Improved network access control method and device
A technology of network access control and network access, which is applied in the field of improved network access control methods and devices, can solve problems such as lack of adaptability, and achieve the effect of strong flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
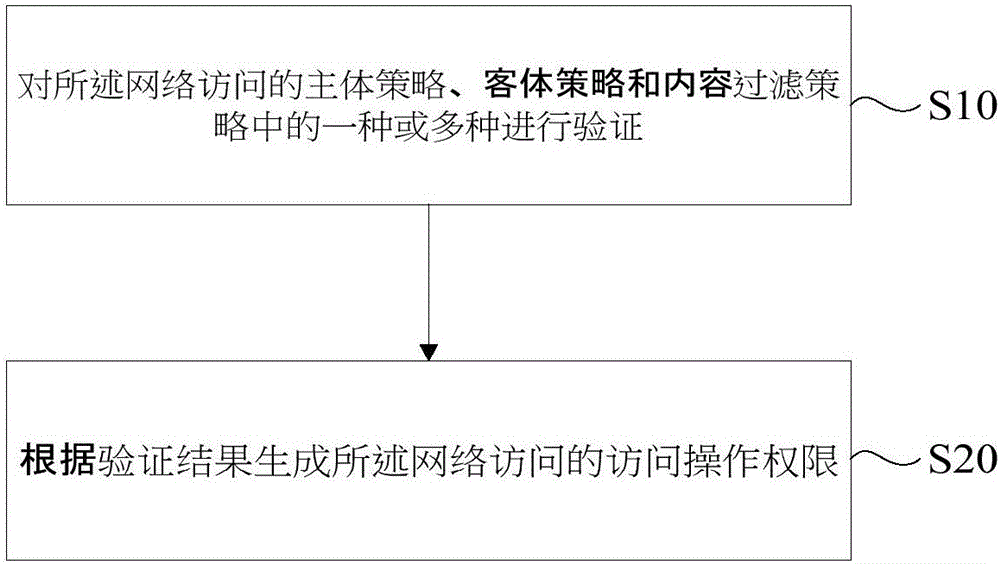
[0034] Access Control (Access Control) refers to the means by which the system restricts the user's identity and the predefined policy group to which it belongs to use data resources. It is usually used by system administrators to control users' access to network resources such as servers, directories, and files. Access control is an important basis for system confidentiality, integrity, availability, and legal use. It is one of the key strategies for network security prevention and resource protection. Authorized access.
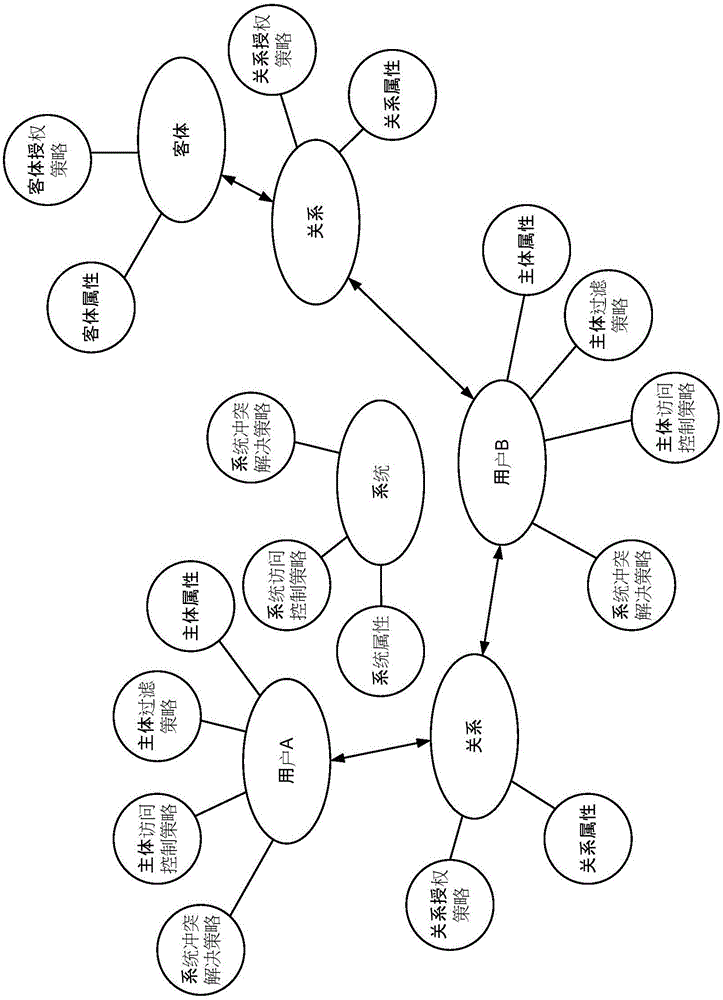
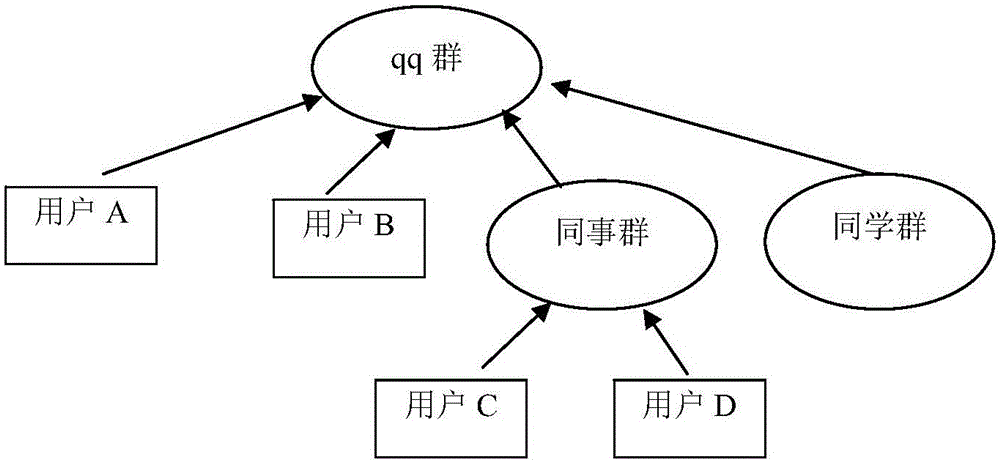
[0035] A social network includes multiple subjects and multiple objects in the network. Network access control includes three elements: subject, object and control strategy.
[0036] (1) Subject S (Subject). Refers to a specific request to access a resource. It is the initiator of an action, but not necessarily the executor of the action. It may be a user, or a process, service, or device started by the user.
[0037] (2) Object O (Object). Refers to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com