Low-electric-leakage bi-CPU core safe chip configuration
A security chip, nuclear security technology, applied in data processing power supply, electrical digital data processing, instruments and other directions, can solve the problems of static power consumption can not be ignored, software design increases the difficulty, etc., to achieve the effect of reducing the overall power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
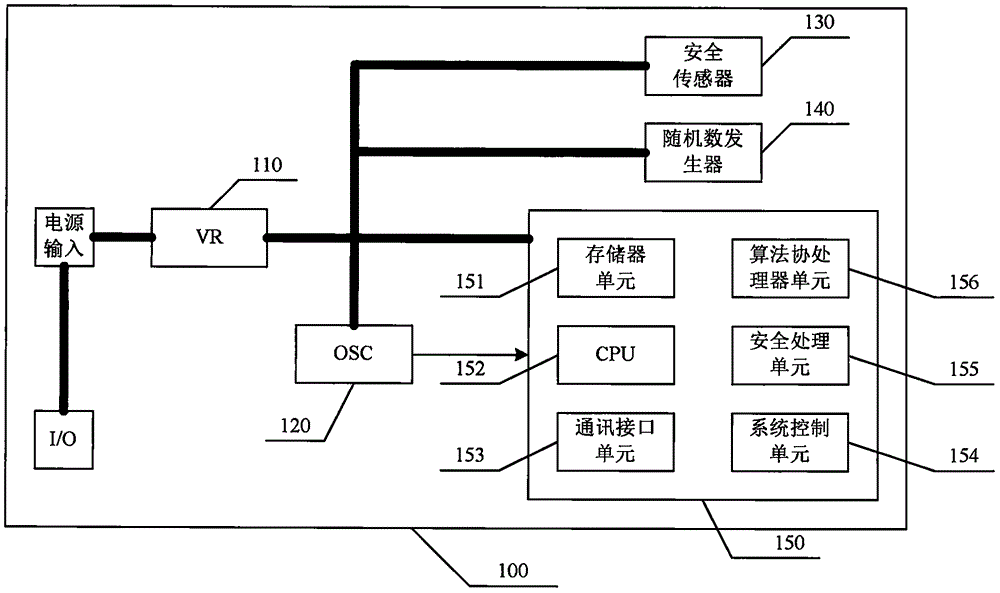
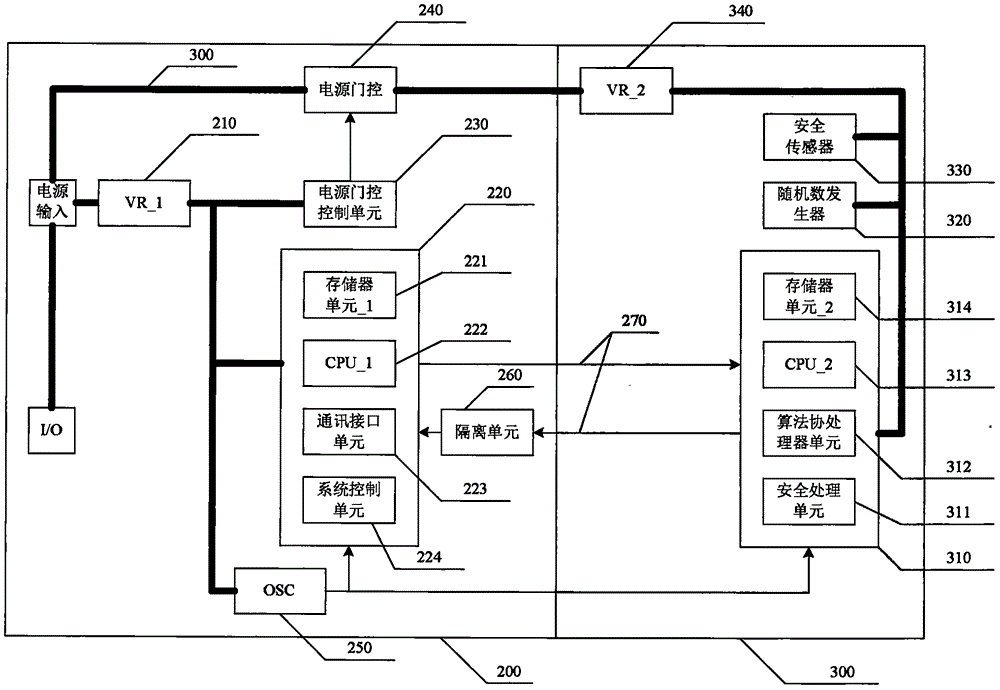
[0009] As shown in FIG. 2, in the security chip, there are two CPU subsystems, one is the CPU_1 subsystem (200), and the other is the CPU_2 subsystem (300). The CPU_1 subsystem completes communication interface processing and instruction analysis, and the CPU_2 subsystem provides cryptographic computing services and sensitive information processing. The CPU_1 subsystem and the CPU_2 subsystem have their own physically separated memory resources, and exchange data through a dedicated data channel (270).
[0010] CPU_1 (222) can adopt standard 8051 and other non-safety CPU cores with low logic gate count and low computing power. In order to realize communication processing and instruction analysis, memory unit_1 (221) and communication interface unit (223) are integrated through a simple system bus. and system control unit (224), memory unit_1 includes RAM and ROM required for normal operation of CPU_1. Because the function is relatively simple, the size of this part of the mem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com