Logistics information security encryption method based on identity authentication and system based on identity authentication
A logistics information and identity verification technology, which is applied in the field of identity verification-based logistics information security encryption method and system, can solve personal privacy threats and other issues, and achieve the effect of eliminating security risks and controlling costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] A method and system for secure encryption of logistics information based on identity verification. The workflow of the secure logistics information system is as follows:
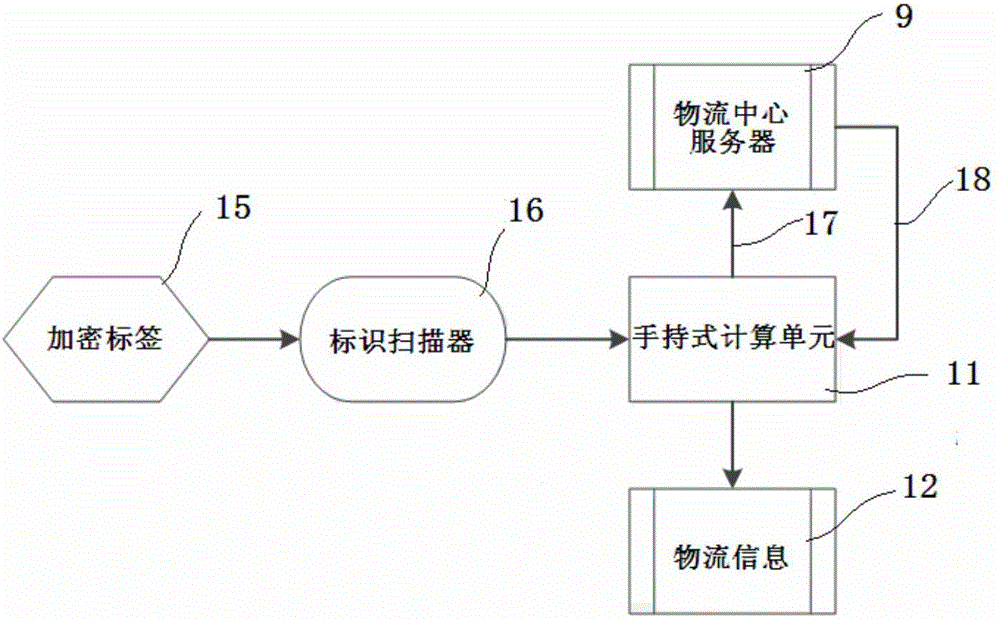
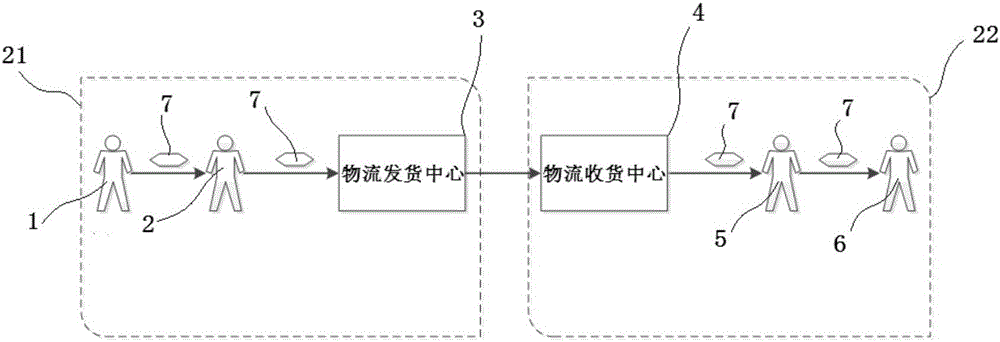
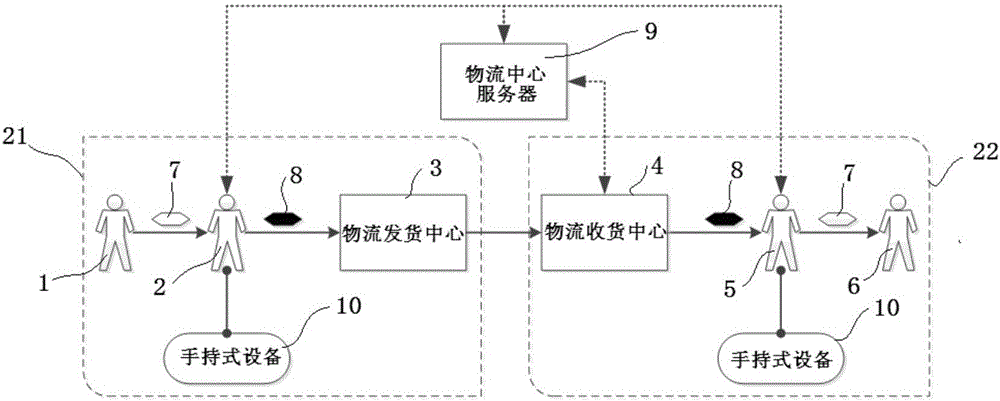
[0036] Such as figure 2 , image 3 As shown, in the goods-picking stage 21, item information processing step 101: when the goods-hunter 2 picks up goods from the sender 1, he inputs the logistics information on the handheld device 10, and communicates with the logistics center server 9 through the handheld device 10 Exchange the encryption key, after encrypting the logistics information, output the encrypted encrypted label 15 through the label printer 14, the encrypted label 15 is a logistics pattern identification (such as a two-dimensional code or a radio frequency electronic tag), which is attached to the item 7 and becomes information encryption Item 8 is then handed over to logistics delivery center 3. The information on the encrypted label 15 includes: encrypted basic logistics information (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com