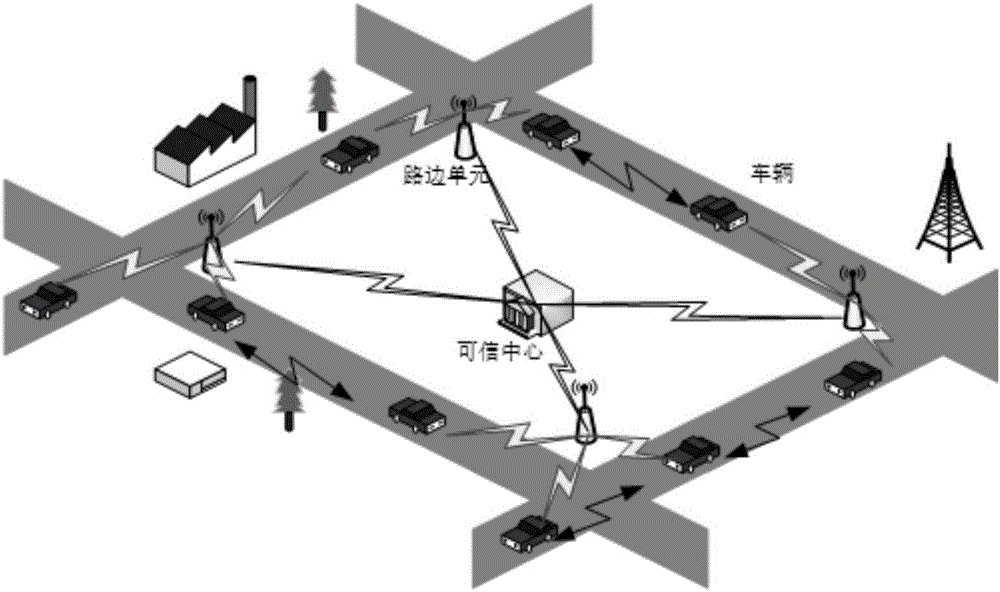
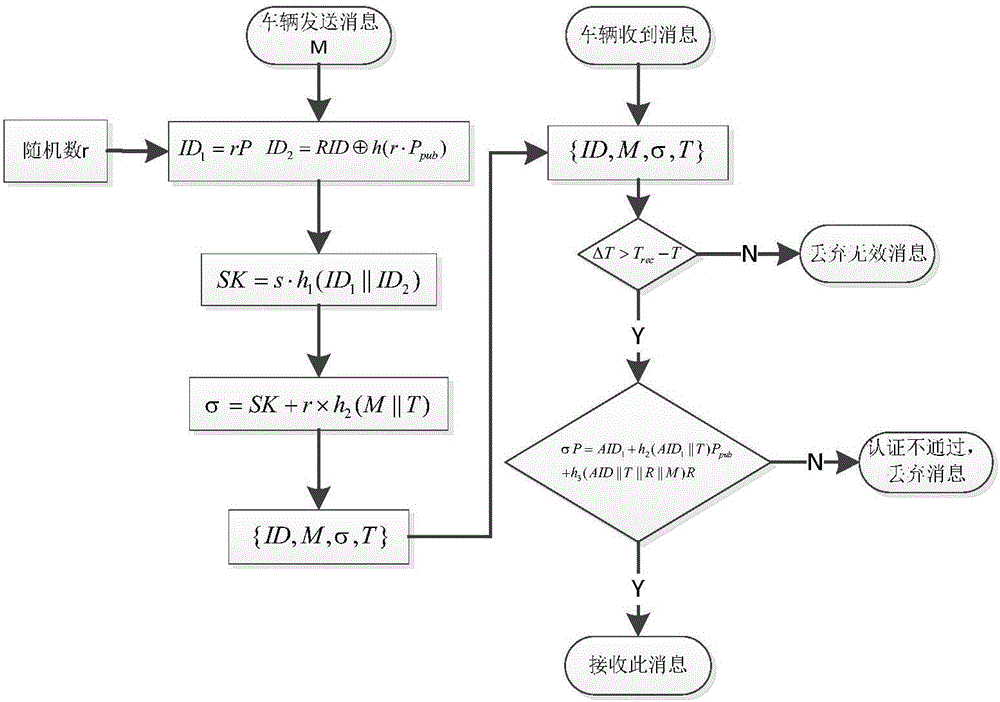
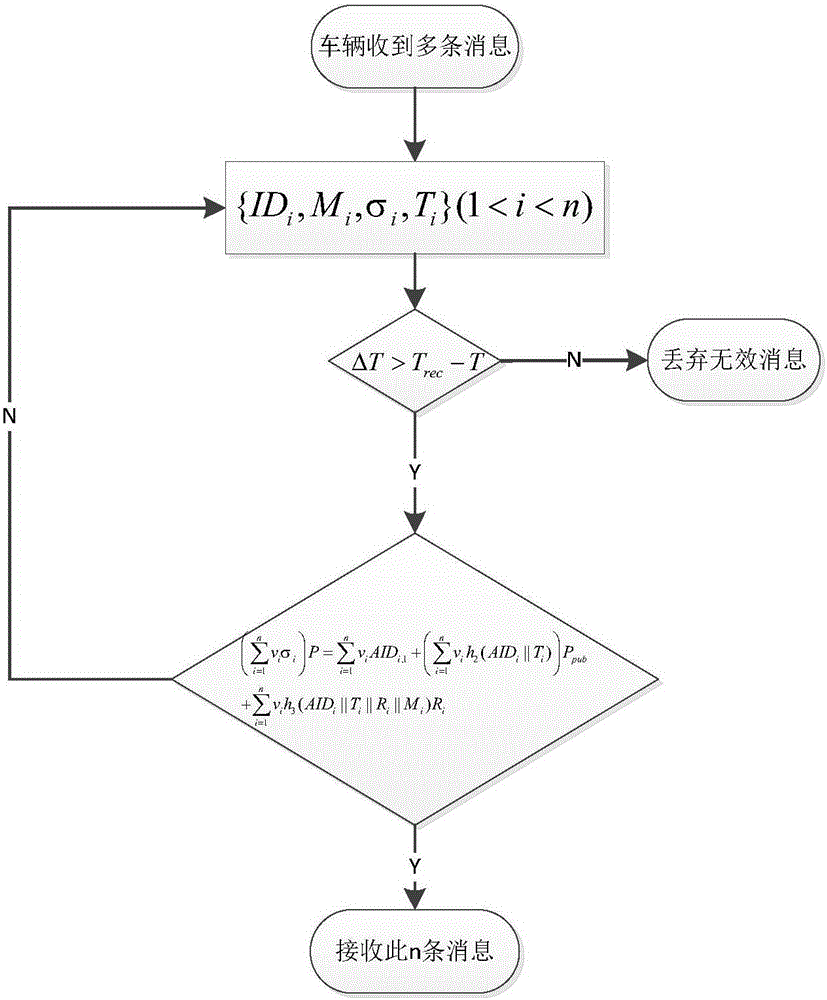
Efficient condition privacy protection and security authentication method in internet of vehicles
A technology for privacy protection and security authentication, applied in the field of Internet of Vehicles and wireless communication, can solve problems such as excessive computing overhead, security loopholes, unsatisfactory, etc., to achieve the effect of reducing computing overhead and ensuring communication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] In bilinear pairing-based schemes, the bilinear map The group G in is generated on the elliptic curve y 2 =x 3 On +xmodn, where n is a 512-bit prime number, and the order q of the group G is a 160-bit prime number. In the scheme based on elliptic curve encryption ECC, when the same security level is achieved, the group G used is generated on the elliptic curve y 2 =x 3 On +ax+bmodn, where n is a 160-bit prime number and order q is a 160-bit prime number. Some of the main cryptographic operations are defined as follows, T bp is the time to perform a bilinear pairing operation, and the time to perform a scalar point product in a group based on bilinear pairings is T mp-bp , the time to perform a scalar point multiplication in the group based on elliptic curve ECC is T mp-ecc ,T mtp is the time to execute a hash function that maps to elements on the group. In the hardware environment of the Intel I7-4770 processor with a main frequency of 3.40GHz, 4Gb memory and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com