Software network authentication binding method and system
A technology of network authentication and software, applied in transmission systems, electrical components, etc., can solve problems such as easy to be illegally embezzled, unreliable software authentication, etc., and achieve the effect of preventing embezzlement and improving reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
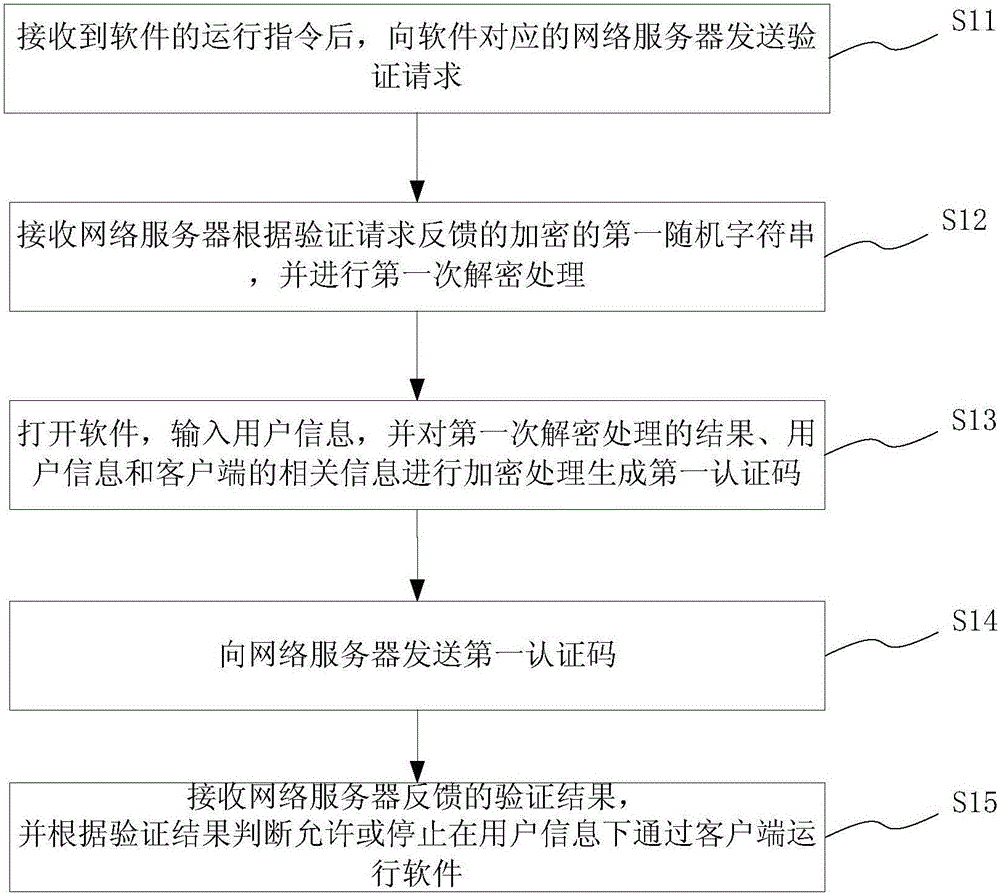
[0061] Such as figure 1 As shown, this embodiment discloses a network authentication binding method for software when the client runs the software, which is implemented through a software authentication binding system on the terminal side, specifically including:
[0062] Step S11, after receiving the running instruction of the software, send a verification request to the network server corresponding to the software:
[0063] When the software authentication binding system on the terminal side receives the software running instruction from the client, it will automatically read the machine code of the client running the software; and send a verification request to the network server through the client.
[0064] Wherein, the machine code is obtained by processing the hardware code of the client; and the hardware code can uniquely identify the client, including but not limited to the serial number of the machine, the MAC address of the network card, or the time stamp of software...
Embodiment 2
[0091] This embodiment also discloses a software network authentication binding method when the client runs the software, which is realized by a software authentication binding system on the terminal side. The network authentication binding method of the software in this embodiment is exactly the same as step S11 and step S12 of the network authentication binding method in embodiment 1, only in order to further ensure that the software and the client are not attacked by the counterfeit server, in step S13 ~ Step S15 is slightly changed.
[0092] Step S13, open the software, input the user information, and encrypt the result of the first decryption process, the user information, the relevant information (machine code) of the client, and the second random character string randomly generated by the client to generate the second random character string. an authentication code;
[0093] Wherein, the second random character string is randomly generated by the software authenticatio...
Embodiment 3
[0103] This embodiment discloses a terminal-side software authentication binding system 500, such as Figure 5 shown, including:
[0104] A verification request sending module 510, configured to send a verification request to the network server 100 corresponding to the software after receiving the running instruction of the software;
[0105] The receiving module 520 is configured to receive feedback information fed back from the network server 100; the feedback information includes an encrypted first random string generated by the network server 100 and a verification result;
[0106] The processing module 530 is configured to perform a first decryption process on the received encrypted first random character string, and generate a first authentication code.
[0107] Wherein, the first authentication code is generated by encrypting the result of the first decryption process, user information and related information of the client;
[0108] The first authentication code is ge...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com