Secure communication method based on memristor chaotic system
A technology of chaotic system and secure communication, applied in secure communication, transmission system, digital transmission system through chaotic signals, etc., can solve the problems of difficult to guarantee security, vulnerable to attack, etc., and achieve convenient physical implementation, difficult to crack, dimension high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to better understand the technical solution of the present invention, the implementation manner is further described in detail below, and an application example is used to illustrate the specific implementation manner, but is not limited thereto.
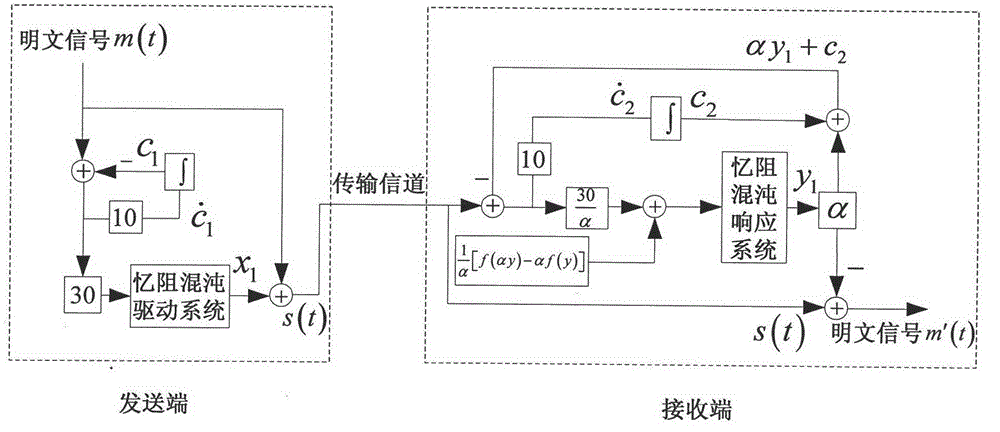
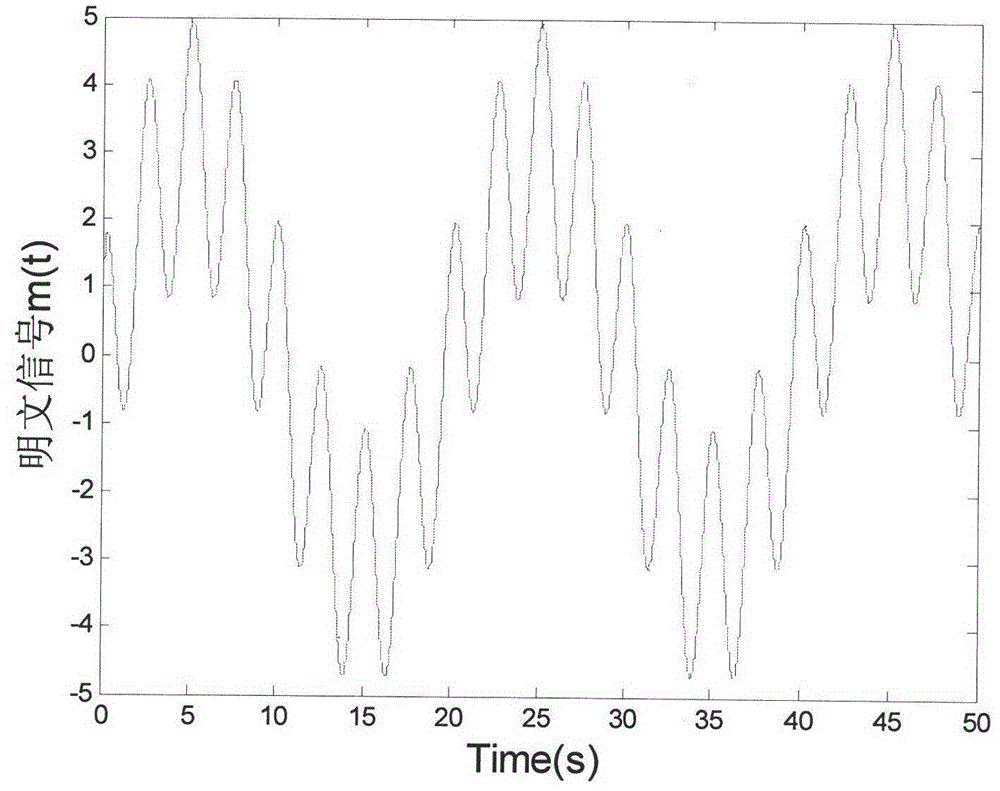
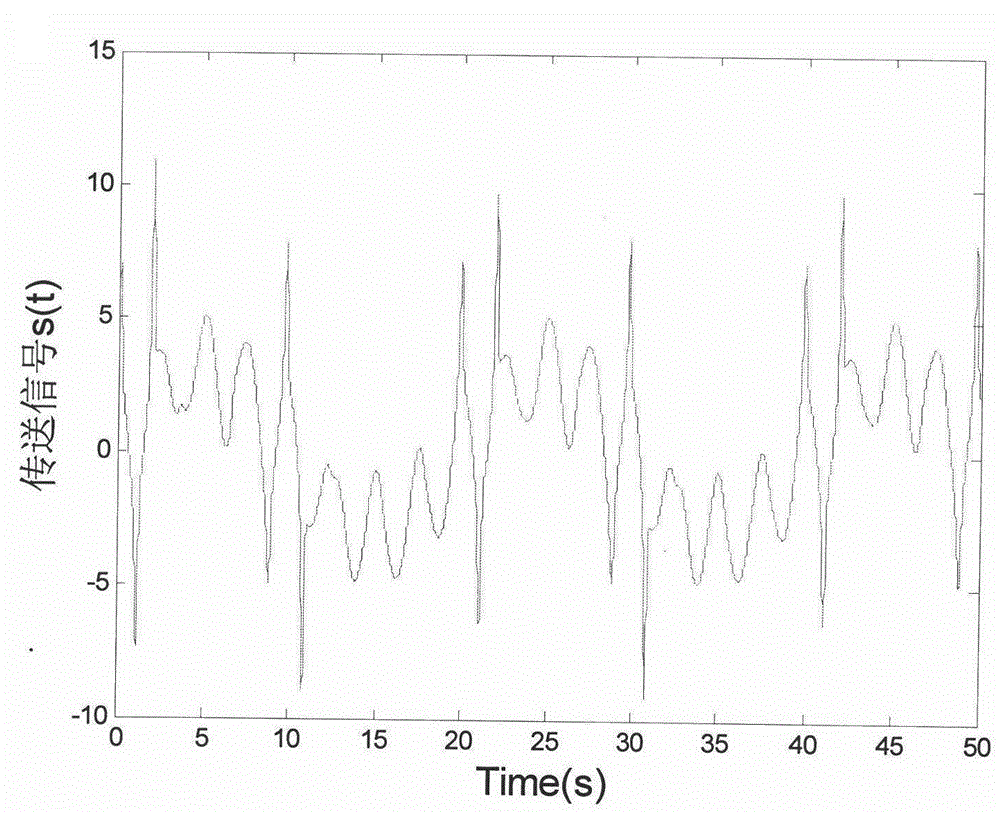
[0025] The plaintext signal to be encrypted is designed as m(t)=3sin(0.1πt)+2cos(0.8πt), where t represents time. The overall structural block diagram of the inventive method is as figure 1 As shown, the specific implementation method can be divided into the following steps:
[0026] (1) Description of four-dimensional memristive chaotic system
[0027] a. Establish memristive chaotic driving system
[0028] The memristive chaotic driving system is selected as
[0029] x · 1 = 10 ( x ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com