Method for acquiring logged-on user password from memory mirroring documents of 64-bit Windows operation system
A technology of memory mirroring and operating system, which is applied in the field of obtaining plaintext passwords of logged-in users, can solve problems such as long time, and achieve the effect of accurate analysis methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
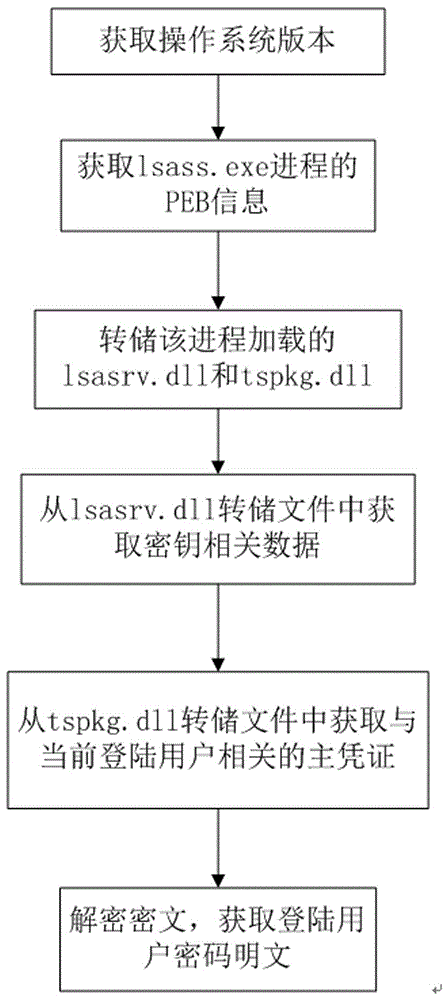
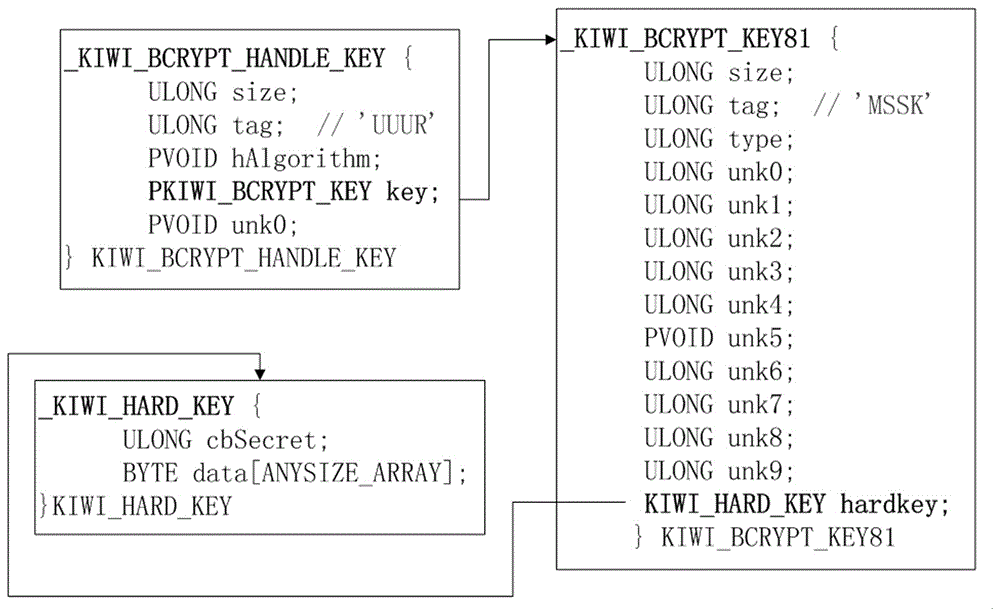
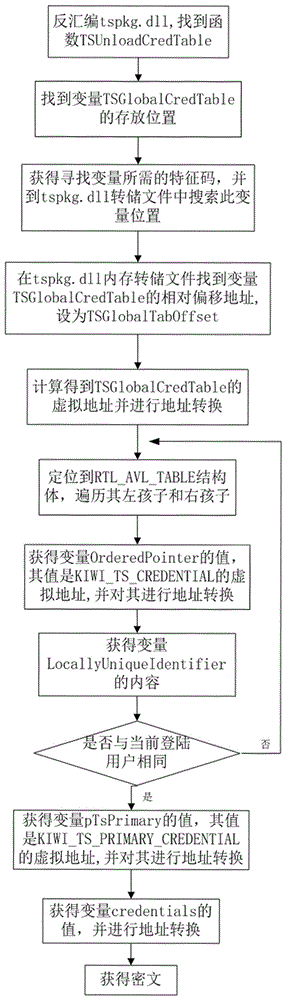
[0021] Such as figure 1As shown, the flow chart of the method for obtaining the plaintext of the logged-in user password from the memory image file of the 64-bit windows operating system of the present invention is provided, which follows "obtaining the operating system version——obtaining the lsass.exe process structure—— Obtain the key - obtain the certificate - decrypt the ciphertext" process. Since the process executes the required function through the dynamic link library loaded by it, the decryption work can be performed by analyzing the dynamic link library loaded by the process performing the login authentication function. Such as figure 1 As shown, the method for obtaining the plaintext of the logged-in user password from the memory image file of the 64-bit windows operating system of the present invention first needs to obtain the operating s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com