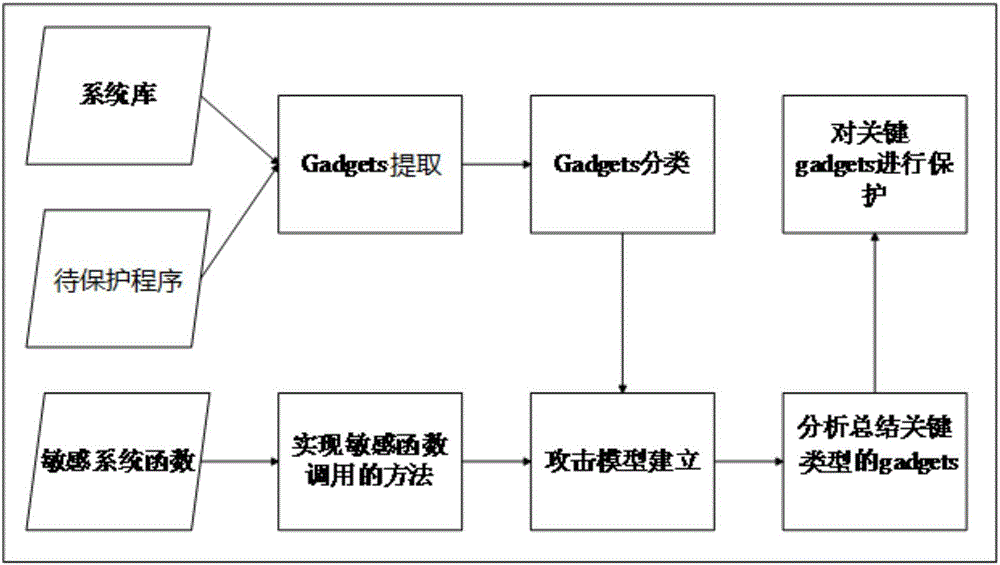
[0030] The ROP protection method based on attack tree of the present invention, see figure 1 , including the following steps:
[0031] Step 1, select the program and system library files to be protected
[0032] It is specifically mentioned here that the system library file is also used as an input. The reason is that the system library file comes with the operating system, and there are also gadgets instruction fragments in it. Some remote attacks target system library files if the attacker finds gadgets instruction fragments in the system library files and hijacks the control flow, so that the attacker can still perform control flow hijacking attacks without knowing the source code.
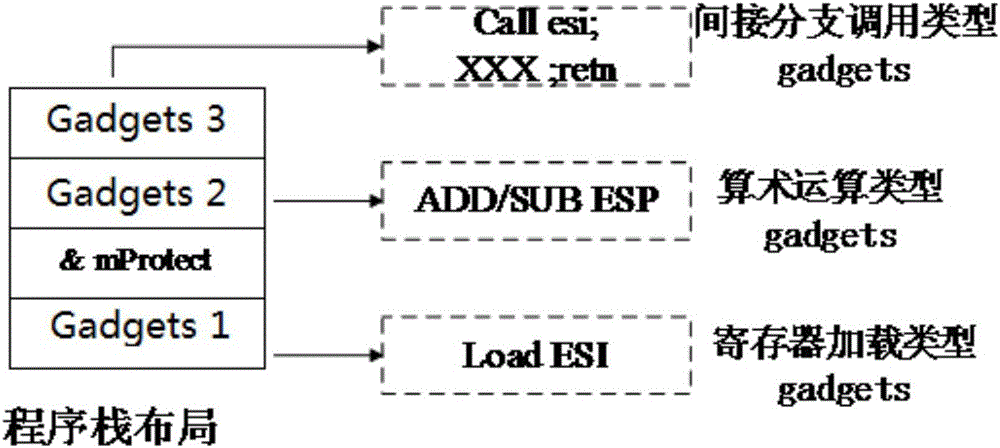
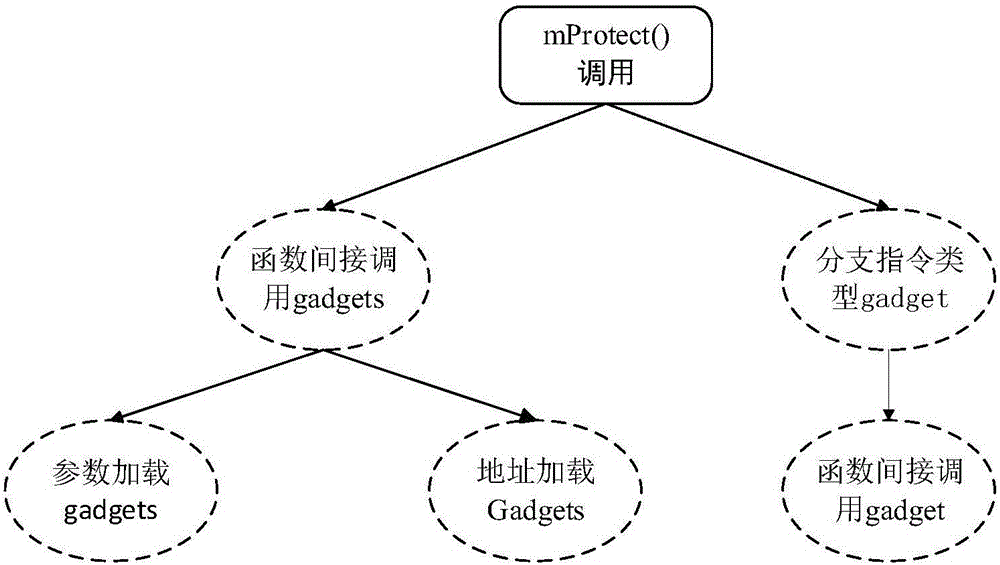
[0033] Step 2, extract the gadgets instruction fragments in the program to be protected and the system library file
[0034] To extract the gadgets instruction fragments in the program to be protected and the library file, an existing tool can be used, such as the mona plug-in. The mona plug...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com